アプリケーション保護機能は、ランタイムアプリケーション自己保護 (RASP) 技術に基づいて開発されています。 この機能は、アプリケーションの実行中に攻撃を検出し、自己保護を提供します。 アプリケーション保護機能を使用するためにコードを変更する必要はありません。 RASPエージェントは、アプリケーションが実行されているサーバーまたはコンテナーにのみインストールする必要があります。 この機能は、ほとんどの未知の脆弱性を悪用することによって起動される攻撃からアプリケーションを保護します。
仕組み
アプリケーション保護機能はRASPテクノロジーを採用しています。 この機能は、フックを使用して、アプリケーションと他のシステム間の相互作用をリアルタイムで監視します。 アプリケーションで疑わしい動作が検出されると、この機能はコンテキストに基づいて攻撃を識別してブロックします。 これにより、サーバー上のwebプロセスで検出されるアプリケーションの脆弱性、ゼロデイの脆弱性、およびメモリ内のwebシェルから保護できます。
シナリオと利点
アプリケーションの内部セキュリティを保護: この機能は、保護するアプリケーションの動作のみを監視し、トラフィックのソースに関係なく、南北および東西のトラフィックからの脅威からアプリケーションを保護します。 この機能は、アプリケーションの起動後すぐに有効になります。 この機能は、アプリケーションの最後の防衛線として機能します。
複雑なコードと暗号化されたトラフィックを簡単に処理: この機能は、アプリケーションのコンテキストを解析できます。 要求が不正な場合でも、アプリケーションの最終的なアクションを監視します。 この機能は、要求送信者のIDと予想されるアクションが一致しない場合に異常を検出できます。 暗号化されたトラフィックを監査できないネットワーク境界デバイスとは異なり、この機能はアプリケーション内の完全に復号化されたリクエストデータにアクセスできます。
偽陽性と偽陰性が低いゼロデイの脆弱性に対する防御: この機能は、重要な関数アプリケーションの実行を分析します。 多数の偽陽性および偽陰性を減らすために容易に利用できない脆弱性を識別し、無視することができる。 RASPは、攻撃ポータルを変更したり、高度な攻撃方法を使用したりしても、攻撃者がバイパスできない重要な機能の実行プロセスを監視することにより、ゼロデイの脆弱性を検出およびブロックできます。
攻撃ソースの追跡と脆弱性の修正: この機能は、セキュリティ担当者と開発者に、元の攻撃ペイロードやコード呼び出しスタックなどの詳細な攻撃パスを提供します。 これにより、脆弱性を特定、再現、修正できます。
O&Mコストの削減: 機能の展開は簡単です。 アプリケーションは、Security Centerコンソールでのみ接続する必要があります。 特定のルールを維持または更新する必要はありません。
制限事項
この機能は、JavaおよびPHPアプリケーションでのみ使用できます。 この機能は、Security Centerエージェントがインストールされているサーバーで使用できます。 サーバーは、Elastic Compute Service (ECS) インスタンス、サードパーティのクラウドサービスプロバイダーのクラウドサーバー、またはデータセンター内のサーバーです。 次の表に、Security Centerエージェントでサポートされているオペレーティングシステムを示します。
オペレーティングシステム | サポートされているシステムバージョン |
Windows (64ビット) |
|
Linux (64ビット) |
|
機能
攻撃検出 (Javaアプリケーション)
次の表に、アプリケーション保護機能が検出および防御できる攻撃の種類と、各種類の攻撃に対して防御するソリューションを示します。
攻撃タイプ | 説明 | 解決策 |
JNIインジェクション | Java Native Interface (JNI) インジェクションは、RASPテクノロジをバイパスする一般的な方法です。 攻撃者がコードを実行する権限を取得した後、攻撃者はJNI関数を使用して外部の悪意のあるダイナミックリンクライブラリを呼び出すことができます。 これにより、攻撃者はJavaレイヤーのセキュリティ保護を回避し、特定の悪意のある動作を隠すことができます。 | サーバーにコード実行の脆弱性がある可能性があります。 脆弱性の場所を確認し、コードを実行する権限を制限します。 |
SQL インジェクション | SQLインジェクション攻撃は、SQLステートメントをwebリクエストまたはwebフォームのクエリ文字列に挿入し、サーバーにSQLステートメントを実行させます。 攻撃者は、webフォームにSQL文を挿入することで、セキュリティの脆弱性が存在するwebサイトのデータを取得できます。 | SQLインジェクションは、SQL文を連結することによって発生します。 入力パラメーターをプリコンパイルするか、ホワイトリストとブラックリストを使用して連結パラメーターを制限します。 |
XXE | XXEインジェクションは、XML外部エンティティインジェクションの略です。 XMLファイルが外部エンティティを参照する場合、攻撃者は悪意のあるコンテンツを構築して、任意のファイル読み取り、コマンド実行、および内部ネットワーク攻撃を引き起こす可能性があります。 | アプリケーションがXMLファイルを解析するときに外部エンティティを読み込む必要があるかどうかを確認します。 そうでない場合は、XML解析構成で外部エンティティを無効にします。 |
悪意のあるDNSクエリ | 攻撃者は複数のメソッドを使用して、悪意のあるDNS (Domain Name System) クエリを悪用できます。 攻撃者は、DNSプロトコルを使用して機密情報を内部ネットワークから持ち出す可能性があります。 攻撃者は、DNSプロトコルを使用して、内部ネットワークシステムにServer-Side Request Forgery (SSRF) やJava Naming and Directory Interface (JNDI) インジェクションなどの脆弱性があるかどうかを確認することもできます。 | 悪意のあるDNSクエリは、ユーザー制御パラメーターに対するサーバー要求によって発生します。 パラメーター設定を確認し、ホワイトリストを設定します。 |
悪意のある反射呼び出し | RASPの自己保護モジュールは、攻撃者が実行中にリフレクションを使用してRASPデータを変更することを禁止します。 | サーバーにコード実行の脆弱性がある可能性があります。 脆弱性の場所を確認し、コードを実行する権限を制限します。 |
SSRF | SSRFは、攻撃者がサーバー側のアプリケーションにHTTPリクエストを実行させることにより、webサイトの内部システムを攻撃することを可能にするwebの脆弱性です。 | SSRFの脆弱性を修正するには、サーバーリクエストのターゲットIPアドレスを制限し、ホワイトリストを介してセキュアな内部リソースへのアクセスのみを許可し、不要な外部ネットワークアクセスを無効にします。 |
悪意のあるファイルの読み取りと書き込み | Javaは、ファイルの読み取りおよび書き込み操作用のRandomAccessFileクラスを提供します。 このクラスを使用してファイルの読み書きを行っても、ファイルパスやファイルの内容を制限しない場合、攻撃者が機密性の高いシステムファイルを読み取ったり、トロイの木馬ファイルをアップロードしたりする可能性があります。 | 期待どおりにファイルを読み取り、アップロードできるかどうかを確認します。 例外が発生した場合は、関数コードを確認してブラックリストを設定します。 |
悪意のあるファイルのアップロード | Webサイトで提供されるファイルアップロード機能では、ファイルの種類が制限されていない場合、攻撃者はトロイの木馬ファイルをアップロードすることでサーバーに対するより高い権限を取得する可能性があります。 これは深刻な害を引き起こします。 | アップロードできるファイルの種類を制限し、実行権限を持つファイル (JSP (Jakarta Server Pages) ファイルなど) のアップロードを禁止します。 |
コマンド注入 | コマンド実行の脆弱性により、攻撃者はサーバー上で任意のシステムコマンドを実行できます。 | ほとんどの場合、リモートコマンドの実行は、Webシェルまたはサーバーの危険なコードによって引き起こされます。 コマンドの実行場所を確認してください。 コマンドの実行がWebシェルによって引き起こされる場合は、Webシェルを適時に削除します。 コマンドを実行してサーバーに通常の機能を実装する場合は、実行できるコマンドを制限するようにホワイトリストを設定します。 |
ディレクトリトラバーサル | ウェブサイトのディレクトリは、ウェブサイトの構成上の欠陥のために任意に閲覧される可能性がある。 これにより、プライバシー情報が開示される。 攻撃者は、開示された情報を使用してWebサイトを攻撃できます。 | Webサイトディレクトリが期待どおりに移動できるかどうかを確認します。 例外が発生した場合は、関数コードを確認し、「. /」や「 .. /」などの関連コマンドを制限するようにブラックリストを設定します。 |
メモリーホース注射 | インメモリWebシェルは、新しいトロイの木馬の手法です。 攻撃者は、Web Application Firewall (WAF) およびホスト防御の検出を効果的に回避するのに役立つ技術的なアプローチを使用して、トロイの木馬をメモリに注入できます。 | サーバーにコード実行の脆弱性がある可能性があります。 脆弱性の場所を確認し、コードを実行する権限を制限します。 |
任意ファイルの読み取り | Webサイトで提供されるファイルのダウンロードおよび読み取り機能では、絶対パスまたはディレクトリトラバーサル文字を使用してファイルを読み取りおよびダウンロードし、ファイルパスが制限されていない場合、攻撃者はこの脆弱性を悪用して機密情報を取得し、サーバーを攻撃する可能性があります。 | ファイルを期待どおりに読み取ることができるかどうかを確認します。 例外が発生した場合は、関数コードを確認し、"./" や "../" などの入力パラメーターを制限するようにブラックリストを設定します。 |
スレッド注入 | スレッド注入は、RASP技術をバイパスする一般的な方法です。 攻撃者がコードを実行する権限を取得した場合、攻撃者はスレッドを作成してRASPにランタイム環境のコンテキストを失わせる可能性があります。 この場合、RASPの防御能力が損なわれる。 | サーバーにコード実行の脆弱性がある可能性があります。 脆弱性の場所を確認し、コードを実行する権限を制限します。 |
悪意のあるアタッチAPI | Attach APIは、実行中のアプリケーションのバイトコードを動的に変更するために使用できるJavaテクノロジです。 攻撃者はこのテクノロジーを使用して、エージェントタイプのメモリホースを注入できます。 この方法は非常に欺瞞的です。 | サーバーにコード実行の脆弱性がある可能性があります。 脆弱性の場所を確認し、コードを実行する権限を制限します。 |
JNDIインジェクション | アプリケーションがJNDIクエリを開始したが、クエリURLが攻撃者によって制御されている場合、攻撃者は、アプリケーションが実行されているサーバーに悪意のあるリンクのクエリを実行させ、悪意のあるクラスをロードさせる可能性があります。 これにより、サーバー上で任意のコードが実行されます。 |
|
脆弱なプロトコルの使用 | サーバーがアクセスするURLがユーザー制御可能で、URLプロトコルがアプリケーションで制限されていない場合、攻撃者はFileやNetDocなどの安全でないプロトコルを介してサーバー上の機密ファイルを読み取る可能性があります。 | URLプロトコルを制限します。 |
デシリアル化攻撃 | Java逆シリアル化は、一連のバイトをJavaオブジェクトに復元するプロセスです。 Javaオブジェクトに高いリスクを引き起こす可能性のあるコードが含まれている場合、攻撃者はJavaオブジェクトのメンバー変数を制御して、非シリアル化プロセス中に攻撃を開始できます。 |
|
任意のファイル削除 | Webサイトが提供するファイル削除機能では、ファイルパスが制限されていない場合、攻撃者は絶対パスまたはディレクトリトラバーサル文字を使用してファイルを削除し、サーバーを攻撃することができます。 | ファイルの削除操作が正常かどうかを確認します。 例外が発生した場合は、関数コードを確認し、"./" や "../" などの入力パラメーターを制限するようにブラックリストを設定します。 |
式言語 (EL) インジェクション | 式は、データのクエリや実行時の処理など、さまざまな機能を提供します。 複数の式は、関数呼び出しなどの高度な権限を必要とする機能も提供します。 機能が制限されていない場合、攻撃者は式の内容を変更し、任意のコードを実行できます。 | 式の内容を厳密に制限し、Java関数呼び出しを無効にします。 この脆弱性がサードパーティのコンポーネントによって引き起こされる場合は、できるだけ早い機会にコンポーネントをアップグレードする必要があります。 |
エンジン噴射 | Javaは、RhinoやNashornなどのさまざまなサードパーティのJavaScriptエンジンと、Apache VelocityやFreeMarkerなどのテンプレートエンジンを提供しています。 ほとんどの場合、これらのエンジンは、関数呼び出しなどの高度な権限を必要とする機能を提供します。 機能が制限されていない場合、攻撃者はエンジンによって実行されるコンテンツを変更し、任意のコードを実行できます。 | エンジンにインポートされたコンテンツを厳密に制限し、Java関数呼び出しを無効にします。 この脆弱性がサードパーティのコンポーネントによって引き起こされる場合は、できるだけ早い機会にコンポーネントをアップグレードする必要があります。 |
悪意のある豆の結合 | 一部のJavaフレームワークは、アプリケーションの実行時にbeanプロパティバインディングをサポートします。 バインドできるbeanプロパティの種類が制限されていない場合、攻撃者は機密のbeanプロパティの値を変更して、アプリケーションの実行を中断したり、任意のコードを実行したりすることができます。 | バインドできるbeanプロパティの型を制限して、classやclass loadersなどのbeanプロパティの値が変更されないようにします。 この脆弱性がサードパーティのコンポーネントによって引き起こされる場合は、できるだけ早い機会にコンポーネントをアップグレードする必要があります。 |
悪意のあるクラスの読み込み | ゼロデイの脆弱性とwebシェルは、悪意のあるクラスのロードに依存します。 悪意のあるクラスがロードされると、攻撃者は悪意のあるクラスを初期化し、コードを実行する権限を取得し、悪意のある操作を実行できます。 |
|
JSTLファイルの包含 | JavaServer Pages Standard Tag Library (JSTL) は、JavaServer Pages (JSP) タグのセットであり、JSPアプリケーションの共通コア機能をカプセル化しています。 ユーザーが制御可能なパラメーターをJSTLに直接連結すると、パラメーターに制限がなく、任意のファイル読み取りやSSRF攻撃を引き起こす特殊なスクリプトを作成できます。 | ユーザー制御可能なパラメーターをJSTLに直接連結しないことを推奨します。 これを行う必要がある場合は、パラメーターの内容に対して厳密なホワイトリスト制御を実行する必要があります。 |
攻撃検出 (PHPアプリケーション)
攻撃タイプ | 説明 | 解決策 |
悪意のあるファイルの包含 | 一般的なセキュリティ問題であるPHPのファイル包含の脆弱性により、攻撃者は入力を操作して任意のファイルを含めて実行できます。 これらの脆弱性は通常、 | ファイルパスを検証および制限して、アプリケーションディレクトリ内の定義済みファイルのみにアクセスできるようにし、攻撃者が悪意のあるパスを挿入しないようにします。 |
SSRF | SSRFは、攻撃者がサーバー側のアプリケーションにHTTPリクエストを実行させることにより、webサイトの内部システムを攻撃することを可能にするwebの脆弱性です。 | SSRFの脆弱性を修正するには、サーバーリクエストのターゲットIPアドレスを制限し、ホワイトリストを介してセキュアな内部リソースへのアクセスのみを許可し、不要な外部ネットワークアクセスを無効にします。 |
デシリアライゼーション | PHPのデシリアル化の脆弱性は、攻撃者がシリアル化されたデータを操作して任意の関数を実行できる重大なセキュリティ問題です。 これらの脆弱性は、 | 信頼できないデータを直接逆シリアル化しないでください。 代わりに、 |
コールバック関数の実行 |
| PHPコールバック関数の悪用を防ぐには、 |
悪意のあるファイルの読み取りと書き込み | ファイルの読み書き機能がファイルパスやコンテンツの制限なしに呼び出された場合、攻撃者は機密性の高いシステムファイルを読み取ったり、トロイの木馬ファイルをアップロードしたりする可能性があります。 | ファイルの読み取りと書き込みに関連する脆弱性を防ぐには、ファイルパスを厳密に検証および制限します。 定義済みディレクトリへのアクセスのみを許可し、ファイルコンテンツのセキュリティチェックを実行して、悪意のあるアップロードを防ぎます。 |
任意のコード実行 | 任意のコード実行の脆弱性は、攻撃者がサーバー上で任意のコードスニペットを実行できる重大なセキュリティ上の問題であり、サーバーを制御したり、機密データを読み取ったり変更したりする可能性があります。 このような脆弱性は通常、ユーザー入力の不適切な検証から発生し、攻撃者が悪意のあるコードを注入できるようになります。 この脆弱性が悪用されると、データ侵害、Webサイトの改ざん、またはマルウェアの挿入につながる可能性があります。 | 厳密な入力検証と出力エンコーディングを使用します。 |
任意ファイルの読み取り | 攻撃者は、ファイル読み取りインターフェイスを利用して、絶対パスまたはディレクトリトラバーサル文字を使用してファイルにアクセスできます。これにより、機密情報を取得してサーバーを攻撃できます。 | ファイル読み取りインターフェイスに厳密な入力検証とパス制限を適用します。 ホワイトリストで検証されたファイルへのアクセスを制限し、ブラックリストで「. /」や「 .. /」などの入力パラメーターを制限します。 |
任意のファイル削除 | 攻撃者は、ファイル削除インターフェイスを利用して、絶対パスまたはディレクトリトラバーサル文字を使用して任意のファイルを削除し、サーバーを攻撃します。 | ファイル削除インターフェイスに厳密な入力検証とパス制限を適用します。 検証済みファイルのみを削除できることを確認し、ブラックリストで「. /」や「 .. /」などの入力パラメーターを制限します。 |
コマンド実行 | コマンド実行の脆弱性により、攻撃者はオペレーティングシステムのコマンドまたはコードをバックエンドサーバーにリモートで注入し、バックエンドシステムを制御できます。 | すべてのユーザー入力を厳密に検証およびフィルタリングします。 未処理の入力を使用してオペレーティングシステムコマンドを構築することを避け、可能な限りシステムコマンドの実行よりも安全なAPIを優先します。 |
ディレクトリトラバーサル | Webサイトの構成上の欠陥により、ディレクトリの任意の閲覧が可能になり、機密情報の開示につながる可能性があります。 攻撃者はこの情報を使用してWebサイトを攻撃できます。 | 適切なサーバー権限を設定し、 |
悪意のあるファイルのアップロード | 攻撃者は、サーバーに対するより高い権限を取得するためにトロイの木馬ファイルをアップロードする可能性があります。 | アップロードできるファイルの種類を厳密に制限し、検証します。 安全なファイルタイプのみを許可し、phpなどの実行可能拡張子を持つファイルを禁止します。 サーバー上のファイルの内容を再確認して、セキュリティを確保します。 |
アプリケーション脆弱性防止
アプリケーション保護機能は、アプリケーションの脆弱性、ゼロデイの脆弱性、およびメモリ内のWebシェルから効果的に防御できます。 以下の図は、それがどのように機能するかを示します。 アプリケーションの脆弱性に対する緊急対応中、アプリケーション保護機能は攻撃を即座にブロックし、脆弱性を修正するための余分な時間を与えます。 アプリケーション保護機能は、リスクの原因と範囲をすばやく特定するのにも役立ちます。 詳細については、「脆弱性の表示と処理」をご参照ください。
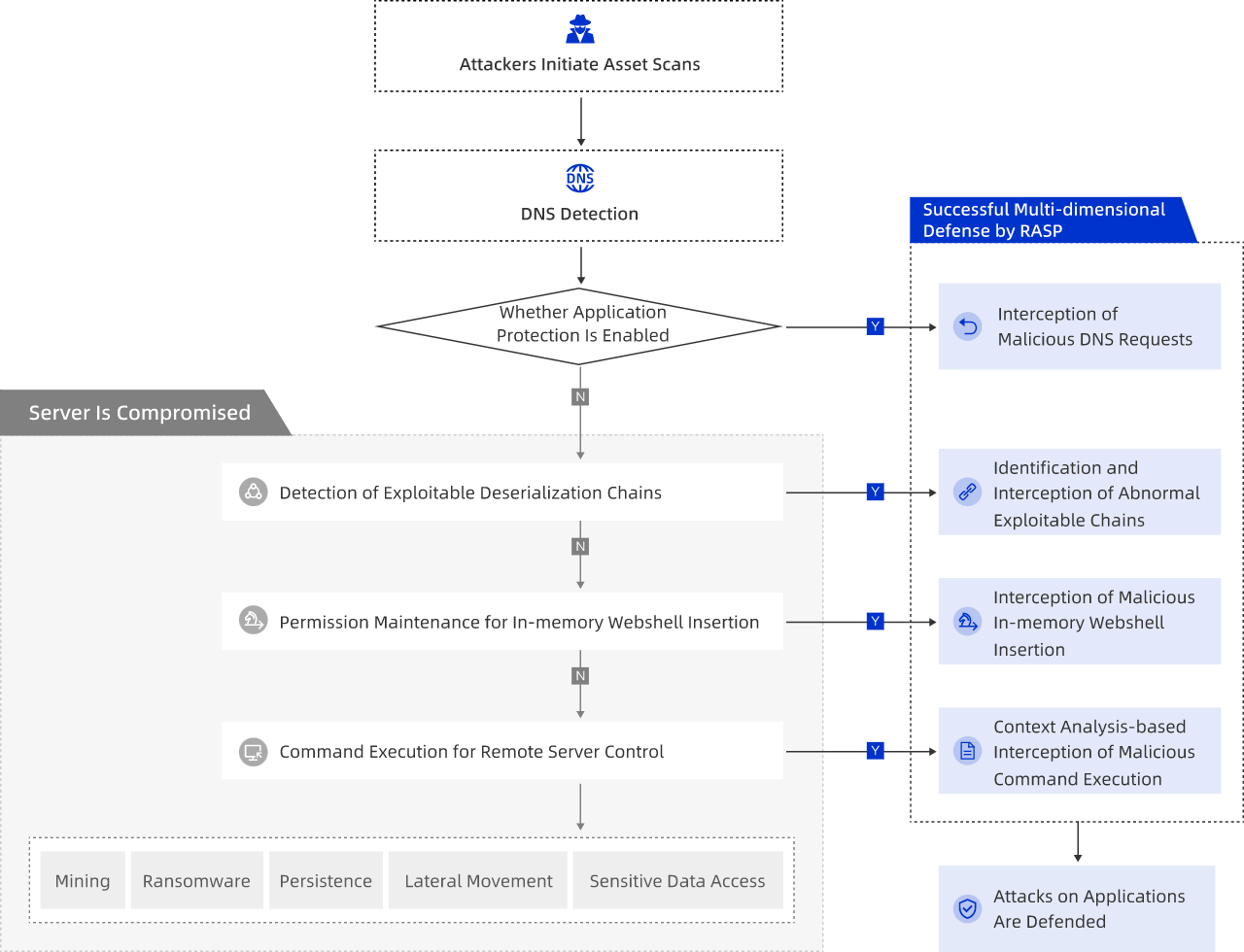
アプリケーションの脆弱性を修正できない場合は、アプリケーション保護機能にアプリケーションプロセスを追加して保護することができます。 脆弱性が検出されたアプリケーションを追加するには、次の手順を実行します。
Security Center コンソールにログインします。 上部のナビゲーションバーで、管理するアセットのリージョンを選択します。 中国 または 全世界 (中国を除く) を選択できます。
左側のナビゲーションウィンドウで、.
アプリケーションの脆弱性 タブで、RASP はリアルタイム保護をサポートします でマークされている脆弱性を見つけます。 タグを作成します。 このタグは、アプリケーション保護機能が脆弱性に対して防御できることを示します。 次に、[操作] 列の すぐに保護する をクリックします。
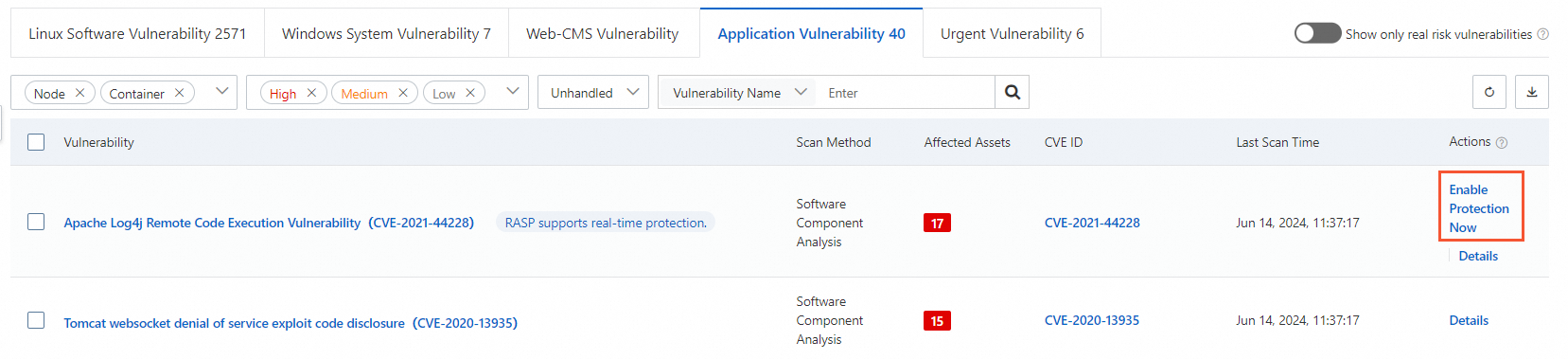
[アクセス管理] パネルで、Application Group Name ドロップダウンリストから目的のアプリケーショングループを選択し、関連するアセットを選択し、OK をクリックします。
必要なアプリケーショングループが存在しない場合は、ドロップダウンリストから [アプリケーショングループの作成] を選択し、アプリケーショングループの名前を入力して OK をクリックします。 新しいアプリケーショングループの保護モードは [ブロック] で、関連する保護ポリシーグループは [通常の実行グループ] です。
脆弱性が検出されたアプリケーションがアプリケーション保護機能に追加され、アプリケーションの脆弱性スキャンが完了すると、アプリケーションが実行されているサーバーのステータスは、脆弱性の詳細パネルの [未処理の脆弱性] タブで Protected に変わります。
アプリケーションの動作分析
アプリケーション動作分析機能は、接続されたアプリケーションをリアルタイムで監視し、アプリケーション動作データを収集および分析し、レポートを生成および視覚化します。 この機能は、アプリケーションの攻撃と防御の詳細を理解し、システムのセキュリティを強化するのに役立ちます。 詳細については、「アプリケーション分析機能の使用」をご参照ください。
インメモリwebshellディフェンス (Javaアプリケーション)
アプリケーション保護機能は、RASPテクノロジーを使用して、メモリデータを分析し、メモリ内Webシェルのブロック注入と実行を分析することで、メモリ内Webシェルを検出します。 詳細については、「インメモリwebshell防止機能の使用」をご参照ください。
弱さ検出 (Javaアプリケーション)
次の表に、アプリケーション保護機能で検出できるアプリケーションの弱点の種類と、関連する修正の提案を示します。
弱さのタイプ | リスクレベル | 説明 | 修正提案 |
脆弱なFastjson構成 | 高い | 逆シリアル化機能は、アプリケーションのFastjsonライブラリに対して有効になっています。 この機能は、攻撃者がリモートコマンドを実行させるために悪用される可能性があります。 特に必要がない限り、機能を無効にすることを推奨します。 | FastjsonのsafeModeをtrueに設定し、autoTypeをfalseに設定します。 |
脆弱なLog4j設定 | 高い | Log4jコンポーネントのルックアップ機能が有効になっています。 この機能は、攻撃者がJNDIインジェクションを開始し、リモートコードを実行させるために悪用される可能性があります。 | Log4jを最新バージョンに更新するか、JARパッケージからorg/apache/logging/log4j/core/lookup/JndiLookup.classファイルを削除します。 |
脆弱な起動パラメータ | 高い | 攻撃者がJava Debug Wire Protocol (JDWP) デバッグポートにアクセスできる場合、攻撃者は任意のコードを実行してリモートコードを実行できます。 | JDWPポートが不要になった場合は、できるだけ早くJDWPポートを無効にします。 JDWPポートをインターネットに公開しないでください。 長期間実行されるアプリケーションのJDWPポートを監視します。 JDWPポートが有効になっている場合は、ポートを無効にします。 |
シロの弱いキー | 高い | Shiroアプリケーションが暗号化に弱いキーを使用する場合、攻撃者はキーを解読してデシリアライゼーション攻撃を開始し、リモートコードを実行することができます。 | Shiroアプリケーションの暗号化キーをできるだけ早く変更します。 |
脆弱なJMX設定 | Medium | リモートJMX接続が有効になっていて、認証リスクが存在する場合、攻撃者はアプリケーションのJMXサービスにリモート接続してコマンドを実行することができます。 | リモートJMX接続を無効にするか、認証に安全なパスワードを使用します。 |
脆弱なRhino構成 | Medium | Rhinoには、攻撃者がリモートコード実行に利用できる保証プロパティが含まれています。 | Rhnioを最新バージョンに更新します。 SafeStandardObjectsを使用してRhnioのコンテキストを定義し、JavaScriptエンジンがJavaコードを呼び出さないようにします。 次のサンプルコードでは、SafeStandardObjectsを使用してRhinoのコンテキストを定義する方法の例を示します。 |
脆弱なスプリング構成 | Medium | Spring Boot Actuatorモジュールでは、heapDump、env、restart、refresh、trace、jolokia、h2-consoleなど、いくつかのエンドポイントが有効になっています。 これにより、機密情報のリークやリモートコードの実行が発生します。 | 特に必要がない限り、エンドポイントを無効にします。 |
脆弱なログインパスワード | Medium | アプリケーションへのログインに使用されるアカウントのパスワードが弱いです。 攻撃者は、パスワードを解読してシステムにログオンし、機密情報とサーバー権限を取得できます。 | できるだけ早くパスワードを複雑なパスワードに変更してください。 |
脆弱なJNDI設定 | 低い | アプリケーションは、useCodebaseOnly、rmi-trustURLCodebase、およびldap-trustURLCodebaseに関連する脆弱な構成を使用します。これにより、JNDIインジェクションが発生する可能性があります。 | JDKを最新バージョンに更新します。 JDKを更新できない場合は、アプリケーションの起動時に次の起動パラメーターを追加します。 |
XMLエンティティ設定の確認 | 低い | 外部エンティティではXML解析が有効になり、アプリケーションでXXE攻撃を引き起こす可能性があります。 | 特に必要がない限り、外部エンティティを使用しないでください。 |
弱いデータベースパスワード | 低い | アプリケーションがデータベースに接続するために使用するアカウントのパスワードが弱い場合、攻撃者はパスワードを悪用してデータベースにアクセスし、機密情報を取得したり、リモートコードを実行したりできます。 | できるだけ早くパスワードを複雑なパスワードに変更してください。 |