You must grant permissions to a Resource Access Management (RAM) user before you can access the resources of Tablestore as the RAM user.Tablestore This topic describes how to use a RAM policy to grant permissions on Tablestore resources to a RAM user.
Background information
Alibaba Cloud allows you to use RAM and Security Token Service (STS) to manage permissions. You can grant different permissions on Tablestore to RAM users or create temporary access tokens that can be used to access Tablestore. RAM and STS make permission management more flexible and secure.
By default, the following system policies of Tablestore are created in RAM: AliyunOTSFullAccess, AliyunOTSReadOnlyAccess, and AliyunOTSWriteOnlyAccess. You can attach these system policies to RAM users based on your business requirements.
If you want to perform finer-grained permission management, you can create a custom policy and attach the policy to a RAM user.
If you want to grant temporary access permissions to a RAM user, you can use an STS token.
Use a system policy
Create a RAM user if you do not have a RAM user. For more information, see Create a RAM user.
Grant permissions to the RAM user. For more information, see Grant permissions to a RAM user.
To grant full permissions on Tablestore to the RAM user, such as the permission to create an instance, attach the AliyunOTSFullAccess policy to the RAM user.
To grant read-only permissions on Tablestore to the RAM user, such as the permission to read data from a table, attach the AliyunOTSReadOnlyAccess policy to the RAM user.
To grant write-only permissions on Tablestore to the RAM user, such as the permission to create a table, attach the AliyunOTSWriteOnlyAccess policy to the RAM user.
Use a custom policy
Create a RAM user if you do not have a RAM user. For more information, see Create a RAM user.
Create a custom policy. For more information, see Create custom policies.
For more information about how to configure a custom policy, see Configure a custom policy.
Attach the custom policy to the RAM user. For more information, see Grant permissions to a RAM user.
Use an STS token
Create a temporary role and grant permissions to the role.
Create a RAM role for a trusted Alibaba Cloud account. For more information, see Create a RAM role for a trusted Alibaba Cloud account.
In this example, two roles named
ramtestappreadonlyandramtestappwriteare created.ramtestappreadonlyis used to read data, andramtestappwriteis used to upload files.Create a custom policy. For more information, see Create custom policies.
For more information about how to configure a custom policy, see Configure a custom policy.
In this example, two policies named
ram-test-app-readonlyandram-test-app-writeare created.ram-test-app-readonly
{ "Statement": [ { "Effect": "Allow", "Action": [ "ots:BatchGet*", "ots:Describe*", "ots:Get*", "ots:List*" ], "Resource": [ "acs:ots:*:*:instance/ram-test-app", "acs:ots:*:*:instance/ram-test-app/table*" ] } ], "Version": "1" }ram-test-app-write
{ "Statement": [ { "Effect": "Allow", "Action": [ "ots:Create*", "ots:Insert*", "ots:Put*", "ots:Update*", "ots:Delete*", "ots:BatchWrite*" ], "Resource": [ "acs:ots:*:*:instance/ram-test-app", "acs:ots:*:*:instance/ram-test-app/table*" ] } ], "Version": "1" }
Grant permissions to the temporary role. For more information, see Grant permissions to a RAM role.
In this example, the
ram-test-app-readonlypolicy is attached to theramtestappreadonlyrole to grant read-only permissions on Tablestore, and theram-test-app-writepolicy is attached to theramtestappwriterole to grant write-only permissions on Tablestore.After you grant the permissions, record the ARN of the role, as shown in the following figure. A RAM user assumes the role based on the ARN.
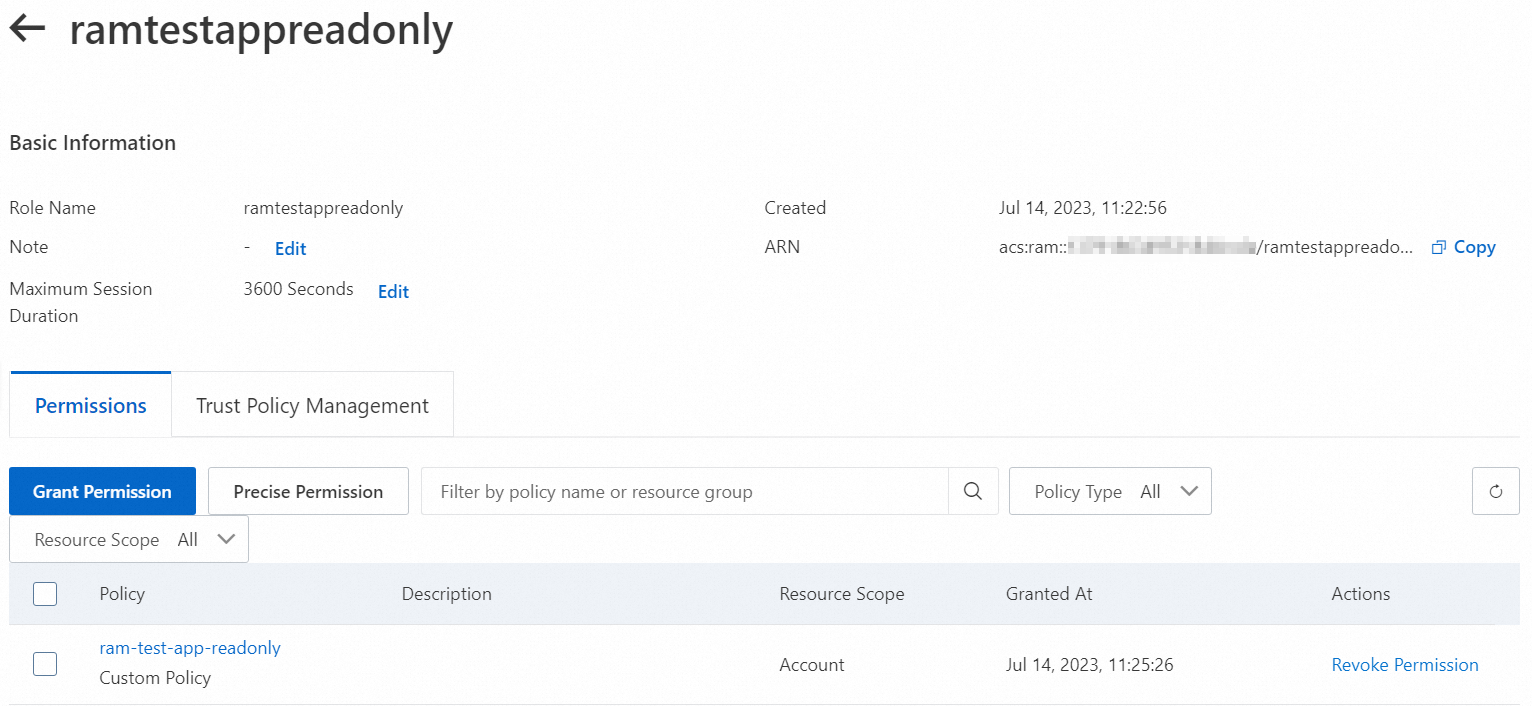
Grant temporary access permissions.
Create a RAM user if you do not have a RAM user. For more information, see Create a RAM user.
Create a custom policy. For more information, see Create custom policies.
For more information about how to configure a custom policy, see Configure a custom policy.
In this example, two policies named
AliyunSTSAssumeRolePolicy2016011401andAliyunSTSAssumeRolePolicy2016011402are created.Resourceindicates the ARN of a temporary role.AliyunSTSAssumeRolePolicy2016011401
{ "Version": "1", "Statement": [ { "Effect": "Allow", "Action": "sts:AssumeRole", "Resource": "acs:ram:198***237:role/ramtestappreadonly" } ] }AliyunSTSAssumeRolePolicy2016011402
{ "Version": "1", "Statement": [ { "Effect": "Allow", "Action": "sts:AssumeRole", "Resource": "acs:ram:198***237:role/ramtestappwrite" } ] }
Grant permissions to the RAM user by allowing the RAM user to assume temporary roles. For more information, see Grant permissions to a RAM user.
In this example, the
AliyunSTSAssumeRolePolicy2016011401andAliyunSTSAssumeRolePolicy2016011402policies are attached to the RAM user namedram_test_app.
Obtain an STS token to assume a RAM role. For more information, see AssumeRole.
Use temporary permissions to read and write data.
You can use temporary permissions to call Tablestore SDKs for different programming languages to access Tablestore. The following example shows how to use Tablestore SDK for Java to create an OTSClient object and pass the parameters that are obtained from STS, such as the AccessKey ID, AccessKey secret, and STS token.
OTSClient client = new OTSClient(otsEndpoint, stsAccessKeyId, stsAccessKeySecret, instanceName, stsToken);