重保情境防護適用於特定時間段的重大活動安全保障,為您提供更加精準和定製化的防禦模式。本文介紹如何開啟和使用重保情境防護模式。
計費說明
產品及服務價格可能會發生變動,最終請以您的阿里雲賬單為準。
特性 | 說明 |
計費模式 | 重保情境防護採用預付費模式,支援30天起購買,並根據開通時所選的時間長度,產生預付費賬單。 |
有效期間 | 重保情境防護在購買後立即生效,有效期間為開通時所選的购买时长。 到期後,重保情境防護功能將自動停止防護。 |
續約 | 重保情境防護暫不支援直接續約。如果您希望繼續使用重保情境防護功能,您可以在到期後再次開通重保情境防護。 |
退款說明 | 重保情境防護購買成功後,不支援任何形式的退訂(包含五天無理由退訂、非五天無理由退訂)及退款。購買前,請根據業務需求評估是否購買。 |
前提條件
已開通WAF 3.0服務。具體操作,請參見開通WAF 3.0訂用帳戶執行個體、開通WAF 3.0隨用隨付執行個體。
不同版本的執行個體對應的開通重保情境防護方式不同。
已開通執行個體的版本
是否預設開通重保情境防護
說明
訂用帳戶旗艦版
是
無需單獨開通重保情境防護,可直接使用該功能。
訂用帳戶進階版和企業版、隨用隨付版
否,可通過臨時升級開通
訂用帳戶基礎版
否,且暫不支援開通重保情境防護
已通過CNAME接入、雲產品接入(CLB(HTTP/HTTPS)、CLB(TCP)、ECS)完成Web業務接入。具體操作,請參見接入概述。
說明通過ALB、MSE或FC接入WAF的防護對象暫不支援該功能。
開通重保情境防護
WAF執行個體為訂用帳戶
登入Web Application Firewall3.0控制台。在頂部功能表列,選擇WAF執行個體的資源群組和地區(中國內地、非中國內地)。
在左側導覽列,選擇。
單擊開通重保防護,在開通重保防護面板,開啟重保情境,並設定還原時間。
仔細閱讀並選中服务协议後,單擊立即購買並完成支付。
開通重保情境防護後,您可以在重保情境防護頁面,在重保情境防護包卡片地區,查看重保情境防護的規格詳情。
WAF執行個體為隨用隨付
登入Web Application Firewall3.0控制台。在頂部功能表列,選擇WAF執行個體的資源群組和地區(中國內地、非中國內地)。
在左側導覽列,選擇。
單擊開通重保防護,在開通重保防護面板,選擇购买时长。
仔細閱讀並選中服务协议後,單擊立即購買並完成支付。
開通重保情境防護後,您可以在重保情境防護頁面,在重保情境防護包卡片地區,查看重保情境防護的規格詳情。
建立重保情境防護規則模板
首次配置重保情境防護時,您必須建立一個重保情境防護規則模板。最多支援建立20個防護模板。
登入Web Application Firewall3.0控制台。在頂部功能表列,選擇WAF執行個體的資源群組和地區(中國內地、非中國內地)。
在左側導覽列,選擇。
在防護模板頁簽,單擊新建模板。
在建立重保防護模板面板,完成以下配置。
配置基本資料。完成後,單擊下一步。
配置項
說明
模板名稱
為該模板設定一個名稱。
長度為1~255個字元,支援中文和大小寫英文字母,可包含數字、半形句號(.)、底線(_)和短劃線(-)。
防護規則
配置要應用的防護規則並配置規則動作。
重保威脅情報:攻防對抗惡意IP情報,精準識別攻擊者。預設開啟,且防護動作配置為觀察。
重保防護規則群組:基於智能防護模型,針對每個使用者產生精準的防護規則集合。預設開啟,且防護動作配置為觀察。
重保IP黑名單:開啟該功能,WAF會觀察或攔截來自特定IP地址或位址區段的請求,支援下發50,000條自訂IP或IP段黑名單。
Shiro還原序列化漏洞防護:開啟該功能,WAF會基於cookie加密技術防護Apache Shiro Java還原序列化漏洞。
生效對象
從已添加的配置防護對象和防護對象組中,選擇要應用該模板的配置防護對象和防護對象組。
如果配置基本資料時,開啟重保IP黑名單防護規則,則需要通過以下方式配置IP黑名單。完成後,單擊下一步。
配置項
操作
新增IP黑名單
單擊新增IP黑名單,可手動添加IP黑名單。
在IP黑名單文字框,輸入要加入黑名單的IP,斷行符號儲存。
說明IP黑名單為IPv6或CIDR掩碼格式的位址區段,多個地址之間用斷行符號或英文逗號分隔,最多配置500個。
設定生效截止時間。可選項:
永久生效。
自訂。單擊時間選取器,指定具體的生效截止時間。
在備忘文字框,輸入備忘資訊後,單擊確定。
成功新增黑名單後,您可在IP黑名單配置面板查看新增的IP黑名單。
匯入IP黑名單
單擊匯入IP黑名單,可大量匯入IP黑名單。
單擊上傳檔案,選擇要匯入的IP黑名單檔案。
重要支援上傳CSV格式檔案。
支援匯入IPv4和IPv6格式的地址和位址區段。
每條規則可匯入一個檔案,每個檔案最多支援2000個IP/IP段,一個IP段佔用1個計數單元,單次匯入的檔案大小不能超過1 MB。
有大批量IP匯入的情況下,可分多次匯入。
設定生效截止時間。可選項:
永久生效。
自訂。單擊時間選取器,指定具體的生效截止時間。
在備忘文字框,輸入備忘資訊後,單擊確定。
成功新增黑名單後,您可在IP黑名單配置面板查看新增的IP黑名單。
清空所有IP
如果已添加IP的請求不再需要被攔截,您可以單擊清空所有IP,刪除所有IP。
清空到期IP
如果已添加IP的生效截止時間已到期,您可以單擊清空到期IP,清空所有到期IP。
單擊完成。
建立的規則模板預設開啟。您可以在規則模板列表執行如下操作:
查看防護模板包含的防護規則、關聯的防護對象/組的數量。
通過模板開關,開啟或關閉模板。
編輯、刪除或複製規則模板。
如果當前防護模板已開啟重保IP黑名單規則,可單擊編輯IP黑名單,添加或修改IP黑名單。
查看重保情境防護資料
登入Web Application Firewall3.0控制台。在頂部功能表列,選擇WAF執行個體的資源群組和地區(中國內地、非中國內地)。
在左側導覽列,選擇。
您可以查看如下資訊。
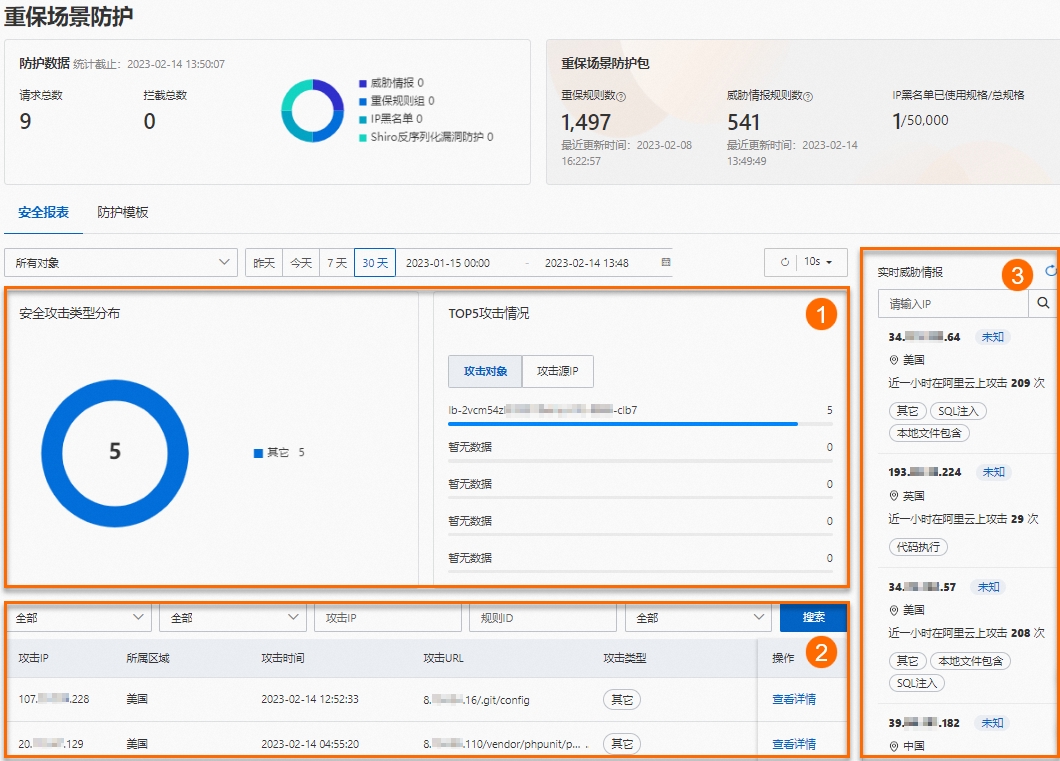
在防護數據卡片地區,查看統計截止時間內的請求總數、攔截總數和通過餅狀圖展示的防護類型及其資料。
在重保情境防護包卡片地區,查看統計截止時間內的重保規則數、威脅情報規則數、IP黑名單已使用規格/總規格等資訊。
在安全報表頁簽,設定要查詢的防護對象和時間範圍,查詢對應的安全報表資料。
防護對象:預設已選擇所有對象,表示查詢已接入WAF防護的所有對象的資料。您可以選擇只查詢某個對象的資料。
時間範圍:預設展示今天的資料。您可以選取查詢昨天、今天、7 天、30 天或最近30天範圍內任意時間的資料。
安全報表資料說明如下表所示。
資料類型
說明
支援的操作
攻擊統計分析(圖示①)
展示在指定時間範圍內,防護對象收到的攻擊請求的統計分析結果,包括:
安全攻擊類型分布:
通過餅狀圖,展示攻擊類型的分布情況。
TOP5攻擊情況:
在攻擊對象頁簽、攻擊源IP頁簽,通過列表,分別展示發起攻擊請求次數最多的前5個攻擊對象、攻擊源IP。按照攻擊次數由大到小排序。
無
攻擊事件記錄(圖示②)
通過列表,展示觸發Web核心防護規則的攻擊請求的資訊。
列表中包含以下資訊:
攻擊IP:發起攻擊請求的IP地址。
所屬地區:攻擊IP所屬地區。
攻擊時間:攻擊的開始時間。
攻擊類型:攻擊的類型,例如,SQL注入、代碼執行等。
規則類型:規則所屬的類型,例如,重保防護規則群組、重保威脅情報等。
規則動作:分為攔截(表示WAF攔截了該請求)和觀察(表示WAF只觀察記錄該請求為攻擊請求,未攔截該請求)。
篩選攻擊事件
您可以在攻擊事件表格上方,使用以下欄位(從左至右依次排序)篩選攻擊事件:
攻擊類型:預設已選擇全部。其他可選項:SQL注入、跨站指令碼、代碼執行、本地檔案包含、遠程檔案包含、Webshell、其他。
規則類型:預設已選擇全部。其他可選項:重保防護規則群組、重保威脅情報、重保IP黑名單、Shiro還原序列化漏洞防護。
規則動作:預設已選擇全部。其他可選項:攔截、觀察。
查看攻擊詳情
在攻擊事件操作列,單擊目標事件的查看詳情,可以查看攻擊詳情,擷取關於攻擊事件和防護規則的更多資訊,例如,規則ID、規則名稱、規則描述、規則動作、攻擊類型等。
即時威脅情報(圖示③)
即時展示攻擊IP威脅情報資訊,包括:
攻擊IP及其屬性。
攻擊IP所屬地區。
近一小時攻擊次數。
攻擊類型。
查詢攻擊IP即時威脅情報
在搜尋方塊輸入要查詢的IP,單擊
 ,可查詢IP對應的威脅情報屬性。
,可查詢IP對應的威脅情報屬性。