To establish an IPsec-VPN connection between a data center and a virtual private cloud (VPC) on Alibaba Cloud, you must configure a VPN gateway on Alibaba Cloud and add VPN configurations to a gateway device in the data center. This topic describes how to add VPN configurations to an H3C firewall in dual-tunnel and single-tunnel modes.
We recommend that you add VPN configurations to an H3C firewall in dual-tunnel mode. For more information about the dual-tunnel mode, see [Upgrade notice] IPsec-VPN connections support the dual-tunnel mode.
Dual-tunnel mode
Scenario

Scenario description:
An enterprise has a data center and allocates the CIDR block 10.34.0.0/24 of the data center for communication with Alibaba Cloud.
The enterprise has deployed a VPC on Alibaba Cloud. The VPC CIDR block is 192.168.0.0/16. Applications are deployed on an Elastic Compute Service (ECS) instance in the VPC.
The enterprise plans to establish an IPsec-VPN connection in dual-tunnel mode between the data center and the VPC on Alibaba Cloud to enable communication between the data center and the VPC.
IP address plan
This section describes the following two sample scenarios based on the number of Internet egresses on the H3C firewall:
Single egress: The H3C firewall is configured with only one Internet egress, which maps to a public IP address.
Dual egresses: The H3C firewall is configured with two Internet egresses, each with a public IP address.
Refer to an appropriate IP address plan based on the device configurations in your data center.
Single egress
The following table describes the IP address plan.
Location | Configuration item | Example |
Data center | H3C firewall IP addresses | Gigabit Ethernet (GE) interface 2 (Internet egress): 10.32.0.175 Next hop: 10.32.0.173 Mapped public IP address: 8.XX.XX.3 |
GE interface 4 (private interface): 10.34.0.20 | ||
Private CIDR block | 10.34.0.0/24 | |
Server IP address | 10.34.0.21 | |
Alibaba Cloud | VPN gateway IP addresses | Active tunnel: 39.XX.XX.17 Standby tunnel: 39.XX.XX.10 |
VPC CIDR block | 192.168.0.0/16 | |
vSwitch CIDR blocks | Zone J: 192.168.1.0/24 Zone K: 192.168.2.0/24 | |
ECS instance IP address | 192.168.1.11 |
Dual egresses
The following table describes the IP address plan.
Location | Configuration item | Example |
Data center | H3C firewall IP addresses | GE interface 2 (Internet Egress 1): 10.32.0.175 Next hop: 10.32.0.173 Mapped public IP address: 8.XX.XX.3 |
GE interface 3 (Internet Egress 2): 10.33.0.238 Next hop: 10.33.0.236 Mapped public IP address: 116.XX.XX.68 | ||
GE interface 4 (private interface): 10.34.0.20 | ||
Private CIDR block | 10.34.0.0/24 | |
Server IP address | 10.34.0.21 | |
Alibaba Cloud | VPN gateway IP addresses | Active tunnel: 39.XX.XX.17 Standby tunnel: 39.XX.XX.10 |
VPC CIDR block | 192.168.0.0/16 | |
vSwitch CIDR blocks | Zone J: 192.168.1.0/24 Zone K: 192.168.2.0/24 | |
ECS instance IP address | 192.168.1.11 |
BGP plan
This topic describes how to configure an H3C firewall for an IPsec-VPN connection that uses static routing or Border Gateway Protocol (BGP) dynamic routing. If you do not need to use BGP dynamic routing, skip this section. The following table describes the CIDR block plan for BGP dynamic routing.
Resource | Tunnel | BGP tunnel CIDR block | BGP IP address | BGP local ASN |
Alibaba Cloud VPN gateway | Tunnel 1 | 169.254.10.0/30 Note On a VPN gateway, the CIDR block of each tunnel must be unique. | 169.254.10.1 | 65535 |
Tunnel 2 | 169.254.20.0/30 | 169.254.20.1 | ||
H3C firewall | Tunnel 1 | 169.254.10.0/30 | 169.254.10.2 | 65500 |
Tunnel 2 | 169.254.20.0/30 | 169.254.20.2 |
IPsec-VPN connection configuration plan
In dual-tunnel mode, Tunnel 1 serves as the active tunnel and Tunnel 2 serves as the standby tunnel. The two tunnels use the same sample values.
The IPsec-VPN connection configurations on Alibaba Cloud and the H3C firewall must be the same for each tunnel.
Configuration item | Example | |
Pre-shared key | ChangeMe**** | |
Internet Key Exchange (IKE) configurations | Version | ikev2 |
Negotiation mode | main | |
Encryption algorithm | aes256 | |
Authentication algorithm | sha256 | |
Diffie-Hellman (DH) group | group14 | |
Security association (SA) lifetime (seconds) | 86400 | |
IPsec configurations | Encryption algorithm | aes256 |
Authentication algorithm | sha256 | |
DH group | group14 | |
SA lifetime (seconds) | 86400 | |
Prerequisites
A VPN gateway, a customer gateway, and an IPsec-VPN connection are created on Alibaba Cloud, and routes are added on the VPN gateway.
For more information about static routing, see Connect a VPC to a data center in dual-tunnel mode.
For more information about BGP dynamic routing, see Connect a VPC to a data center in dual-tunnel mode and enable BGP dynamic routing.
Different customer gateway configurations are required in single-egress and dual-egress scenarios:
In the single-egress scenario, you need to create only one customer gateway. When you create an IPsec-VPN connection, use the same customer gateway for the active and standby tunnels.
In the dual-egress scenario, you need to create two customer gateways. When you create an IPsec-VPN connection, use a separate customer gateway for each of the active and standby tunnels.
Procedure
In this example, H3C SecPath vFW1000 E1185 is used. The firewall configurations may vary with different models and versions. You can refer to the relevant documentation or consult the firewall manufacturer to configure the firewall based on the version of the firewall that you use.
This section provides configuration examples in four scenarios. Refer to an appropriate configuration procedure based on the device configurations in your data center.
Single egress and static routing
In the single-egress scenario, you can bind the single egress of an H3C firewall to two tunnel interfaces and configure different IPsec profiles for the tunnel interfaces to connect to the active and standby tunnels on Alibaba Cloud.
Step 1: Configure interfaces and networking
Separately configure an IP address and a security zone for the public and private interfaces of the H3C firewall, and add routes on the H3C firewall.
# Configure a public interface.
interface GigabitEthernet 2/0
ip addr 10.32.0.175 24
quit
# Configure a private interface.
interface GigabitEthernet 4/0
ip addr 10.34.0.10 24
quit
# Add the public and private interfaces to their respective security zone.
security-zone name Untrust
import interface GigabitEthernet 2/0
quit
security-zone name Trust
import interface GigabitEthernet 4/0
quit
# Configure routes for the public IP addresses of the peer VPN gateway on Alibaba Cloud, with the next hop pointing to the gateway IP address that routes traffic to the Internet.
ip route-static 39.XX.XX.17 32 10.32.0.173
ip route-static 39.XX.XX.10 32 10.32.0.173
# Configure a route for the CIDR block of the local internal network, with the next hop pointing to the gateway IP address that routes traffic to the internal network.
ip route-static 10.0.0.0 8 10.34.0.253Step 2: Configure tunnels
Create two tunnel interfaces to connect to the active and standby tunnels on Alibaba Cloud.
# Configure the tunnel interfaces and apply IPsec to the tunnel interfaces.
interface tunnel 1 mode ipsec
ip address unnumbered interface GigabitEthernet 2/0
quit
interface tunnel 2 mode ipsec
ip address unnumbered interface GigabitEthernet 2/0
quit
# Add the tunnel interfaces to the Untrust security zone.
security-zone name Untrust
import interface Tunnel 1
import interface Tunnel 2
quitStep 3: Configure an IPsec proposal and related policies
Configure IPsec and IKE. The IPsec and IKE configurations must be consistent with those on the Alibaba Cloud side.
# Configure an IPsec proposal.
ipsec transform-set to-ali-trans
encapsulation-mode tunnel
protocol esp
esp authentication-algorithm sha256
esp encryption-algorithm aes-cbc-256
pfs dh-group14
quit
# Configure an IKEv2 proposal and an IKEv2 policy.
ikev2 proposal to-ali-prop
dh group14
encryption aes-cbc-256
integrity sha256
prf sha256
quit
ikev2 policy to-ali-policy
priority 1
proposal to-ali-prop
quit
# Configure IKEv2 keychains. Specify the active and standby tunnels on Alibaba Cloud as the two peers. Set the address parameter to the public IP addresses of the active and standby tunnels on Alibaba Cloud.
ikev2 keychain to_ali_key1
peer to-ali-peer1
address 39.XX.XX.17 32
identity address 39.XX.XX.17
pre-shared-key plaintext ChangeMe****
quit
quit
ikev2 keychain to_ali_key2
peer to-ali-peer2
address 39.XX.XX.10 32
identity address 39.XX.XX.10
pre-shared-key plaintext ChangeMe****
quit
quit
# Configure IKEv2 profiles. Specify the active and standby tunnels on Alibaba Cloud as the two peers.
ikev2 profile to-ali-profile1
authentication-method local pre-share
authentication-method remote pre-share
keychain to_ali_key1
identity local address 8.XX.XX.3
match remote identity address 39.XX.XX.17 32
sa duration 86400
dpd interval 30 periodic
quit
ikev2 profile to-ali-profile2
authentication-method local pre-share
authentication-method remote pre-share
keychain to_ali_key2
identity local address 8.XX.XX.3
match remote identity address 39.XX.XX.10 32
sa duration 86400
dpd interval 30 periodic
quit
# Configure IPsec profiles and reference the preceding IKEv2 profiles.
# We recommend that you specify only the time-based SA lifetime. If you specify the traffic-based SA lifetime, set it to the maximum value.
ipsec profile to-ali-profile1 isakmp
transform-set to-ali-trans
ikev2-profile to-ali-profile1
sa duration time-based 86400
quit
ipsec profile to-ali-profile2 isakmp
transform-set to-ali-trans
ikev2-profile to-ali-profile2
sa duration time-based 86400
quit
# Configure the tunnel interfaces and apply the IPsec profiles to the tunnel interfaces.
interface tunnel 1 mode ipsec
ip address unnumbered interface GigabitEthernet 2/0
tunnel protection ipsec profile to-ali-profile1
source 10.32.0.175
destination 39.XX.XX.17
quit
interface tunnel 2 mode ipsec
ip address unnumbered interface GigabitEthernet 2/0
tunnel protection ipsec profile to-ali-profile2
source 10.32.0.175
destination 39.XX.XX.10
quit
# Configure routes for the peer VPC CIDR block to point to the tunnel interfaces. Tunnel 1 serves as the active tunnel and has a higher priority than Tunnel 2.
ip route-static 192.168.0.0 16 Tunnel 1 preference 10
ip route-static 192.168.0.0 16 Tunnel 2 preference 20Step 4: Configure an ACL
Configure an access control list (ACL) to allow IKE protocol traffic and IPsec data traffic.
In this example, the configurations are simplified. You can configure a fine-grained ACL based on your business requirements.
If you want to connect multiple CIDR blocks of the data center to the VPC, we recommend that you connect the data center to the H3C firewall in destination-based routing mode. For more information, see the "Recommended solutions" section of the Configuration suggestions and FAQ about enabling communication among CIDR blocks topic.
# Configure an ACL to allow IKE negotiation packets and IPsec data packets between the Untrust security zone and any other zone. In this example, the configurations are simplified. You can configure a fine-grained ACL based on your business requirements.
acl advanced 3001
rule 0 permit ip
quit
zone-pair security source any destination any
packet-filter 3001
quitStep 5: Verify results
After you add routes from the server in the data center to the H3C firewall, you can test the network connectivity between the data center and the VPC on Alibaba Cloud from the data center. You can also verify whether a switchover can be performed between the active and standby tunnels.
Test the network connectivity between the VPC and data center.
Log on to an ECS instance in the VPC. For more information about how to log on to an ECS instance, see Connection method overview.
Run the
pingcommand on the ECS instance to ping a server in the data center to test the accessibility of the data center.If an echo reply packet is returned to the ECS instance, it indicates that the VPC can communicate with the data center.
ping <Private IP address of a server in the data center>
Test high availability of the IPsec-VPN connection.
Log on to an ECS instance in the VPC. For more information about how to log on to an ECS instance, see Connection method overview.
Run the following command to consecutively send packets from the ECS instance to the data center:
ping <Private IP address of a server in the data center> -c 10000Close the active tunnel of the IPsec-VPN connection.
You can close the active tunnel by modifying the pre-shared key of the active tunnel. The active tunnel is closed when the two sides of the tunnel use different pre-shared keys.
After the active tunnel is closed, you can check the traffic status on the ECS instance. If the traffic is interrupted and then resumed, it indicates that the standby tunnel automatically takes over after the active tunnel is down.
Single egress and BGP dynamic routing
In the single-egress scenario, you can bind the single egress of an H3C firewall to two tunnel interfaces and configure different IPsec profiles for the tunnel interfaces to connect to the active and standby tunnels on Alibaba Cloud.
Step 1: Configure interfaces and networking
Separately configure an IP address and a security zone for the public and private interfaces of the H3C firewall, and add routes on the H3C firewall.
# Configure a public interface.
interface GigabitEthernet 2/0
ip addr 10.32.0.175 24
quit
# Configure a private interface.
interface GigabitEthernet 4/0
ip addr 10.34.0.10 24
quit
# Add the public and private interfaces to their respective security zone.
security-zone name Untrust
import interface GigabitEthernet 2/0
quit
security-zone name Trust
import interface GigabitEthernet 4/0
quit
# Configure routes for the public IP addresses of the peer VPN gateway on Alibaba Cloud, with the next hop pointing to the gateway IP address that routes traffic to the Internet.
ip route-static 39.XX.XX.17 32 10.32.0.173
ip route-static 39.XX.XX.10 32 10.32.0.173
# Configure a route for the CIDR block of the local internal network, with the next hop pointing to the gateway IP address that routes traffic to the internal network.
ip route-static 10.0.0.0 8 10.34.0.253Step 2: Configure tunnels
Create two tunnel interfaces to connect to the active and standby tunnels on Alibaba Cloud.
# Configure the tunnel interfaces and apply IPsec to the tunnel interfaces.
interface tunnel 1 mode ipsec
ip address unnumbered interface GigabitEthernet 2/0
quit
interface tunnel 2 mode ipsec
ip address unnumbered interface GigabitEthernet 2/0
quit
# Add the tunnel interfaces to the Untrust security zone.
security-zone name Untrust
import interface Tunnel 1
import interface Tunnel 2
quitStep 3: Configure an IPsec proposal and related policies
Configure IPsec and IKE. The IPsec and IKE configurations must be consistent with those on the Alibaba Cloud side.
# Configure an IPsec proposal.
ipsec transform-set to-ali-trans
encapsulation-mode tunnel
protocol esp
esp authentication-algorithm sha256
esp encryption-algorithm aes-cbc-256
pfs dh-group14
quit
# Configure an IKEv2 proposal and an IKEv2 policy.
ikev2 proposal to-ali-prop
dh group14
encryption aes-cbc-256
integrity sha256
prf sha256
quit
ikev2 policy to-ali-policy
priority 1
proposal to-ali-prop
quit
# Configure IKEv2 keychains. Specify the active and standby tunnels on Alibaba Cloud as the two peers. Set the address parameter to the public IP addresses of the active and standby tunnels on Alibaba Cloud.
ikev2 keychain to_ali_key1
peer to-ali-peer1
address 39.XX.XX.17 32
identity address 39.XX.XX.17
pre-shared-key plaintext ChangeMe****
quit
quit
ikev2 keychain to_ali_key2
peer to-ali-peer2
address 39.XX.XX.10 32
identity address 39.XX.XX.10
pre-shared-key plaintext ChangeMe****
quit
quit
# Configure IKEv2 profiles. Specify the active and standby tunnels on Alibaba Cloud as the two peers.
ikev2 profile to-ali-profile1
authentication-method local pre-share
authentication-method remote pre-share
keychain to_ali_key1
identity local address 8.XX.XX.3
match remote identity address 39.XX.XX.17 32
sa duration 86400
dpd interval 30 periodic
quit
ikev2 profile to-ali-profile2
authentication-method local pre-share
authentication-method remote pre-share
keychain to_ali_key2
identity local address 8.XX.XX.3
match remote identity address 39.XX.XX.10 32
sa duration 86400
dpd interval 30 periodic
quit
# Configure IPsec profiles and reference the preceding IKEv2 profiles.
# We recommend that you specify only the time-based SA lifetime. If you specify the traffic-based SA lifetime, set it to the maximum value.
ipsec profile to-ali-profile1 isakmp
transform-set to-ali-trans
ikev2-profile to-ali-profile1
sa duration time-based 86400
quit
ipsec profile to-ali-profile2 isakmp
transform-set to-ali-trans
ikev2-profile to-ali-profile2
sa duration time-based 86400
quit
# Configure the tunnel interfaces and apply the IPsec profiles to the tunnel interfaces.
interface tunnel 1 mode ipsec
ip address unnumbered interface GigabitEthernet 2/0
tunnel protection ipsec profile to-ali-profile1
source 10.32.0.175
destination 39.XX.XX.17
quit
interface tunnel 2 mode ipsec
ip address unnumbered interface GigabitEthernet 2/0
tunnel protection ipsec profile to-ali-profile2
source 10.32.0.175
destination 39.XX.XX.10
quit
# Configure routes for the peer VPC CIDR block to point to the tunnel interfaces. Tunnel 1 serves as the active tunnel and has a higher priority than Tunnel 2.
ip route-static 192.168.0.0 16 Tunnel 1 preference 10
ip route-static 192.168.0.0 16 Tunnel 2 preference 20Step 4: Configure an ACL
Configure an ACL to allow IKE protocol traffic and IPsec data traffic.
In this example, the configurations are simplified. You can configure a fine-grained ACL based on your business requirements.
If you want to connect multiple CIDR blocks of the data center to the VPC, we recommend that you connect the data center to the H3C firewall in destination-based routing mode. For more information, see the "Recommended solutions" section of the Configuration suggestions and FAQ about enabling communication among CIDR blocks topic.
# Configure an ACL to allow IKE negotiation packets and IPsec data packets between the Untrust security zone and any other zone. In this example, the configurations are simplified. You can configure a fine-grained ACL based on your business requirements.
acl advanced 3001
rule 0 permit ip
quit
zone-pair security source any destination any
packet-filter 3001
quitStep 5: Configure BGP dynamic routing
# Configure IP addresses for the tunnel interfaces to establish BGP peering with the VPN gateway on Alibaba Cloud.
interface tunnel 1 mode ipsec
ip address 169.254.10.2 30
quit
interface tunnel 2 mode ipsec
ip address 169.254.20.2 30
quit
# Delete the static routes that point to the tunnels in the static routing scenario.
undo ip route-static 192.168.0.0 16 Tunnel 1 preference 10
undo ip route-static 192.168.0.0 16 Tunnel 2 preference 20
# Configure BGP dynamic routing. The H3C firewall advertises 10.0.0.0/8 to the VPN gateway on Alibaba Cloud.
bgp 65500
peer 169.254.10.1 as-number 65535
peer 169.254.20.1 as-number 65535
address-family ipv4 unicast
peer 169.254.10.1 enable
peer 169.254.20.1 enable
network 10.0.0.0 8 # Advertise the CIDR block 10.0.0.0/8.After the configuration is complete, check the BGP connection.
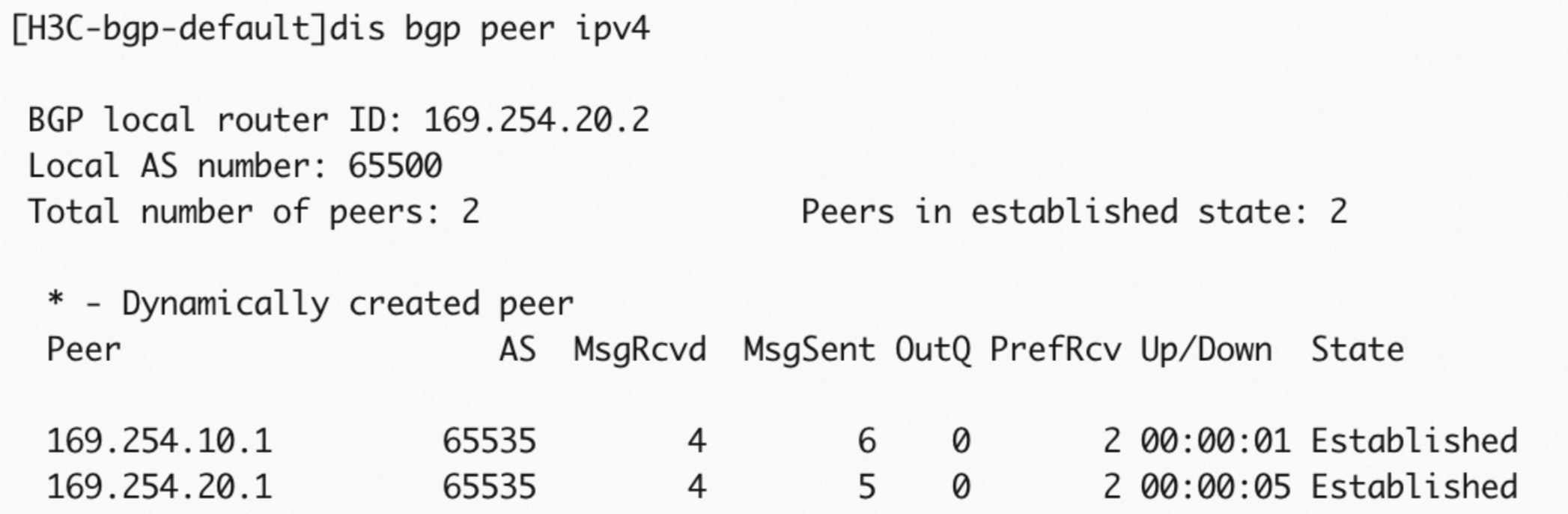
Check the BGP dynamic routing.
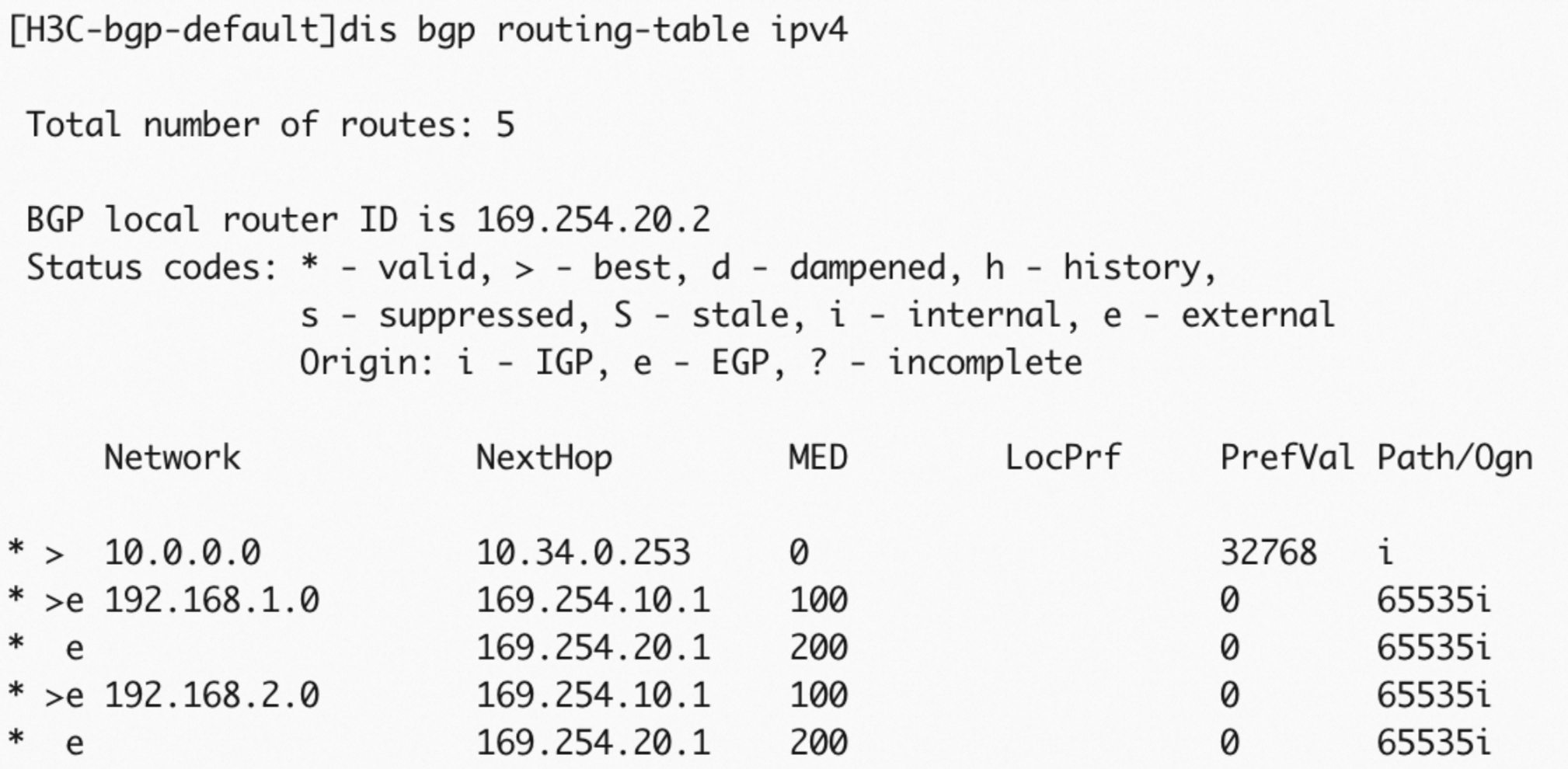
Check the route table.
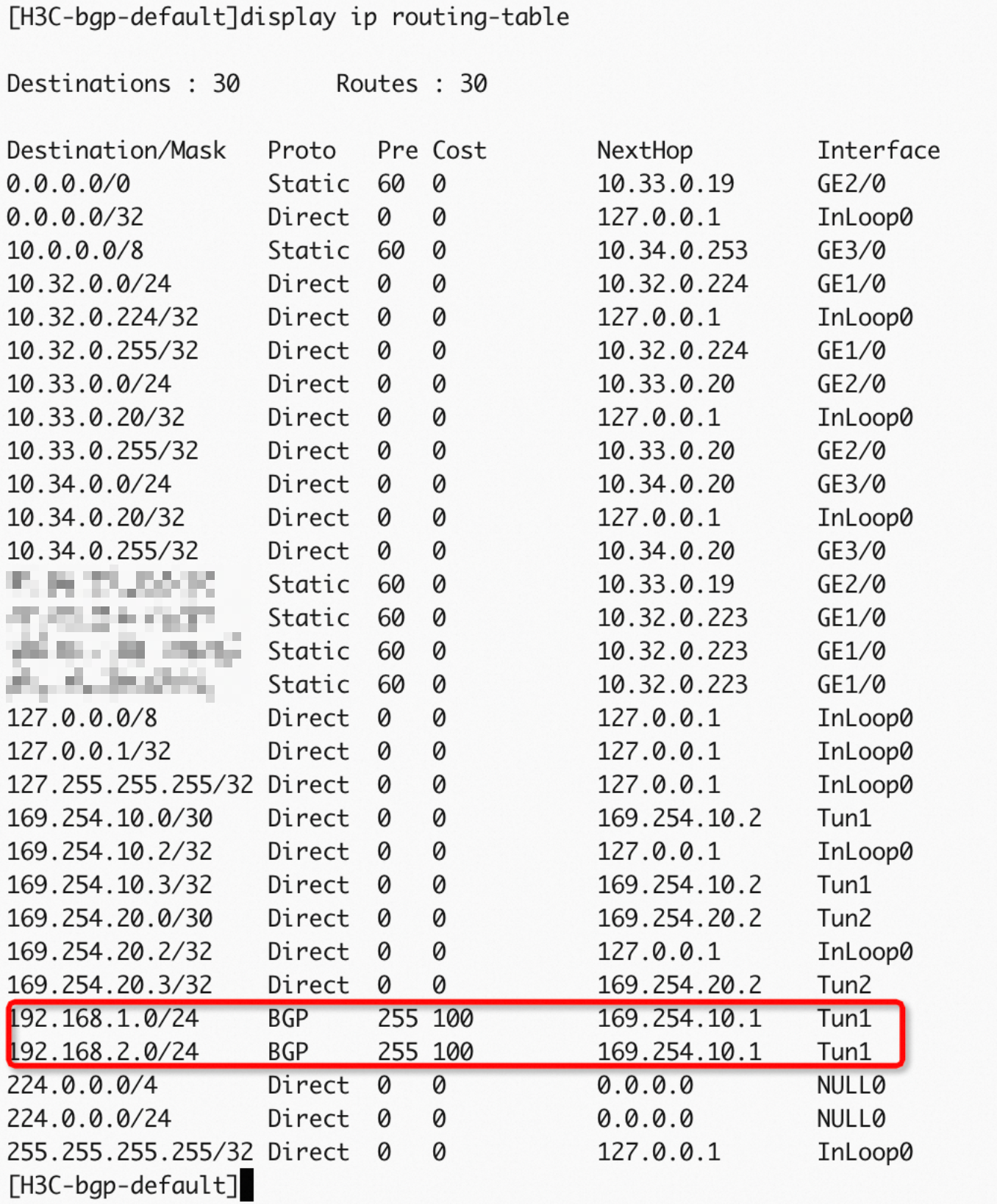
Step 6: Verify results
After you add routes from the client in the data center to the H3C firewall, you can test the network connectivity between the data center and the VPC on Alibaba Cloud from the data center. You can also verify whether a switchover can be performed between the active and standby tunnels.
Test the network connectivity between the VPC and data center.
Log on to an ECS instance in the VPC. For more information about how to log on to an ECS instance, see Connection method overview.
Run the
pingcommand on the ECS instance to ping a server in the data center to test the accessibility of the data center.If an echo reply packet is returned to the ECS instance, it indicates that the VPC can communicate with the data center.
ping <Private IP address of a server in the data center>
Test high availability of the IPsec-VPN connection.
Log on to an ECS instance in the VPC. For more information about how to log on to an ECS instance, see Connection method overview.
Run the following command to consecutively send packets from the ECS instance to the data center:
ping <Private IP address of a server in the data center> -c 10000Close the active tunnel of the IPsec-VPN connection.
You can close the active tunnel by modifying the pre-shared key of the active tunnel. The active tunnel is closed when the two sides of the tunnel use different pre-shared keys.
After the active tunnel is closed, you can check the traffic status on the ECS instance. If the traffic is interrupted and then resumed, it indicates that the standby tunnel automatically takes over after the active tunnel is down.
Dual egresses and static routing
In the dual-egress scenario, you can bind two egresses of an H3C firewall to two tunnel interfaces and configure different IPsec profiles for the tunnel interfaces to connect to the active and standby tunnels on Alibaba Cloud.
Step 1: Configure interfaces and networking
Separately configure an IP address and a security zone for the public and private interfaces of the H3C firewall, and add routes on the H3C firewall.
# Configure Public Interface 1.
interface GigabitEthernet 2/0
ip addr 10.32.0.175 24
quit
# Configure Public Interface 2.
interface GigabitEthernet 3/0
ip addr 10.33.0.238 24
quit
# Configure a private interface.
interface GigabitEthernet 4/0
ip addr 10.34.0.10 24
quit
# Add the public and private interfaces to their respective security zone.
security-zone name Untrust
import interface GigabitEthernet 2/0
import interface GigabitEthernet 3/0
quit
security-zone name Trust
import interface GigabitEthernet 4/0
quit
# Configure 32-bit routes for the public IP addresses of the peer VPN gateway on Alibaba Cloud, with the next hops pointing to the gateway IP addresses that route traffic to the Internet.
ip route-static 39.XX.XX.17 32 10.32.0.173
ip route-static 39.XX.XX.10 32 10.33.0.236
# Configure a route for the CIDR block of the local internal network, with the next hop pointing to the gateway IP address that routes traffic to the internal network.
ip route-static 10.0.0.0 8 10.34.0.253
Step 2: Configure tunnels
Create two tunnel interfaces to connect to the active and standby tunnels on Alibaba Cloud.
# Configure the tunnel interfaces and apply IPsec to the tunnel interfaces.
interface tunnel 1 mode ipsec
ip address unnumbered interface GigabitEthernet 2/0
quit
interface tunnel 2 mode ipsec
ip address unnumbered interface GigabitEthernet 3/0
quit
# Add the tunnel interfaces to the Untrust security zone.
security-zone name Untrust
import interface Tunnel 1
import interface Tunnel 2
quitStep 3: Configure an IPsec proposal and related policies
Configure IPsec and IKE. The IPsec and IKE configurations must be consistent with those on the Alibaba Cloud side.
# Configure an IPsec proposal.
ipsec transform-set to-ali-trans
encapsulation-mode tunnel
protocol esp
esp authentication-algorithm sha256
esp encryption-algorithm aes-cbc-256
pfs dh-group14
quit
# Configure an IKEv2 proposal and an IKEv2 policy.
ikev2 proposal to-ali-prop
dh group14
encryption aes-cbc-256
integrity sha256
prf sha256
quit
ikev2 policy to-ali-policy
priority 1
proposal to-ali-prop
quit
# Configure IKEv2 keychains. Specify the active and standby tunnels on Alibaba Cloud as the two peers. Set the address parameter to the public IP addresses of the active and standby tunnels on Alibaba Cloud.
ikev2 keychain to_ali_key1
peer to-ali-peer1
address 39.XX.XX.17 32
identity address 39.XX.XX.17
pre-shared-key plaintext ChangeMe****
quit
quit
ikev2 keychain to_ali_key2
peer to-ali-peer2
address 39.XX.XX.10 32
identity address 39.XX.XX.10
pre-shared-key plaintext ChangeMe****
quit
quit
# Configure IKEv2 profiles. Specify the active and standby tunnels on Alibaba Cloud as the two peers.
ikev2 profile to-ali-profile1
authentication-method local pre-share
authentication-method remote pre-share
keychain to_ali_key1
identity local address 8.XX.XX.3
match remote identity address 39.XX.XX.17 32
sa duration 86400
dpd interval 30 periodic
quit
ikev2 profile to-ali-profile2
authentication-method local pre-share
authentication-method remote pre-share
keychain to_ali_key2
identity local address 116.XX.XX.68
match remote identity address 39.XX.XX.10 32
sa duration 86400
dpd interval 30 periodic
quit
# Configure IPsec profiles and reference the preceding IKEv2 profiles.
# We recommend that you specify only the time-based SA lifetime. If you specify the traffic-based SA lifetime, set it to the maximum value.
ipsec profile to-ali-profile1 isakmp
transform-set to-ali-trans
ikev2-profile to-ali-profile1
sa duration time-based 86400
quit
ipsec profile to-ali-profile2 isakmp
transform-set to-ali-trans
ikev2-profile to-ali-profile2
sa duration time-based 86400
quit
# Configure the tunnel interfaces and apply the IPsec profiles to the tunnel interfaces.
interface tunnel 1 mode ipsec
ip address unnumbered interface GigabitEthernet 2/0
tunnel protection ipsec profile to-ali-profile1
source 10.32.0.175
destination 39.XX.XX.17
quit
interface tunnel 2 mode ipsec
ip address unnumbered interface GigabitEthernet 3/0
tunnel protection ipsec profile to-ali-profile2
source 10.33.0.238
destination 39.XX.XX.10
quit
# Configure routes for the peer VPC CIDR block to point to the tunnel interfaces. Tunnel 1 serves as the active tunnel and has a higher priority than Tunnel 2.
ip route-static 192.168.0.0 16 Tunnel 1 preference 10
ip route-static 192.168.0.0 16 Tunnel 2 preference 20Step 4: Configure an ACL
Configure an ACL to allow IKE protocol traffic and IPsec data traffic.
In this example, the configurations are simplified. You can configure a fine-grained ACL based on your business requirements.
If you want to connect multiple CIDR blocks of the data center to the VPC, we recommend that you connect the data center to the H3C firewall in destination-based routing mode. For more information, see the "Recommended solutions" section of the Configuration suggestions and FAQ about enabling communication among CIDR blocks topic.
# Configure an ACL to allow IKE negotiation packets and IPsec data packets between the Untrust security zone and any other zone. In this example, the configurations are simplified. You can configure a fine-grained ACL based on your business requirements.
acl advanced 3001
rule 0 permit ip
quit
zone-pair security source any destination any
packet-filter 3001
quitStep 5: Verify results
After you add routes from the client in the data center to the H3C firewall, you can test the network connectivity between the data center and the VPC on Alibaba Cloud from the data center. You can also verify whether a switchover can be performed between the active and standby tunnels.
Test the network connectivity between the VPC and data center.
Log on to an ECS instance in the VPC. For more information about how to log on to an ECS instance, see Connection method overview.
Run the
pingcommand on the ECS instance to ping a server in the data center to test the accessibility of the data center.If an echo reply packet is returned to the ECS instance, it indicates that the VPC can communicate with the data center.
ping <Private IP address of a server in the data center>
Test high availability of the IPsec-VPN connection.
Log on to an ECS instance in the VPC. For more information about how to log on to an ECS instance, see Connection method overview.
Run the following command to consecutively send packets from the ECS instance to the data center:
ping <Private IP address of a server in the data center> -c 10000Close the active tunnel of the IPsec-VPN connection.
You can close the active tunnel by modifying the pre-shared key of the active tunnel. The active tunnel is closed when the two sides of the tunnel use different pre-shared keys.
After the active tunnel is closed, you can check the traffic status on the ECS instance. If the traffic is interrupted and then resumed, it indicates that the standby tunnel automatically takes over after the active tunnel is down.
Dual egresses and BGP dynamic routing
In the dual-egress scenario, you can bind two egresses of an H3C firewall to two tunnel interfaces and configure different IPsec profiles for the tunnel interfaces to connect to the active and standby tunnels on Alibaba Cloud.
Step 1: Configure interfaces and networking
Separately configure an IP address and a security zone for the public and private interfaces of the H3C firewall, and add routes on the H3C firewall.
# Configure Public Interface 1.
interface GigabitEthernet 2/0
ip addr 10.32.0.175 24
quit
# Configure Public Interface 2.
interface GigabitEthernet 3/0
ip addr 10.33.0.238 24
quit
# Configure a private interface.
interface GigabitEthernet 4/0
ip addr 10.34.0.10 24
quit
# Add the public and private interfaces to their respective security zone.
security-zone name Untrust
import interface GigabitEthernet 2/0
import interface GigabitEthernet 3/0
quit
security-zone name Trust
import interface GigabitEthernet 4/0
quit
# Configure 32-bit routes for the public IP addresses of the peer VPN gateway on Alibaba Cloud, with the next hops pointing to the gateway IP addresses that route traffic to the Internet.
ip route-static 39.XX.XX.17 32 10.32.0.173
ip route-static 39.XX.XX.10 32 10.33.0.236
# Configure a route for the CIDR block of the local internal network, with the next hop pointing to the gateway IP address that routes traffic to the internal network.
ip route-static 10.0.0.0 8 10.34.0.253
Step 2: Configure tunnels
Create two tunnel interfaces to connect to the active and standby tunnels on Alibaba Cloud.
# Configure the tunnel interfaces and apply IPsec to the tunnel interfaces.
interface tunnel 1 mode ipsec
ip address unnumbered interface GigabitEthernet 2/0
quit
interface tunnel 2 mode ipsec
ip address unnumbered interface GigabitEthernet 3/0
quit
# Add the tunnel interfaces to the Untrust security zone.
security-zone name Untrust
import interface Tunnel 1
import interface Tunnel 2
quitStep 3: Configure an IPsec proposal and related policies
Configure IPsec and IKE. The IPsec and IKE configurations must be consistent with those on the Alibaba Cloud side.
# Configure an IPsec proposal.
ipsec transform-set to-ali-trans
encapsulation-mode tunnel
protocol esp
esp authentication-algorithm sha256
esp encryption-algorithm aes-cbc-256
pfs dh-group14
quit
# Configure an IKEv2 proposal and an IKEv2 policy.
ikev2 proposal to-ali-prop
dh group14
encryption aes-cbc-256
integrity sha256
prf sha256
quit
ikev2 policy to-ali-policy
priority 1
proposal to-ali-prop
quit
# Configure IKEv2 keychains. Specify the active and standby tunnels on Alibaba Cloud as the two peers. Set the address parameter to the public IP addresses of the active and standby tunnels on Alibaba Cloud.
ikev2 keychain to_ali_key1
peer to-ali-peer1
address 39.XX.XX.17 32
identity address 39.XX.XX.17
pre-shared-key plaintext ChangeMe****
quit
quit
ikev2 keychain to_ali_key2
peer to-ali-peer2
address 39.XX.XX.10 32
identity address 39.XX.XX.10
pre-shared-key plaintext ChangeMe****
quit
quit
# Configure IKEv2 profiles. Specify the active and standby tunnels on Alibaba Cloud as the two peers.
ikev2 profile to-ali-profile1
authentication-method local pre-share
authentication-method remote pre-share
keychain to_ali_key1
identity local address 8.XX.XX.3
match remote identity address 39.XX.XX.17 32
sa duration 86400
dpd interval 30 periodic
quit
ikev2 profile to-ali-profile2
authentication-method local pre-share
authentication-method remote pre-share
keychain to_ali_key2
identity local address 116.XX.XX.68
match remote identity address 39.XX.XX.10 32
sa duration 86400
dpd interval 30 periodic
quit
# Configure IPsec profiles and reference the preceding IKEv2 profiles.
# We recommend that you specify only the time-based SA lifetime. If you specify the traffic-based SA lifetime, set it to the maximum value.
ipsec profile to-ali-profile1 isakmp
transform-set to-ali-trans
ikev2-profile to-ali-profile1
sa duration time-based 86400
quit
ipsec profile to-ali-profile2 isakmp
transform-set to-ali-trans
ikev2-profile to-ali-profile2
sa duration time-based 86400
quit
# Configure the tunnel interfaces and apply the IPsec profiles to the tunnel interfaces.
interface tunnel 1 mode ipsec
ip address unnumbered interface GigabitEthernet 2/0
tunnel protection ipsec profile to-ali-profile1
source 10.32.0.175
destination 39.XX.XX.17
quit
interface tunnel 2 mode ipsec
ip address unnumbered interface GigabitEthernet 3/0
tunnel protection ipsec profile to-ali-profile2
source 10.33.0.238
destination 39.XX.XX.10
quit
# Configure routes for the peer VPC CIDR block to point to the tunnel interfaces. Tunnel 1 serves as the active tunnel and has a higher priority than Tunnel 2.
ip route-static 192.168.0.0 16 Tunnel 1 preference 10
ip route-static 192.168.0.0 16 Tunnel 2 preference 20Step 4: Configure an ACL
Configure an ACL to allow IKE protocol traffic and IPsec data traffic.
In this example, the configurations are simplified. You can configure a fine-grained ACL based on your business requirements.
If you want to connect multiple CIDR blocks of the data center to the VPC, we recommend that you connect the data center to the H3C firewall in destination-based routing mode. For more information, see the "Recommended solutions" section of the Configuration suggestions and FAQ about enabling communication among CIDR blocks topic.
# Configure an ACL to allow IKE negotiation packets and IPsec data packets between the Untrust security zone and any other zone. In this example, the configurations are simplified. You can configure a fine-grained ACL based on your business requirements.
acl advanced 3001
rule 0 permit ip
quit
zone-pair security source any destination any
packet-filter 3001
quitStep 5: Configure BGP dynamic routing
# Configure IP addresses for the tunnel interfaces to establish BGP peering with the VPN gateway on Alibaba Cloud.
interface tunnel 1 mode ipsec
ip address 169.254.10.2 30
quit
interface tunnel 2 mode ipsec
ip address 169.254.20.2 30
quit
# Delete the static routes that point to the tunnels in the static routing scenario.
undo ip route-static 192.168.0.0 16 Tunnel 1 preference 10
undo ip route-static 192.168.0.0 16 Tunnel 2 preference 20
# Configure BGP dynamic routing. The H3C firewall advertises 10.0.0.0/8 to the VPN gateway on Alibaba Cloud.
bgp 65500
peer 169.254.10.1 as-number 65535
peer 169.254.20.1 as-number 65535
address-family ipv4 unicast
peer 169.254.10.1 enable
peer 169.254.20.1 enable
network 10.0.0.0 8 # Advertise the CIDR block 10.0.0.0/8.After the configuration is complete, check the BGP connection.

Check the BGP dynamic routing.

Check the route table.

Step 6: Verify results
After you add routes from the client in the data center to the H3C firewall, you can test the network connectivity between the data center and the VPC on Alibaba Cloud from the data center. You can also verify whether a switchover can be performed between the active and standby tunnels.
Test the network connectivity between the VPC and data center.
Log on to an ECS instance in the VPC. For more information about how to log on to an ECS instance, see Connection method overview.
Run the
pingcommand on the ECS instance to ping a server in the data center to test the accessibility of the data center.If an echo reply packet is returned to the ECS instance, it indicates that the VPC can communicate with the data center.
ping <Private IP address of a server in the data center>
Test high availability of the IPsec-VPN connection.
Log on to an ECS instance in the VPC. For more information about how to log on to an ECS instance, see Connection method overview.
Run the following command to consecutively send packets from the ECS instance to the data center:
ping <Private IP address of a server in the data center> -c 10000Close the active tunnel of the IPsec-VPN connection.
You can close the active tunnel by modifying the pre-shared key of the active tunnel. The active tunnel is closed when the two sides of the tunnel use different pre-shared keys.
After the active tunnel is closed, you can check the traffic status on the ECS instance. If the traffic is interrupted and then resumed, it indicates that the standby tunnel automatically takes over after the active tunnel is down.
