If IoT manufacturers cannot ensure absolute security of their devices, the potential impact on the digital economy will be devastating.
Since the fourth quarter of 2016, attacks with the IoT devices as targets or sources have been dominating the news headlines. Unsecured IoT devices became prime targets that can get quickly picked and used by attackers. It is also a well-known fact that these devices are often used as botnets to initiate large-scale DDoS attacks.
For example, the notorious Mirai botnet makes use of login vulnerabilities of unsecured IoT devices such as network cameras and home routers for attacks and has initiated the most significant DDoS attack known till date. In addition to initiation of DDoS attacks, attackers also use breached IoT devices to pry into data of other users, and ransom hijacked devices or used as an interface to penetrate into the network connected to the IoT devices.
This report provides some insights by comparing and analyzing the IoT-related attack data collected in 2015 and 2016.
The first conclusion that the data reveals is a rapid increase of specific attack vectors and sudden decrease of other attack vectors. In-depth analysis of the data shows that cybercriminals continue to act as highly focused opportunists. For example, attacks that get initiated using known vulnerabilities of home routers and network cameras increase significantly. The reason for the increase and persistence of such attacks is that manufacturers are not able to release patches or updates in time to fix known problems.
Some vulnerabilities are caused by defective firmware that may involve tens of thousands of devices produced by manufacturers using the same firmware. Currently, it is tough to create and deliver patches because most devices lack appropriate update mechanisms. Manual update (if possible) is equally challenging. However, it is rare to update devices that get deployed on a large scale using an automatic system.
Currently, criminals targeting IoT devices have successfully taken advantage of known vulnerabilities, such as those related to the default username, password, and static code backdoor. In addition to log in through these simple device entries, cybercriminals also use other quick and available methods (except for the default password) to penetrate into and take advantage of the IoT devices. For example, vulnerabilities that are caused by non-standard codes used to implement connection and communication with the IoT devices.
These problems are getting more serious. IoT devices that are extremely vulnerable have flooded the market. In addition to the high possibility of getting breached, millions of IoT devices get disabled or not updated, resulting in excessive help requests by consumers.
Challenges in the risk model presented by the IoT devices are another aspect of the impact. Even if cybercriminal can intrude your online smart brush toothbrush, they will not pay attention to the frequency at which you brush your teeth. However, if the toothbrush gets connected to the home network or even a mobile phone, and the mobile phone gets connected to the same home network, and then to your company network, the prediction might be that IoT device vulnerabilities of consumers will cause more far-reaching consequences.
More impacts are related to the commercial, industrial, and medical IoT devices. These devices are large in quantity and diversified in models, for example, the meters, pumps, instruments, industrial control systems, inventory management systems, and automatic production workshops. Particular attention is necessary for projects connected to key infrastructure or hyperlink environments, such as the networked buildings or smart cities.
If IoT manufacturers cannot ensure absolute security of their devices, the potential impact on the digital economy could be devastating. If you do not watch out for these problems, key services may get interrupted, and consequently, consumers may hesitate when purchasing IoT devices. As IoT devices with vulnerabilities become common, there might be a prediction that attacks targeted at IoT devices will continue and grow increasingly complicated, and more vulnerabilities on IoT communication and data collection link chain will get maliciously exploited.
Let's first take a look at the IoT-based IPS attack data and compare data collected in 2015 and 2016.
The following figures have common characteristics:
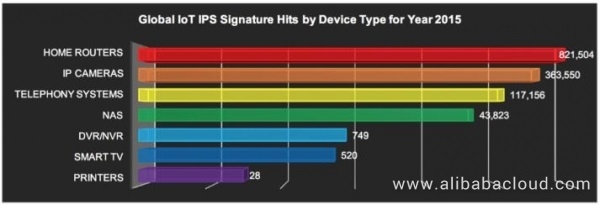
Figure 1. Attacked IoT devices worldwide in 2015 (analyzed by device type)
Figure 1 shows that in 2015, home routers caused most IoT IPS attacks (about 820,000 attacks), followed by attacks caused by network cameras, telecom systems, and network attached storages (NASs). A comparison shows that DVRs/NVRs, smart TVs, or printers cause fewer attacks than the above.
The data collected in 2015 is analyzed by region, including the Americas, Europe & Middle East & Africa (EMEA), and Asia Pacific.
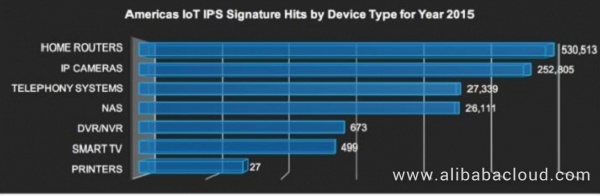
Figure 2. Attacked IoT devices in the America region in 2015 (analyzed by device type)
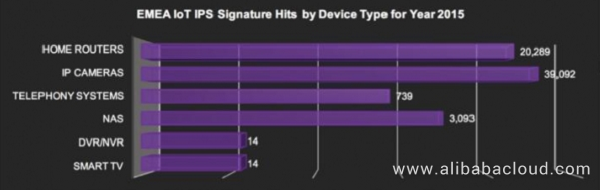
Figure 3. Attacked IoT devices in the Europe & Middle East & Africa region in 2015 (analyzed by device type)
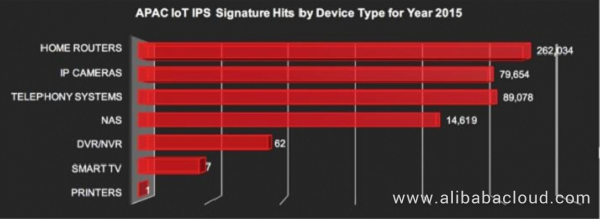
Figure 4. Attacked IoT devices in the Asia Pacific region in 2015 (analyzed by device type)
Figure 5 shows the same IoT devices used to collect IPS attack data in 2016.
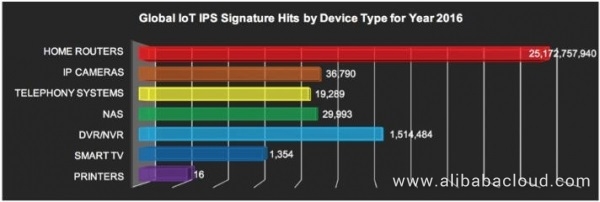
Figure 5. Attacked IoT devices worldwide in 2016 (analyzed by device type)
As shown in Figure 5, home routers still cause the majority of IPS attacks in 2016. Also, the number of attacks increase exponentially (more than 3000th power) to more than 25 billion. Figure 5 also shows other differences. For example, the number of attacks targeted at DVRs/NVRs increases by more than 2000 folds, and the number of attacks aimed at smart TVs has almost tripled. Interestingly, the number of attacks targeted at NASs, network cameras, telecom systems, and printers decreases significantly, and the multiplication factor ranges from -1.5 to about -10 power.
The data collected in 2016 is analyzed by region, including the Americas, Europe & Middle East & Africa (EMEA), and Asia Pacific.
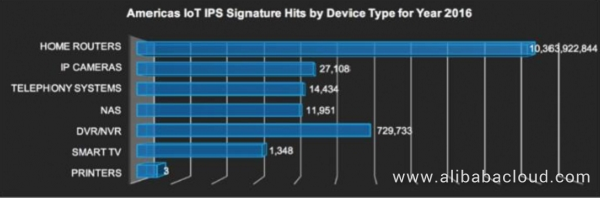
Figure 6. Attacked IoT devices in the America region in 2016 (analyzed by device type)
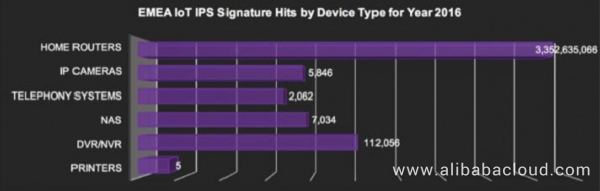
Figure 7. Attacked IoT devices in the Europe & Middle East & Africa region in 2016 (analyzed by device type)
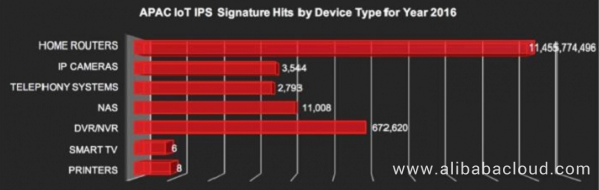
Figure 8. Attacked IoT devices in the Asia Pacific region in 2016 (analyzed by device type)
The number of IoT device attacks in 2016 increase exponentially as compared with that in 2015.
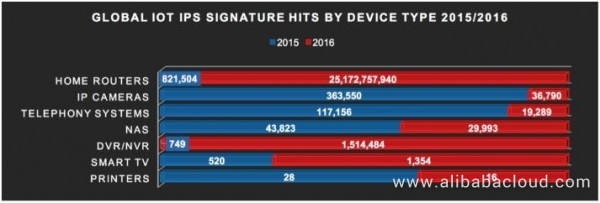
Figure 9. Comparison between attacked IoT devices worldwide in 2015 and 2016 (analyzed by device type)
Note that the preceding figures do not include the notorious Mirai botnet attack initiated in September 2016. They only track the increase or decrease in the normal threat traffic of IoT devices.
In this article, we had an overview of the vulnerabilities that are prevalent in IoT devices and how attackers are taking advantage of these devices. We also discussed the major worldwide trends in the attacks on IoT devices. The number of attacks per year is increasing.
We need significant measures and updates to keep a track on these attacks so that we can come up to a solution. We perceive the introduction of blockchain technology as a revolution for IoT. However, it is still at an initial stage.
To read more about IoT solutions, visit www.alibabacloud.com/solutions/IoT.
Implementing a Modern WordPress Workflow on Alibaba Cloud - Part 4
Alibaba Deploys Alibaba Open Channel SSD for Next Generation Data Centers

2,599 posts | 764 followers
FollowAlibaba Clouder - April 26, 2018
Alibaba Cloud Community - January 6, 2022
Alibaba Clouder - July 27, 2018
Alibaba Cloud Community - January 31, 2022
Alibaba Clouder - June 11, 2019
Alibaba Cloud New Products - June 2, 2020

2,599 posts | 764 followers
Follow IoT Platform
IoT Platform
Provides secure and reliable communication between devices and the IoT Platform which allows you to manage a large number of devices on a single IoT Platform.
Learn More IoT Solution
IoT Solution
A cloud solution for smart technology providers to quickly build stable, cost-efficient, and reliable ubiquitous platforms
Learn More Anti-DDoS
Anti-DDoS
A comprehensive DDoS protection for enterprise to intelligently defend sophisticated DDoS attacks, reduce business loss risks, and mitigate potential security threats.
Learn More Anti DDoS Basic
Anti DDoS Basic
A cloud-based security service that protects your data and application from DDoS attacks
Learn MoreMore Posts by Alibaba Clouder
5599644100050691 December 7, 2018 at 1:36 pm
You might be hacked, someone you know, someone you are close to, maybe your spouse has all your devices bugged, or that workmate that seems to be one step ahead of you might be using that spyware trojan on you. its possible you don't even know this because there a spyware that would just sync with your phone even though you might be losing battery, files, speed and data on your device. Be sure today by contacting rootgatehacks At tutanota dot com by mail..They also provide counter measures