This topic describes how to configure active/standby connections between a data center and a virtual private cloud (VPC) by using IPsec-VPN and an Express Connect circuit.
Scenarios
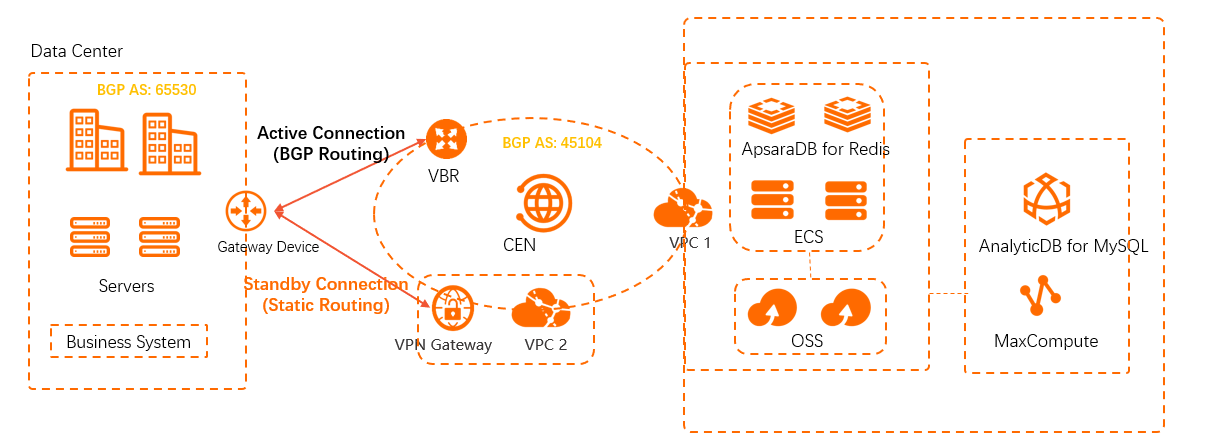
This topic uses the following scenario to show how to use both IPsec-VPN and an Express Connect circuit to connect a data center to a VPC. A company has a data center in Hangzhou, and has deployed VPC1 in the China (Hangzhou) region. In VPC1, cloud services such as Elastic Compute Service (ECS) are deployed for interaction and data analytics. The company wants to establish active/standby connections between the data center and VPC1. The following section describes the connections:
Connection 1: Create an Express Connect circuit and use Cloud Enterprise Network (CEN) to connect the data center to VPC1.
Connection 2: Associate a VPN gateway with an independent VPC (VPC2). VPC2 does not have any services deployed and serves only as a transit node to connect the data center to the cloud through an IPsec-VPN connection. Then, the data center can connect to VPC1 through the IPsec-VPN connection and CEN.
When the Express Connect circuit and IPsec-VPN connection are working as expected, VPC1 can learn the routes that point to the data center through the Express Connect circuit and the IPsec-VPN connection. By default, the routes learned through the Express Connect circuit have a higher priority than those learned through the IPsec-VPN connection. Therefore, data is transferred from VPC1 to the data center through the Express Connect circuit by default.
When the Express Connect circuit is down, the routes learned from the Express Connect circuit are withdrawn and the routes learned through the IPsec-VPN connection automatically take effect. Data is transferred from VPC1 to the data center through the IPsec-VPN connection. When the Express Connect circuit recovers, the Express Connect circuit takes over and the IPsec-VPN connection serves as the standby connection.
Preparations
You must plan routing protocols for the data center and network instances. In this topic, the following routing protocols are used:
Static routing is used between the data center gateway and VPN gateway.
Border Gateway Protocol (BGP) dynamic routing is used between the gateway device of the data center and the virtual border router (VBR).
NoteIn scenarios in which a VPN gateway works as a standby connection and an Express Connect circuit works as an active connection:
If the VPN gateway is associated with an independent VPC (for example, VPC2 in this topic), the VBR must use BGP dynamic routing. The VPN gateway can use static routing or BGP dynamic routing.
If the VPN gateway is associated with a VPC where services are deployed (for example, VPC1 in this topic), both the VBR and VPN gateway must use BGP dynamic routing.
You must plan networks for the data center and network instances. Make sure that the CIDR block of the data center does not overlap with those of the network instances. In this topic, the following CIDR blocks are used.
Item
CIDR block
IP address
VPC1
192.168.0.0/16
IP address of the ECS instance: 192.168.20.161
VPC2
10.0.0.0/16
N/A
VBR
10.1.0.0/30
VLAN ID: 0
IPv4 address on the Alibaba Cloud side: 10.1.0.1/30
IPv4 address on the customer side: 10.1.0.2/30
In this topic, the device on the customer side refers to the gateway device in the data center.
Data center
172.16.0.0/16
IP address of the client: 172.16.1.188
Data center gateway
10.1.0.0/30
Public IP address: 211.XX.XX.68
IP address of the interface connected to the Express Connect circuit: 10.1.0.2/30
The BGP autonomous system number (ASN): 65530
VPC1 and VPC2 are created in the China (Hangzhou) region. The cloud services that are used for business interaction and data analytics are deployed in VPC1. No service is deployed in VPC2. VPC2 is associated with a VPN gateway and serves as a transit VPC between the data center and VPC1. For more information, see Create and manage a VPC.
Check the gateway device in the data center. Make sure that it supports standard IKEv1 and IKEv2 protocols. To check whether the gateway supports the IKEv1 and IKEv2 protocols, contact the gateway manufacturer.
A static IP address is assigned to the gateway device in the data center.
You understand the security group rules of the ECS instances in VPC1. Make sure that the rules allow the data center to access the ECS instances in VPC1. For more information, see View security group rules and Add a security group rule.
Procedure
Step 1: Deploy an Express Connect circuit
Create an Express Connect circuit.
You must apply for an Express Connect circuit in the China (Hangzhou) region. For more information, see Create and manage a dedicated connection over an Express Connect circuit or Overview of hosted connections.
Create a VBR.
Log on to the Express Connect console.
In the left-side navigation pane, click Virtual Border Routers (VBRs).
In the top navigation bar, select the region where you want to create the VBR.
In this example, the China (Hangzhou) region is selected.
On the Virtual Border Routers (VBRs) page, click Create VBR.
In the Create VBR panel, set the following parameters and click OK.
Account: Select Current Account.
Name: VBR is used in this example.
Physical Connection Interface: Select an Express Connect circuit.
VLAN ID: Set this parameter to 0.
Set VBR Bandwidth Value: Specify the maximum bandwidth of the VBR.
IPv4 Address (Alibaba Cloud Gateway): Set this parameter to 10.1.0.1.
IPv4 Address (Data Center Gateway): Set this parameter to 10.1.0.2.
Subnet Mask (IPv4): Set this parameter to 255.255.255.252.
Configure a BGP group.
On the Virtual Border Routers (VBRs) page, click the ID of the VBR that you want to manage.
On the details page, click the BGP Groups tab.
Click Create BGP Group, set the following parameters, and then click OK.
Name: Enter a name for the BGP group. In this example, test is used.
Peer ASN: Enter the ASN of the gateway device in the data center. In this example, 65530 is used.
BGP Key: Enter the key of the BGP group. This parameter is not set in this example.
Description: Enter the description of the BGP group. In this example, test is used.
Configure the BGP peer.
On the VBR details page, click the BGP Peers tab.
On the BGP Peers tab, click Create BGP Peer.
In the Create BGP Peer panel, set the following parameters and click OK.
BGP Group: Select a BGP group. The BGP group named test is used in this example.
BGP Peer IP: Enter an IP address for the BGP peer. In this example, 10.1.0.2 is used, which is the port IP address of the gateway device in the data center.
Step 2: Deploy a VPN gateway
Create a VPN gateway.
Log on to the VPN Gateway console.
In the top navigation bar, select the China (Hangzhou) region.
On the VPN Gateways page, click Create VPN Gateway.
On the buy page, set the following parameters, click Buy Now, and then complete the payment.
Name: Enter a name for the VPN gateway.
Region: Select the region where you want to deploy the VPN gateway.
In this example, the VPN gateway is associated with VPC2. Make sure that VPC2 and the VPN gateway are deployed in the same region. In this example, the China (Hangzhou) region is selected.
Gateway Type: Select the type of the NAT gateway that you want to create. In this example, Standard is selected.
Network Type: Select the network type of the VPN gateway. Public is selected in this example.
Tunnels: The system displays the mode supported by the IPsec-VPN connection in the region.
VPC: Select the VPC where you want to deploy the VPN gateway. VPC2 is selected in this example.
VSwitch: Select a vSwitch from the VPC.
If you select Single-tunnel, you need to specify only one vSwitch.
If you select Dual-tunnel, you need to specify two vSwitches.
After the IPsec-VPN feature is enabled, the system creates an elastic network interface (ENI) for each of the two vSwitches as an interface to communicate with the VPC over an IPsec-VPN connection. Each ENI occupies one IP address in the vSwitch.
NoteBy default, the system selects a vSwitch. You can change or use the default vSwitch.
After a VPN gateway is created, you cannot modify the vSwitch associated with the VPN gateway. You can view the vSwitch associated with the VPN gateway, the zone to which the vSwitch belongs, and the ENI in the vSwitch on the details page of the VPN gateway.
vSwitch 2: Select another vSwitch from the VPC.
Ignore this parameter if the IPsec-VPN connection uses the single-tunnel mode.
Maximum Bandwidth: Specify the maximum bandwidth for the VPN gateway. The bandwidth is used for data transfer over the Internet.
Traffic: By default, the VPN gateway uses the pay-by-data-transfer metering method. For more information, see Billing.
IPsec-VPN: You can enable or disable the IPsec-VPN feature. After you enable this feature, you can establish connections between a data center and a VPC or between two VPCs. In this example, Enable is selected.
SSL-VPN: You can enable or disable the SSL-VPN feature. After you enable this feature, you can connect to the VPC from a client regardless of the location. In this example, Disable is selected.
Duration: By default, the VPN gateway is billed on an hourly basis.
Service-linked Role: Click Create Service-linked Role and the system automatically creates the service-linked role AliyunServiceRoleForVpn.
For more information, see AliyunServiceRoleForVpn. If Created is displayed, it indicates that the service-linked role is already created and you do not need to create it again.
Return to the VPN Gateways page, check and record the public IP address of the VPN gateway for further route configuration for the data center.
A newly created VPN gateway is in the Preparing state. After about 1 to 5 minutes, it enters the Normal state. The Normal state indicates that the VPN gateway is initialized and ready for use.
Create a customer gateway.
In the left-side navigation pane, choose .
On the Customer Gateway page, click Create Customer Gateway.
In the Create Customer Gateway panel, set the following parameters and click OK.
Name: Enter a name for the customer gateway.
IP Address: Enter the public IP address of the gateway device in the data center that you want to connect to VPC2. In this example, 211.XX.XX.68 is used.
ASN: Enter the ASN of the gateway device in the data center. This parameter is not set in this example.
Description: Enter a description for the customer gateway.
Create an IPsec-VPN connection.
In the left-side navigation pane, choose .
On the IPsec-VPN connection page, click Create IPsec-VPN Connection.
On the Create IPsec-VPN Connection page, set the parameters for the IPsec-VPN connection, and click OK.
Name: Enter a name for the IPsec-VPN connection.
Associate Resource: Select the type of network resource to be associated with the IPsec-VPN connection. In this example, VPN Gateway is selected.
VPN Gateway: Select the VPN gateway that you created.
Customer Gateway: Select the customer gateway you created.
Routing Mode: Select a routing mode. In this example, Destination Routing Mode is selected.
Effective Immediately: Select whether to immediately start negotiations. In this example, No is selected.
Yes: starts negotiations after the configuration is completed.
No: starts negotiations when inbound traffic is detected.
Pre-Shared Key: Enter the pre-shared key. The pre-shared key of the gateway device in the data center must be the same as this value. In this example, a random value is used by default.
Encryption Configuration: In this example, IKEv1 is used and the other parameters use the default settings.
For more information, see Create and manage an IPsec-VPN connection in single-tunnel mode.
Configure routes on the VPN gateway.
You must use the VPN gateway to advertise the routes of the data center to VPC2.
After an IPsec-VPN connection is created, click OK in the Established dialog box and advertise the routes on the VPN gateway.
In the left-side navigation pane, choose .
On the VPN Gateways page, find the VPN gateway you created and click the ID.
On the Destination-based Route Table tab, click Add Route Entry.
In the Add Route Entry panel, set the following parameters and click OK.
Destination CIDR Block: Enter the CIDR block of the data center. In this example, 172.16.0.0/16 is used.
Next Hop Type: Select IPsec-VPN connection.
Next Hop: Select the IPsec-VPN connection you created.
Advertise to VPC: Specify whether to automatically advertise new routes to the route table of VPC2. In this example, Yes is selected.
Weight: Select a weight for the route. In this example, 100 is used, which indicates a high priority.
NoteIf the VPN gateway contains routes that have the same destination CIDR block, you cannot specify the weights of these routes to 100 at the same time.
Add the VPN configurations to the data center gateway.
In the left-side navigation pane, choose .
On the IPsec Connections page, find the IPsec-VPN connection and click Generate Peer Configuration in the Actions column.
Add the IPsec connection configurations to the data center gateway. For more information, see Configure an on-premises gateway device.
Step 3: Configure a CEN instance
After you configure the Express Connect circuit and VPN gateway, you must attach VPC1, VPC2 and the VBR to a Cloud Enterprise Network (CEN) instance. The CEN instance can connect the data center to VPC1.
Create a CEN instance.
Log on to the CEN console.
On the Instances page, click Create CEN Instance.
In the Create CEN Instance dialog box, configure the following parameters and click OK:
Name: Enter a name for the CEN instance.
Description: Enter a description for the CEN instance.
Create a transit router.
Create a transit router in the region to which the VPC and VBR belong. The transit router is used to connect the VPC and VBR to CEN.
On the Instances page, click the ID of the CEN instance that you want to manage.
Choose and click Create Transit Router.
In the Create Transit Router dialog box, set the parameters and click OK.
Create a transit router in the China (Hangzhou) region based on the following information.
Parameter
Description
China (Hangzhou)
Region
Select the region where you want to create the transit router.
China (Hangzhou) is selected in this example.
Edition
The edition of the transit router.
The transit router edition that is supported in the selected region is automatically displayed.
Activate Multicast
Specify whether to enable multicast.
In this example, the default setting is used. Multicast is disabled.
Name
Enter a name for the transit router.
In this example, a custom name is specified for the transit router.
Description
Enter a description for the transit router.
In this example, a custom description is specified for the transit router.
Transit Router CIDR
Enter a CIDR block for the transit router.
For more information, see Transit router CIDR blocks.
In this example, no CIDR block is specified for the transit router.
Attach VPC1 and VPC2 to the CEN instance.
On the Instances page, click the ID of the CEN instance that you want to manage.
On the tab, find the transit router in the China (Hangzhou) region and click Create Connection in the Actions column.
On the Connection with Peer Network Instance page, configure the following parameters and click OK:
The following table describes the parameters for VPC1 and VPC2. Connect VPC1 and VPC2 to the transit router based on the following information.
NoteThe first time you perform this operation, the system automatically creates the service-linked role AliyunServiceRoleForCEN. This role allows transit routers to create ENIs on vSwitches in VPCs. For more information, see AliyunServiceRoleForCEN.
Parameter
Description
VPC1
VPC2
Network Type
Select the type of network instance that you want to connect.
VPC
VPC
Region
The region where the desired VBR instance is deployed.
China (Hangzhou)
China (Hangzhou)
Transit Router
The ID of the transit router in the selected region is automatically displayed.
Resource Owner ID
Select the Alibaba Cloud account to which the network instance belongs.
Your Account
Your Account
Billing Method
Default value: Pay-As-You-Go.
For more information, see Billing.
Attachment Name
Enter a name for the network connection.
VPC1-test
VPC2-test
Networks
Select the ID of the network instance.
Select VPC1.
Select VPC2.
VSwitch
Select the vSwitches that are deployed in the zones of the transit router.
If the transit router (TR) supports only one zone in the current region, you need to select a vSwitch in the zone.
If the TR supports multiple zones in the current region, you need to select at least two vSwitches that reside in different zones. When the VPC and TR communicate, the vSwitches are used to implement zone-disaster recovery.
We recommend that you select a vSwitch in each zone to reduce the network latency and improve network performance because data can be transmitted over a shorter distance.
Make sure that each selected vSwitch has at least one idle IP address. If the VPC does not have a vSwitch in the zone supported by the TR or the vSwitch does not have an idle IP address, create a new vSwitch in the zone. For more information, see Create and manage a vSwitch.
For more information, see Create a VPC connection.
Select one vSwitch in Zone H and one vSwitch in Zone I.
Select one vSwitch in Zone H and one vSwitch in Zone I.
Advanced Settings
The following advanced features are selected by default. You can select or clear the advanced features based on business requirements.
Keep the default settings for VPC1 and VPC2. All advanced features are enabled for the VPCs.
Associate with Default Route Table of Transit Router
After this feature is enabled, the VPC connection is automatically associated with the default route table of the transit router. The transit router forwards the traffic of the VPC based on the default route table.
Propagate System Routes to Default Route Table of Transit Router
After this feature is enabled, the system routes of the VPC are advertised to the default route table of the transit router. This way, the VPC can communicate with other network instances that are connected to the transit router.
Automatically Creates Route That Points to Transit Router and Adds to All Route Tables of Current VPC
After this feature is enabled, the system automatically adds the following three routes to all route tables of the VPC: 10.0.0.0/8, 172.16.0.0/12, and 192.168.0.0/16. The next hops of the routes point to the VPC. The routes are used to forward traffic from the VPC to the transit router. By default, transit routers do not advertise routes to VPCs.
ImportantIf such a route is already in the route table of the VPC, the system cannot advertise this route. You must manually add a route that points to the VPC connection to the route table of the VPC. Otherwise, network communication cannot be established between the VPC and the transit router.
To check whether such routes exist, click Check Route below Advanced Settings.
Attach the VBR to the CEN instance.
On the Instances page, click the ID of the CEN instance that you want to manage.
On the tab, find the transit router in the China (Hangzhou) region and click Create Connection in the Actions column.
On the Connection with Peer Network Instance page, configure the following parameters and click OK:
Network Type: Select the type of network instance that you want to attach. In this example, Virtual Border Router (VBR) is selected.
Region: Select the region where the network instance is deployed. In this example, China (Hangzhou) is selected.
Transit Router: The system automatically displays the transit router ID in the current region.
Resource Owner ID: Select the Alibaba Cloud account to which the network instance belongs. Your Account is used in this example.
Attachment Name: Enter a name for the network instance. VBR is used in this example.
Networks: Select the ID of the network instance that you want to attach. In this example, the ID of the VBR is selected.
Advanced Settings: By default, the system automatically enables the following advanced features. In this example, the default settings are used.
Associate with Default Route Table of Transit Router
After this feature is enabled, the VBR connection is automatically associated with the default route table of the transit router. The transit router forwards the traffic of the VBR based on the default route table.
Propagate System Routes to Default Route Table of Transit Router
After this feature is enabled, the system routes of the VBR are advertised to the default route table of the transit router. This way, the VBR can communicate with other network instances that are connected to the transit router.
Propagate Routes to VBR
After this feature is enabled, the system automatically advertises the routes in the transit router route table that is associated with the VBR connection to the VBR.
Advertise the routes of the data center from VPC2 to CEN.
After you use the VPN gateway to advertise the routes of the data center to VPC2, the routes in VPC2 are in the NonPublished state by default. You must manually advertise the routes of the data center from VPC2 to CEN. This way, VPC1 can learn the routes of the data center from VPC2.
Log on to the CEN console.
On the Instances page, find the CEN instance that you want to manage and click its ID.
On the details page, find the transit router in the China (Hangzhou) region and click its ID.
On the transit router details page, click the Network Instance Route Table tab.
On the Network Instance Route Table tab, view the routes of VPC2, find the routes whose destination is the data center, and click Advertise in the Advertisement Status column.
In the PublishRoute message, click OK.
Configure health checks for the Express Connect circuit.
You must configure health checks for the Express Connect circuit. Probe packets are sent during the health check based on the interval that you specify. If a specified number of probe packets are consecutively lost within a period of time, the CEN instance routes traffic over the IPsec-VPN connection.
Log on to the CEN console.
In the left-side navigation pane, click Health Check.
On the Health Check page, select the region of the VBR and click Set Health Check.
On the Set Health Check page, set the parameters and click OK.
Instances: Select the CEN instance to which the VBR is attached.
Virtual Border Router (VBR): Select the VBR that you want to monitor.
Source IP: In this example, Automatic IP Address is selected.
If you select Automatic IP Address, the system automatically allocates IP addresses in the 100.96.0.0/16 CIDR block to probe the connectivity of the Express Connect circuit.
Destination IP: Enter the IP address on the customer side of the VBR.
Probe Interval (Seconds): Specify the time interval at which probe packets are sent for health checks. Unit: seconds. In this example, the default value is used.
Probe Packets: Specify the number of probe packets that are sent at each interval. Unit: clients. The default value is used in this example.
Change Route: Specify whether to enable the route switching feature. In this example, the default setting is used. The route switching feature is enabled.
This feature is enabled by default. If a redundant route is configured on the CEN instance, the health check feature immediately switches to the redundant route if an error is detected on the Express Connect circuit.
If you disable this feature, health checks only perform probing. If an error is detected on the Express Connect circuit, the route is not switched.
WarningBefore you clear the check box, make sure that network traffic can be switched to a redundant route by using other mechanisms. Otherwise, network connections are interrupted if the Express Connect circuit fails.
Step 4: Configure the data center gateway
The following sample code is provided only for reference. The commands may vary with different vendors. Contact your vendor to obtain the information about specific commands.
#Configure BGP dynamic routing, establish a BGP peering connection to the VBR, and advertise the routes of the data center to Alibaba Cloud.
interface GigabitEthernet 0/12 #The port is used to connect the gateway device of the data center to the Express Connect circuit.
no switchport
ip address 10.1.0.2 255.255.255.252 #The IP address of the port. The IP address must be the same as the IPv4 address of the VBR on the customer side.
router bgp 65530
bgp router-id 10.1.0.2
network 172.16.0.0 mask 255.255.0.0 #Advertise the routes of the data center to Alibaba Cloud.
neighbor 10.1.0.1 remote-as 45104 #Establish a peering connection to the VBR.
exit
#Set the priority of the route that points to VPC1 through the VPN gateway. The priority must be lower than that of the BGP route.
ip route 192.168.0.0 255.255.0.0 <The public IP address of the VPN gateway> preference 255
# Configure a reverse route for probe packets.
ip route <The source IP address for the health check> 255.255.255.255 10.1.0.1
Step 5: Test the network connectivity
Open the command-line interface (CLI) on a client in the data center.
Run the
pingcommand to ping the IP address of an ECS instance in VPC1. The IP address of the ECS instance falls within the 192.168.0.0/16 CIDR block. If the client receives a response packet, it indicates that the data center is connected to VPC1.On the data center gateway, disable the port of the Express Connect circuit and stop the Express Connect circuit connection. Run the
pingcommand on the client again to test the connectivity between the data center and VPC1. If you receive a response packet, it indicates that the standby IPsec-VPN connection is working as expected.