IPsec-VPNは、インターネットを介した安全な通信を可能にするルートベースのテクノロジーです。 IPsec-VPN接続が確立されると、オンプレミスのクライアントは、仮想プライベートネットワーク (VPN) を介して仮想プライベートクラウド (VPC) にデプロイされているサービスに接続できます。 このトピックでは、IPsec-VPNを使用して、オンプレミスクライアントをElastic Desktop Service (EDS) EnterpriseのオフィスネットワークのVPCに接続する方法について説明します。
準備
開始する前に、Access cloud computers over VPCのトピックをよく確認し、次の準備を完了してください。
Cloud Enterprise Network (CEN) インスタンスを作成します。 詳細については、「CENインスタンスの作成. 」をご参照ください。
VPCを作成し、VPCをCENインスタンスにアタッチします。 詳細については、「VPC と vSwitch の作成」または「ネットワークインスタンスをCENインスタンスにアタッチする」をご参照ください。
オフィスネットワークを作成し、そのVPCをCENインスタンスに接続します。 詳細については、「コンビニエンスオフィスネットワークの作成と管理」および「エンタープライズ AD オフィスネットワークの作成と管理」をご参照ください。
重要オフィスネットワークを作成する前に、オフィスネットワークとCENインスタンス間、またはオフィスネットワークとデータセンター間のCIDRブロックの競合を防ぐために、オフィスネットワークのIPv4 CIDRブロックを計画する必要があります。 詳細については、「CIDRブロックの計画」をご参照ください。
すでにオフィスネットワークを作成している場合は、コンビニエンスオフィスネットワークをCENインスタンスに接続します。
Active Directory (AD) システムをElastic Compute Service (ECS) インスタンスにデプロイする場合、ADサーバーのVPCをCENインスタンスにアタッチする必要があります。 ADシステムをオンプレミスサーバーに展開する場合は、オンプレミスネットワークをクラウドネットワークに接続する必要があります。 エンタープライズADオフィスネットワークを作成し、オンプレミスサーバーとクラウド間の接続を確立できます。 次に、ADドメインを設定できます。
クラウドコンピュータとアカウントを作成します。 次に、クラウドコンピューターをアカウントに割り当てます。
アカウントの作成方法の詳細については、「コンビニエンスアカウントの作成」または「企業 AD アカウントの作成と管理」をご参照ください。
クラウドコンピューターの作成方法と割り当て方法の詳細については、「クラウドコンピューターの作成」および「クラウドコンピューターのユーザーへの割り当て」をご参照ください。
クラウドコンピューターに接続できるAlibaba Cloud Workspaceクライアントを取得します。 詳細については、「クライアントの使用」をご参照ください。
説明このトピックで説明するソリューションは、次のAlibaba Cloud Workspaceクライアントをサポートしています。WindowsクライアントおよびmacOSクライアント
.
サンプルCIDRブロック
オンプレミスデバイスとクラウドインスタンスが使用するネットワーク間のCIDRブロックの競合を防ぐために、CIDRブロックを計画する必要があります。 このセクションでは、次の表で説明するCIDRブロックを使用します。 実際のCIDRブロックが優先されます。
設定アイテム | CIDRブロック /IPアドレス | 説明 |
VPC Officeネットワーク | 172.16.0.0/12 | クラウドコンピューターが存在するオフィスネットワークで使用されるVPCのCIDRブロック。 Alibaba Cloud PrivateLink (エンドポイントサービス) はCIDRブロックを使用します。 |
ユーザーVPC | 192.168.0.0/16 | VPN接続を確立するために作成したVPC。 |
オンプレミスデータセンター | 10.0.0.0/24 | Alibaba Cloud Workspaceクライアントが使用するオンプレミスネットワークのCIDRブロック。 VPN接続はCIDRブロックから開始されます。 |
データセンターゲートウェイ | 115.XX.XX.154 | オンプレミスデータセンターのゲートウェイのパブリックIPアドレス。 |
VPNゲートウェイに接続するには、データセンターゲートウェイが標準のIKEv1およびIKEv2プロトコルをサポートする必要があります。 IKEv2およびIKEv1は、2つのインターネット鍵交換 (IKE) 反復である。 ゲートウェイがIKEv1およびIKEv2プロトコルをサポートしているかどうかを確認するには、ゲートウェイの製造元にお問い合わせください。
ステップ1: IPsec-VPNの設定
VPNゲートウェイを作成し、IPsec-VPNを有効にします。 詳細については、「VPN gatewayの作成」をご参照ください。
カスタマーゲートウェイを作成します。 詳細については、「カスタマーゲートウェイの作成と管理」をご参照ください。
IPsec-VPN 接続を作成します。 詳細については、「IPsec 接続を作成する」をご参照ください。
ピアCIDRブロックをCENに公開します。
VPCコンソールにログインします。
In the left-side navigation pane, click Route Tables.
[ルートテーブル] ページで、ユーザーVPCのルートテーブルを見つけ、ルートテーブルのIDをクリックします。
ルートテーブルの詳細ページで、[ルートエントリリスト] タブを選択し、[カスタムルート] タブをクリックします。
設定したピアCIDRブロック (オンプレミスデータセンターで使用されるプライベートネットワークのCIDRブロック) を見つけ、[操作] 列の [発行] をクリックします。
CIDRブロックの [ステータス] 列の値が [パブリッシュ] の場合、CIDRブロックはパブリッシュされます。
手順2: VPN設定をデータセンターゲートウェイにロードする
VPCコンソールにログインします。
左側のナビゲーションウィンドウで、 を選択します。
上部のナビゲーションバーで、IPsec-VPN接続のリージョンを選択します。
[IPsec接続] ページで、IPsec-VPN接続を見つけ、[操作] 列の [ピア構成の生成] をクリックします。
ダウンロードしたIPsec-VPN接続設定をデータセンターゲートウェイにロードします。
詳細については、「H3Cファイアウォールの設定」をご参照ください。
手順3: エンタープライズVPC IPアドレスまたはクラウドサービスルートの設定
ビジネス要件に基づいて、次のいずれかのソリューションを選択できます。ソリューション1とソリューション2では、エンタープライズVPCのIPアドレスを設定する方法について説明します。 主な違いは、ソリューション1が静的IPアドレスを使用することです。これにより、エンドユーザーはカスタムIPアドレスを設定する必要がないため、プロセスが簡単になります。
解決策1: エンタープライズVPCの静的IPアドレスの設定
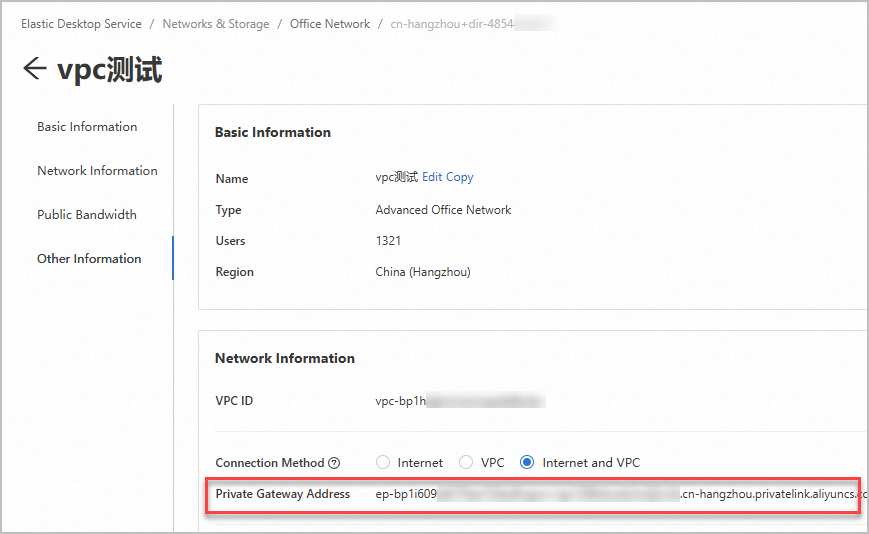
オフィスネットワークのプライベートゲートウェイアドレスを取得します。
EDS Enterpriseコンソールにログインします。
左側のナビゲーションウィンドウで、 を選択します。
[Officeネットワーク] ページで、目的のオフィスネットワークを見つけて、ネットワークIDをクリックします。
オフィスネットワークの詳細ページの [ネットワーク情報] セクションで、[Private Gateway Address] パラメーターを見つけ、パラメーター値をコピーします。 プライベートゲートウェイアドレスは、後続のステップで必要とされる。
エンタープライズDNSサーバーでCNAMEレコードを設定し、
private.wuying.comドメイン名をプライベートゲートウェイアドレスに指定します。エンドユーザーとしてAlibaba Cloud Workspaceクライアントでネットワークアクセスモードを設定します。
Windowsクライアントを開きます。
ログインページの右上隅で、 アイコンをクリックし、[接続設定] をクリックします。
[接続設定] ダイアログボックスで、次のパラメーターを設定します。
重要Windowsクライアントのバージョンが7.7以降であることを確認します。 そうしないと、エンタープライズVPC IPアドレスを設定できません。
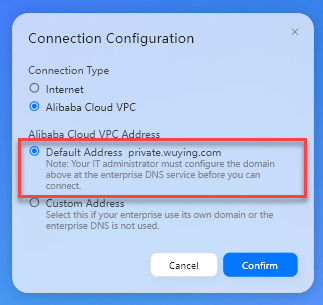
接続タイプ: 値をAlibaba Cloud VPCに設定します。
Alibaba Cloud VPCアドレス: 値をデフォルトアドレスに設定します。
[確認] をクリックします。
解決策2: エンタープライズVPCのカスタムIPアドレスの設定
オフィスネットワークのプライベートゲートウェイアドレスを取得し、エンドユーザーに転送します。
EDS Enterpriseコンソールにログインします。
左側のナビゲーションウィンドウで、 を選択します。
[Officeネットワーク] ページで、目的のオフィスネットワークを見つけて、ネットワークIDをクリックします。
オフィスネットワークの詳細ページの [ネットワーク情報] セクションで、[Private Gateway Address] パラメーターを見つけ、パラメーター値をコピーします。 プライベートゲートウェイアドレスは、後続のステップで必要とされる。

エンドユーザーとしてAlibaba Cloud Workspaceクライアントでネットワークアクセスモードを設定します。
Windowsクライアントを開きます。
ログインページの右上隅で、 アイコンをクリックし、[接続設定] をクリックします。

[接続設定] ダイアログボックスで、次のパラメーターを設定します。
重要Windowsクライアントのバージョンが7.7以降であることを確認します。 そうしないと、エンタープライズVPC IPアドレスを設定できません。
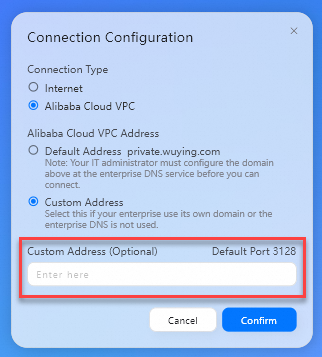
接続タイプ: 値をAlibaba Cloud VPCに設定します。
Alibaba Cloud VPCアドレス: 値をカスタムアドレスに設定します。
カスタムアドレス: 取得したオフィスネットワークのプライベートゲートウェイアドレスを入力します。
[確認] をクリックします。
解決策3: クラウドサービスのルーティングとDNSの設定
クラウドサービスのルートを設定します。
VPC経由でアクセスできるAlibaba cloudのクラウドサービスのCIDRブロックは
100.64.0.0/10です。これはRFC 6598で定義されている予約済みCIDRブロックです。 想定どおりにAlibaba Cloud WorkspaceクライアントからEDS Enterprise APIを呼び出すには、VPNのオンプレミスネットワークの100.64.0.0/10CIDRブロックを追加して、CIDRブロック宛てのリクエストをクラウドのVPCユーザーに転送します。説明100.xxx. xxx.xxx CIDRブロックが他のCIDRブロックと競合する場合は、ソリューション1またはソリューション2を使用することを推奨します。
複数のリージョンでクラウドコンピューターを使用する場合は、EDS EnterpriseのCIDRブロックとして
100.64.0.0/10を指定します。 高度なネットワークを設定する場合は、[ポートの概要] を参照して、クラウドサービスのCIDRブロックを指定します。 なお、VPC制御サービスに対応するドメイン名のIPアドレスは、クラウドサービスのIPアドレスです。
(オプション) DNSを設定する前に、次のコマンドを実行して、ドメイン名が解決できるかどうかをテストします。
nslookup ecd-vpc.cn-hangzhou.aliyuncs.comIPアドレスが返されると、ドメイン名を解決できます。 この場合、次のステップをスキップできます。 IPアドレスが返されない場合は、次の手順を実行してDNSを設定します。
(オプション) DNSを設定します。
VPC経由でクラウドコンピューターにアクセスするには、EDS Enterprise APIに関連するドメイン名とVPCに存在するストリーミングゲートウェイを解決するDNSが必要です。 この例では、DNSサーバーに次のIPアドレスが使用されています。
100.100.2.136
100.100.2.138
次のいずれかの方法を使用して、DNSアドレスを設定できます。
上記のDNSアドレスをデータセンターのDynamic Host Configuration Protocol (DHCP) サービスに追加します。
オンプレミスデータセンターのDNSサーバー上のトランジットルーターを設定して、
aliyuncs.comで終了するドメイン名解決リクエストを100.100.2.136または100.100.2.138にルーティングします。
手順4: クラウドコンピューターがVPC経由で接続できるかどうかを確認する
このセクションでは、Alibaba Cloud Workspace V7.7のWindowsクライアントを例として、クラウドコンピューターがVPC経由で接続できるかどうかを確認します。 使用するAlibaba Cloud Workspaceクライアントの実際のタイプが優先されます。
Windowsクライアントを開きます。
ログインページの右上隅で、 アイコンをクリックし、[接続設定] をクリックします。
[接続設定] ダイアログボックスで、[接続タイプ] パラメーターを [Alibaba Cloud VPC] に設定します。
メールアドレスに送信されたログイン資格情報を入力します
これには、オフィスネットワークIDまたは組織ID、ユーザー名、およびパスワードが含まれます。 次に、[次へ] アイコンをクリックして続行します。
リソースリストからクラウドコンピューターを見つけます。 次に、クラウドコンピューターを起動して接続します。
説明ネットワーク要求のタイムアウトなどのエラーが発生した場合、ネットワーク接続は確立されません。 上記のネットワーク設定が正しく設定されているかどうかを確認します。 次に、クライアントに再ログオンし、クラウドコンピューターに接続します。