資產暴露分析功能可以對阿里雲上的雲資源(例如ECS、網關資產、系統組件、連接埠、AI應用組件等)進行全面掃描和分析,識別出可能暴露在公網的安全風險和漏洞,協助您及時發現和解決問題,提高雲資源的安全性。本文介紹如何使用Security Center資產暴露分析功能。
版本限制
支援的資產類型
資產暴露分析功能支援統計阿里雲伺服器ECS、雲資料庫Tair(相容 Redis)、雲資料庫RDS和ApsaraDB for MongoDB在互連網上的暴露情況,不支援統計非阿里雲產品在互連網上的暴露情況。
統計資料說明
資產暴露分析結果會每天自動重新整理。Security Center的资产暴露分析頁面為您展示資產在互連網暴露情況的統計資料和詳細資料列表。下表為統計資料的說明。
統計項 | 說明 |
弱口令 | 暴露在互連網上的ECS伺服器以及資料庫系統弱口令的總數量。單擊相應數值,可查看存在弱口令的暴露資產列表。 |
可被利用漏洞 | 暴露在互連網上可被駭客利用的漏洞總數量,以及高危、中危、低危漏洞數量。單擊漏洞總數量可查看存在漏洞的資產列表。不同類型的漏洞使用不同顏色表示:
|
暴露资产/公网IP数 | 暴露在互連網上的Elastic Compute Service、雲資料庫Tair(相容 Redis)、雲資料庫RDS和ApsaraDB for MongoDB總數量,以及公網IP總數量。 |
网关资产 | 暴露在互連網上的網關資產(負載平衡、NAT Gateway)總數量。單擊相應數值開啟网关资产面板,可查看網關資產的列表。在网关资产面板,單擊網關資產名稱可跳轉至對應資產詳情頁面。 |
暴露連接埠 | 暴露在互連網上的連接埠總數量。單擊相應數值開啟暴露連接埠面板,可查看暴露連接埠的列表。在暴露連接埠面板,單擊暴露連接埠名稱查看存在該暴露連接埠的資產列表。 |
暴露組件 | 暴露在互連網上的您ECS伺服器的系統組件(例如OpenSSL、OpenSSH)總數量。單擊相應數值開啟暴露組件面板,可查看暴露組件的列表。在暴露組件面板,單擊暴露組件名稱查看存在該暴露組件的資產列表。 |
AI應用組件 | 暴露在互連網上的AI應用組件總數量。單擊相應數字開啟AI應用組件面板,可查看暴露AI組件的列表。在AI應用組件面板,單擊AI組件名稱查看存在該暴露AI應用組件的資產列表。 |
掃描資產暴露情況
前提條件
Elastic Compute Service已安裝Security Center用戶端且用戶端處於線上狀態,即主機資產頁面該ECS客戶端列顯示![]() 表徵圖。
表徵圖。
每天自動掃描
Security Center預設每天自動執行一次暴露資產的掃描任務,無需您手動設定。您可以在任務管理頁面,瞭解自動掃描任務的詳細資料。
手動一鍵掃描
需要立即查看最新的資產暴露情況時,您可以手動執行一鍵掃描操作。
在左側導覽列,選擇。在控制台左上方,選擇需防護資產所在的地區:中國內地或非中國內地。
在资产暴露分析頁面,單擊資產暴露掃描下的一鍵掃描。
查看掃描任務
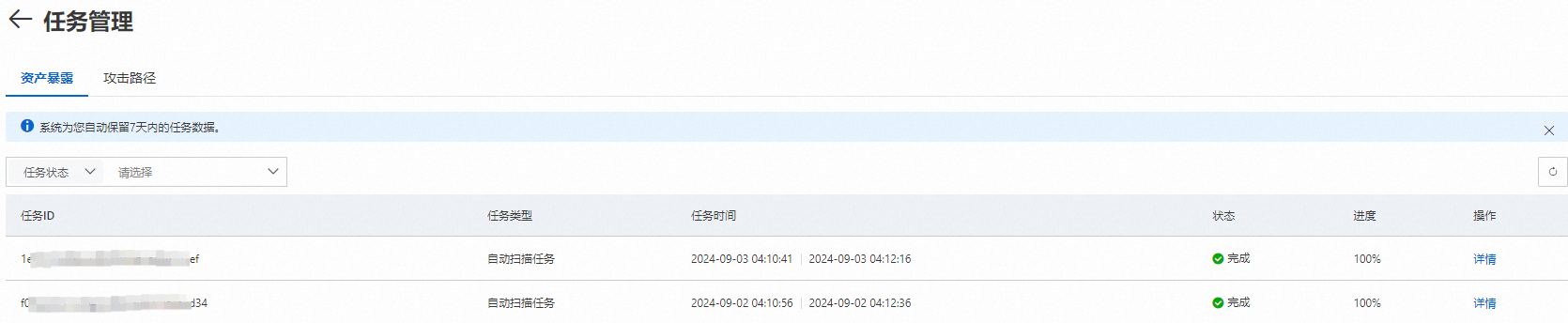
Security Center提供任務管理頁面,預設記錄7天內發起的自動和手動掃描任務。
在左側導覽列,選擇。在控制台左上方,選擇需防護資產所在的地區:中國內地或非中國內地。
在资产暴露分析頁面,單擊右上方的任務管理。
在任務管理頁面,您可以根據任務類型、狀態(未開始、執行中、等待資料擷取、資料擷取中、完成、逾時、終止或失敗)或任務時間,查看任務ID、任務類型、任務時間、狀態和進度百分比。
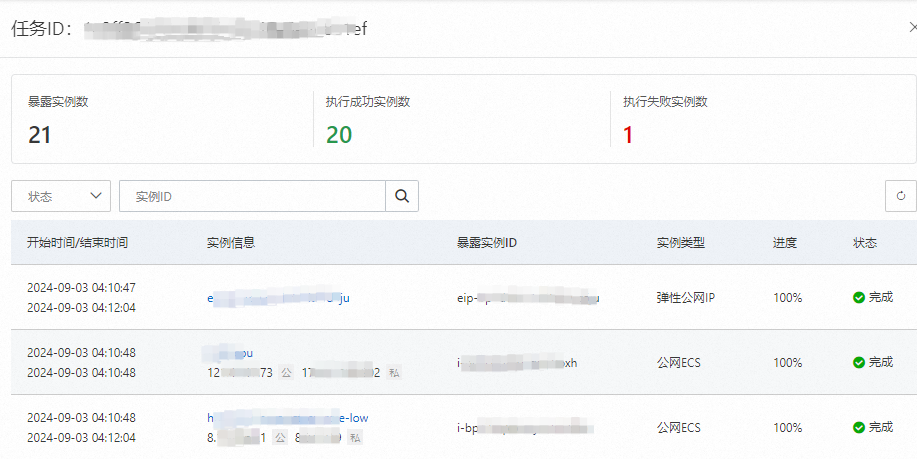
單擊目標任務的詳情,可查看本次掃描任務的暴露資產詳情,包括暴露執行個體數、執行成功執行個體數、執行失敗執行個體數以及資產執行個體列表。
支援根據狀態和資產執行個體ID篩選查看特定資產的掃描結果。
查看資產暴露詳情
在左側導覽列,選擇。在控制台左上方,選擇需防護資產所在的地區:中國內地或非中國內地。
在资产暴露分析頁面,查看資產暴露資訊。
查看資產暴露總覽資料
在资产暴露分析頁面上方總覽地區,您可以查看資產暴露的總體情況,包括弱口令、可被利用漏洞等總覽資料。單擊下方數字,可查看對應資料的詳情。
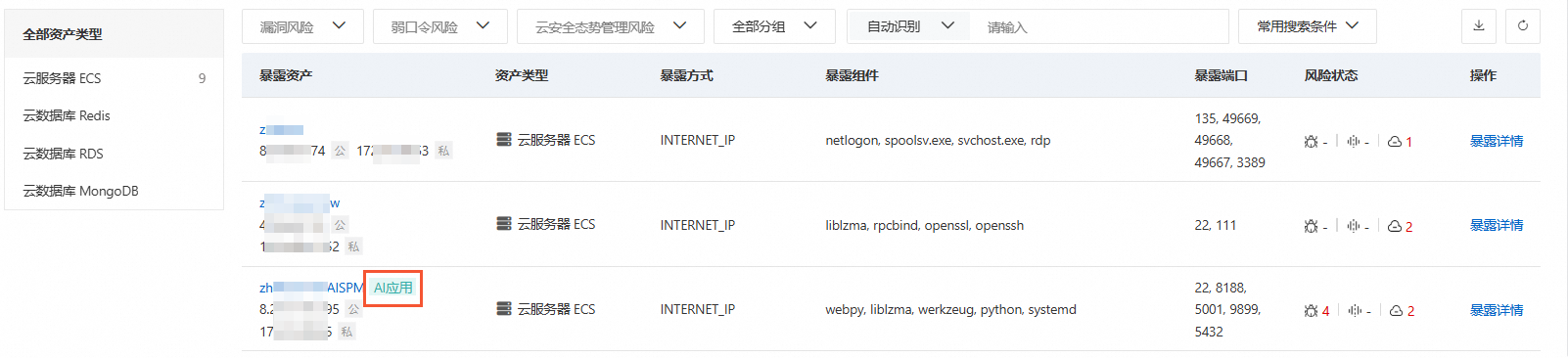
瞭解暴露資產列表
您可使用頁面提供的搜尋組件從有無漏洞、資產分組、連接埠等維度篩選查看資產暴露情況。
如果您的暴露資產處存在AI應用標籤,說明當前資產中存在對外暴露的AI組件。
瞭解資產暴露詳情
單擊要查看的資產操作列的暴露详情,可在資產的暴露詳情面板,查看資產暴露通訊鏈路拓撲圖、鏈路詳情和風險詳情。
在暴露詳情面板的上方,單擊資產下拉式清單,篩選並查看目標資產的暴露詳情。
查看風險詳情:
在弱口令頁簽,查看檢測出的弱口令詳情。您可以單擊檢測出的弱口令風險名稱,跳轉到該資產的基準檢查頁簽下,查看該資產上檢測出的所有基準風險。
駭客可能會利用您資產上的弱口令進行非法登入,竊取伺服器資料或破壞伺服器,建議您及時修複弱口令風險。
在可被利用漏洞、全部漏洞頁簽下,單擊漏洞連結,可跳轉漏洞詳情頁面。您可以查看漏洞資訊並根據漏洞修複建議手動修複相應漏洞。
建議您及時修複高危漏洞。
在風險配置頁簽下,單擊雲產品配置檢查風險項,可跳轉到雲產品頁面對應雲產品的詳情頁面。您可以查看雲安全態勢管理頁簽的風險項詳情並及時修複相應風險。
查看暴露鏈路:
如果您的ECS伺服器或資料庫資產可以通過多種方式訪問互連網,通訊鏈路拓撲圖會為您展示多條訪問互連網的路徑。
例如您的ECS伺服器可以通過NAT Gateway和負載平衡訪問公網,通訊鏈路拓撲圖將為您展示訪問互連網的兩條通訊鏈路。單擊不同訪問路徑上的資產表徵圖,可以切換到該路徑,查看該路徑詳情。
說明資產暴露通訊鏈路拓撲圖顏色和資產中存在的漏洞的等級的對應關係如下:
紅色:資產中存在弱口令風險或可被駭客通過互連網利用的高危漏洞。
橙色:資產中存在可被駭客通過互連網利用的中危漏洞。
灰色:資產中存在可被駭客通過互連網利用的低危漏洞。
綠色:資產中不存在弱口令風險或可被駭客通過互連網利用的漏洞。
以上拓撲圖顏色和漏洞等級的對應關係僅對您的資產生效,不對網路鏈路圖的其餘部分(例如互連網)生效,互連網表徵圖預設為灰色。
匯出資產暴露資料
您可以單擊暴露資產列表右上方
 表徵圖,將暴露資產的詳細資料統一匯出並儲存到本地。匯出的檔案為Excel格式。
表徵圖,將暴露資產的詳細資料統一匯出並儲存到本地。匯出的檔案為Excel格式。
相關文檔
如果您需要減少ECS在互連網的暴露面,可選擇使用下述解決方案。
如果您需要處理資產中檢測出的漏洞,可參考下述文檔處理。
如果您需修複系統中的弱口令,可參考下述文檔處理。