By GXIC
At a recent Central Political Bureau Standing Committee meeting, the government proposed to accelerate the development and construction of 5G, data centers, artificial intelligence (AI), Internet of Things (IoT), and other new infrastructures. Eight provinces or direct-controlled municipalities, including Beijing, Shanghai, and Jiangsu, announced nearly RMB 34 trillion in new infrastructure investments. The state's high level of focus and support in this area has become the core driver of economic transformations, upgrades, and future economic growth.
As the launch pad of China's rapid and long-term development in science, technology, and economy, new infrastructure is a key component of the initiative to "rejuvenate the country through science and technology." The new infrastructure includes the seven major fields of 5G base station construction, charging stations for new-energy vehicles, big data centers, AI, industrial Internet, ultra-high voltage (UHV), and intercity and urban rail transportation. So far, IoT technology has been deeply integrated into each aspect of the new infrastructure construction. As the informational infrastructure of the future continues to develop, IoT technology will become ubiquitous.

According to statistics from the Global System for Mobile Communications Association (GSMA), the number of IoT devices around the world increased rapidly from 2010 to 2018, at a compound growth rate of nearly 21%. In 2018, the number of connected IoT devices in the world reached 9.1 billion. According to the GSMA's forecasts, the number of global IoT devices (including cellular and non-cellular devices) will reach 25.2 billion in 2025. By the end of 2019, China became the world's largest IoT market. Of the 1.5 billion devices connected to cellular networks worldwide, 960 million of them (64%) came from China.
Given the development of new infrastructure in China, the rapid development of the IoT industry has found a golden opportunity for further boosting. As the number of IoT devices increases with each passing day, security has become a major and urgent concern. The large device base, widespread fragmentation, and vulnerabilities of hardware and software make the cost of attacks on IoT devices extremely low. As a result, attacks are increasing in scale and attack methods are developing rapidly. Security threats have become the norm in the IoT field. In 2018, global security spending reached USD 96 billion, up 8% from USD 89 billion in 2017. The number of IoT security incidents in China was expected to rise from 7,648 in 2018 to 56,121 in 2019, with an increase of nearly 600% over the previous year.
In this circumstance, the following issues must be considered in the planning and construction of the IoT during new infrastructure construction and a part of subsequent operations. How to securely connect and manage a large number of devices, how to break down data silos and make full use of data resources and terminal resources, how to ensure the security of the IoT, how to ensure the reliability of intelligent terminals, and how to identify and deal with malicious attacks? Without resolving these issues, it will be difficult to maximize the effectiveness of the new infrastructure.
The Cyber Security Law of the People's Republic of China, Cryptography Law of the People's Republic of China, and Classified Protection of Cybersecurity 2.0, a series of IoT security policies and regulations have been published over the past two years. These policies and regulations extend from traditional network security to IoT security, showing China's determination to actively promote IoT technology to comprehensively improve security capabilities.

Driven by the new infrastructure, the IoT security industry will support the vigorous development of China's digital industry. For enterprises, the vigorous promotion of IoT security centered on controllable technology and incorporating information security technology is the best and fastest way to advance the construction of new infrastructure.
In March 2018, Alibaba entered the IoT market, making IoT the fifth major focus of Alibaba Group after e-commerce, finance, logistics, and cloud computing.
Alibaba Cloud IoT aims to be a builder of the IoT infrastructure and plans to connect 10 billion devices within 5 years. To achieve this, we require the support of powerful security capabilities. Alibaba Cloud Link Security, our IoT security platform, provides high security for hundreds of millions of connections and millions of concurrent connections. This platform constantly promotes the secure, mature, and commercial development of IoT technology, and consolidates the security foundation for new infrastructure.
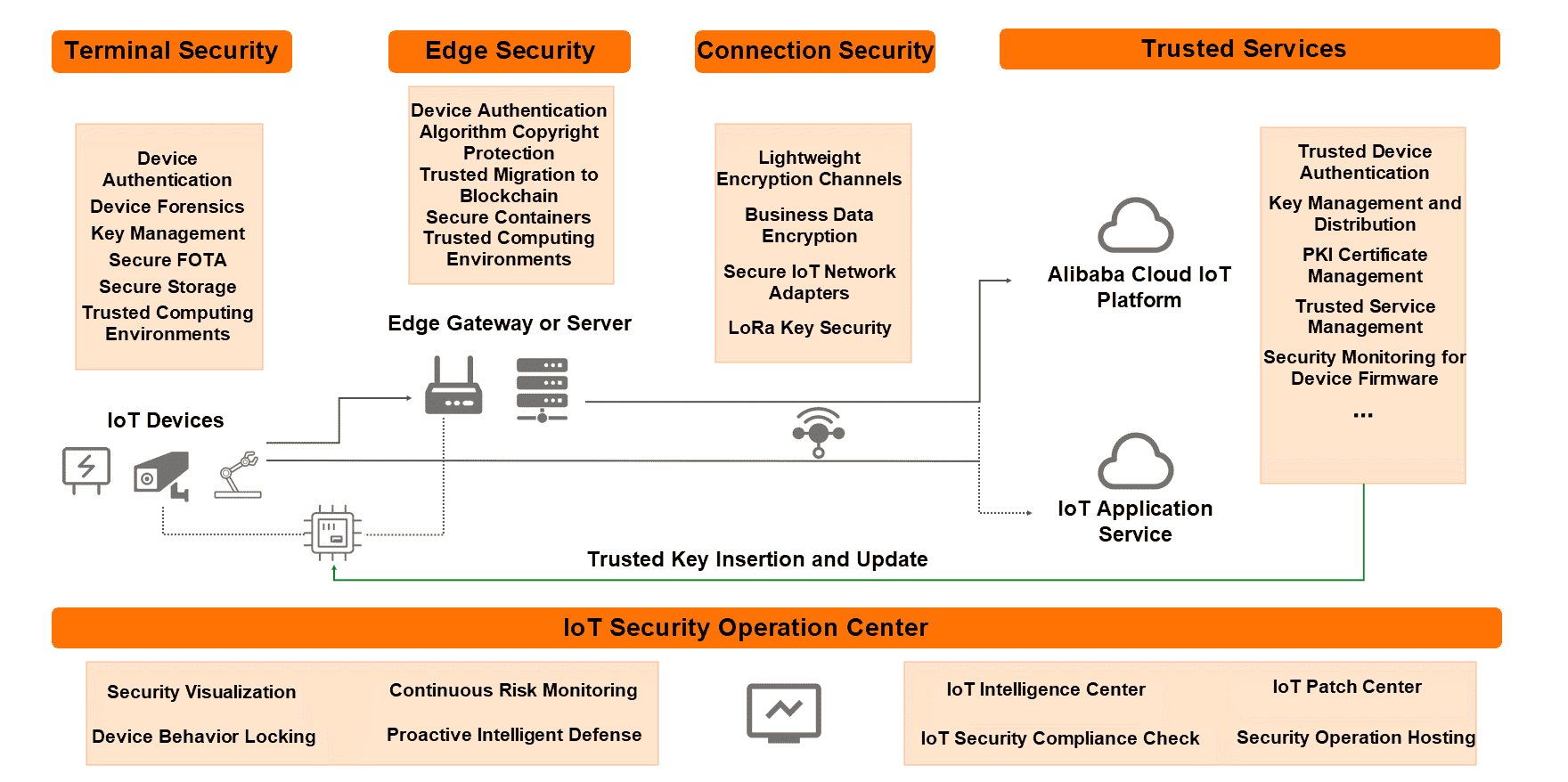
Since its emergence, the IoT industry has suffered from four main security pain points:
1) High security access requirements due to dispersed distribution
2) Lack of overall security solutions due to long links
3) Difficult security operations due to a shortage of specialists
4) Inconsistent security standards due to multiple scenarios
To address these pain points, Alibaba Cloud IoT has built the powerful Link Security platform. This platform implants security throughout the entire lifecycle of IoT device development, testing, production, access, and operation by providing a series of lightweight and adaptive security products and solutions. The platform focuses on device security, edge security, and access security and moves the acquisition of trusted data to the cloud. It uses blockchain technology to ensure the trusted transfer of data.
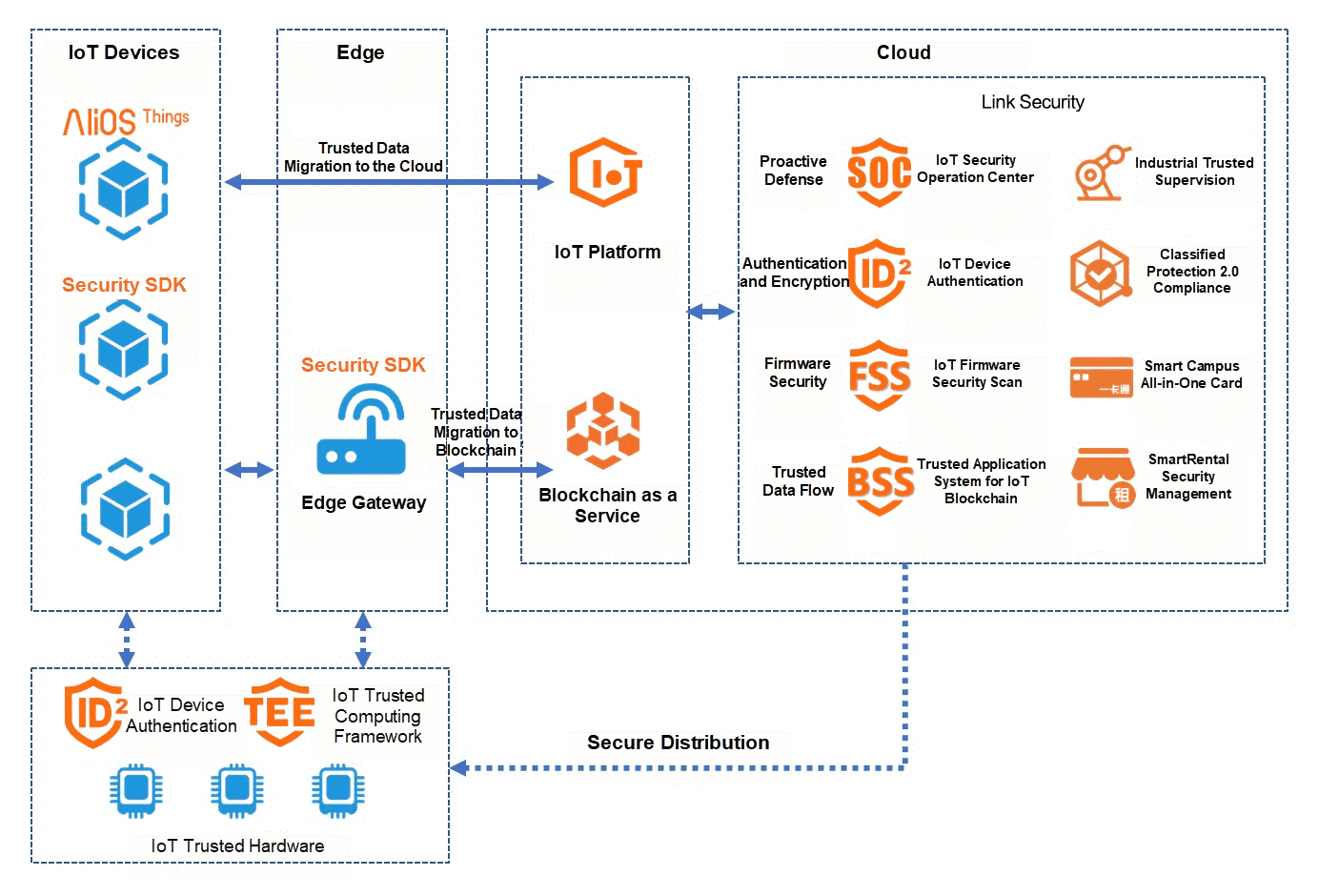
When you connect devices to the platform, Link ID² device authentication is one of the taken core security measures. ID² device identity information is globally unique and cannot be tampered with or counterfeited. Moreover, this information is built-in secure and trusted carriers (such as security chips) to further strengthen the protection of identity information. ID² provides a cloud-based root of trust for IoT devices. You can build trusted services for upper-layer businesses based on the trusted root. This ensures the legitimacy of IoT devices and data security from the source. To date, we have performed over 1.1 billion ID² authentications, with a peak of 8,000 per second. ID² provides a variety of identity key algorithms, including cryptographic algorithms recommended by Chinese authorities. In 2019, the security of commercial cryptography applications was assessed and basic compliance was achieved.
Link TEE is an important security assurance solution that the platform deploys on devices. Based on hardware isolation security technology, it provides a secure computing environment for private data and sensitive code and supports the extended development of secure applications. Link TEE is the cornerstone of trusted IoT. Link TEE is also the only product in the world that has received the GlobalPlatform TEE full configuration security certification from the International Organization for Standardization.
Link SOC is the core component of the platform that links devices and systems. It provides a one-stop and panoramic visualization of device security management. It also dynamically monitors the security implementation status and operational risk profile of connected IoT devices. It helps enterprises identify and eliminate potential security threats in the IoT system. This greatly reduces the period from incident occurrence to exception detection to response and disposal. Overall, this process helps contain the spread of risks. It also controls the impact scope of risk events on the business to provide a stable assurance of business system availability. SOC also provides hosted security operations as a value-added service to reduce enterprises' investment in security personnel.
The platform also combines IoT security with blockchain technology to upgrade IoT devices and data from security to trust. This allows IoT technologies to provide innovative solutions for manufacturing supervision, supply chain management, remote supervision, the removal of counterfeit goods from circulation, and quality tracing. It accurately digitizes the physical world and provides practical security for IoT data through the application of secure and reliable IoT technology, empowering the industry.
So far, the platform is used in many fields like single product, industry, real estate, campuses, and cities. It links entities in the ecosystem such as chips, modules, equipment, software services, communication operations, and testing and certification. It also integrates the sales resources of Taobao, Tmall, and the Alibaba Cloud IoT marketplace to build an ecosystem feedback loop. To date, the platform has integrated over 70 types of security hardware, cooperated with more than 100 manufacturers, and shipped more than 40 million security terminals.
In response to the national call, Alibaba Cloud passed the IoT security assessment based on Classified Protection 2.0 (Level 3), becoming the first IoT security service platform in China to do so. At the same time, the platform provides one-stop classified protection solutions to help enterprises quickly achieve classified protection compliance. From this, you can see that Alibaba Cloud is confident and determined to succeed in the field of IoT security.
We are currently sinking our cloud capabilities to the infrastructure. In this way, we will provide comprehensive security protection capabilities and assist in the secure construction of new infrastructure while enabling the intelligence of everything.
New Release: Alibaba Cloud DAS – Reduce Database Management Costs by 90%
Ant Financial's ApsaraDB for OceanBase Now Available on Alibaba Cloud

31 posts | 5 followers
FollowAlibaba Clouder - July 23, 2021
Alibaba Developer - April 18, 2022
Alibaba Clouder - October 15, 2018
Alibaba Clouder - September 30, 2019
Nick Patrocky - February 17, 2024
Alibaba Cloud Community - August 26, 2022

31 posts | 5 followers
Follow Offline Visual Intelligence Software Packages
Offline Visual Intelligence Software Packages
Offline SDKs for visual production, such as image segmentation, video segmentation, and character recognition, based on deep learning technologies developed by Alibaba Cloud.
Learn More Security Solution
Security Solution
Alibaba Cloud is committed to safeguarding the cloud security for every business.
Learn More CloudBox
CloudBox
Fully managed, locally deployed Alibaba Cloud infrastructure and services with consistent user experience and management APIs with Alibaba Cloud public cloud.
Learn More Security Overview
Security Overview
Simple, secure, and intelligent services.
Learn MoreMore Posts by Alibaba Cloud New Products