By Raymond Huang, Senior Security Engineer
Data security and user privacy are among the top concerns for cloud customers, and is the focal point of research at Alibaba Cloud. Alibaba Cloud strives to provide customers with consistent, reliable, secure, and regulation-compliant cloud computing services, helping customers ensure the availability, confidentiality, and integrity of their systems and data. In this article, we will take a closer look at Alibaba Cloud's data security architecture, and explore how we provide a compliant data protection solution in a trustworthy and controllable cloud security environment.
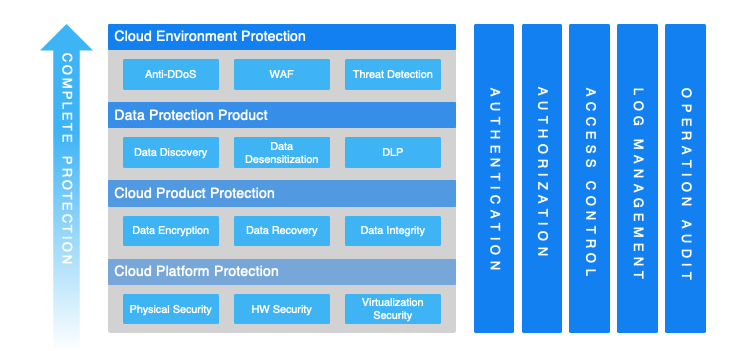
Figure 1. Cloud data security architectural solution
The overall architecture of cloud data security aims to provide users with cloud data protection from the underlying cloud platform to the upper-layer cloud environment. As shown in the diagram above, the architecture includes security modules of various layers, and the users can build trustworthy data security solutions on the cloud layer by layer, similar to building a house. In addition to the security modules of all layers, common functions such as authentication, authorization, access control, and log auditing are also necessary for a comprehensive cloud data security solution. These functions provide users with controllable and compliant cloud data security solutions.
In general, cloud data security solutions aim to be trustworthy, controllable, and compliant. In other words, only by providing a compliant data protection solution in a trustworthy and controllable cloud security environment can one create a top-level data security solution for cloud users.
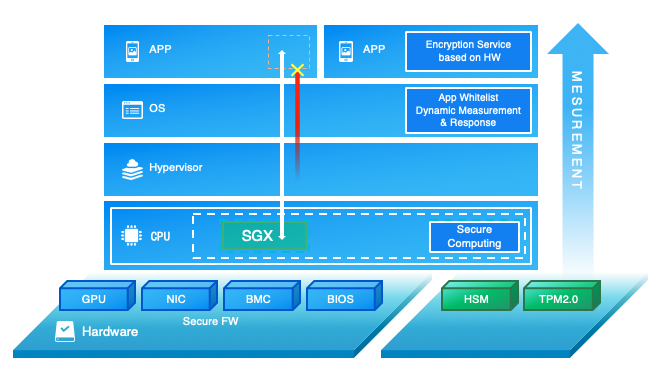
Figure 2. Alibaba Cloud infrastructure security
Alibaba Cloud provides users with high-security infrastructure capabilities by default, so that users can safely store and use data on a trusted cloud platform. It is worth noting that Alibaba Cloud infrastructure secures and scans hardware and firmware, provides a TPM2.0-compliant computing environment, and offers hardware encryption (HSM) and chip-level (SGX) encryption computing capabilities at the cloud platform layer.
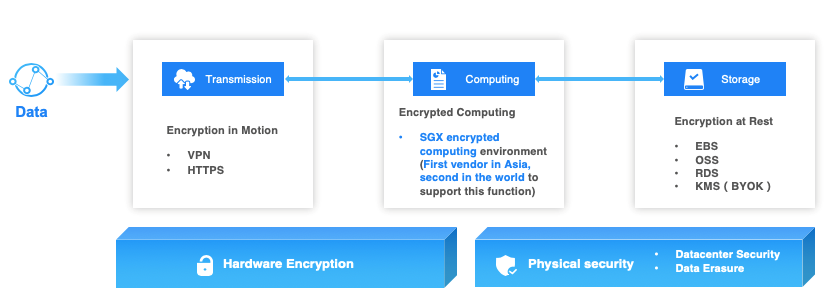 Figure 3. End-to-end data encryption
Figure 3. End-to-end data encryption
At the cloud product layer, data security is mainly embodied in products’ security features, such as end-to-end data encryption, backup, and verification of cloud products. Among these, end-to-end data encryption is a best practice in the field of data encryption protection.
End-to-end data encryption provides advanced data encryption capabilities on transmission links (i.e. data-in-motion), compute nodes (i.e. data-in-use), and storage nodes (i.e. data-at-rest). Specifically, transmission encryption mainly relies on SSL/TLS encryption and provides AES256 encryption protection.
For data encryption in compute nodes, Alibaba Cloud provides a chip-level SGX encryption computing environment, and is looking for more ways to encrypt and protect the runtime memory on compute nodes in the future.
For encryption in storage nodes, Alibaba Cloud not only provides AES256 data-at-rest encryption capabilities in various products, but also provides the Bring Your Own Key (BYOK) function through Key Management Service (KMS). Together with KMS, Alibaba Cloud can provide users with end-to-end data encryption protection.

Figure 4. Data encryption process
In general, a data encryption process calculates the cipher text out of plain text data by using internationally recognized/standardized encryption algorithms. In the encryption process, the proper security protection and management of keys play a vital role. That is to say, if one maintains control over the key, one maintains the control of the overall encryption operations.
One of Alibaba Cloud's most important principles is that user data belongs to users, and the cloud platform cannot use the data for other purposes without proper authorization. Therefore, the Bring Your Own Key (BYOK) function is an important technique which Alibaba Cloud adopts to protect user data privacy and further control how the encrypted data would be used.
Namely, a user's own master key (i.e. CMK) is a user resource, and anyone who wants to use such a resource must be authorized by the owner (such as Alibaba Cloud's RAM). This gives the user full autonomy and control over the use of the encrypted data. In addition, any attempt to access user resources (such as CMKs) will be fully recorded by log auditing (such as Alibaba Cloud's ActionTrail). Therefore, the use of cloud data remains completely transparent even after encryption.
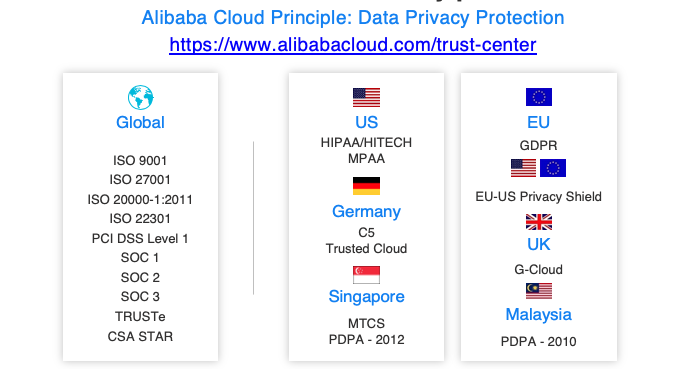
Figure 5. Alibaba Cloud security compliance certifications
In addition to providing trustworthy and controllable data protection techniques, Alibaba Cloud also provides various authoritative compliance certifications. A compliance certification is a third party's endorsement of Alibaba Cloud's data security implementation and technical capabilities. In particular, globally recognized compliance certifications are crucial for Alibaba Cloud's success in various markets around the world.
Alibaba Cloud's security mission is to maximize cloud security, provide stronger security solutions, build a solid security foundation for users, and liberate users from cloud security and infrastructures so that they focus on their own business needs. This is especially true at the data protection domain, where it is necessary to provide users with the most powerful and comprehensive data security protection techniques and capabilities. Alibaba Cloud's goal is to allow users to migrate to the cloud without fear of data security issues, and to allow users view cloud migration as a way to strengthen security.

2,593 posts | 793 followers
Follow5544031433091282 - October 23, 2023
Alibaba Clouder - August 21, 2020
ray - April 25, 2024
Alibaba Cloud Indonesia - September 13, 2023
Alibaba Clouder - November 2, 2018
Alibaba Clouder - July 10, 2019

2,593 posts | 793 followers
Follow Key Management Service
Key Management Service
Create, delete and manage encryption keys with Alibaba Cloud Key Management Service
Learn More OSS(Object Storage Service)
OSS(Object Storage Service)
An encrypted and secure cloud storage service which stores, processes and accesses massive amounts of data from anywhere in the world
Learn More ECS(Elastic Compute Service)
ECS(Elastic Compute Service)
Elastic and secure virtual cloud servers to cater all your cloud hosting needs.
Learn MoreMore Posts by Alibaba Clouder