アクセス資格情報のリークは、クラウドにデプロイされているリソースとサービスに深刻なセキュリティリスクをもたらします。 このトピックでは、さまざまなシナリオで、アクセス資格情報を使用してAlibaba CloudのAPI操作を安全に呼び出す方法について説明します。
アクセス資格情報とは何ですか?
アクセス資格情報は、ID認証に使用される情報のセットです。 API、CLI、SDK、Terraformなどの開発ツールを使用してAlibaba Cloudにアクセスする場合、ID認証に合格するために有効なアクセス資格情報を提供する必要があります。 次のリストに、一般的なタイプのアクセス資格情報を示します。
AccessKeyペア: 各AccessKeyペアは、AccessKey IDとAccessKeyシークレットで構成されています。 AccessKeyペアは、Alibaba CloudがAlibaba CloudアカウントとRAM (Resource access Management) ユーザーに提供する永続的なアクセス資格情報です。 詳細については、「AccessKeyペアの作成」をご参照ください。
Security Token Service (STS) トークン: STSトークンは、Alibaba CloudがRAMロールに提供する一時的なアクセス資格情報です。 STSトークンのカスタム有効期間とアクセス許可を設定できます。 詳細については、「STSとは何ですか?」をご参照ください。
一般的なアクセス資格情報のリーク
開発者は、ビジネスコードでAccessKeyペアをハードコードします。 コードリポジトリを読み取る権限を持つ開発者は、AccessKeyペアを取得できます。 一部の開発者は、ビジネスコードをオープンソースコミュニティやコードホスティングサービスにアップロードすることさえあります。 これにより、さらに大きなセキュリティリスクが発生します。
一部の開発者は、クライアントがAPI操作を直接呼び出すことができるように、クライアントコードにAccessKeyペアを含めます。 攻撃者はクライアントコードを解凍し、AccessKeyペア情報を取得できます。
他のユーザーと共有される技術文書または資料には、AccessKeyペア情報が含まれています。
製品ドキュメントのサンプルコードには、AccessKeyペアの情報が含まれています。
開発者が管理権限を持たないAPI操作の応答には、AccessKeyペア情報が含まれます。
アクセス資格情報を使用する安全な方法
アクセス資格情報を使用するための安全な方法は、主にアクセス資格情報の公開時間と範囲を減らすことに重点を置いています。 次の表に、一般的なシナリオでアクセス資格情報を使用する安全な方法を示します。
移動方法 | シナリオ |
アプリケーションがContainer Service for Kubernetes (ACK) クラスターにデプロイされている場合、ACKクラスターのサービスアカウントのRAMロール (RRSA) 機能を有効にできます。 このようにして、ACKクラスターにデプロイされた各アプリケーションは、Alibaba CloudのAPI操作を呼び出すために異なるRAMロールを引き受けることができます。 | |
アプリケーションがElastic Compute Service (ECS) インスタンスにデプロイされている場合、特定の権限を持つインスタンスRAMロールをECSインスタンスにアタッチできます。 これにより、ECSインスタンスにデプロイされたアプリケーションは、Alibaba CloudのAPI操作を呼び出すことができます。 | |
企業のR&D、O&M、および製品担当者がO&M、管理、およびデバッグにAccessKeyペアを使用する場合は、ロールベースのシングルサインオン (SSO) を実装することをお勧めします。 これにより、企業のユーザーは対応するRAMロールを引き受け、STSトークンを取得して必要な操作を実行できます。 | |
Function Computeにデプロイされたアプリケーションが他のAlibaba Cloudリソースにアクセスする必要がある場合、関数をFunction Compute RAMロールに関連付けることができます。 これにより、アプリケーションはSTSトークンを使用してクラウドリソースにアクセスできます。 これにより、永続的なアクセス資格情報によって引き起こされる可能性のあるセキュリティリスクを防ぎます。 | |
上記のソリューションが適用されない場合は、Alibaba CloudのAPI操作を呼び出すようにシステム環境変数を設定することを推奨します。 |
ACKクラスターにデプロイされたアプリケーションを使用してRAMロールを想定する
前提条件
RAMと連携するAlibaba Cloudサービスが使用されます。 詳細については、「RAMで動作するサービス」をご参照ください。
RRSA機能は、Kubernetes 1.22を実行するACKクラスターのみをサポートします。 RRSA機能をサポートするACKクラスターには、ACK Basicクラスター、ACK Proクラスター、ACK Serverless Basicクラスター、ACK Serverless Proクラスター、ACK Edge Proクラスターがあります。
Alibaba Cloud SDK V2.0がインストールされています。
自己管理ゲートウェイを使用するサービスの自己開発SDKはインストールされていません。
作業原理
RRSA機能を使用すると、ACKクラスター内のさまざまなアプリケーションがさまざまなRAMロールを引き受けることができます。 アプリケーションはSTSトークンを取得し、トークンを使用して特定のRAMロールを引き受け、関連するクラウドサービスにアクセスできます。 これにより、最小権限の原則が適用され、アプリケーションはAccessKeyペアを使用する必要なくAPI操作を呼び出すことができ、AccessKeyペアのリークを防止できます。
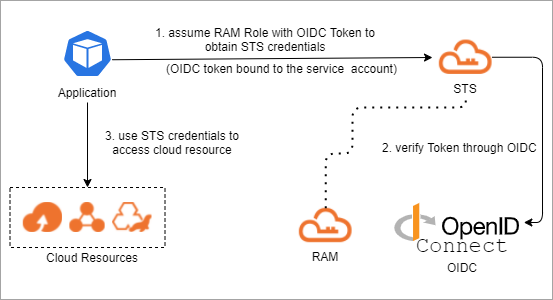
次の手順は、RRSAを使用してアクセス制御を実施する場合に、アプリケーションがクラウドリソースにアクセスする方法を示しています。
テナントは、サービスアカウントトークンボリューム予測の機能が有効になっているポッドをデプロイします。
ACKクラスターは、サービスアカウントOpenID Connect (OIDC) トークンファイルを作成し、トークンファイルをポッドにマウントします。
ポッド内のアプリケーションは、OIDCトークンファイルを使用してSTSのAssumeRoleWithOIDC APIを呼び出し、RAMロールを引き受けるために使用されるSTSトークンを取得します。
説明アプリケーションでこれらの操作を実行できるようにするには、まずOIDC IDプロバイダーを作成し、ポッドで使用されるサービスアカウントが指定されたRAMロールを引き受けることを許可する必要があります。 詳細については、「AssumeRoleWithOIDC」をご参照ください。
OIDCトークンファイル内のOIDCトークンは一時的なトークンです。 OIDCトークンファイルから最新のトークンを読み取るようにアプリケーションを設定することを推奨します。 クラスターは、トークンの有効期限が切れる前に、OIDCトークンファイルのトークンを更新します。
ポッド内のアプリケーションは、STSトークンを使用して指定されたRAMロールを引き受け、関連するクラウドサービスのAPIを呼び出します。
設定方法
ACKクラスターのRRSA機能を有効にします。 詳細については、「RRSAの有効化」をご参照ください。
ACKクラスターでRRSA機能を使用します。 詳細については、「RRSAの使用」をご参照ください。
サンプルコード
Alibaba Cloud SDK V2.0は、RRSAのOIDCトークン認証をサポートしています。 デフォルトでは、STSトークン認証をサポートし、Alibaba cloud SDK V2.0に基づいて開発されたすべてのクラウドサービスSDKは、RRSA OIDCトークン認証をサポートしています。 次の表に、サポートされているSDKのバージョンとデモを示します。
プログラミング言语 | サポートされているSDKバージョン | デモ |
Go | Alibaba Cloud Credentials for Go 1.2.6以降。 詳細については、「方法6: OIDC IdPのRAMロールの使用」をご参照ください。 | |
Java | Alibaba Cloud Credentials for Java 0.2.10以降。 詳細については、「方法6: OIDC IdPのRAMロールの使用」をご参照ください。 | |
Python 3 | Alibaba Cloud Credentials for Python 0.3.1以降。 詳細については、「方法6: OIDC IdPのRAMロールの使用」をご参照ください。 | |
Node.jsとTypeScript | TypeScript/Node.jsのAlibaba Cloud資格情報2.2.6以降。 詳細については、「方法6: OIDC IdPのRAMロールの使用」をご参照ください。 |
ECSでインスタンスRAMロールを想定
前提条件
RAMと連携するAlibaba Cloudサービスが使用されます。 詳細については、「RAMで動作するサービス」をご参照ください。
Alibaba Cloud SDK V2.0がインストールされています。
自己管理ゲートウェイを使用するサービスの自己開発SDKはインストールされていません。
作業原理
インスタンスのRAM (Resource Access Management) ロールをECS (Elastic Compute Service) インスタンスにアタッチできます。 ECSインスタンスは、インスタンスRAMロールのSecurity Token Service (STS) の一時的な認証情報を使用して、他のAlibaba CloudサービスのAPIにアクセスできます。 STSの一時的な資格情報は定期的に更新されます。 これにより、AccessKeyペアのセキュリティが確保され、RAMを使用したきめ細かなアクセス制御と権限管理が実装されます。
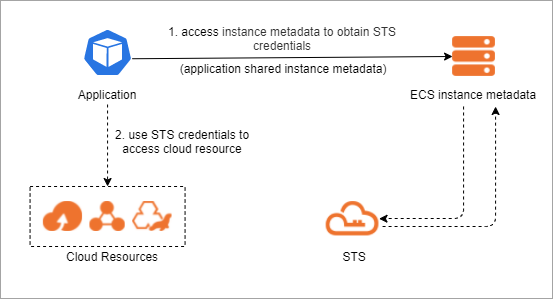
次のリストは、プロセスを説明しています。
アプリケーションは、ECSインスタンスメタデータにアクセスしてSTSトークンを取得します。 詳細については、「ECSインスタンスメタデータの概要」をご参照ください。
アプリケーションはSTSトークンを使用してクラウドリソースにアクセスします。 詳細については、「STSとは何ですか?」をご参照ください。
設定方法
インスタンスRAMロールをECSインスタンスにアタッチします。 詳細については、「インスタンスRAMロール」をご参照ください。
サンプルコード
Alibaba Cloud Credentialsは、Alibaba Cloudが開発者向けに提供する資格管理ツールです。 Alibaba Cloud Credentialsを使用して、インスタンスRAMロールをECSインスタンスに簡単にアタッチできます。 次のサンプルコードは、ECSのDescribeRegions操作を呼び出す方法の例を示しています。
プログラミング言语 | 関連ドキュメント |
Go | |
Java | |
Python | |
PHP | |
Node.js | |
.NET |
開発とデバッグにSTSトークンを使用
シナリオ
企業のR&D、O&M、および製品担当者が、O&M、管理、およびデバッグにAccessKeyペアを使用する場合は、ロールベースSSOを実装することを推奨します。 これにより、企業のユーザーは対応するRAMロールを引き受け、STSトークンを取得して必要な操作を実行できます。
設定方法
単一のAlibaba Cloudアカウントを使用する場合は、ジョブの責任でユーザーにRAMロールを割り当てることを推奨します。 詳細については、「概要」をご参照ください。 ユーザーはCLIツールsaml2alibabacloudを使用して、IDプロバイダー (IdP) 側での認証後にSTSトークンを取得できます。 詳細については、「saml2alibabacloud」をご参照ください。
複数のAlibaba Cloudアカウントを使用する場合は、CloudSSOを使用してアカウントのSSOを設定することを推奨します。 詳細は、「SSOの設定」をご参照ください。 設定が完了すると、ユーザーはCLIを使用してCloudSSOにログインし、Alibaba Cloudリソースにアクセスできます。 詳細については、「Alibaba Cloud CLIを使用したCloudSSOおよびAlibaba Cloudリソースへのアクセス」をご参照ください。
Function ComputeでのSTSトークンの使用
シナリオ
Function Computeにデプロイされたアプリケーションが他のAlibaba Cloudリソースにアクセスする必要があり、RAMユーザーのAccessKeyペアを関連する関数でハードコードする場合、AccessKeyペアのリークが発生し、O&Mが困難になる可能性があります。 この場合、RAMロールを関数にアタッチできます。 これにより、アプリケーションはSTSトークンを使用してクラウドリソースにアクセスでき、永続的なアクセス資格情報によるセキュリティリスクが回避されます。
ソリューションアーキテクチャ
このソリューションでは、function Computeの関数RAMロールを使用して、一時的なアクセス資格情報を取得して使用します。 このソリューションでは、アクセス権限を動的に管理し、一時的に付与できます。 これにより、AccessKeyペアの長期的な公開によって引き起こされるリスクを防ぎ、システムをより安全かつ柔軟にします。 管理者は、関数のロールを設定し、ロールに権限を1回付与するだけで済みます。 その後の操作では、関数は実行時に一時的なアクセス資格情報を動的に取得して使用できます。 これにより、O&M管理が簡素化されます。
管理者は、信頼できるエンティティがFunction ComputeであるRAMロールを作成し、そのRAMロールに権限を付与します。 権限には、クラウドサービスの特定のクラウドリソースにアクセスするために必要な権限が含まれます (次の図では1とマークされています) 。 次に、管理者は作成したRAMロールをfunction Computeの関数 (次の図では2とマーク) に関連付けます。 アプリケーションが関数コンテキスト (次の図では3とマーク) から一時的なアクセス資格情報を取得しようとすると、function Computeは信頼できるAlibaba CloudサービスとしてAssumeRole操作を呼び出し、RAMまたはSTSからSTSトークンを取得します (次の図ではiとマーク) 。 次に、アプリケーションは取得したSTSトークンを使用して、クラウドサービスのAPI操作を呼び出すことができます (次の図では4とマークされています) 。 クラウドサービスがリクエストを処理して結果を返した後、アプリケーションは結果を受け取り、その後の操作を実行します。
設定方法
詳細については、「他のAlibaba CloudサービスにアクセスするためのFunction Compute権限の付与」をご参照ください。
システム環境変数の設定
設定方法
ALIBABA_CLOUD_ACCESS_KEY_IDおよびALIBABA_CLOUD_ACCESS_KEY_SECRET環境変数を設定します。
LinuxおよびmacOS
以下のコマンドを実行します。
export ALIBABA_CLOUD_ACCESS_KEY_ID=<access_key_id> export ALIBABA_CLOUD_ACCESS_KEY_SECRET=<access_key_secret><access_key_id>をAccessKey IDに、<access_key_secret>をAccessKey secretに置き換えます。Windows
環境変数ファイルを作成し、
ALIBABA_CLOUD_ACCESS_KEY_IDとALIBABA_CLOUD_ACCESS_KEY_SECRET環境変数をファイルに追加してから、ALIBABA_CLOUD_ACCESS_KEY_IDのAccessKey IDとALIBABA_CLOUD_ACCESS_KEY_SECRETのAccessKeyシークレットを指定します。Windowsオペレーティングシステムを再起動します。
Alibaba Cloud SDKのサンプルコード
Alibaba Cloud SDKを使用すると、デフォルトのアクセス資格情報を作成するための環境変数と環境変数を設定できます。 API操作を呼び出すと、システムはデフォルトのアクセス資格情報からAccessKeyペアを読み取り、AccessKeyペアを使用して認証を完了します。 次のサンプルコードは、ECSのDescribeRegions操作を呼び出す方法の例を示しています。
プログラミング言語 | 関連ドキュメント |
Go | |
Java | |
Python | |
PHP | |
Node.js | |
.NET |
一般的なサンプルコード
自己管理ゲートウェイを使用するサービスの自己開発SDKの場合、Javaを使用して環境変数をロードする方法の例を次のサンプルコードに示します。
import com.aliyun.credentials.Client;
import com.aliyun.credentials.models.Config;
public class DemoTest {
public static void main(String[] args) throws Exception{
Config config = new Config();
// Which type of credential you want
config.setType("access_key");
// AccessKeyId of your ram user
config.setAccessKeyId(System.getenv("ALIBABA_CLOUD_ACCESS_KEY_ID"));
// AccessKeySecret of your ram user
config.setAccessKeySecret(System.getenv("ALIBABA_CLOUD_ACCESS_KEY_SECRET"));
Client client = new Client(config);
}
}資格情報のリークにアクセスするソリューション
AccessKeyペアのリーク: 詳細については、「AccessKeyペアのリークの解決策」をご参照ください。
STSトークンリーク: 詳細については、「STSトークンが公開された場合はどうすればよいですか?」をご参照ください。
関連ドキュメント
クラウドセキュリティのベストプラクティスの詳細については、以下のトピックを参照してください。