本文介紹Cloud Firewall執行個體基本資料、整體防護能力、統計資訊、流量拓撲可視化總覽資訊,協助您瞭解網路資產的安全狀況以及雲資產的互連網邊界流量和VPC邊界流量。
總覽
Cloud Firewall總覽頁簽向您展示了Cloud Firewall的整體防護能力和統計資訊,協助您瞭解網路資產的安全狀況。
通過總覽頁面,您可以集中查看已接入防護的全量資產、流量趨勢、安全事件等資料統計資訊。
Cloud Firewall執行個體通過 新加坡的管控平面實現管控。
在概覽頁簽,您可以查看如下資料。
地區名稱
說明
支援的操作
实例保护状态
該地區為您展示當前購買的Cloud Firewall版本,不同的版本展示的資訊有差異。
临时带宽升级:通過頻寬升級功能,按小時臨時調整公網流量和VPC流量的處理能力。達到設定的還原時間後,公網流量和VPC流量的處理能力將自動降低到升級前的規格。具體操作,請參見升級和降配。
升級:通過變更配置功能,提高Cloud Firewall的服務版本、調整服務規格。具體操作,請參見升級和降配。
續約:手動續約。具體操作,請參見續約說明。
自动续费:開通自動續約後,您購買的Cloud Firewall服務到期前9天,系統會自動扣款並在您餘額充足的情況下為您完成續約操作。具體操作,請參見續約說明。
釋放:Cloud Firewall執行個體到期前15天和到期後7天,支援手動釋放執行個體。具體操作,請參見釋放執行個體。
說明建議您在業務低峰期先關閉Cloud Firewall開關,確認業務無異常後,再釋放執行個體。
更多:包含公網的流量處理能力、近期流量峰值(近7天)、公網IP防護授權數;VPC的流量處理能力、近期流量峰值、VPC防火牆授權數;日誌審計儲存量;多帳號授權數。
待處理事件
該地區展示了近期Cloud Firewall在您已開啟防護的資產中發現的已失陷主機、待防护漏洞数、对外开放端口、異常外聯。
為您展示當前待處理的例外狀況事件,單擊立即处理,根據介面指示定位到指定的例外狀況事件並處理。
资产接入保护
該地區展示了您的資產保護情況,包含:
已開啟或未開啟互連網邊界防火牆防護的公網IP資產數量。
已建立和未建立的VPC邊界防火牆數量。
已建立和未建立的NAT防火牆數量。
主機邊界防火牆防護的安全性群組數量。
對於沒有開啟防護的資產,您可以單擊未防護的資產數量,跳轉到防火牆開關頁面,開啟對應的Cloud Firewall。更多資訊,請參見互連網邊界防火牆、(待下線)開啟或關閉VPC邊界防火牆、NAT邊界防火牆。
單擊地區右上方的查看明细和账单,將會跳轉到账单管理頁面,方便您查看已出賬單的明細。
安全防护
該地區展示了近期Cloud Firewall為您的資產觸發的安全防護的次數,包含防护总次数、入侵攻击拦截数、访问控制拦截数、漏洞攻击拦截数、敏感数据泄露事件数。
查看詳情:單擊展開,可以查看不同防護模組的資料詳情。
安全策略
該地區展示了存取控制策略的相關資料,包含待下发智能策略数、总ACL策略数(近7日的變化量)。
單擊待下發智能策略的數量,頁面將會跳轉到存取控制頁面的智能策略推薦面板,方便您查看和下發Cloud Firewall為您推薦的智能策略。具體操作,請參見智能策略。
單擊總ACL策略數的數量,頁面將會跳轉到存取控制頁面,方便您查看或操作每條策略。
近期更新
該地區展示了近期Cloud Firewall的虛擬補丁、基礎防禦和功能更新的更新記錄。
您可以單擊不同頁簽(虛擬補丁、基礎防禦、功能更新),查看對應的更新記錄。
流量趨勢
該地區展示了近期已開啟防護的資產上的互連網邊界防火牆和VPC邊界防火牆。Cloud Firewall隨用隨付版不支援流量趨勢。
互連網邊界防火牆:整體流量趨勢和Cloud Firewall在入方向、出方向攔截的會話數量的變化趨勢。
VPC邊界防火牆:VPC的流量變化趨勢和VPC攔截變化趨勢。
僅Cloud Firewall企業版和旗艦版的總覽頁支援VPC邊界防火牆。
如果您的業務實際流量超出購買的防護頻寬,Cloud Firewall只對防護頻寬範圍內的流量提供防護。對於超出防護頻寬的流量,Cloud Firewall預設不提供防護。此時,您需要擴充防護頻寬規格。具體操作,請參見升級和降配。
說明關於如何排查流量峰值異常的IP,請參見業務流量超出Cloud Firewall支援的頻寬規格怎麼辦?。
設定查詢時間:單擊右上方的時間下拉式清單,選擇待查詢的時間範圍。
查看互連網邊界防火牆的趨勢圖:
查看入方向和出方向的流量趨勢圖:在流量趨勢頁簽,將滑鼠懸浮在趨勢圖上,展示指定時間點入方向和出方向的流量明細。您可以單擊入方向峰值和出方向峰值右側的
 表徵圖。然後在顯示的氣泡中,單擊去查看,跳轉到公網暴露頁面和主動外聯頁面,查看具體的流量峰值資訊。
表徵圖。然後在顯示的氣泡中,單擊去查看,跳轉到公網暴露頁面和主動外聯頁面,查看具體的流量峰值資訊。入方向流量=公網暴露請求流量+公網暴露響應流量
入方向峰值指公網暴露總流量峰值,因為Cloud Firewall的流量採用時間段峰值彙總的資料,所以總流量峰值會小於等於請求與響應之和。
出方向流量=主動外聯請求流量+主動外聯響應流量
出方向峰值指主動外聯總流量峰值,因為Cloud Firewall的流量採用時間段峰值彙總的資料,所以總流量峰值會小於等於請求與響應之和。
說明目前在Cloud Firewall互連網邊界防火牆僅能查看公網IP。如果您需要查看私網IP,需要先開啟NAT防火牆。
查看入方向攔截趨勢:在入方向攔截趨勢頁簽,將滑鼠懸浮在趨勢圖上,展示指定時間點攔截入方向流量的會話數。您可以在趨勢圖左上方查看攔截的峰值。
查看出方向攔截趨勢:在出方向攔截趨勢頁簽,將滑鼠懸浮在趨勢圖上,展示指定時間點攔截出方向流量的會話數。您可以在趨勢圖左上方查看攔截的峰值。
查看VPC邊界防火牆的流量趨勢圖:
查看VPC流量趨勢圖:在VPC流量趋势頁簽,將滑鼠懸浮在趨勢圖上,展示指定時間點總VPC流量數(已去重)。然後單擊查看明细,在VPC流量明细面板,查看該時間點的VPC流量明細。
您也可以單擊目標VPC操作列的查看詳情,跳轉到VPC訪問活動頁面。更多內容,請參見VPC互訪。
查看VPC攔截趨勢圖:在VPC拦截趋势頁簽,將滑鼠懸浮在趨勢圖上,展示指定時間點攔截VPC流量的會話數。您可以在趨勢圖左上方查看攔截的峰值。
場景資料
該地區展示了近期Cloud Firewall檢測到已開啟防護的資產受到的暴力破解、攻擊者掃描、挖礦行為、資料庫防護的風險,以及Cloud Firewall做的防護資訊。
設定查詢時間:單擊右上方的時間下拉式清單,選擇要查詢的時間範圍。
切換要查看的情境資料:單擊不同頁簽(暴力破解、掃描、挖矿行为、数据库防护),可以查看對應的資料。不同資料的具體說明如下:
暴力破解:展示了暴力破解的攻擊統計資料和攻擊應用、攻擊資產的排行圖。
掃描:展示了掃描風險統計資料和掃描應用、被掃描資產排行圖。
挖矿行为:展示了挖礦病毒的攻擊統計資料和攻擊應用、攻擊資產的排行圖。
数据库防护:展示了資料庫防護的攻擊統計資料和攻擊應用、攻擊資產的排行圖。
流量拓撲可視化
流量拓撲可視化功能展示了Cloud Firewall防護的雲資產的流量拓撲圖。目前拓撲圖支援展示雲資產的互連網邊界流量和VPC邊界流量。僅企業版和旗艦版Cloud Firewall支援該功能。
登入Cloud Firewall控制台。在左側導覽列,單擊概覽。
在流量拓扑可视化頁簽,您可以查看如下資料。
地區名稱
說明
支援的操作
總覽
該地區展示了公網IP、网元保护数、流量、入侵防护状态、攻击、ACL統計資訊。
公網IP:
总IP数:表示當前阿里雲帳號下所有公網資產IP的總數量。
未保护IP数:表示未開啟防火牆開關的IP的總數量。
單擊立即保护,可跳轉至防火牆開關頁面的互联网边界防火墙頁簽,您可以對未開啟防護的雲資產開啟防火牆開關。
网元保护数:
网元总数:表示當前阿里雲帳號下所有的網元數。
未保護:表示接入VPC防火牆保護的網元數,含VPC、VBR、TR、VPN、ECR(不含手動模式計量)。
單擊立即保护,可跳轉至防火牆開關頁面的VPC邊界防火牆頁簽,您可以對未開啟防護的VPC開啟防火牆開關。
流量:
近7天流量峰值:表示距離目前時間7天內,Cloud Firewall防護的流量的峰值。
出流量峰值:表示距離目前時間7天內,Cloud Firewall防護的出方向流量的峰值。
入流量峰值:表示距離目前時間7天內,Cloud Firewall防護的入方向流量的峰值。
入侵防护状态:
展示入侵防禦狀態是同步自防护配置頁面中威脅引擎運行模式的狀態。相關內容,請參見威脅引擎運行模式。
攻击:
已拦截攻击数:表示Cloud Firewall已攔截的惡意攻擊的次數。
总攻击数:表示Cloud Firewall防護的雲資產受到惡意攻擊的總次數。
ACL:展示已建立的存取控制策略的數量。
無
互連網邊界防火牆
該地區展示了當前阿里雲帳號下所有的公網資產與互連網之間的流量拓撲圖。
單擊雲資產表徵圖,展示該雲資產的公網IP。在頁面左側查看未保护IP和已保护IP。
單擊指定的IP,在頁面左側面板展示該IP入方向和出方向流量的詳情。
入向頁簽展示IP、开放活动端口、是否推荐智能策略、ACL访问控制等資訊。
出向頁簽展示外联域名、外联IP、是否推荐智能策略、ACL访问控制等資訊。
VPC邊界防火牆
所有VPC:展示當前阿里雲帳號下所有通過Express Connect串連的VPC和雲企業網中的VPC,將游標放置在VPC上,會展示該VPC的具體資訊。
 表徵圖表示VPC已開啟防護。
表徵圖表示VPC已開啟防護。 表徵圖表示VPC未開啟防護。
表徵圖表示VPC未開啟防護。
互联VPC:展示通過Express Connect串連的VPC和雲企業網中VPC的詳細資料。展開,您可以查看VPC間的流量拓撲圖。
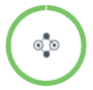 表徵圖表示通過Express Connect串連的VPC。
表徵圖表示通過Express Connect串連的VPC。 表徵圖表示雲企業網中的VPC。
表徵圖表示雲企業網中的VPC。
在頁面左側,展示雲企業網和Express Connect中存在互聯關係的VPC總數和所有存在互聯關係的VPC,您可單擊VPC的名稱,查看具體的流量拓撲圖。
無