This topic provides answers to some frequently asked questions about enabling communication among CIDR blocks by using IPsec-VPN and provides configuration suggestions.
Configuration suggestions
If you want to establish an IPsec-VPN connection to enable communication between CIDR blocks, we recommend that you use IKEv2.
NoteIf the peer gateway device does not support IKEv2, you can configure the IPsec-VPN connection and the peer gateway device to use IKEv1. In scenarios where IPsec-VPN connections use IKEv1, you can configure only one local CIDR block and one peer CIDR block for each IPsec-VPN connection. For more information, see the Recommended solutions section of this topic.
If the peer gateway device is provided by Cisco or H3C, we recommend that you use the following configurations:
The IPsec-VPN connection on Alibaba Cloud supports only one value for each of Encryption Algorithm, Authentication Algorithm, and DH Group in IKE Configurations and IPsec Configurations. Make sure that only one value is set for each of Encryption Algorithm, Authentication Algorithm, and DH Group (PFS) in IKE Configurations and IPsec Configurations of the peer gateway device.
If the Dead Peer Detection (DPD) feature is enabled for the IPsec-VPN connection, the customer gateway device must be configured with standard DPD settings.
The security association (SA) lifetime configured for the IPsec-VPN connection must be the same as that of the peer gateway device.
If the peer gateway device allows you to set its traffic-based SA lifetime, you need to set it to the maximum value, which is 0 bytes for some device suppliers.
Recommended solutions
When you connect a data center to a virtual private cloud (VPC) to enable communication among CIDR blocks, we recommend that you use the following solutions.
Solution | Applicable IKE version | Description | Benefit or limit | Configuration example |
Solution 1 (recommended) |
| Use one IPsec-VPN connection to connect the data center to the VPC. Set the routing mode of the IPsec-VPN connection to the destination-based routing mode, and set the source CIDR block and destination CIDR block of Protected Data Flows of the peer gateway device to | Benefits:
| |
Solution 2 (second choice) |
| Use one IPsec-VPN connection to connect the data center to the VPC. Aggregate the data center-side CIDR blocks into one CIDR block and the VPC-side CIDR blocks into another. Then, configure an aggregate route for the IPsec-VPN connection and the peer gateway device. | Limits: If you want to add or delete CIDR blocks, you may need to configure a new aggregate route and modify the configurations of the IPsec-VPN connection and the peer gateway device. The modifications will cause IPsec renegotiation, which results in temporary traffic interruptions. | |
Method 3 |
| Establish multiple IPsec-VPN connections between the data center and the VPC. Each CIDR block uses one IPsec-VPN connection to communicate with another CIDR block. The IPsec-VPN connections must meet the following requirements:
Note If multiple IPsec-VPN connections are associated with the same VPN gateway and customer gateway, and use the same Internet Key Exchange (IKE) version, the IPsec-VPN connections share the same Phase 1 negotiation. In scenarios where multiple IPsec-VPN connections share the same Phase 1 negotiation, the IPsec-VPN connections must have the same Pre-Shared Key and IKE Configurations, including the Version, Negotiation Mode, Encryption Algorithm, Authentication Algorithm, DH Group, and SA Life Cycle (seconds) (in seconds). This ensures that the IKE Configurations of each IPsec-VPN connection can be shared during IPsec negotiations. | Limits: If you want to modify CIDR blocks, you need to modify the configurations of the IPsec-VPN connection and customer gateway device. The modifications will cause IPsec renegotiation, which results in temporary traffic interruptions. |
Configuration examples
Configuration examples of Solution 1
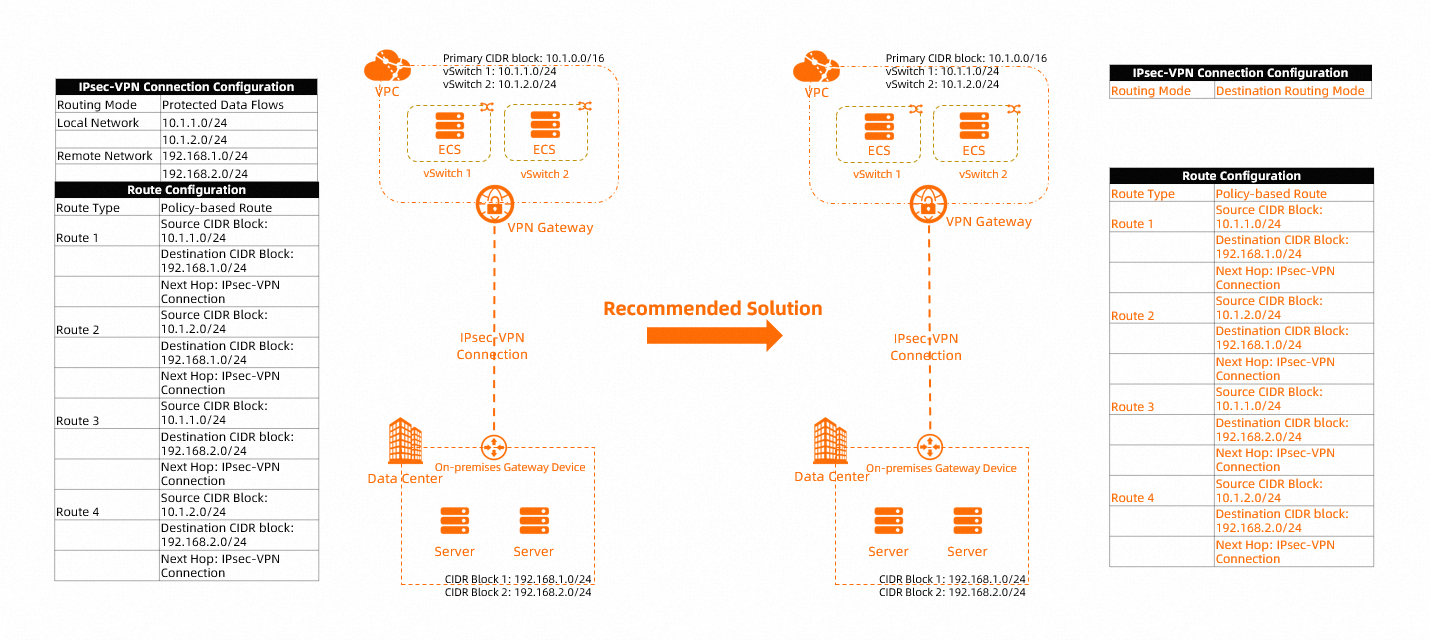
The scenario shown in the following figure is used in this topic. In this scenario, the VPC CIDR blocks 10.1.1.0/24 and 10.1.2.0/24 need to communicate with the data center CIDR blocks 192.168.1.0/24 and 192.168.2.0/24. We recommend that you use the following configurations:
When you configure an IPsec-VPN connection on Alibaba Cloud, set Routing Mode to Destination Routing Mode. For more information, see the Create an IPsec-VPN connection section of the "Create and manage IPsec-VPN connections in single-tunnel mode" topic.
When you configure routes for the VPN gateway, we recommend that you use policy-based routes. For more information, see Configure policy-based routes.
Add a protected data flow whose source CIDR block and destination CIDR block are both 0.0.0.0/0 to the on-premises gateway device. For more information about the command, consult the supplier of the gateway device.
Configuration example of solution 2
Example 1
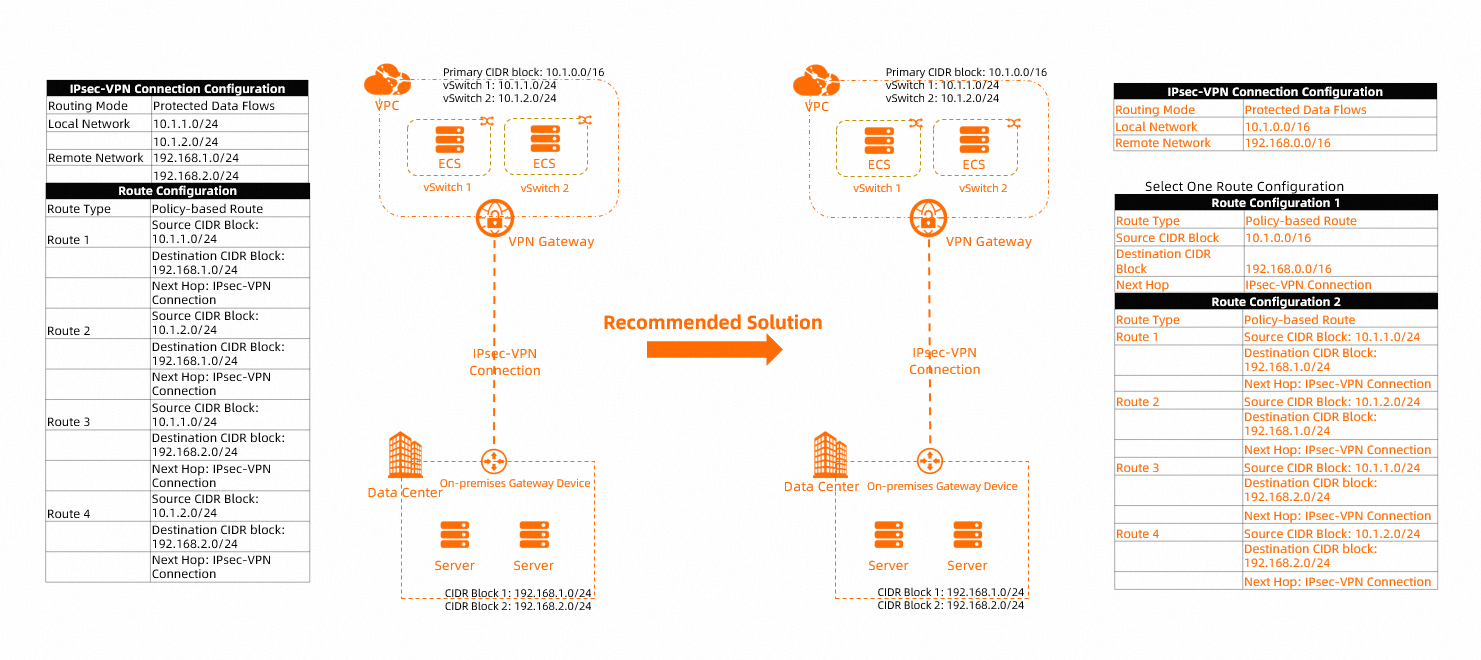
The scenario shown in the following figure is used in this topic. In this scenario, the VPC CIDR blocks 10.1.1.0/24 and 10.1.2.0/24 need to communicate with the data center CIDR blocks 192.168.1.0/24 and 192.168.2.0/24. We recommend that you use the following configurations:
When you configure an IPsec-VPN connection on Alibaba Cloud, set Routing Mode to Protected Data Flows, set Local Network to 10.1.0.0/16, which is an aggregate CIDR block of the VPC, and set Remote Network to 192.168.0.0/16, which is an aggregate CIDR block of the data center. For more information, see the Create an IPsec-VPN connection section of the "Create and manage IPsec-VPN connections in single-tunnel mode" topic.
After you set Routing Mode to Protected Data Flows, the system automatically adds a policy-based route whose next hop is the IPsec-VPN connection to the Policy-based Route Table. The Source CIDR Block of the policy-based route is the Local Network of the IPsec-VPN connection and the Destination CIDR Block is the Remote Network. By default, this policy-based route is not advertised to the VPC.
If you use the default policy-based route, you need to advertise the default policy-based route to the VPC. If you want to add a custom policy-based route, you must first delete the policy-based route that is automatically added by the system. For more information, see Configure policy-based routes.
Example 2
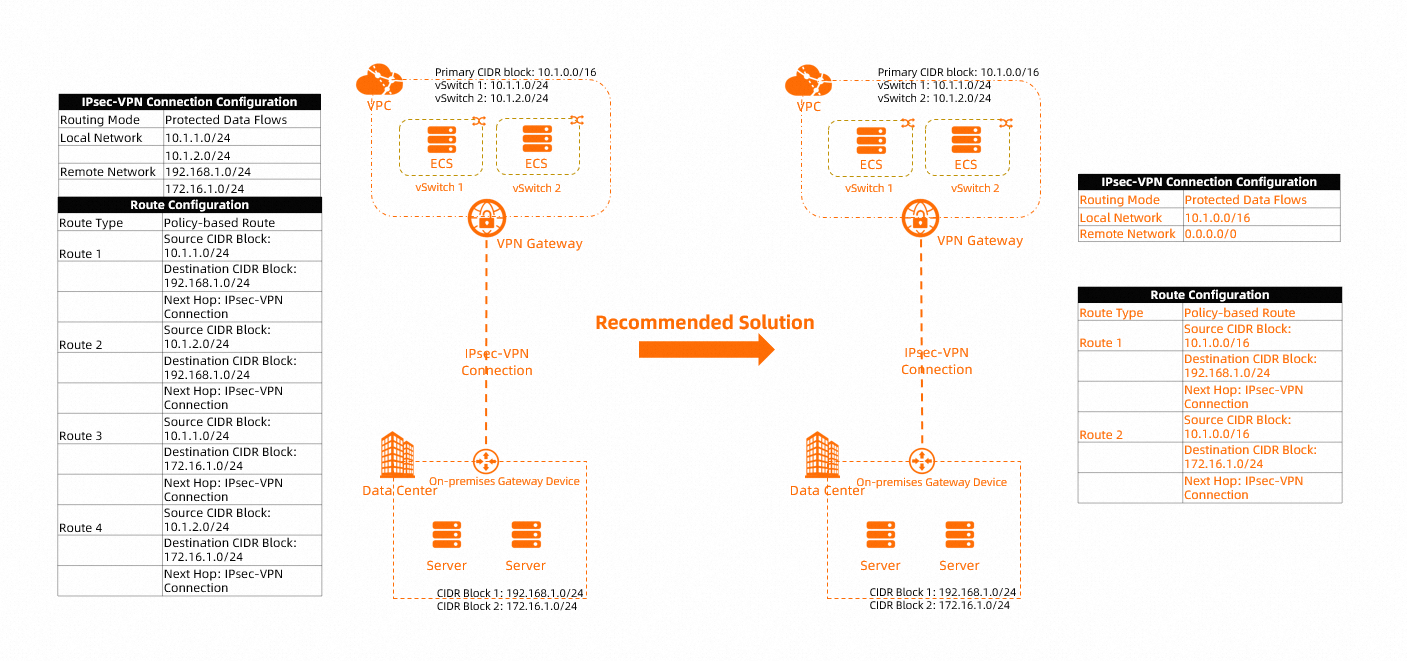
The scenario shown in the following figure is used in this topic. In this scenario, the VPC CIDR blocks 10.1.1.0/24 and 10.1.2.0/24 need to communicate with the data center CIDR blocks 192.168.1.0/24 and 172.16.1.0/24. We recommend that you use the following configurations:
When you configure an IPsec-VPN connection on Alibaba Cloud, set Routing Mode to Protected Data Flows, set Local Network to 10.1.0.0/16, which is an aggregate CIDR block of the VPC, and set Remote Network to 0.0.0.0/0. For more information, see the Create an IPsec-VPN connection section of the "Create and manage IPsec-VPN connections in single-tunnel mode" topic.
NoteThe CIDR blocks of the data center cannot be aggregated into one CIDR block. Therefore, we recommend that you set Remote Network to 0.0.0.0/0.
After you set Routing Mode to Protected Data Flows, the system automatically adds a policy-based route whose next hop is the IPsec-VPN connection to the Policy-based Route Table. The Source CIDR Block of the policy-based route is the Local Network of the IPsec-VPN connection and the Destination CIDR Block is the Remote Network. By default, this policy-based route is not advertised to the VPC.
We recommend that you do not configure a route whose destination CIDR block is 0.0.0.0/0 for the Policy-based Route Table. Instead, delete the policy-based route that is automatically added by the system and add a more specific policy-based route. For more information, see Configure policy-based routes.
Configuration examples of Solution 3
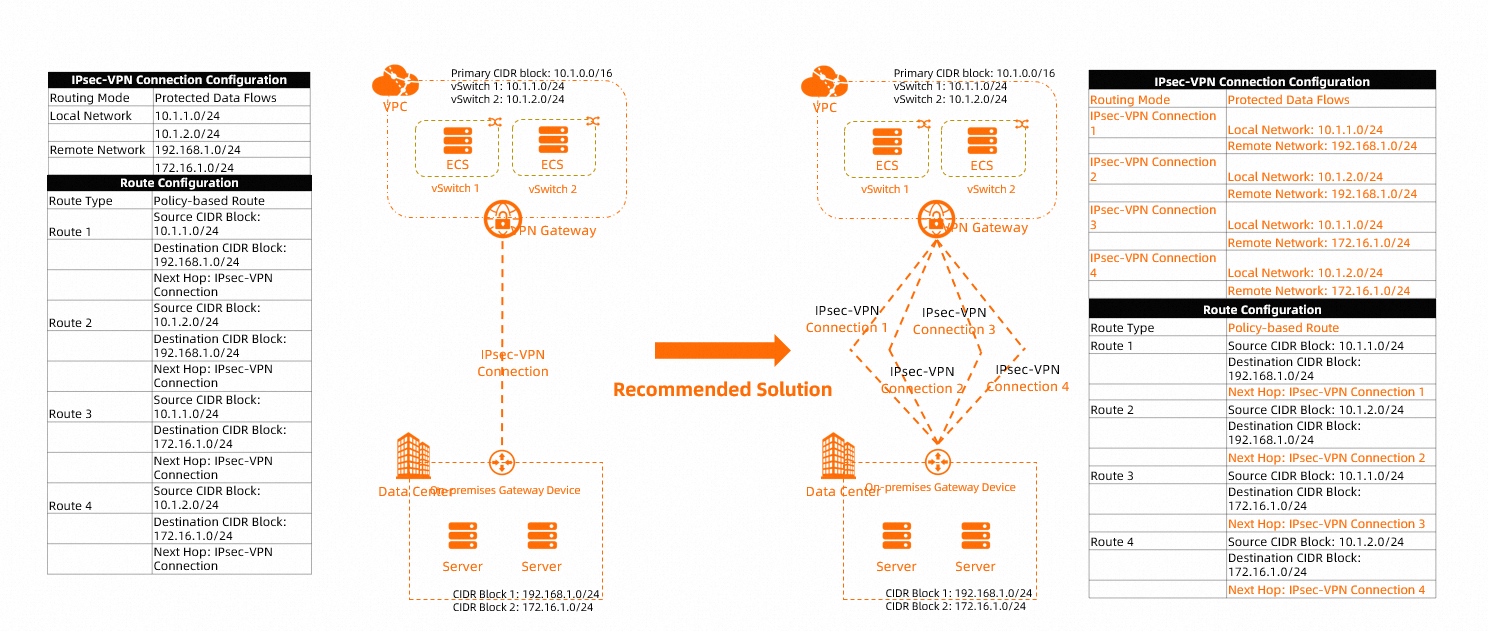
The scenario shown in the following figure is used in this topic. In this scenario, the VPC CIDR blocks 10.1.1.0/24 and 10.1.2.0/24 need to communicate with the data center CIDR blocks 192.168.1.0/24 and 172.16.1.0/24. We recommend that you use the following configurations:
Create multiple IPsec-VPN connections on Alibaba Cloud and set Routing Mode to Protected Data Flows for each IPsec-VPN connection. Specify one Local Network and one Remote Network for each IPsec-VPN connection. For more information, see the Create an IPsec-VPN connection section of the "Create and manage IPsec-VPN connections in single-tunnel mode" topic.
After you set Routing Mode to Protected Data Flows, the system automatically adds a policy-based route whose next hop is the IPsec-VPN connection to the Policy-based Route Table. The Source CIDR Block of the policy-based route is the Local Network of the IPsec-VPN connection and the Destination CIDR Block is the Remote Network. By default, this policy-based route is not advertised to the VPC.
You need to advertise the four policy-based routes that are automatically added by the system to the VPC. For more information, see Configure policy-based routes.
FAQ
Why does the system prompt that Phase 2 negotiations succeed but communication is successful only between some CIDR blocks?
Possible causes
In scenarios where a data center is connected to a VPC by using IPsec-VPN connections, if the peer gateway device is provided by Cisco or H3C, the routing mode of the IPsec-VPN connection is set to Protected Data Flows, and multiple CIDR blocks are specified, only one CIDR block can be used for communication.
This is because Alibaba Cloud VPN gateways are incompatible with the IPsec protocol used by the peer gateway device provided by Cisco or H3C. In this case, the Alibaba Cloud VPN gateway uses one SA to negotiate with the peer gateway device. However, the peer gateway device uses multiple SAs to negotiate with the VPN gateway.
Solutions
For more information, see the Recommended solutions section of this topic.
How do I enable communication among CIDR blocks if the on-premises gateway device does not support IKEv2?
If the on-premises gateway device does not support IKEv2, you can configure the IPsec-VPN connections and the on-premises gateway device to use IKEv1.
In scenarios where IPsec-VPN connections use IKEv1, you can configure only one local CIDR block and one peer CIDR block for each IPsec-VPN connection. For more information, see the Recommended solutions section of this topic.