Tablestore supports data encryption at rest. You can specify an encryption method when you create a data table to ensure data security.
Background information
Key Management Service (KMS) is an end-to-end service platform for key management, data encryption, and secret management. KMS provides simple, reliable, secure, and standard-compliant capabilities to encrypt and protect data and manage secrets. KMS helps reduce your costs of procurement, operations and maintenance (O&M), and research and development (R&D) on cryptographic infrastructure, data encryption products, and secrets management products. This way, you can focus on the development of your business.
Tablestore provides two encryption methods: KMS CMK-based encryption and Bring Your Own Key (BYOK)-based encryption. The keys for both methods must be obtained from KMS. Choose an encryption method based on your business requirements.
KMS CMK-based encryption: Tablestore uses the default key of the customer master key (CMK) type to generate a service key to encrypt data, and automatically decrypts the data when the data is read. You do not need to purchase or create a KMS instance when you use this encryption method.
BYOK-based encryption: Tablestore uses a software-protected key that you create and host in KMS to encrypt data. Before you use this method, you must create a software-protected key in the KMS console and create a Resource Access Management (RAM) role with encryption and decryption permissions for Tablestore to assume.
Usage notes
The data encryption feature can be enabled and configured only when you create a data table. After a data table is created, the data encryption feature cannot be disabled. Proceed with caution.
The data encryption feature is currently supported in the following regions: China (Hangzhou), China (Shanghai), China (Beijing), China (Zhangjiakou), China (Ulanqab), China (Shenzhen), China (Hong Kong), Japan (Tokyo), Singapore, Indonesia (Jakarta), Germany (Frankfurt), UK (London), US (Silicon Valley), and US (Virginia).
Encryption methods
KMS CMK-based encryption
When you use KMS CMK-based encryption, you do not need to purchase or create a KMS instance. You only need to turn on the Encryption switch and select CMK of KMS for the Encryption Type parameter when you create a data table in the Tablestore console.
Log on to the Tablestore console.
At the top of the page, select a region.
On the Overview page, click the name of the instance that you want to manage or click Manage Instance in the Actions column of the instance.
On the Instance Details tab, click Create Table.
In the Create Table dialog box, configure the parameters.
Enter a table name and configure the primary key.
Turn on the Encryption switch and select CMK of KMS for the Encryption Type parameter.
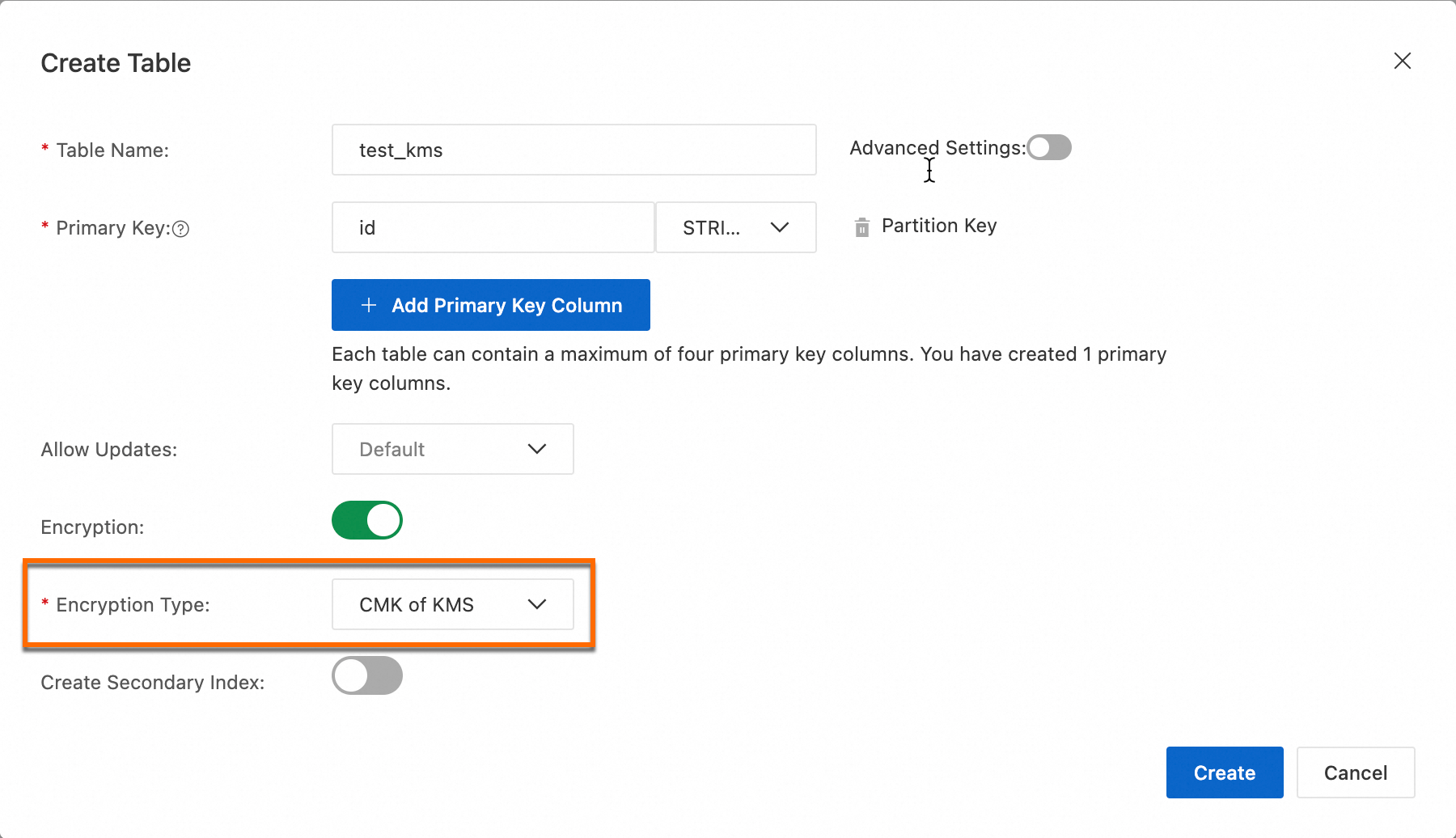
Click Create.
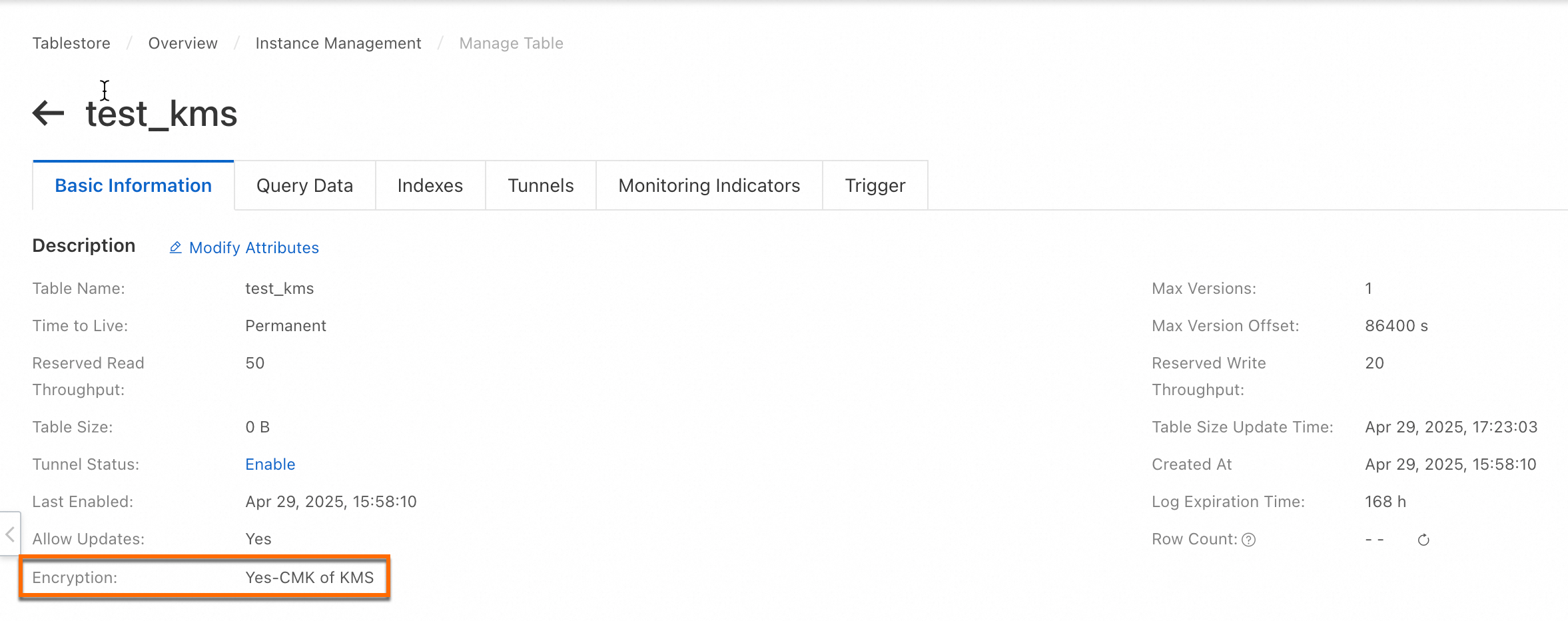
After the table is created, you can check whether the data encryption feature is enabled by performing the following operations: Click the name of the data table and check whether the value of the Encryption field in the Description section of the Basic Information tab is Yes-CMK of KMS.
BYOK-based encryption
To use BYOK-based encryption, you must obtain the key ID and RAM role ARN before you create a data table.
Key ID: Tablestore uses this key to encrypt and decrypt data.
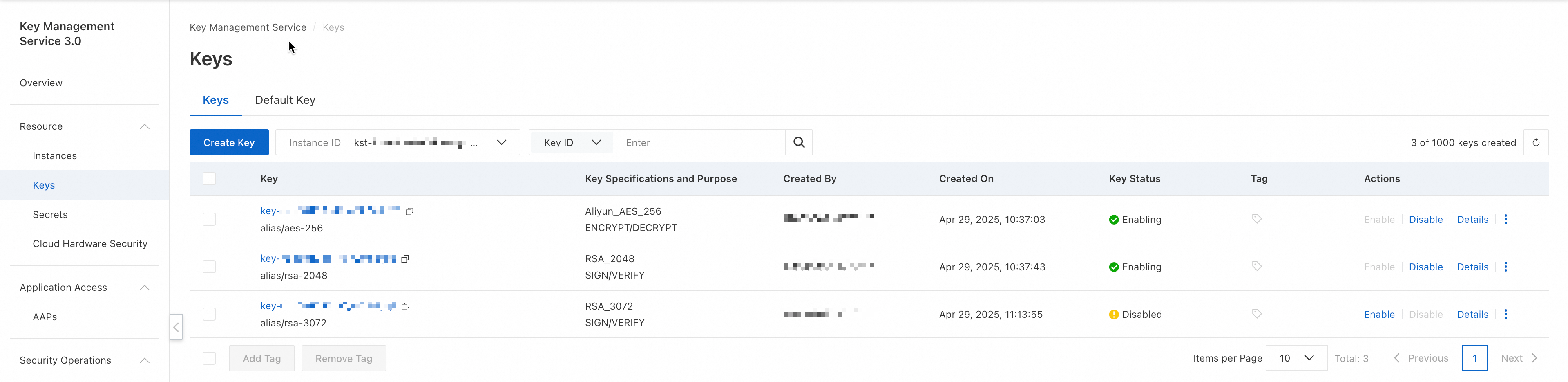
Log on to the KMS console.
Click Keys in the left navigation pane, select a key from the key list, and copy the key ID. You can also create a new software-protected key. For more information, see Manage keys.
RAM role ARN: Tablestore calls KMS to encrypt and decrypt data by assuming a RAM role. You must create a RAM role and grant permissions to the RAM role.
Create a RAM role.
Log on to the RAM console.
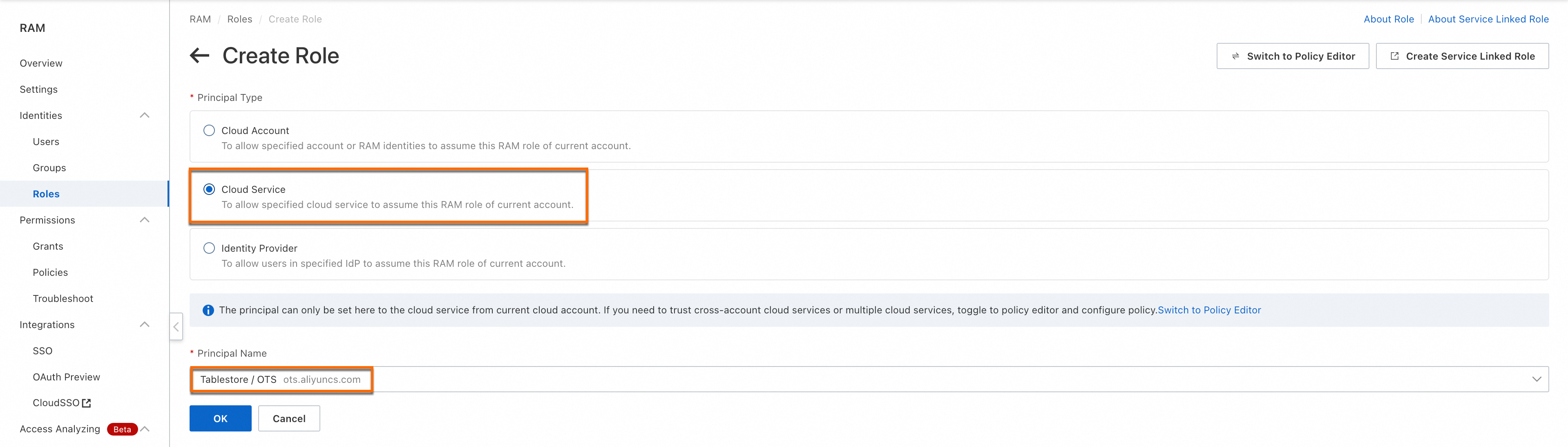
Choose . On the Roles page, click Create Role.
Select Cloud Service for the Principal Type parameter, and Tablestore / OTS for the Principal Name parameter. Click OK.
In the Create Role dialog box, enter a role name in the Role Name field, such as TablestoreBYOK, and click OK. Follow the on-screen instructions to complete verification and create the role.
Create a custom policy.
Log on to the RAM console.
Choose . On the Policies page, click Create Policy.
Select the JSON tab, enter the following script content, and click OK.
{ "Version": "1", "Statement": [ { "Effect": "Allow", "Action": [ "kms:Decrypt", "kms:GenerateDataKey" ], "Resource": [ "*" ] } ] }In the Create Policy dialog box, enter a policy name in the Policy Name field, such as TablestoreBYOKPolicy, and click OK.
Attach the custom policy to the RAM role.
Log on to the RAM console.
Choose , and click Grant Permission in the Actions column of the RAM role.
In the Grant Permission panel, enter the policy name to search in the Policy section, select the custom policy, and click Grant permissions to attach the custom policy to the RAM role.
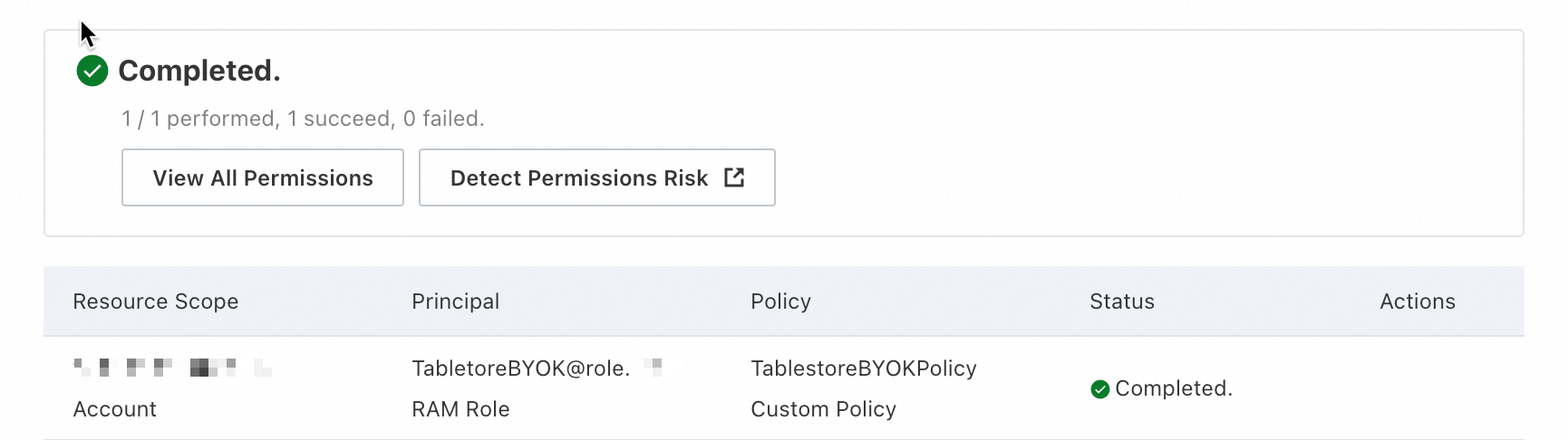
Obtain the ARN of the RAM role.
Log on to the RAM console.
Choose . On the Roles page, click the name of the role.
Copy the ARN of the RAM role in the Basic Information section.

After you obtain the key ID and RAM role ARN, you can create a data table encrypted by using the BYOK-based encryption method in the Tablestore console.
Log on to the Tablestore console.
At the top of the page, select a region.
On the Overview page, click the name of the instance or click Manage Instance in the Actions column of the instance.
On the Instance Details tab, click Create Table.
In the Create Table dialog box, configure the parameters.
Enter a table name and configure the primary key.
Turn on the Encryption switch, select BYOK-based Key for the Encryption Type parameter, and enter the key ID and RAM role ARN.
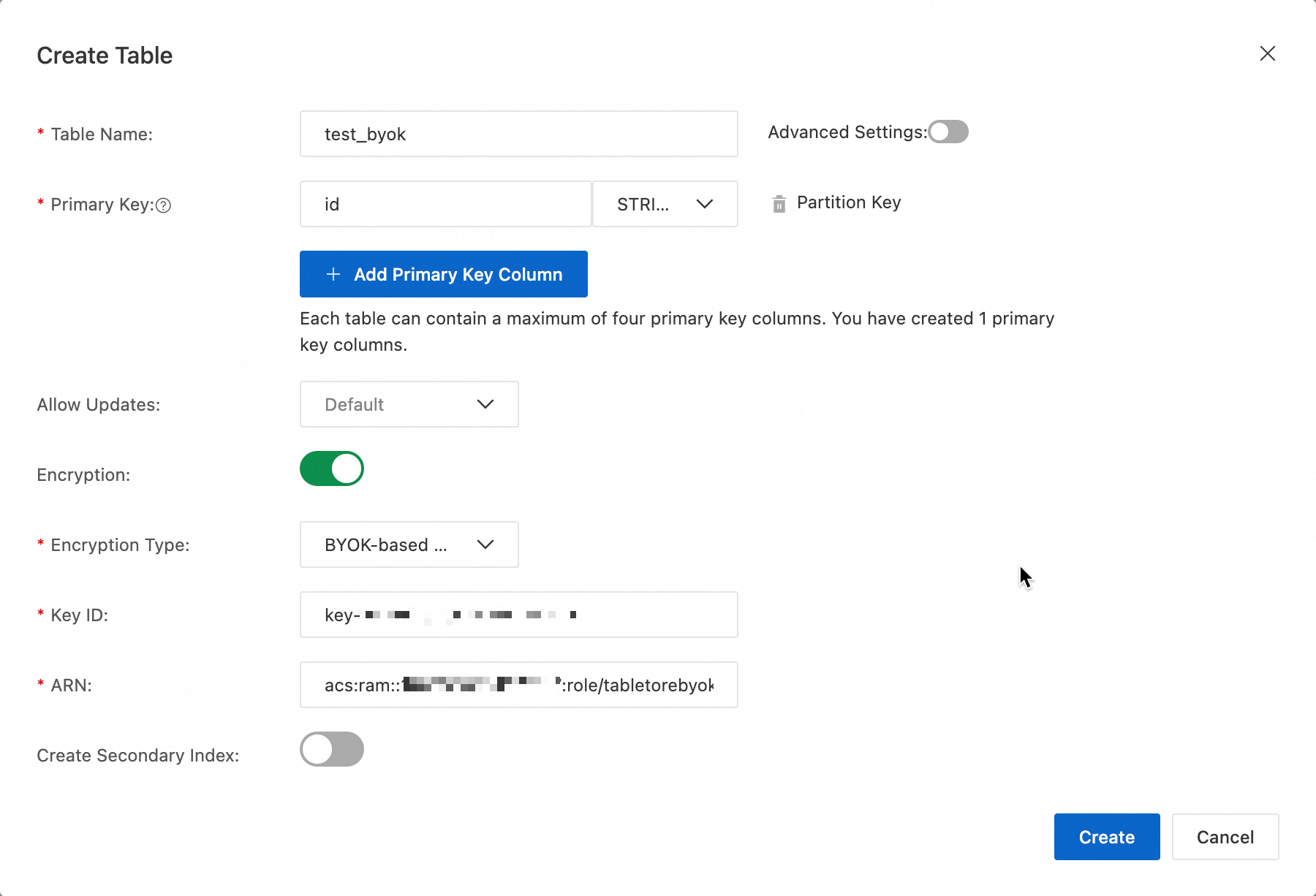
Click Create.
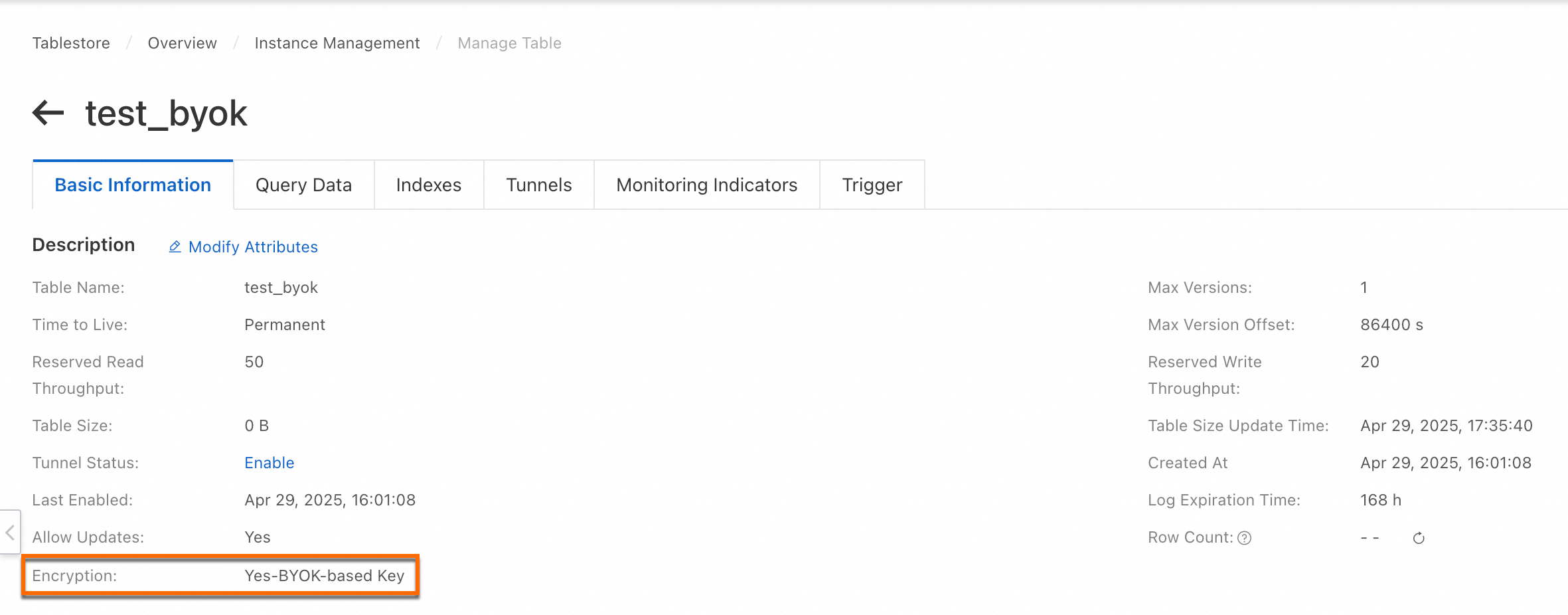
After the table is created, you can check whether the data encryption feature is enabled by performing the following operations: Click the name of the data table and check whether the value of the Encryption field in the Description section of the Basic Information tab is Yes-BYOK-based Key.
Development integration
You can specify an encryption method when you create a data table by using Tablestore SDK for Java or Tablestore SDK for Go.
Billing
You are charged for data encryption by KMS. For more information, see Billing.