By default, you can access a Tablestore instance in the Tablestore console or by using the classic network endpoint or the virtual private cloud (VPC) endpoint. You can set the Access Type parameter to Bound VPCs or Tablestore Console or Bound VPCs for a Tablestore instance and bind a VPC to the instance. This way, resources in the Tablestore instance can be accessed over the bound VPC. However, you cannot access resources in the instance over the Internet, the classic network, or other VPCs that are not bound to the instance. This helps ensure access security.
Network types of Tablestore instances
By default, Tablestore creates a public endpoint, a virtual private cloud (VPC) endpoint, and a classic network endpoint for each instance. For more information, see Endpoints.
Public endpoint: used for access over the Internet. Users can use the public endpoint to access resources in the Tablestore instance over the Internet.
ImportantIf you access Tablestore over the Internet, you are charged for outbound traffic over the Internet. For more information, see Billing overview.
Classic network endpoint: used for access from Elastic Compute Service (ECS) instances that reside in the same region as the Tablestore instance. When applications on ECS instances access a Tablestore instance in the same region over the classic network, the response latency is lower and no traffic over the Internet is generated.
VPC endpoint: used for access from applications in bound VPCs. Applications in bound VPCs can use the VPC endpoint to access the Tablestore instance. For more information, see What is a VPC?
Tablestore supports various combinations of network types to meet different network security requirements. The following table describes the network types.
Network type | Description |
Custom | By default, a Tablestore instance does not allow access over the Internet. You can access a Tablestore instance only in the Tablestore console or by using the classic network or VPC endpoint. Important To access a Tablestore instance over the Internet, log on to the Tablestore console and manually allow access over the Internet. |
Tablestore Console or Bound VPCs | The Tablestore instance allows access in the Tablestore console or over bound VPCs. You cannot access the Tablestore instance over the Internet or the classic network. This ensures network isolation. Important Before you select this network type for an instance, make sure that your business does not require access over the Internet or the classic network. |
Bound VPCs | The Tablestore instance allows access only over bound VPCs. You cannot access the Tablestore instance in the Tablestore console or over the Internet or the classic network. You also cannot access resources in the instance in the Tablestore console. This ensures network isolation. Important Before you select this network type for an instance, make sure that your business does not require access over the Internet or the classic network or in the Tablestore console. |
Allow access to a Tablestore instance over bound VPCs
Prerequisites
Network planning is complete, and a VPC and a vSwitch are created. For more information, see Plan networks and Create a VPC with an IPv4 CIDR block.
A Tablestore instance is created. For more information, see Activate Tablestore and create an instance.
Step 1: Change the network type
By default, you can access a Tablestore instance in the Tablestore console or by using the classic network endpoint or VPC endpoint. If you want a Tablestore instance to allow access only in the Tablestore console or over bound VPCs, you can set the Access Type parameter to Tablestore Console or Bound VPCs or Bound VPCs for the instance.
This way, the Tablestore instance prohibits access over the Internet or the classic network. Proceed with caution.
Log on to the Tablestore console.
In the upper part of the page, select a resource group and a region.
In the Instance List section of the Overview page, click the name of the instance that you want to manage or click Manage Instance in the Actions column of the instance.
In the Network Access Control section of the Network Management tab, select an access type based on your network security requirements.
To allow access only in the Tablestore console or over bound VPCs, set the Access Type parameter to Tablestore Console or Bound VPCs.
To allow access only over bound VPCs, set the Access Type parameter to Bound VPCs.
NoteIf you set the Access Type parameter to Custom, you can configure the allowed network types and allowed source type.
In the Warning dialog box, read the message, select the check box, and then click OK.
Step 2: Bind a VPC to the instance
After you bind a VPC to a Tablestore instance, only the Elastic Compute Service (ECS) instances in the VPC that reside in the same region as the Tablestore instance can access the Tablestore instance.
If you want to manage VPCs as a Resource Access Management (RAM) user, make sure that the AliyunVPCReadOnlyAccess policy is attached to the RAM user by using the Alibaba Cloud account to which the RAM user belongs. Otherwise, you cannot obtain information about VPCs.
Log on to the Tablestore console.
In the upper part of the page, select a resource group and a region.
In the Instance List section of the Overview page, click the name of the instance that you want to manage or click Manage Instance in the Actions column of the instance.
On the Network Management tab, click Bind VPC.
In the Bind VPC dialog box, select a VPC and a vSwitch, and enter a name for the VPC.
The name of a VPC can contain only letters and digits and must start with a letter. The name must be 3 to 16 characters in length.
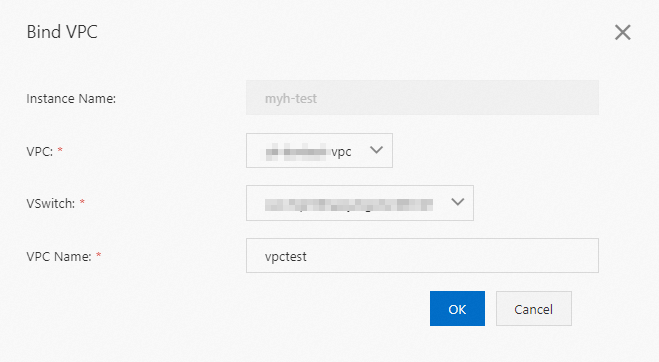
Click OK.
After the VPC is bound to the Tablestore instance, you can view information about the VPC in the VPCs section on the Network Management tab. The ECS instances in the VPC can use the VPC endpoint to access the Tablestore instance to which the VPC is bound.
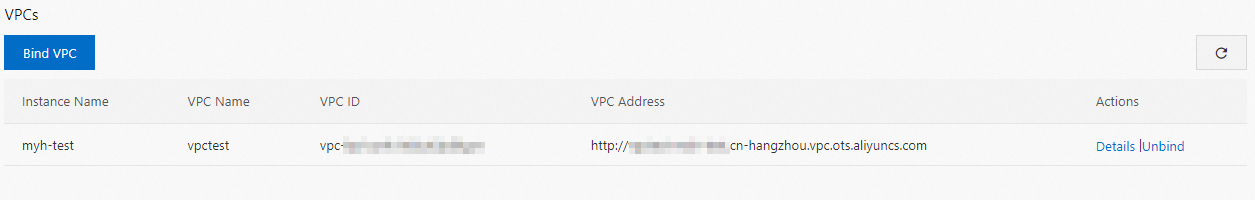
You can also perform additional operations on the VPC. The following table describes the operations.
Operation
Description
View details of the VPC
You can click Details in the Actions column of the VPC to view information about the VPC. The information includes the VPC ID, VPC name, VPC endpoint, and name of the Tablestore instances to which the VPC is bound.
Unbind the VPC from the Tablestore instance
If you no longer need to access the Tablestore instance over the VPC, you can unbind the VPC from the Tablestore instance.
ImportantAfter you unbind the VPC from the Tablestore instance, ECS instances in the VPC can no longer use the VPC endpoint to access the Tablestore instance. Proceed with caution. To access the Tablestore instance from the ECS instances, re-bind the VPC to the Tablestore instance.
Click Unbind in the Actions column of the VPC.
In the Unbind VPC dialog box, make sure that you understand the risks and select the check box.
Click OK.
Step 3: Access resources in the Tablestore instance from ECS instances in the bound VPC
Use Tablestore SDKs or the Tablestore CLI to access resources in the Tablestore instance from the ECS instances in the bound VPC by using the VPC endpoint.
More access control methods
You can further limit access to Tablestore resources by using the following methods:
You can attach RAM policies to RAM users to control access to Tablestore resources. For example, you can limit the IP addresses, protocols, and Transport Layer Security (TLS) versions that users can use to access Tablestore resources and the time when users can access Tablestore resources. For more information, see Use a RAM policy to grant permissions to a RAM user and Create a custom policy.
You can configure an instance policy for a Tablestore instance to limit the access sources of the instance, including the VPCs, IP addresses, and TLS versions that users can use to access the instance. For more information, see Use instance policies to restrict the access sources of an instance and Configure an instance policy.
You can use the control policy feature of Resource Directory to define the permission boundaries of enterprise accounts in a resource directory. For example, you can limit the TLS versions that can be used to access Tablestore resources and allow users to create only instances that do not support public access. For more information, see Use a custom access control policy to define the permission boundaries of enterprise users and Use custom access control policies.