The previous article uses an official example to demonstrate how to deploy applications in this Istio environment. Based on this example, this article will explain how to use Istio functions, such as traffic routing, fault injection, rate limiting, and traffic shifting.
To quickly review this official example, visit https://istio.io/docs/examples/bookinfo/ . As shown below, the example application is composed of four separate microservices that are compiled in different languages. These services are not dependent on Istio.
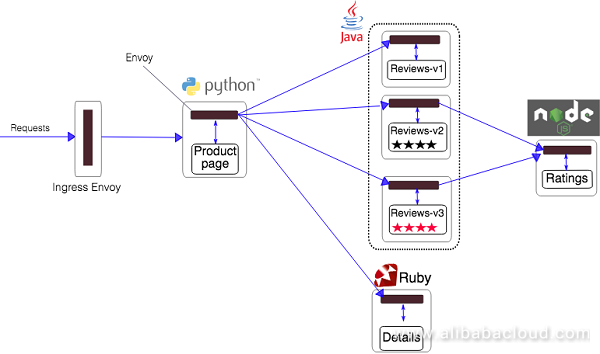
The BookInfo example application deploys three versions of the reviews service. Therefore, a default route must be configured.Otherwise, when the application is accessed for multiple times, the displayed review content sometimes contains the rating information, and sometimes does not contain the rating information.This symptom occurs because when no default route is explicitly specified for the application, Istio routes the requests to all available versions of the reviews service at random.
Run the following command to set the default version of all microservices to v1:
istioctl create -f samples/bookinfo/routing/route-rule-all-v1.yamlYou can run the following command to display all the routing rules that have been created:
istioctl get virtualservices -o yamlAs routing rules are distributed to the proxies in an asynchronized manner, these rules are synchronized to all pods after a period of time.Therefore, you need to wait for a few seconds and then try to access the application.
Open the URL of the BookInfo application in the browser: http://{EXTERNAL-IP}/productpage.
For more information on getting the EXTERNAL-IP, refer to the previous article.
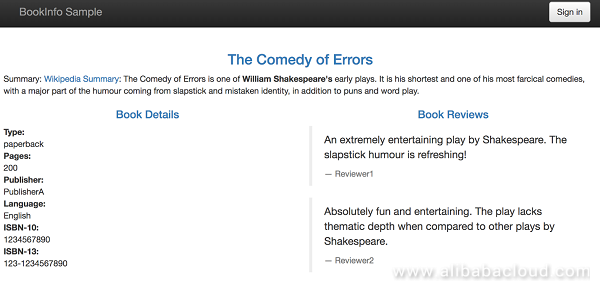
The productpage of the BookInfo application is displayed, where the review information without stars is displayed, because the reviews v1 service does not call the ratings service.
Run the following command to route requests from the test user "jason" to reviews v2 to enable the ratings service.
kubectl replace -f samples/bookinfo/routing/route-rule-reviews-test-v2.yamlRun the following command to confirm that the rule is created:
kubectl get virtualservice reviews -o yaml
apiVersion: networking.istio.io/v1alpha3
kind: VirtualService
metadata:
clusterName: ""
creationTimestamp: 2018-06-04T10:49:53Z
generation: 0
name: reviews
namespace: default
resourceVersion: "2596548"
selfLink: /apis/networking.istio.io/v1alpha3/namespaces/default/virtualservices/reviews
uid: 03528fd9-67e5-11e8-af82-00163e0c19c2
spec:
hosts:
- reviews
http:
- match:
- headers:
cookie:
regex: ^(.*?;)?(user=jason)(;.*)?$
route:
- destination:
host: reviews
subset: v2
- route:
- destination:
host: reviews
subset: v1After confirming that the rule is created, open the URL of the BookInfo application in the browser: http://{EXTERNAL-IP}/productpage.
Log on to the productpage as user "jason". The rating information should be displayed at the bottom of each review record.
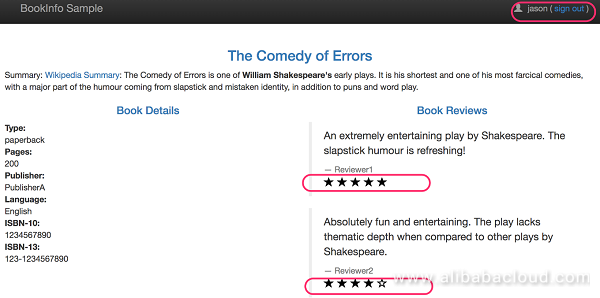
The mechanism is as follows: Use Istio to route all the requests to reviews v1 service. Then, configure a routing rule, which selectively routes requests to the reviews v2 service based on the request header, for example, the user's cookie.
To test the resiliency of the Bookinfo application, inject a 7s delay between the reviews v2 and ratings microservices for user "jason".As the reviews v2 service sets a 10s timeout for calls to the ratings service, it is expected that the end-to-end flow can continue without any errors.
Use HTTP Delay to create a fault injection rule to delay the traffic coming from user "jason":
kubectl replace -f samples/bookinfo/routing/route-rule-ratings-test-delay.yamlAfter confirming that the rule is created, open the URL of the BookInfo application in the browser: http://{EXTERNAL-IP}/productpage.
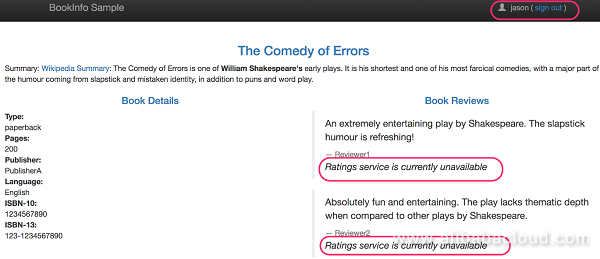
Log on to the productpage as user "jason". The following page should be displayed:
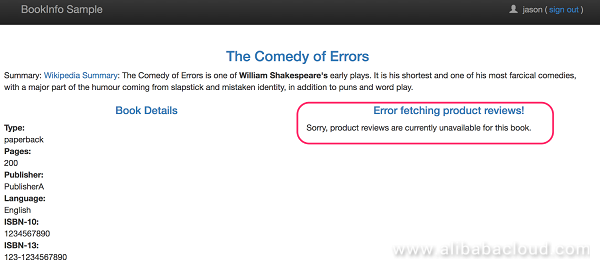
The reviews service fails because the timeout between the productpage and reviews services is shorter than the timeout between the reviews and ratings services, that is, (3 seconds + 1 retry = 6 seconds) is shorter than 10 seconds.Bugs like this can occur in typical enterprise applications where different teams develop different microservices independently.Istio's fault injection rules help you identify such anomalies without impacting end users.
Similarly, use HTTP Abort to create a fault injection rule:
kubectl replace -f samples/bookinfo/routing/route-rule-ratings-test-abort.yamlAfter confirming that the rule is created, open the URL of the BookInfo application in the browser: http://{EXTERNAL-IP}/productpage.
Log on to the productpage as user "jason". The following page should be displayed:
In addition to content-based routing, Istio also supports the weight-based routing rule.
First, set the default version of all microservices to v1.
kubectl replace -f samples/bookinfo/routing/route-rule-all-v1.yamlSecond, run the following command to route 50% of requests from the reviews v1 service to the reviews v3 service:
kubectl replace -f samples/bookinfo/routing/route-rule-reviews-50-v3.yamlRefresh the productpage for multiple times in the browser. You have a 50% probability to see the review content marked with red stars on the page.
Note that this method is completely different from using the deployment feature of the container orchestration platform for version migration.The container orchestration platform uses the instance scaling method to manage the traffic.In contrast, Istio allows two versions of the reviews service to scale up and down independently, without affecting the traffic distribution between them.
We can use Alibaba Cloud Container Service for Kubernetes to quickly build an Istio open platform for connecting, managing, and securing microservices, and to introduce and configure multiple relevant services for applications.Based on the official example, this article explains how to use Istio functions, such as traffic routing, fault injection, rate limiting, and traffic shifting.You are welcome to use Alibaba Cloud Container Service for Kubernetes to quickly build an Istio open platform and integrate Istio to microservice development in your project.
This article series introduces Istio and its core components, as well as describes how to quickly build an Istio open platform for connecting, managing, and securing microservices on the basis of Alibaba Cloud Container Service for Kubernetes. These articles also use an official example to demonstrate how to deploy an application in the Istio environment; how to configure intelligent routing and distributed tracing; and how to configure Istio functions of collecting, querying, and visualizing the telemetry data.
To review these articles, see:
Go through Istio features with samples on Alibaba Cloud Container Service for Kubernetes
Distributed Tracking with Istio on Alibaba Cloud Container Service for Kubernetes

56 posts | 8 followers
FollowXi Ning Wang - August 23, 2018
Xi Ning Wang - August 17, 2018
Xi Ning Wang - August 17, 2018
Xi Ning Wang - August 21, 2018
Xi Ning Wang - August 23, 2018
Xi Ning Wang - August 30, 2018

56 posts | 8 followers
Follow Container Service for Kubernetes
Container Service for Kubernetes
Alibaba Cloud Container Service for Kubernetes is a fully managed cloud container management service that supports native Kubernetes and integrates with other Alibaba Cloud products.
Learn More ACK One
ACK One
Provides a control plane to allow users to manage Kubernetes clusters that run based on different infrastructure resources
Learn More Cloud-Native Applications Management Solution
Cloud-Native Applications Management Solution
Accelerate and secure the development, deployment, and management of containerized applications cost-effectively.
Learn More Container Registry
Container Registry
A secure image hosting platform providing containerized image lifecycle management
Learn MoreMore Posts by Xi Ning Wang(王夕宁)