A few months back, Alibaba Cloud security team observed a new trend of DDoS attack where common, everyday mobile apps are becoming DDoS attack tools, and the traditional mitigation policies are not effective anymore for the attacks launched by mobile botnets.
This article further analyzes characteristic features of the DDoS attack mitigated by the intelligent protection engine of Alibaba Cloud Anti-DDoS Service.
The tracing analysis show that these DDoS attacks were caused because by a large number of users installing malicious apps that were disguised as normal applications on their mobile phones. These malicious apps will initiate attacks to target websites dynamically by the attacker. More than 500,000 mobile devices were seen using this DDoS attack tools in the past few months, giving a single attack the same severity as a PC botnet DDoS attack. It is clear malicious apps disguised as common applications have turned a massive number of mobile devices into a new generation of botnets. This pattern indicates that hackers are upgrading their techniques to deliver more severe impact.
1. Evenly distributed mobile device operating system affected
About 40% are iOS system devices and 60% are Android system devices.
2. Huge attack with a large number of mobile devices
In a single attack, the peak number of requests per second (QPS) can reach millions, which are initiated through more than 500,000 mobile devices, with very few source IP addresses repetition in each attack instance.
3. Geographically distributed attack source IP addresses
Attack source IP addresses came from nearly 40 different ISPs in more than 160 countries around the world.
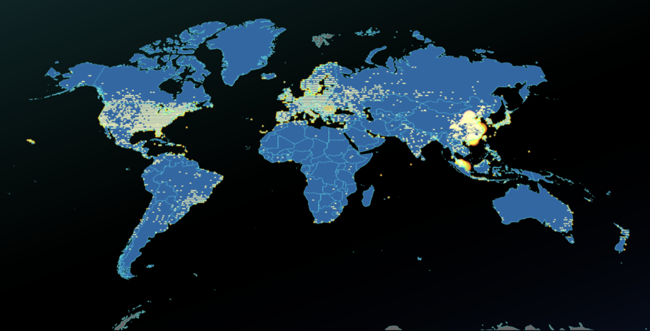
Distribution of attack source IP addresses
4. Cellular base stations contributing most attack source IP addresses
Nearly half of the attack source IP addresses originated from large cellular base station gateway IP addresses, meaning that the same source IP address carries both attack traffic and a large amount of normal user traffic.
5. Irregular attack scheduling
Due to the way mobile phones constantly change connection to networks and how apps start and stop, we have observed an unusually high number of attack source IP addresses. More than half of the attack source IP addresses were not attack initiations, the attack duration of each source IP address varies, and the request frequency of a single attack source IP address is not high.
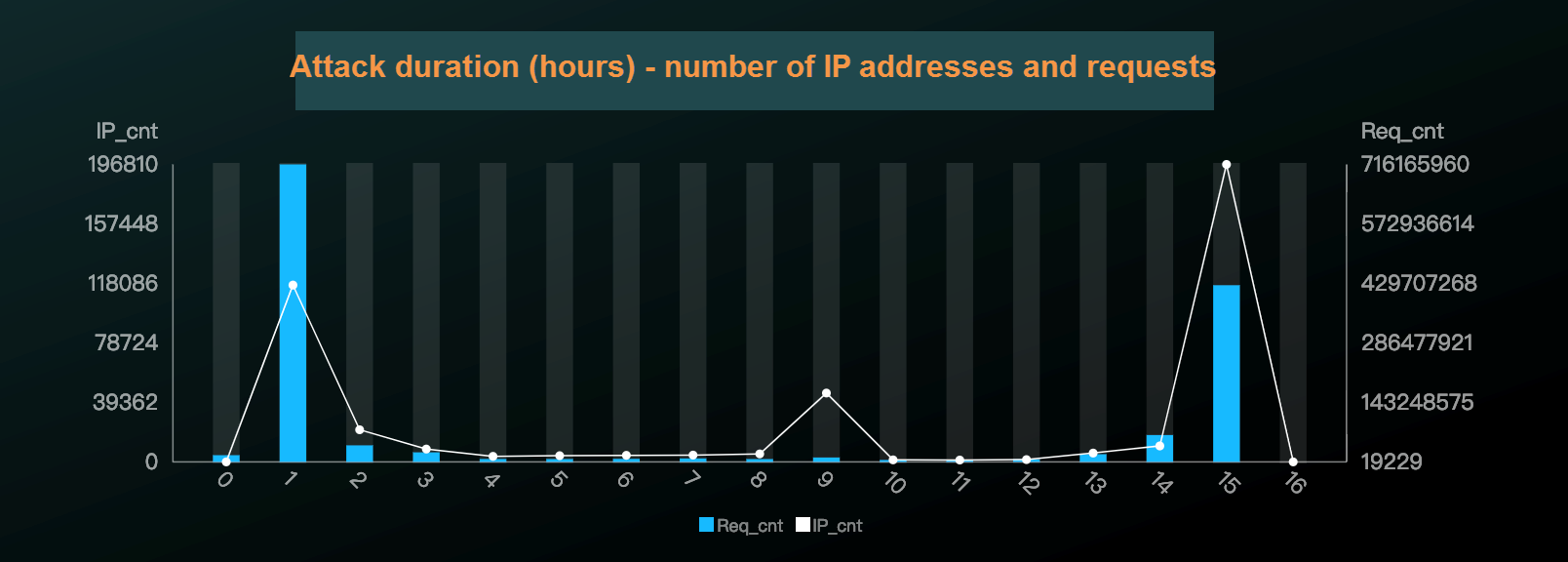
Number of IP addresses with different attack durations and the number of their requests in an attack
The combination of rate-limiting and blacklisting was an effective mitigation policy in the era of PC botnets. However, mobile devices are far more uqibuitous than PCs, resulting in a large quantity of attacks initiated by malicious apps disguising as normal applications, even though the apps may themselves are obscure. Even if the request frequency of a single device is low, the aggregated number of requests from all devices can overwhelm the target site, making it easy for a hacker to attack the target site without triggering any rate limiting policies.
In addition, majority of the attack sources are large cellular base station gateway IP addresses rendering traditional defense policies such as blacklisting useless, as blacklisting a cellular base station will result in a large number of normal users unable to access the cellular services. New mobile devices of the botnet were constantly added in the attack process, so a blacklist mechanism may not be enough to effectively block the attack. The once-effective mitigation policies are now ineffective in the face of new attacks.
1. Hackers embed WebView into an app, which will request the central control link after starting. The page that the link directs to is embedded and loaded with three JS files, which dynamically obtain the JSON instructions in Asynchronous JavaScript and XML (AJAX) mode.
2. When no attack is involved, the content of the received JSON instruction is as follows: {"message": "no data", "code": 404}. In such cases, the JS files enter into a continuous loop after being loaded and periodically rereads the JSON instruction.
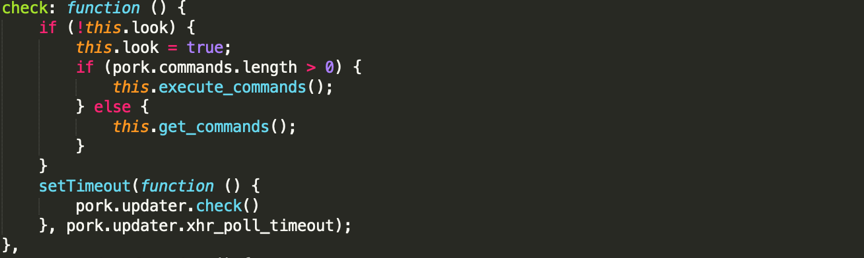
Looping or executing attacks based on the JSON instruction
3. After a hacker issues an attack-type JSON instruction, JS files exit the loop and messages are delivered back to WebView after the JSON instruction is parsed. The JSON instruction specifies the packet content that is required for an attack, such as target URL, request method, and header, and specifies the scheduling parameters, such as attack frequency, conditions for starting an attack, and attack end time, making the attack more complex and flexible.
4. WebView retrieves the device information through the UserAgent to determine whether the device uses the iOS or Android system. It calls different functions for different device systems to trigger the loading of Java code in a malicious app and makes the device initiate an attack based on the JSON instruction.
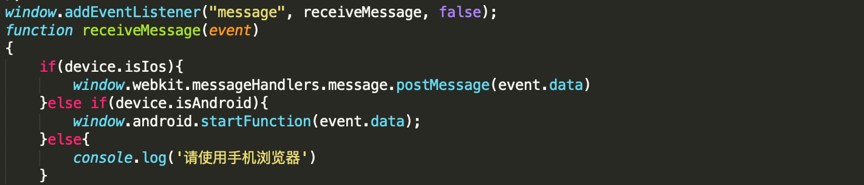
Determine device systems: iOS or Android
With the methods and techniques employed above, we could consider users who installed this fraudulent app found in black markets as puppets to launch a DDoS attack successfully toward target businesses.
This also reveals a black-market industry. The owners of malicious applications attracts users to install and use these apps through various channels with deceptive advertisements. The owners profit from the use of fraudulent apps and also seek to further profits by providing DDOS attack services using affected user devices as botnets.
Based on the attack flowchart, hackers can issue JSON instructions to make mobile devices attack a specific target in a specific way for any given purpose.
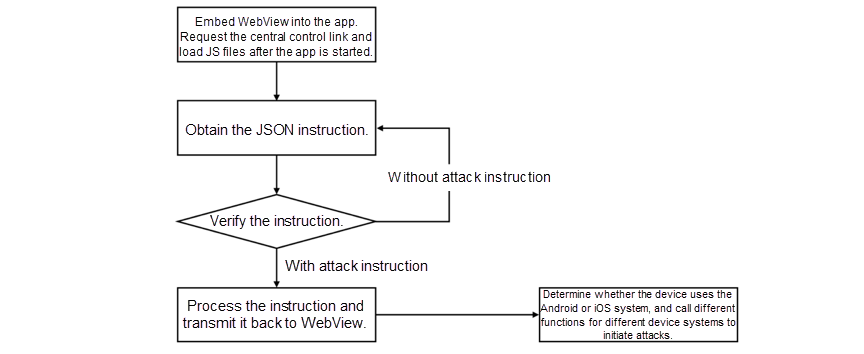
Attack flowchart
In addition to maliciously controlling mobile devices to initiate attacks, fraudulent apps can also implant malicious code to privately send paid SMS messages, steal user fees by using SMS payment channels of ISPs, and access user address books, geographical locations, identity cards, bank accounts, and other sensitive information. They can harass users with advertising and telecommunications fraud, or even cause greater losses such as identity theft.
In the era of PC botnets, enterprise Anti-DDoS policies are relatively ineffective
If mitigation was ineffective, manual intervention was required for packet capture and analysis. Protection rules were then configured according to the specific attack conditions. However, this method has a slow response speed and results in serious damage to the business.
When massive numbers of mobile devices become new attack sources, Attacks can easily bypass the preceding defense logic. Enterprises can no longer rely on rate-limiting and blacklisting, but must adopt more intelligent means of protection:
Although hackers had only upgraded their attack sources, enterprises are facing heavy security defense workloads and must take actions as early as possible to be well prepared. Alternatively, enterprises can purchase Alibaba Cloud Security Anti-DDoS products to effectively defend against volumetric DDoS attacks and application DDoS attacks for professional and intelligent protection.
If you are an individual user, to ensure device security and data privacy, the Alibaba Cloud security team recommends that you install approved apps from authorized channels to avoid turning your mobile phone into a DDoS attack tool. When installing an app, always carefully inspect the permissions it requests. If you find that the app requests high-risk permissions that do not match its functions, such as accessing your address book and sending SMS messages, exercise caution because it may put you at risk.
Xulu: Cryptojacking Leveraging Shodan, Tor, and Malicious Docker Container

32 posts | 15 followers
FollowAlibaba Clouder - July 27, 2018
Alibaba Cloud Security - November 6, 2019
Alibaba Clouder - June 11, 2019
Alibaba Clouder - July 5, 2018
Alibaba Clouder - June 11, 2019
Alibaba Cloud Security - January 13, 2019

32 posts | 15 followers
Follow Anti-DDoS
Anti-DDoS
A comprehensive DDoS protection for enterprise to intelligently defend sophisticated DDoS attacks, reduce business loss risks, and mitigate potential security threats.
Learn More Security Center
Security Center
A unified security management system that identifies, analyzes, and notifies you of security threats in real time
Learn More Security Solution
Security Solution
Alibaba Cloud is committed to safeguarding the cloud security for every business.
Learn More Security Overview
Security Overview
Simple, secure, and intelligent services.
Learn MoreMore Posts by Alibaba Cloud Security