If you want to deny or allow requests from specific IP addresses to a Network Load Balancer (NLB) instance, you can configure a security group for the NLB instance to implement access control. NLB security groups can be used as whitelists or blacklists, which implement fine-grained access control.
Sample scenarios
Before an NLB instance is added to a security group, the listener ports of the NLB instance accept all requests by default.
After an NLB instance is added to a security group which does not contain any Deny rules, the listener ports of the NLB instance accept all requests by default. If you want to allow requests only from specific IP addresses to your NLB instance, you must create at least one Deny rule.
If your NLB instance has access control requirements and you want to control inbound traffic to the NLB instance, you can add the NLB instance to a security group and configure security group rules based on your business requirements.
The outbound traffic of an NLB instance refers to responses returned to user requests. To ensure that your service is not affected, NLB security groups do not limit outbound traffic. You do not need to configure outbound rules for security groups.
When an NLB instance is created, the system automatically creates a managed security group in the VPC where the NLB instance resides. This security group is controlled by the NLB instance, so you can view its details but cannot make changes to it. The managed security group includes the following types of security group rules:
Rules with priority 1: These rules allow the local IP addresses used by the NLB instance to enable communication between the instance and its backend servers, as well as for health checks.
We recommend not adding security group rules with priority 1 that deny the NLB instance's local IP addresses to avoid conflicts, as such conflicts may disrupt communication between the NLB instance and backend servers. You can log on to the NLB console to check the local IP addresses of your NLB instance.
Rules with priority 100: These rules allow all IP addresses. Without any configured deny rules, an NLB instance in this security group checks all requests using its listeners.
The default access control rules (which are invisible) of either a basic security group or advanced security group include a rule that denies all requests. In this case, the default allow rule in the managed security group for the NLB instance takes effect.
The following scenarios are used to demonstrate how whitelists and blacklists work. For more information, see Security group rules.
A blacklist denies access from specific IP addresses.

A whitelist allows access only from specific IP addresses.

Limits
Item | Security group type | Description |
Security groups supported by NLB |
|
For more information about basic security groups and advanced security groups, see Basic security groups and advanced security groups. |
Security groups not supported by NLB | Managed security group | For more information about managed security groups, see Managed security groups. |
Prerequisites
Four Elastic Compute Service (ECS) instances are created. For more information about how to create an ECS instance, see Purchase an ECS instance.
ECS01 and ECS02 function as backend servers of the NLB instance. Applications are deployed on ECS01 and ECS02.
The following sample commands are used to deploy test applications on ECS01 and ECS02:
ECS03 and ECS04 are Internet-facing instances used to access the NLB instance. You can also use an existing Linux server to access the NLB instance. In this case, you do not need to create ECS03 and ECS04.
A domain name is registered, an Internet content provider (ICP) number is obtained for the domain name, and a CNAME record is created to map the custom domain name to the domain name of your NLB instance. For more information, see Register a generic domain nameRegister a domain name on Alibaba Cloud, ICP filing process, and Step 4: Create a DNS record.
The following table describes the configurations of the ECS instances used in this topic.
Instance
ECS configuration
VPC
IP address
Procedure
ECS01
Instance type: ecs.u1-c1m1.large
CPUs and memory: 2 vCPUs and 2 GiB of memory
Operating system: Alibaba Cloud Linux 3.2104 LTS 64-bit
Network type: VPC
VPC01
Private: 192.168.0.24
Public: not assigned
The instances are specified as the backend servers of the NLB instance.
ECS02
Private: 192.168.0.37
Public: not assigned
ECS03
VPC02
Private: 192.168.0.25
Public: 47.XX.XX.55
The instances are used as clients to access the NLB instance.
ECS04
Private: 192.168.0.26
Public: 101.XX.XX.251
Step 1: Create a server group
Log on to the NLB console.
In the top navigation bar, select the region where you want to create a server group. In this example, China (Hangzhou) is selected.
In the left-side navigation pane, choose NLB > Server Groups.
On the Server Groups page, click Create Server Group.
In the Create Server Group dialog box, set the following parameters and click Create.
The following table describes the key parameters for creating a server group. Use the default values for other parameters. For more information, see Create a server group.
Parameter
Description
Server Group Type
Specify a type of server group. In this example, Server Type is selected.
Server Group Name
Enter a name for the server group. In this example, RS01 is used.
VPC
Select a VPC from the drop-down list. In this example, VPC1 is selected. The server group must reside in the same VPC as ECS01 and ECS02.
Backend Server Protocol
Select a backend protocol. In this example, TCP is selected.
In the Server group created dialog box, click Add Backend Server.
On the Backend Servers tab, click Add Backend Server.
In the Add Backend Server panel, select ECS01 and ECS02 and click Next.
Specify ports and weights for the backend servers and click OK. In this example, port 80 is specified and the default weight is used.
Step 2: Create an NLB instance and configure listeners
In the left-side navigation pane, choose . On the Instances page, click Create NLB.
On the NLB (Pay-As-You-Go) page, set the following parameters.
The following table describes only some of the parameters. For more information about other parameters, see Create an NLB instance.
Region: In this example, China (Hangzhou) is selected.
Network Type: In this example, Internet is selected.
VPC: In this example, VPC01 is selected.
Click Buy Now and complete the payment.
Return to the Instances page, find the NLB instance that you created, and click the ID of the NLB instance.
Click the Listener tab. On the Listener tab, click Quick Create Listener. In the Quick Create Listener dialog box, set the following parameters to create a TCP listener that uses port 80 and click OK.
Parameter
Procedure
Listener Protocol
Select a listener protocol. In this example, TCP is selected.
Listener Port
In this example, port 80 is used.
Server Group
Select Server Type and select a server group from the drop-down list next to Server Type.
In this example, the server group created in Step 1: Create a server group is selected.
Check the accessibility of the NLB instance when the NLB instance is not added to a security group. The command
curl -s http://whatismyip.akamai.com/can be used to query the public IP address of the client which sends the request.Log on to ECS03. Run the following command to test whether ECS03 can access the NLB instance:
telnet Domain name 80.If you receive echo reply packets as shown in the following figure, ECS03 can access the NLB instance.

Log on to ECS04. Run the following command to test whether ECS04 can access the NLB instance:
telnet Domain name 80.If you receive echo reply packets as shown in the following figure, ECS04 can access the NLB instance.

The results show that before the NLB instance is added to a security group, ECS03 and ECS04 can access the NLB instance.
Step 3: Create a security group
Before you add your NLB instance to a security group, you must create a security group in the ECS console. This section describes how to create two security groups.
Security Group 1 as a blacklist
Add a Deny rule that denies access from specified IP addresses. In this example, a Deny rule that denies access from the public IP address 47.XX.XX.55 of ECS03 is created. You can keep the default security group rule. The following table describes the configurations of the rule.
Policy
Priority
Protocol
Port range
Authorization object
Deny
1
All
Destination: -1/-1
Source: 47.XX.XX.55
Security Group 2 as a whitelist
Add an Allow rule that allows access from specific IP addresses and a Deny rule that denies access from specific IP addresses. In this example, an Allow rule that allows access from the public IP address 47.XX.XX.55 of ECS03, and a Deny rule are created. The following table describes the configurations of the rules.
Policy
Priority
Protocol
Port range
Authorization object
Yes
1
All
Destination: -1/-1
Source: 47.XX.XX.55
Deny
100
All
Destination: -1/-1
Source: 0.0.0.0/0
Log on to the ECS console.
In the left-side navigation pane, choose .
In the top navigation bar, select the region where you want to create a security group. In this example, China (Hangzhou) is selected.
On the Security Groups page, click Create Security Group.
On the Create Security Group page, set the parameters in the Basic Information section.
Specify the following parameters. For more information about other parameters, see Create a security group.
Network: In this example, VPC 1 is selected. The security group must reside in the same VPC as the NLB instance.
Security Group Type: In this example, Basic Security Group is selected.
On the Create Security Group page, set the parameters in the Access Rule section.
On the Inbound tab, click Add Rule to add rules based on the configurations of the rules in Security Group 1 and Security Group 2.
Click Create Security Group.
Step 4: Add the NLB instance to the security group and verify the result
Use Security Group 1 as a blacklist
Add the NLB instance to Security Group 1 created in Step 3, and test whether the rule in Security Group 1 takes effect on the NLB instance.
Log on to the NLB console.
In the top navigation bar, select the region where the NLB instance is deployed. In this example, China (Hangzhou) is selected.
In the left-side navigation pane, choose NLB > Instances. On the page that appears, find the NLB instance created in Step 2: Create an NLB instance and configure listeners and click the instance ID. On the instance details page, click the Security Groups tab.
On the Security Groups tab, click Create Security Group. In the Add NLB Instance to Security Group dialog box, select the security group created in Step 3 and click OK.
In the left-side panel, click the ID of the security group that you want to manage. You can click the Inbound Policies or Outbound Policies tab to view the security group rules.
The following table describes the parameters that are relevant to this topic.
Policy
Priority
Protocol
Port range
Authorization object
Deny
1
All
Destination: -1/-1Source: 47.XX.XX.55Test whether access to the NLB instance in the security group is denied. The command
curl -s http://whatismyip.akamai.comcan be used to query the public IP address of the client which sends requests.Log on to ECS03. Run the following command to test whether ECS03 can access the NLB instance:
telnet Domain name 80.If you receive echo reply packets as shown in the following figure, ECS04 failed to access the NLB instance.

Log on to ECS04. Run the following command to test whether ECS04 can access the NLB instance:
telnet Domain name 80.If you receive echo reply packets as shown in the following figure, ECS04 can access the NLB instance.

The results show that after the NLB instance is added to Security Group 1, IP addresses specified in the Deny rule can no longer access the NLB instance. IP address not specified in the Deny rule can access the NLB instance.
Use Security Group 2 as a whitelist
Add the NLB instance to Security Group 2 created in Step 3, and test whether the rules in Security Group 2 take effect on the NLB instance.
Log on to the NLB console.
In the top navigation bar, select the region where the NLB instance is deployed. In this example, China (Hangzhou) is selected.
In the left-side navigation pane, choose NLB > Instances. On the page that appears, find the NLB instance created in Step 2: Create an NLB instance and configure listeners and click the instance ID. On the instance details page, click the Security Groups tab.
On the Security Groups tab, click Create Security Group. In the Add NLB Instance to Security Group dialog box, select Security Group 2 created in Step 3 and click OK.
In the left-side panel, click the ID of the security group that you want to manage. You can click the Inbound Policies or Outbound Policies tab to view the security group rules.
Policy
Priority
Protocol
Port range
Authorization object
Yes
1
All
Destination: -1/-1
Source: 47.XX.XX.55
Deny
100
All
Destination: -1/-1
Source: 0.0.0.0/0
Test whether access to the NLB instance in the security group is denied. The command
curl -s http://whatismyip.akamai.comcan be used to query the public IP address of the client which sends requests.Log on to ECS03. Run the following command to test whether ECS03 can access the NLB instance:
telnet Domain name 80.If you receive echo reply packets as shown in the following figure, ECS04 can access the NLB instance.
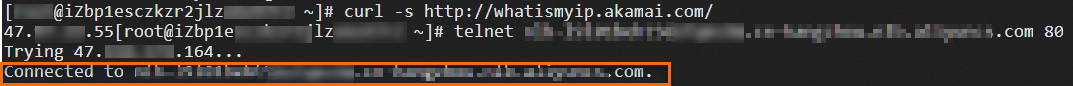
Log on to ECS04. Run the command to test whether ECS04 can access the NLB instance:
telnet Domain name 80.If you receive echo reply packets as shown in the following figure, ECS04 failed to access the NLB instance.
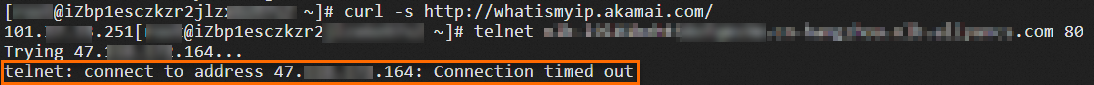
The results show that after the NLB instance is added to Security Group 2, only IP addresses specified in the Allow rules of Security Group 2 can access the NLB instance.
References
For more information about how to add an NLB instance to and remove an NLB instance from a security group, see Add an NLB instance to a security group.
For more information about how to enable fine-grained access control based on listeners or ports, see Configure security groups for NLB instances.
For more information about security groups, see Security groups.