By Yong Yang
This article explains how to address security risks from data leaks by encrypting sensitive data, such as AccessKey IDs, with keys generated by Key Management Service (KMS). Additionally, it demonstrates how to efficiently manage the primary AccessKey ID for Microservices Engine (MSE) by using KMS's secret management capabilities, ensuring a secure and controllable end-to-end business experience without exposing AccessKey IDs.
Many users increasingly store sensitive data in Nacos, such as data sources, tokens, usernames, and passwords, when using Nacos to manage configurations. First, user-built Nacos instances lack security protection and are vulnerable to attacks. Second, sensitive information stored in plaintext is easily stolen, which poses significant risks to the company's information security. Multi-Level Protection Scheme (MLPS) Level 3 is a scheme that aims to protect important information systems. It has the following requirements for application and data security:
• Secure coding principles should be followed in the software development process to reduce potential vulnerabilities.
• Data should be encrypted as necessary during storage and processing, and data integrity check mechanisms should also be set up.
• After sensitive data, such as AccessKey IDs, is compromised, its plaintext is easily obtained and can be directly exploited.
KMS provides an integrated solution for encrypting and decrypting sensitive configurations in MSE Nacos. In this solution, KMS encrypts and decrypts sensitive configurations and MSE Nacos stores the encrypted configurations. The following figure shows the overall product logic architecture.
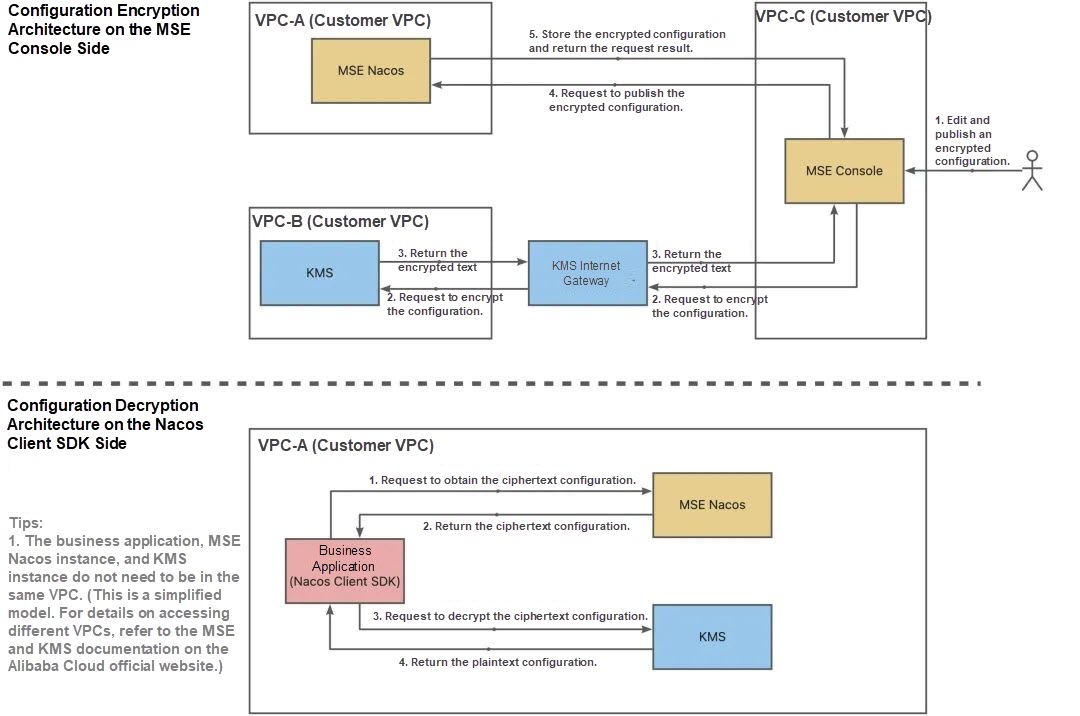
The overall architecture shows that sensitive configurations are transmitted and stored in ciphertext throughout the entire solution, which significantly enhances the security of these configurations.
From the perspective of security and compliance, KMS provides the following features in the configuration encryption and decryption solution for MSE Nacos:
Sensitive data is encrypted on the application side, and the ciphertext is stored in the Nacos configuration center to effectively prevent sensitive data breaches.
MSE Nacos helps you configure and enable TLS data transmission encryption to ensure secure transmission links and prevent data from being intercepted.
On the application side, the Nacos client stores the encrypted configuration data on disks. In the MSE console, you can export or import plaintext configurations and ciphertext configurations with one click, create data backup policies for users and provide valid paths. The MSE console will support scheduled backup policies for ciphertext data. Stay tuned for updates.
MSE provides you with one-stop configuration lifecycle management. You can create, modify, view, and delete encrypted configurations and normal configurations in the MSE console.
MSE provides fine-grained (down to the single configuration dimension) Resource Access Management (RAM) permission control. You can configure fine-grained and multi-dimensional permission control policies based on specific scenarios.
MSE records all configuration operation information, including key details such as configuration change time, operator, and change content, making the entire data process traceable.
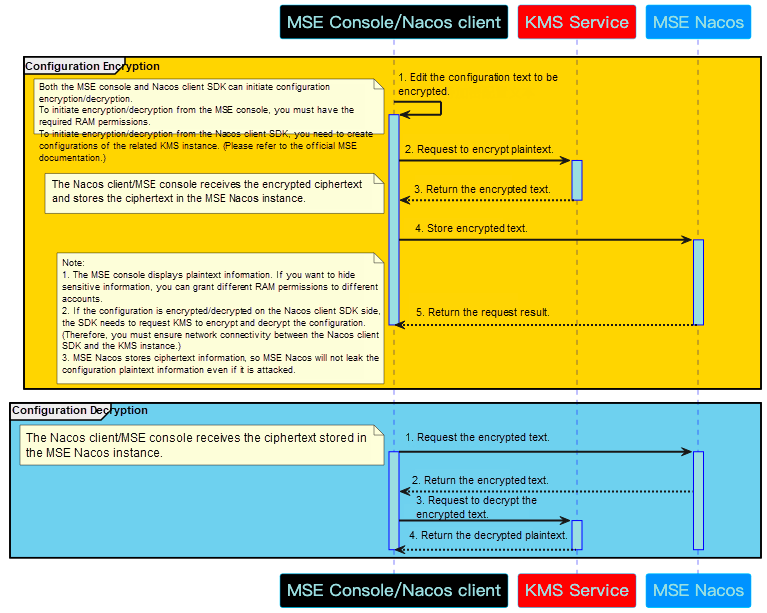
As you can see, the entire process involves four entities: MSE console, Nacos client (i.e. the business application side), KMS service, and MSE Nacos. The process of configuration encryption is as follows:
• The MSE console/Nacos client SDK (i.e. the business application side) edits the configuration text to be encrypted. Note that both the MSE console and Nacos client SDK can initiate configuration encryption/decryption. To initiate encryption/decryption from the MSE console, you need to log on to the MSE console on the Alibaba Cloud official website and have the required RAM permissions. To initiate encryption/decryption from the Nacos client SDK, you need to create configurations of the related KMS instance. The creation method will be described later.
• The MSE console/Nacos client SDK requests the KMS service to encrypt the edited plaintext configurations.
• The KMS service returns the ciphertext configurations to the MSE console/Nacos client SDK.
• The MSE console/Nacos client SDK requests MSE Nacos to store the ciphertext configurations. Note that all plaintext configurations are used on the MSE console/Nacos client SDK side, and MSE Nacos stores only the ciphertext configurations. Therefore, even if MSE Nacos is attacked, no plaintext information of any encrypted configurations will be disclosed. This means you only need to focus on securing the business application side, significantly reducing data security risks.
• MSE Nacos returns the result to the MSE console/Nacos client SDK.
Configuration decryption is essentially the reverse process of configuration encryption and will not be discussed further here. Note that you can obtain all plaintext configurations from the MSE console/Nacos client SDK but cannot obtain them from MSE Nacos.
This section describes how to use the configuration encryption capability provided by MSE. For more information, see "Configuration encryption" in the MSE documentation.
The entire best practice mainly includes the following steps:
• Activate MSE.
• Log on to the MSE console and create a Nacos engine that uses the Developer Edition or Professional Edition.
• Activate KMS.
• Log on to the KMS console, create a dedicated KMS instance, and create a key.
• In the MSE console, enable the configuration encryption feature, bind the KMS key to the Nacos instance, and create and use encrypted configurations.
• Create and use encrypted configurations through the Nacos client SDK.
You can log on to the MSE console to view and activate MSE.
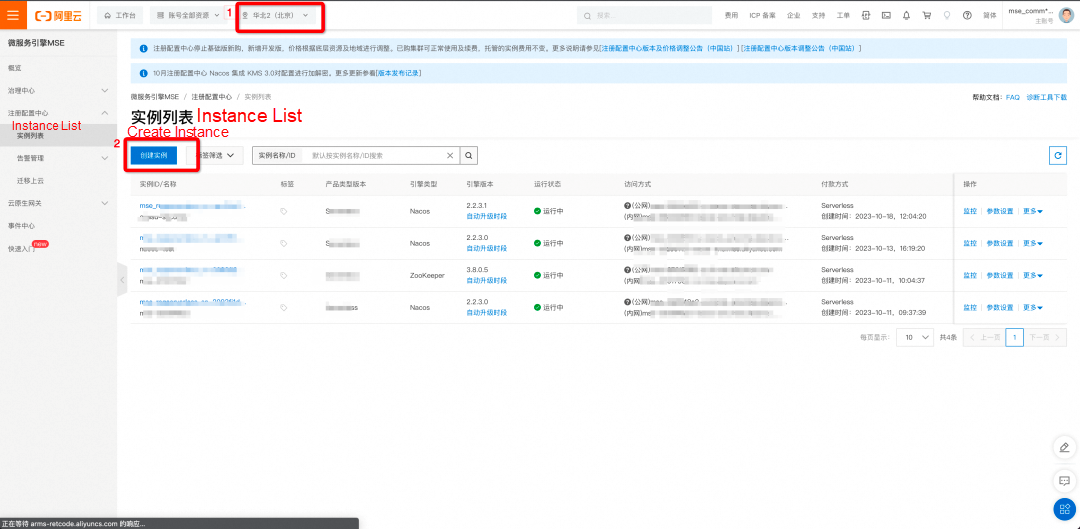
Log on to the MSE console. In the left-side navigation pane, choose Microservices Registry > Instances. Select a region and then click Create Instance. For more information about how to create a MSE Nacos instance, see Create a Nacos engine in the MSE documentation.
You can log on to the KMS console to view and activate KMS.
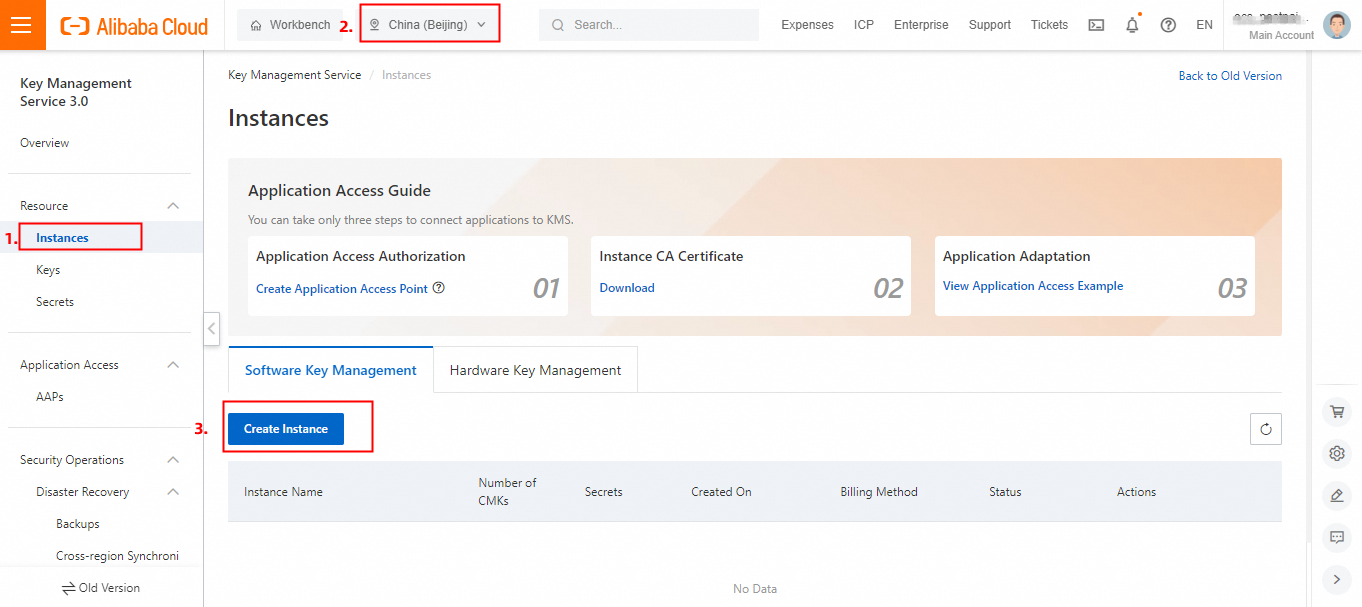
In the KMS console, click Instances in the left-side navigation pane, select a region (such as Beijing), and click Create Instance.
Note:
When you create a dedicated KMS instance, you must determine resource specifications for the instance. Note that only one key is required to use the configuration encryption and decryption capabilities of MSE Nacos. For more information about instance specifications, see Purchase and enable a KMS instance.
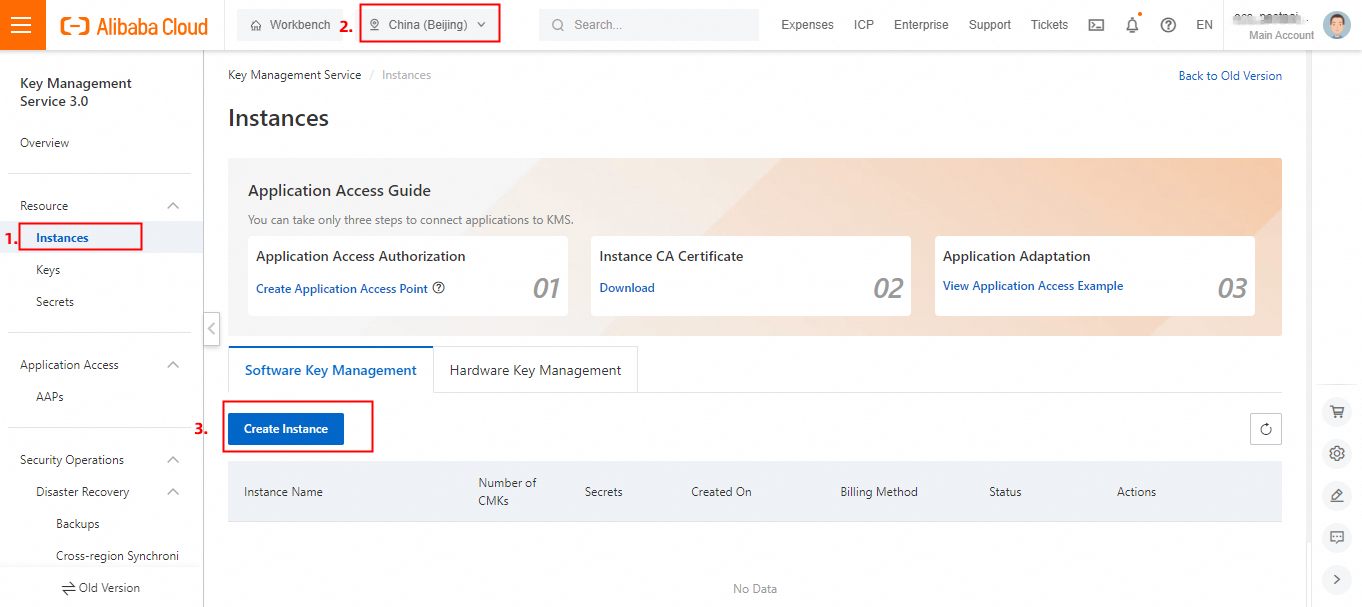
After the KMS instance is created, you also need to create a key. In the KMS console, click Keys in the left-side navigation pane, select a region (such as Beijing), and click Create Key.
For a key used for configuration encryption and decryption in MSE Nacos, you must determine two parameters:
You can set other key parameters based on your requirements. For more information about key management features, see Getting started with keys.
Log on to the MSE console, enable the configuration encryption feature for the MSE Nacos instance, and bind a KMS key to the MSE Nacos instance.
On the details page of the MSE Nacos instance, click Parameter Settings and set the parameter ConfigSecretEnabled to true.
Note: If it was set to false previously, resetting the value to true will cause the instance to restart.
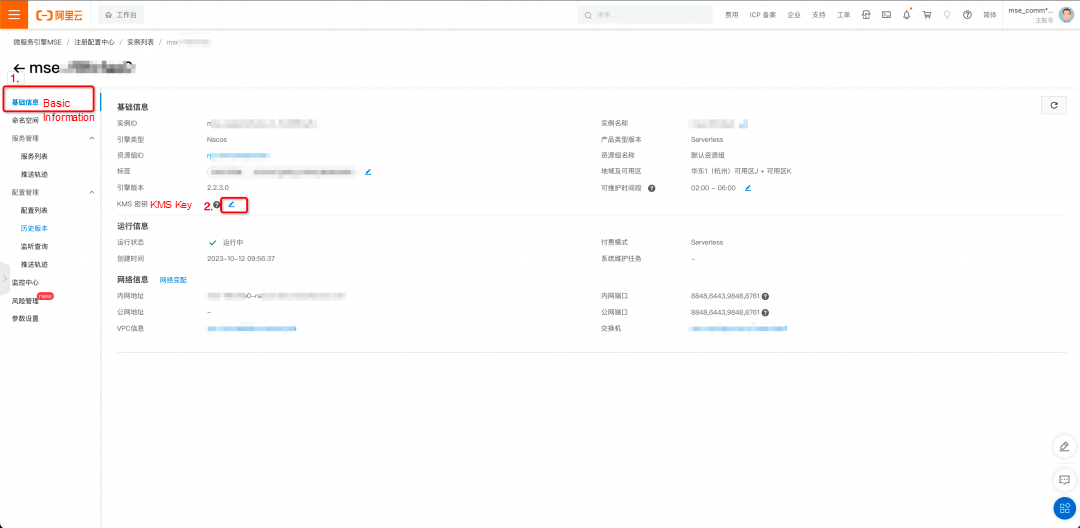
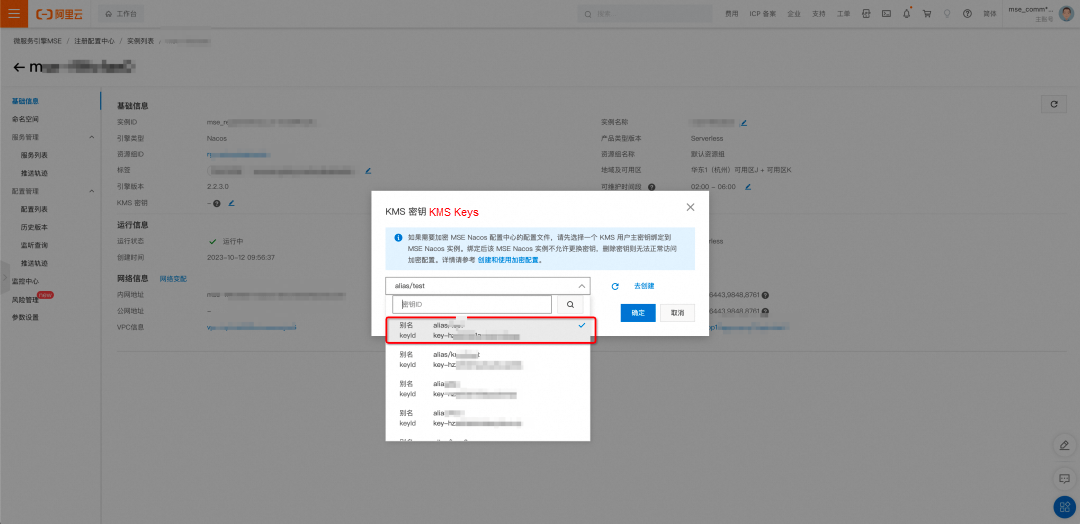
On the details page of the MSE Nacos instance, click Basic Information. In the basic information section, click the icon in the red box next to the KMS Key attribute to bind the KMS key created in Step 4 to this MSE Nacos instance. (The encrypted configurations edited in the MSE console will use this KMS key, so do not delete or disable it. Otherwise, the configuration encryption and decryption capabilities of MSE Nacos will become unavailable.)
After the binding is complete, you will see that the KMS key has been bound successfully in the basic information of the MSE Nacos instance. You can click the KeyId to go to the details page of the key in the KMS console.
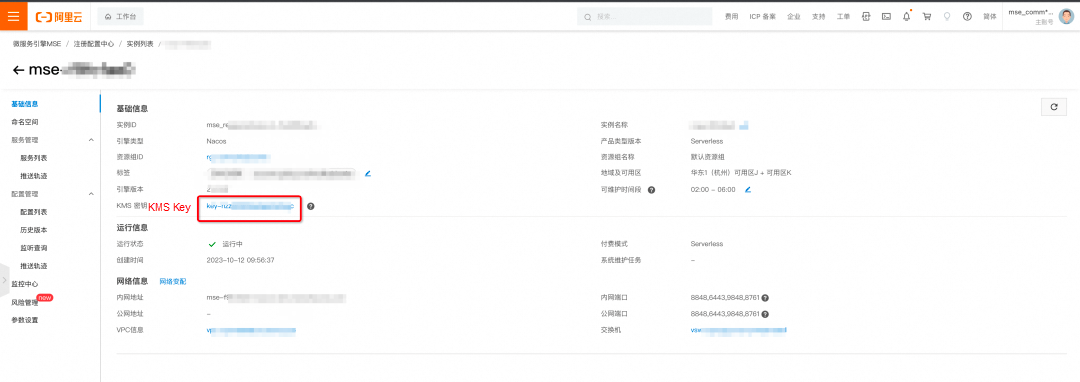
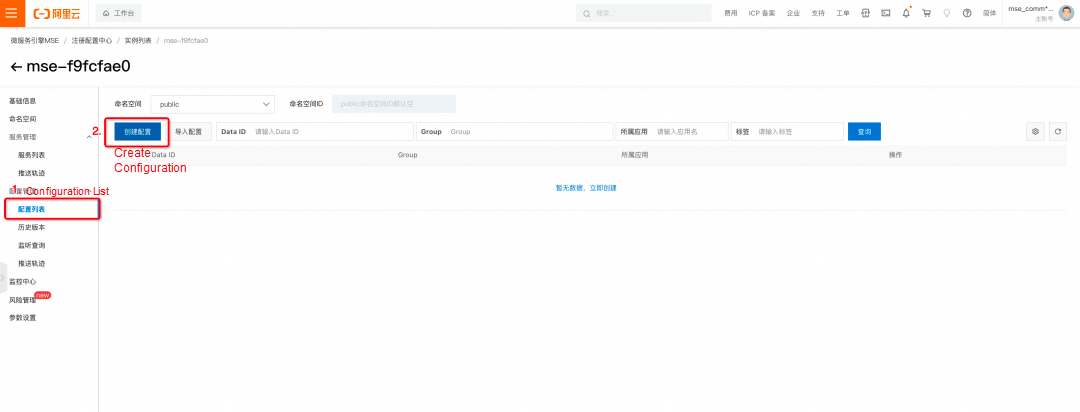
On the details page of the MSE Nacos instance, click Configuration List and then click Create Configuration.
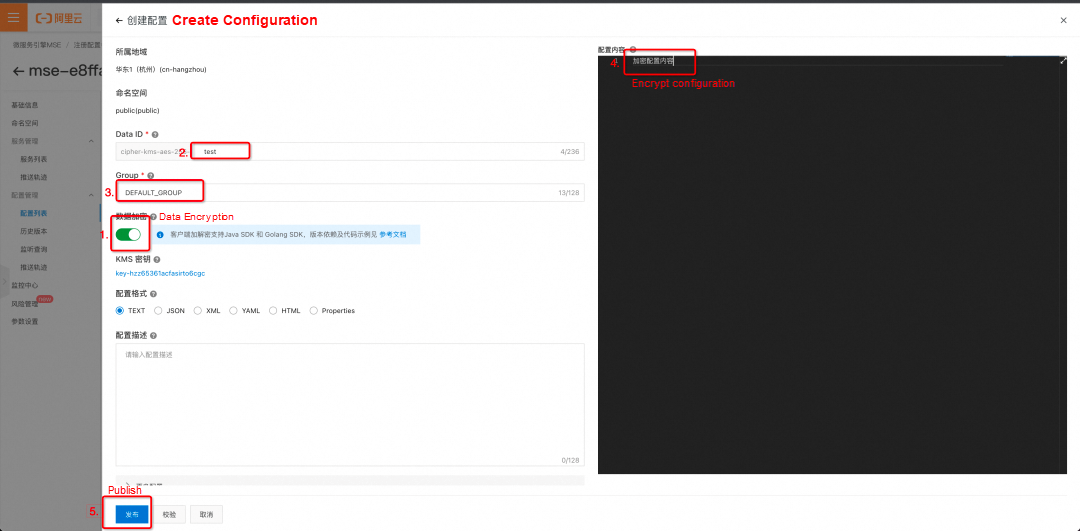
On the configuration editing page, turn on the Data Encryption switch first, as shown in Step 1 in the figure above. Then, edit other parameters as required, following Steps 2, 3, and 4 in the figure. Finally, click Release, as shown in Step 5. You can view the encrypted configuration you created in the MSE console.
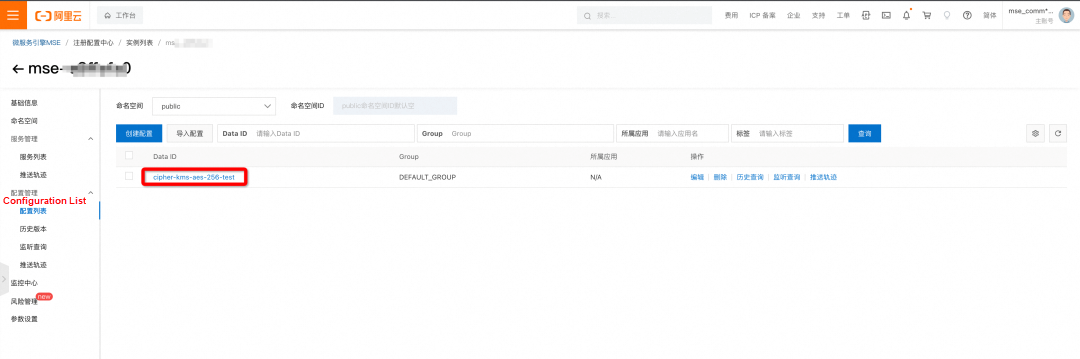
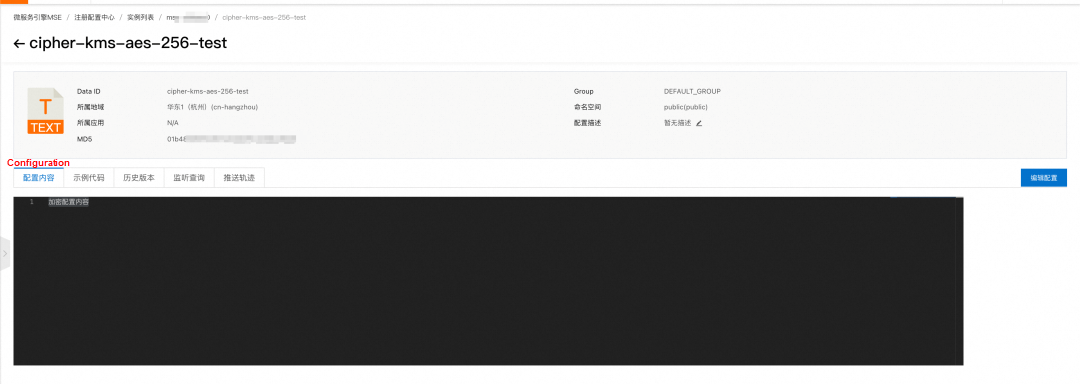
Note:
You can also use the Nacos client SDK to publish and obtain encrypted configurations. In this example, the SDK for Java is used.
To enable RAM authentication for the MSE Nacos instance, you need to click Parameter Settings in the left-side navigation pane on the details page of the instance and set the parameter ConfigAuthEnabled to true. The instance needs to be saved and restarted for the setting to take effect.
Log on to the KMS console, create an application access point (required) and obtain the instance CA certificate (optional) for the KMS instance to which the KMS key bound to the MSE Nacos instance belongs, as shown in the following figure.
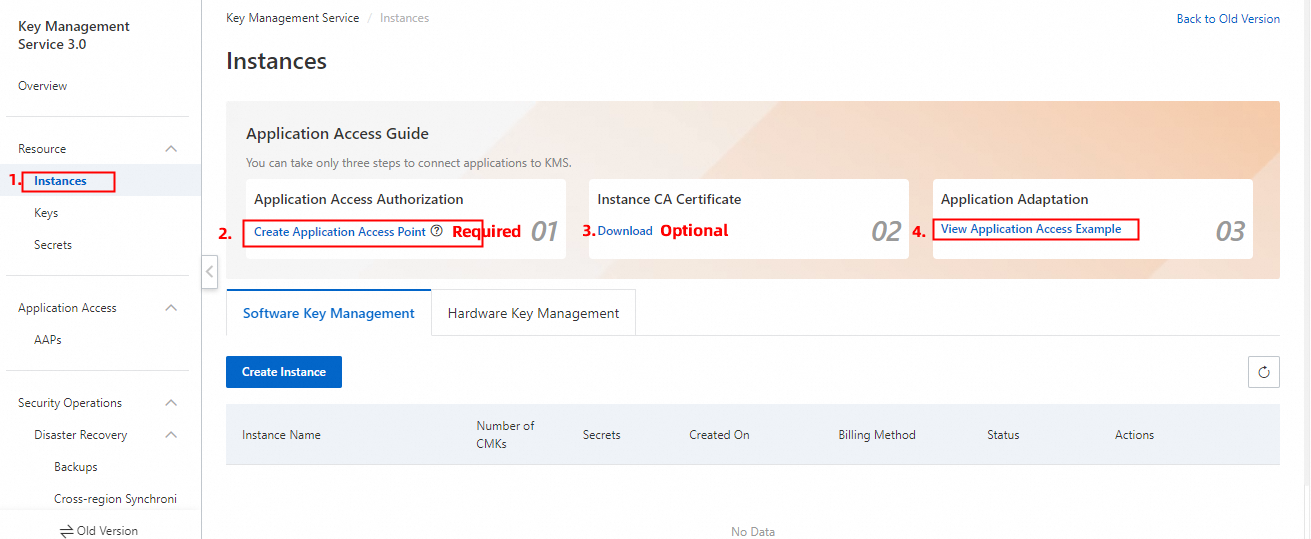
Click Create Application Access Point and specify the following information to create an application access point:
• Scope (KMS Instance): Select the instance ID corresponding to the KeyId bound to the MSE Nacos instance.
• Network Control Rules: Enter the CIDR block of the instance where the application service that uses configuration encryption and decryption is located.
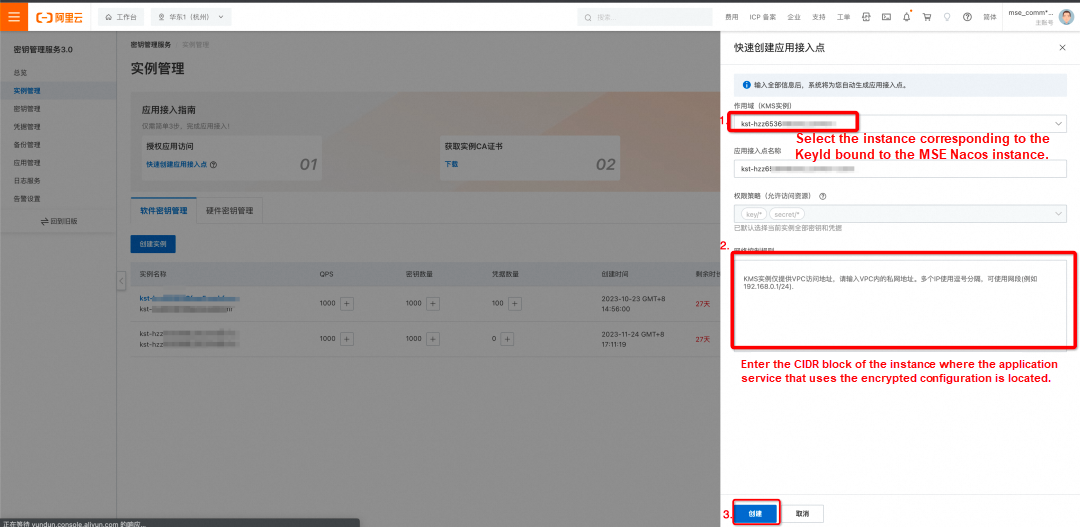
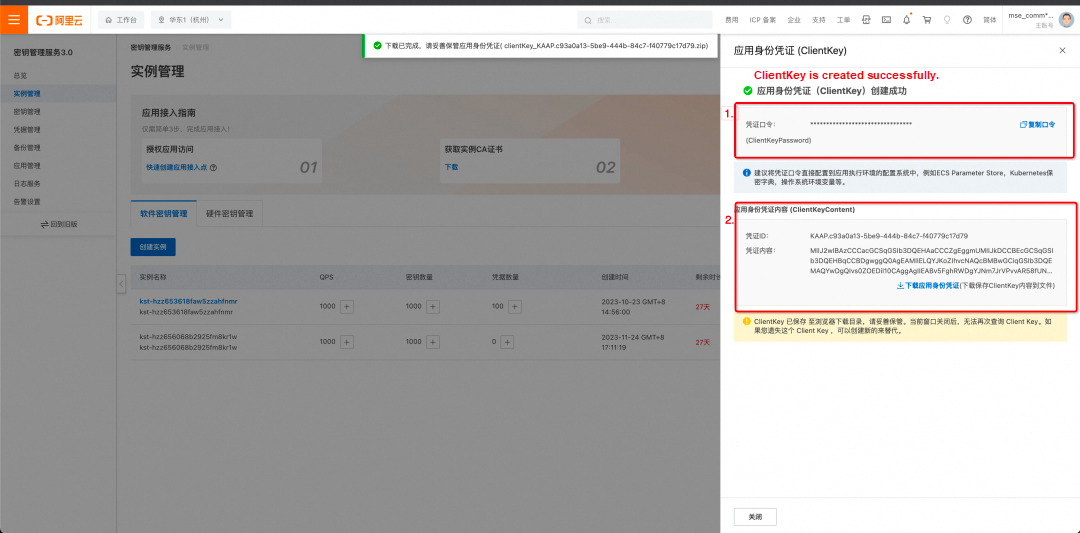
(Required) After creating the application access point, you will receive the following information. Please store this information securely, as it will be needed during the initialization of the Nacos client SDK and cannot be retrieved again from the KMS console.
(Optional) Obtain a CA certificate. If you wish to use TLS to strengthen the encryption and decryption communication link, you can obtain a CA certificate and add it to the initialization configurations of the Nacos client.
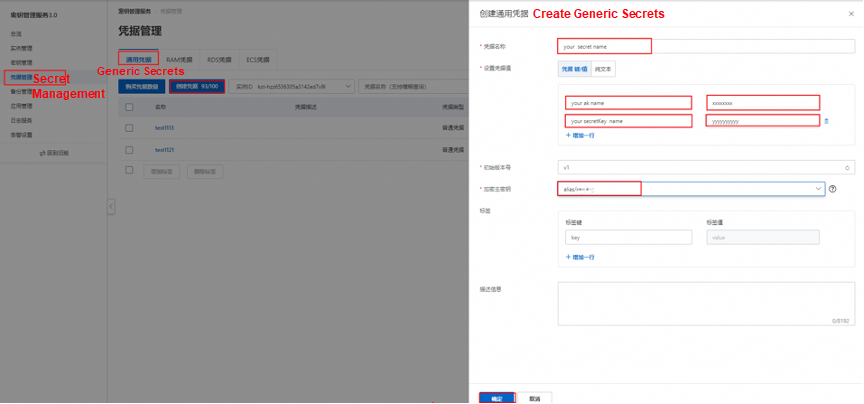
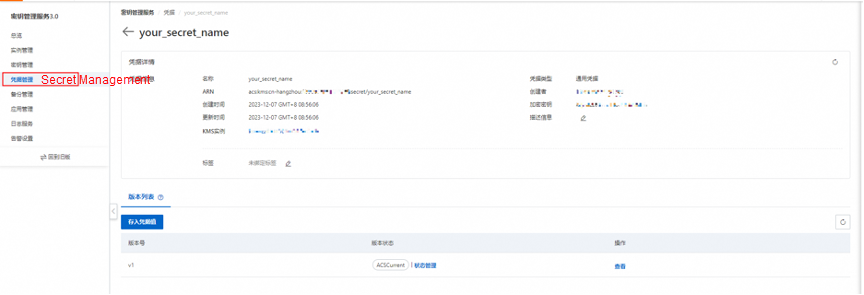
Note: Disabling the AccessKey ID will result in the inability to access MSE Nacos.
1. Add the following maven dependencies to your code:
com.alibaba.nacos
nacos-client
1.4.3
com.alibaba.nacos
nacos-client-mse-extension
1.0.3
com.aliyun
alibabacloud-secretsmanager-client
1.3.62. Initialize the Nacos client, then publish and obtain the encrypted configuration.
try {
try {
boolean getAliyunAKStatus = true;
int tryGetSecretInfoCount = 0;
// Initialize the secret client.
SecretCacheClient secretCacheClientclient = SecretCacheClientBuilder.newCacheClientBuilder(BaseSecretManagerClientBuilder.standard().withCustomConfigFile(#your custom kms scret config file pat#).build()).build();
// Use the secret client to retrieve secret information.
String accessKey = "";
String secretKey = "";
SecretInfo secretInfo=secretCacheClientclient.getSecretInfo("#your secret name#");
System.out.println("secretInfo====="+secretInfo.getSecretValue());
JSONObject jsonObj = null;
jsonObj=new JSONObject(secretInfo.getSecretValue());
accessKey=jsonObj.getString("your ak name");
secretKey=jsonObj.getString("your secretKey name");
while (getAliyunAKStatus){
try{
secretCacheClientclient = SecretCacheClientBuilder.newCacheClientBuilder(BaseSecretManagerClientBuilder.standard().withCustomConfigFile(#your custom kms scret config file pat#).build()).build();
secretInfo=secretCacheClientclient.getSecretInfo("acs/ram/user/wb-qc719783");
jsonObj=new JSONObject(secretInfo.getSecretValue());
accessKey=jsonObj.getString("AccessKeyId");
secretKey=jsonObj.getString("AccessKeySecret");
getAliyunAKStatus = false;
}catch (Exception e){
// If the retrieval fails, retry up to three times.
if (tryGetSecretInfoCount < 2){
tryGetSecretInfoCount ++;
Thread.sleep(2000);
continue;
}else{
e.printStackTrace();
}
}
}
Properties properties = new Properties();
properties.put("serverAddr", "mse-xxxxxx-p.nacos-ans.mse.aliyuncs.com");
properties.put("accessKey", accessKey);// The AccessKey ID is used for RAM authentication of MSE Nacos. If RAM authentication is not enabled, ignore this configuration.
properties.put("secretKey", secretKey);// The AccessKey secret is used for RAM authentication of MSE Nacos. If RAM authentication is not enabled, ignore this configuration.
properties.put("regionId", "cn-hangzhou");
properties.put("kms_region_id", "cn-hangzhou");
properties.put("kmsEndpoint", "kst-hzz6xxxr.cryptoservice.kms.aliyuncs.com");
properties.put("keyId", "alias/acs/mse");
properties.put("kmsVersion", "v3.0");
properties.put("kmsClientKeyContent", "clientKey_content");
// Configure one of the kmsClientKeyContent and kmsClientKeyFilePath parameters. The kmsClientKeyContent parameter takes precedence.
// properties.put("kmsClientKeyFilePath", "clientKey_hangzhou.json");
properties.put("kmsPasswordKey", "10xxxd1d");
properties.put("kmsCaFileContent", "ca_content");
// Configure one of the kmsCaFileContent and kmsCaFilePath parameters. The kmsCaFileContent parameter takes precedence.
// properties.put("kmsCaFilePath", "ca.pem");
ConfigService configService = NacosFactory.createConfigService(properties);
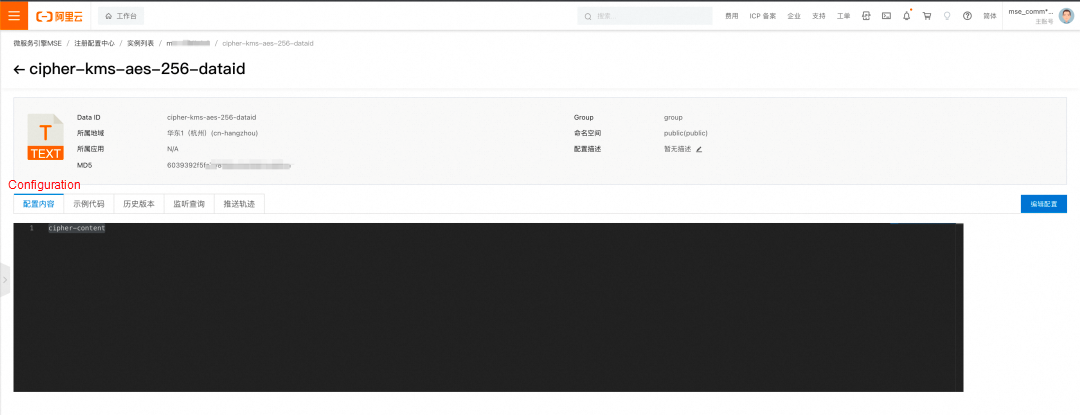
// Publish the encrypted configuration. (dataId is prefixed with "cipher-kms-aes-256-".)
configService.publishConfig("cipher-kms-aes-256-dataid", "group", "cipher-content"));
// Obtain the encrypted configuration.
System.out.println("content:::"+configService.getConfig("cipher-kms-aes-256-dataid", "group", 6000));
} catch (Exception e) {
e.printStackTrace();
}3. In the MSE console, you can view and edit the encrypted configuration that you published through the Nacos client SDK.
For more information, see KMS Instance SDK for Java and KMS Instance SDK for Go, as well as the topic on configuration encryption in the MSE documentation and topics related to encryption in the KMS documentation.
Disclaimer: The views expressed herein are for reference only and don't necessarily represent the official views of Alibaba Cloud.
Best Practice for Using KMS to Encrypt Sensitive Configurations in the Apollo Configuration Center
Level up Your Cloud Game With Alibaba Cloud's Double 11 Mega Sale

1,320 posts | 464 followers
FollowAlibaba Cloud Native Community - February 20, 2025
Alibaba Cloud Community - November 12, 2024
Alibaba Cloud Native Community - June 18, 2024
Alibaba Cloud Native Community - March 27, 2025
Alibaba Cloud Native Community - April 15, 2025
Alibaba Cloud Native Community - April 16, 2025

1,320 posts | 464 followers
Follow Cloud Hardware Security Module (HSM)
Cloud Hardware Security Module (HSM)
Industry-standard hardware security modules (HSMs) deployed on Alibaba Cloud.
Learn More Key Management Service
Key Management Service
Create, delete and manage encryption keys with Alibaba Cloud Key Management Service
Learn More Microservices Engine (MSE)
Microservices Engine (MSE)
MSE provides a fully managed registration and configuration center, and gateway and microservices governance capabilities.
Learn More Security Center
Security Center
A unified security management system that identifies, analyzes, and notifies you of security threats in real time
Learn MoreMore Posts by Alibaba Cloud Community