To use Web Application Firewall (WAF) to protect a website, you must add the domain name of the website to WAF. This topic describes how to add a domain name to WAF in CNAME record mode and check whether the domain name is successfully added to WAF.
How WAF protection works
After you add the domain name of a website to WAF in CNAME record mode, all the website traffic is redirected to WAF for inspection. WAF filters out malicious traffic and forwards normal traffic to the origin server. This ensures the service and data security of the website. In this case, WAF inspects and forwards traffic as a reverse proxy cluster.

Prerequisites
A WAF 3.0 instance is purchased. For more information, see Purchase a subscription WAF 3.0 instance and Purchase a pay-as-you-go WAF 3.0 instance.
If the domain name of your website is hosted on a server in the Chinese Mainland, make sure that an ICP filing is complete for the domain name and the ICP filing information is valid when your website is protected by WAF.
NoteWAF instances that are deployed in the Chinese Mainland region regularly check whether the ICP filing information of your domain names is valid. If the ICP filing information of a domain name becomes invalid, WAF manages the domain name based on relevant laws and regulations. For example, WAF may stop forwarding requests for the domain name or delete the configurations of the domain name.
If your website is hosted on Alibaba Cloud, you can apply for an ICP filing for your domain name by using the Alibaba Cloud ICP Filing system. For more information, see Scenarios.
If your website is not deployed on Alibaba Cloud, you can contact Alibaba Cloud or another cloud service provider to apply for an ICP filing.
Procedure
Log on to the WAF 3.0 console. In the top navigation bar, select the resource group and region of the WAF instance. You can select Chinese Mainland or Outside Chinese Mainland.
In the left-side navigation pane, click Website Configuration.
On the CNAME Record tab, click Add.
In the Configure Listener step, configure the parameters and click Next. The following table describes the parameters.
Parameter
Description
Domain Name
Enter the domain name that you want to protect. You can enter an exact-match domain name, such as
www.aliyundoc.com, or a wildcard domain name, such as*.aliyundoc.com. You can enter only one domain name.The first time you add a domain name to WAF, you must verify your ownership of the domain name. You can add the domain name to WAF only after your ownership passes the verification. For more information, see Verify the ownership of a domain name.
NoteYou can use a wildcard domain name to cover all subdomains that are at the same level as and different levels from the wildcard domain name. For example,
*.aliyundoc.comcan coverwww.aliyundoc.com,example.aliyundoc.com, andwww.example.aliyundoc.com.A second-level wildcard domain name can cover its second-level parent domain name. For example,
*.aliyundoc.comcan coveraliyundoc.com.A third-level wildcard domain name cannot cover its third-level parent domain name. For example,
*.example.aliyundoc.comcannot coverexample.aliyundoc.com.If you add an exact-match domain name and a wildcard domain name that covers the exact-match domain name, the protection rules that are configured for the exact-match domain name take precedence.
Protocol Type
Select the protocol type and ports that are used by the website. Press the Enter key each time you enter a port number.
NoteThe port number that you enter must be supported by WAF. To view the HTTP and HTTPS ports that are supported by WAF, click View Port Range. For more information, see View supported ports.
If you select HTTPS, configure the HTTPSUpload Type parameter to specify the method that you want to use to upload an SSL certificate. Then, upload the SSL certificate bound to the domain name to WAF. This way, WAF can monitor the HTTPS traffic of the website.
Specify the method that you want to use to upload an SSL certificate.
NoteWAF (version_share_vm) does not support HTTPS.
If you select HTTPS and upload a certificate, you can perform the following operations based on your business requirements:
If your website supports HTTP/2, select HTTP2 to protect HTTP/2 requests.
NoteThe HTTP/2 ports are the same as the HTTPS ports.
Advanced Settings
Whether Layer 7 Proxy, Such as Anti-DDoS Pro, Anti-DDoS Premium, or Alibaba Cloud CDN, Is Deployed in Front of WAF
Specify whether a Layer 7 proxy, such as Anti-DDoS Proxy or Alibaba Cloud CDN, is deployed in front of WAF. Valid values:
More Settings
Resource Group
Select the resource group to which you want to add the domain name from the drop-down list. If you do not select a resource group, the domain name is added to the default resource group.
NoteYou can use Resource Management to create resource groups and manage resources within your Alibaba Cloud account by department or project. For more information, see Create a resource group.
In the Configure Forwarding Rule step, configure the parameters and click Submit. The following table describes the parameters.
Parameter
Description
Load Balancing Algorithm
If you specify multiple origin server addresses, select the Load Balancing Algorithm that you want WAF to use to forward back-to-origin requests to the origin servers. Valid values:
Origin Server Address
Specify the public IP address or domain name of the origin server. The IP address or domain name is used to receive the back-to-origin requests that are forwarded by WAF. Valid values:
- Important
If the public IP address of the origin server changes, you need to manually add the new back-to-origin IP address.
Standby Link Back-to-origin
If the primary address of the origin server is unreachable, the system automatically switches to the secondary address, which requires up to 30 seconds to take effect. After the primary address is restored, the system automatically switches back to it.
- Important
If the public IP address of the origin server changes, you need to manually add the new back-to-origin IP address.
Advanced HTTPS Settings
Other Advanced Settings
In the Add Completed step, obtain the CNAME assigned to the domain name. Modify the DNS record to point the domain name to the CNAME that is provided by WAF. For more information, see Modify the DNS record of a domain name.
ImportantBefore you modify the DNS record, make sure that the following conditions are met:
The forwarding configurations for your website are correct and have taken effect. If you modify the DNS record before the forwarding configurations for your website take effect, service interruptions may occur. For more information, see Verify domain name settings.
The back-to-origin CIDR blocks of WAF are added to the IP address whitelist of the third-party firewall used by the origin server on which the domain name is hosted. This prevents normal requests that are forwarded by WAF from being blocked. On the CNAME Record tab, you can click Back-to-origin CIDR Blocks above the domain name list to view and copy the back-to-origin CIDR blocks of WAF. For more information, see Allow access from back-to-origin CIDR blocks of WAF.
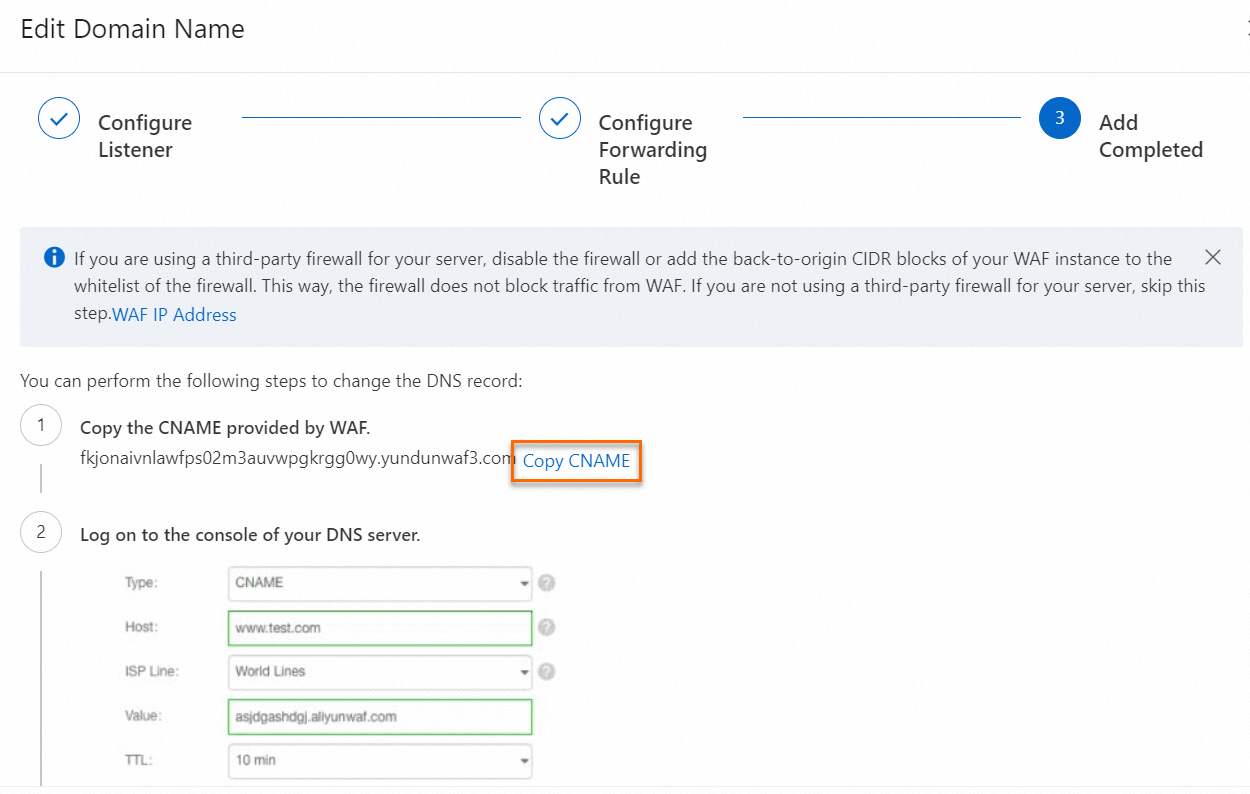
After you complete the preceding configurations, you can perform the following operations to check whether the domain name is protected by WAF:
Enter the domain name in your browser. If you can access the website, the domain name is protected by WAF.
Enter the domain name and malicious code such as
<Protected domain name>/alert(xss)andalert(xss). If a 405 error page appears, the attack is blocked and the domain name is protected by WAF.
ImportantIf you add a domain name to WAF in CNAME record mode, WAF checks whether ICP filing is complete for the domain name and whether the ICP filing information is valid on a regular basis. If the ICP filing information of the domain name becomes invalid, WAF stops forwarding requests for the domain name.
If the ICP filing information of a domain name that is added to WAF becomes invalid, you must re-apply for an ICP filing for the domain name. After the application is successful, you can go to the CNAME Record tab of the Website Configuration page and click Add Again in the Actions column to re-add the domain name to WAF.
More operations
View the DNS resolution status of a domain name
WAF checks the DNS resolution status of protected domain names and identifies domain names whose DNS records are abnormal. You can view the DNS resolution status of the domain names that you added to WAF in the domain name list and modify the DNS records based on the error messages that are displayed in the WAF console.
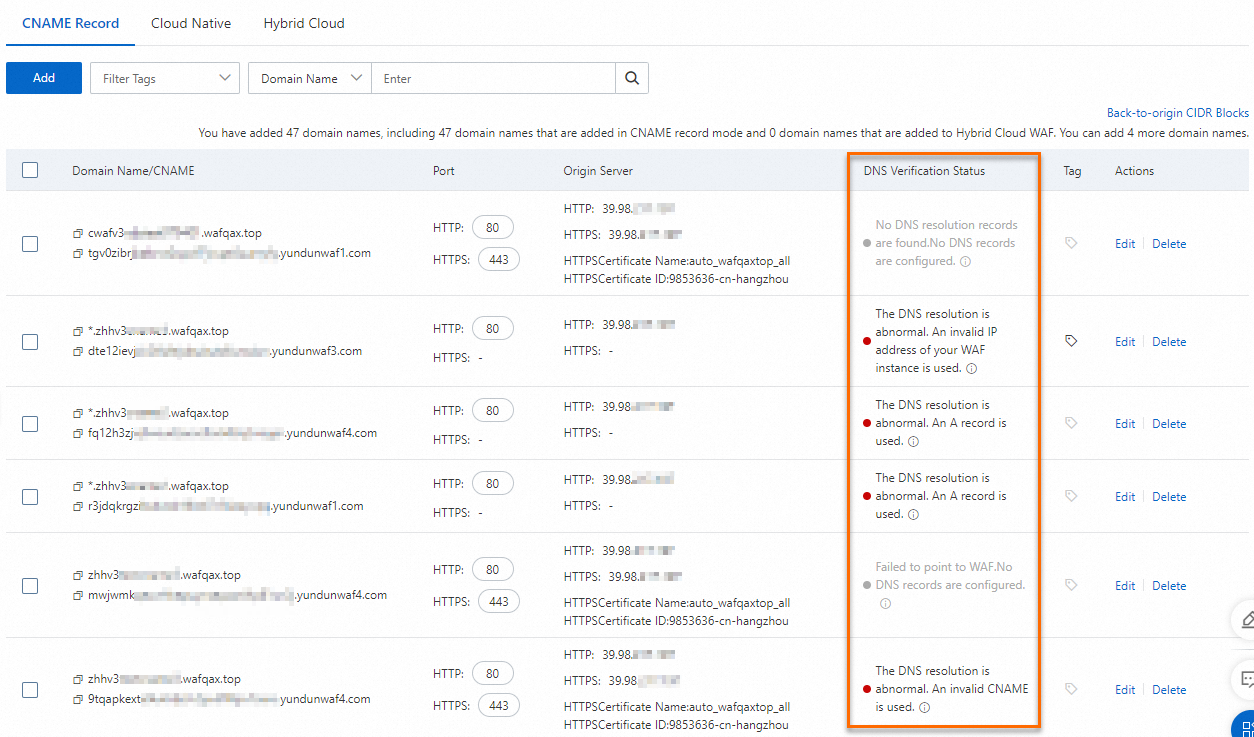
DNS Verification Status | Description | Operation |
The DNS resolution is normal. | The domain name is pointed to the CNAME that is provided by WAF. | None. |
The DNS resolution is abnormal. An A record is used. | An A record is used and service interruptions may occur. | Delete the A record and add a CNAME record to point the domain name to the CNAME that is provided by WAF. For more information, see Modify the DNS record of a domain name. |
The DNS resolution is abnormal. An invalid IP address of your WAF instance is used. | An A record is used and the domain name is pointed to an invalid WAF IP address. Service interruptions may occur. | Delete the A record and add a CNAME record to point the domain name to the CNAME that is provided by WAF. For more information, see Modify the DNS record of a domain name. |
The DNS resolution is abnormal. An invalid CNAME is used. | A CNAME record is used and the domain name is pointed to an invalid CNAME. Service interruptions may occur. | Modify the CNAME record to point the domain name to the CNAME that is provided by WAF. For more information, see Modify the DNS record of a domain name. |
The issue of unknown DNS resolution occurs. A proxy is deployed. | A Layer 7 proxy is used in front of WAF and the back-to-origin address is not the CNAME that is provided by WAF. | Check whether the back-to-origin address is the CNAME that is provided by WAF. |
The verification timed out. | None. | Click the |
No DNS resolution records are found. No DNS records are configured. | No DNS records are configured for the domain name. A CNAME record must be added to point the domain name to the CNAME that is provided by WAF. | Add a CNAME record to point the domain name to the CNAME that is provided by WAF. For more information, see Modify the DNS record of a domain name. |
Failed to point to WAF. No DNS records are configured. | The domain name is not pointed to the CNAME provided by WAF. A CNAME record must be added to point the domain name to the CNAME that is provided by WAF. | Modify the CNAME record to point the domain name to the CNAME that is provided by WAF. For more information, see Modify the DNS record of a domain name. |
Add tags to or remove tags from domain names
You can add tags to domain names that are added to WAF and search for specific domain names by tag.
Modify or remove a domain name that is added to WAF
Before you remove a domain name, you must change the DNS record configuration back to the original configuration. For example, you can modify the DNS record to resolve the domain name to the IP address of the origin server. If you do not change the DNS record configuration, WAF cannot forward the requests that are sent to the domain name to the origin server and your website cannot be accessed.
Find the domain name that you want to manage and click Edit or Delete in the Actions column.
Configure default SSL or TLS settings
If you add multiple domain names to the same WAF instance, a shared WAF virtual IP address (VIP) is used to monitor the traffic of the domain names.
To meet the security compliance and compatibility requirements of HTTPS in different scenarios, WAF allows you to configure SSL or TLS settings for IPv4 VIPs. Before you perform compliance scan and detection, you can upload an HTTPS certificate for the VIP and disable or enable specific TLS protocol versions and cipher suites.
If you purchase and enable an exclusive IP address, the configuration takes effect for the exclusive IP address. For more information about exclusive IP addresses, see Exclusive IP addresses.
Click Default SSL/TLS Settings above the domain name list.

In the Default SSL/TLS Settings dialog box, configure the parameters and click OK. The following table describes the parameters.
Parameter
Description
HTTPSUpload Type
Specify the method used to upload the SSL certificate. For more information, see the HTTPSUpload Type parameter in this topic.
TLS Version
Specify the TLS protocol versions that are supported for HTTPS communication. Valid values:
TLS 1.0 and Later (Best Compatibility and Low Security) (default)
TLS 1.1 and Later (High Compatibility and High Security)
TLS 1.2 and Later (High Compatibility and Best Security)
If you want to enable TLS 1.3, select Support TLS 1.3.
HTTPSCipher Suite
Specify the cipher suites that are supported for HTTPS communication. Valid values:
All Cipher Suites (High Compatibility and Low Security) (default)
Custom Cipher Suite (Select It Based on Protocol Version. Proceed with Caution.)
For more information about custom cipher suites, see View supported cipher suites.
Update the SSL certificate bound to a domain name
If the SSL certificate that is bound to a domain name is about to expire or the certificate is changed, such as when the certificate is revoked, you must update the certificate.
If the remaining validity period of the certificate is less than 30 days, the
 icon is displayed in the domain name list. This indicates that your certificate is about to expire. In this case, you must update the certificate at the earliest opportunity.
icon is displayed in the domain name list. This indicates that your certificate is about to expire. In this case, you must update the certificate at the earliest opportunity. If you want to receive notifications by using methods such as email or text message when the certificate is about to expire, you can configure notifications for the certificate. For more information, see Configure notifications for SSL certificates.
To prevent service interruptions due to certificate expiration, enable the certificate hosting feature of Certificate Management Service. If you enable this feature for a certificate, the system automatically applies for a new certificate when the hosted certificate is about to expire. For more information, see Introduction to the certificate hosting feature.
To update an SSL certificate that is bound to a domain name, perform the following steps:
Renew the certificate or upload a third-party certificate to Certificate Management Service. For more information, see Certificate renewal or Upload and share an SSL certificate.
Synchronize the certificate to WAF.
In the Certificate Management Service console, deploy the certificate to WAF. For more information, see Deploy certificates to Alibaba Cloud services.
Upload the certificate in the WAF console.
On the CNAME Record tab of the Website Configuration page, find the domain name whose certificate you want to update and click Edit in the Actions column.
Set the HTTPSUpload Type parameter to Select Existing Certificate and select the new certificate.
What to do next
After you add a domain name to WAF, the domain name is automatically added as a protected object of WAF and the protection rules of the core protection rule module are automatically enabled for the protected object. The name of the protected object is in the Domain name-waf format. You can view the protected object and configure protection rules for the protected object on the page.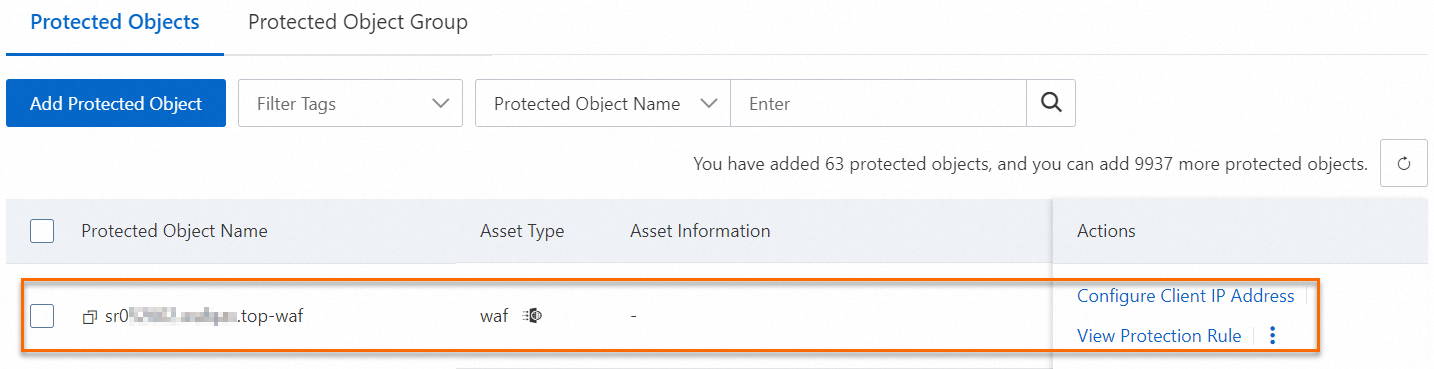
References
For more information about protected objects, protection rules, and protection processes, see Protection configuration overview.
For more information about how to add a domain name to WAF by calling an API operation, see CreateDomain.
For more information about how to query the details of a domain name that is added to WAF in CNAME record mode, see DescribeDomainDetail.
 icon to the right of the tag. Then, the tag is removed from the domain name.
icon to the right of the tag. Then, the tag is removed from the domain name.