You can create standard, privileged, and global read-only accounts for an ApsaraDB RDS for SQL Server instance in the ApsaraDB RDS console or by calling an API operation.
Scope
The first account for an instance must be a privileged account or a superuser account (SA permissions).
Privileged and standard accounts can be created for instances of all specifications. Global read-only accounts can be created for instances that meet the following requirements:
Database version: SQL Server 2016 or later.
Instance family: General-purpose or dedicated.
Account limits:
Standard accounts: No limit.
Privileged accounts: A maximum of one privileged account per instance.
Global read-only accounts: A maximum of two global read-only accounts per instance.
Account permission rules
Privileged account management rules
Scenarios | Permission behavior |
Create a privileged account | When created, the account is automatically granted the db_owner role for all existing databases. No manual authorization is required. |
Add a database |
|
| |
Recreate a privileged account |
|
Standard account management rules
Scenario | Permission behavior |
Create a standard account |
|
Add a database |
|
| |
Recreate a standard account with the same name |
|
Global read-only account management rules
Scenario | Permission behavior |
Create a global read-only account |
|
Add a database | For new databases (databases created after the account is created), the account is automatically granted read-only access. You do not need to manually grant permissions or change the scope. |
Delete a global read-only account |
|
Recreate a global read-only account |
|
Notes
Set a strong password: To ensure database security, set a strong password for the database account and change it regularly. You can also set a password policy for the account to control the password validity period and enhance account security.
Principle of least privilege: When you assign permissions to a database account, follow the principle of least privilege. Create accounts based on business roles and assign read-only and read/write permissions as needed. If necessary, you can create database accounts and databases with finer granularity. This ensures that each database account can access only the data required for its business. If write operations are not required, assign read-only permissions.
Create an account
Go to the Instances page. In the top navigation bar, select the region in which the RDS instance resides. Then, find the RDS instance and click the ID of the instance.
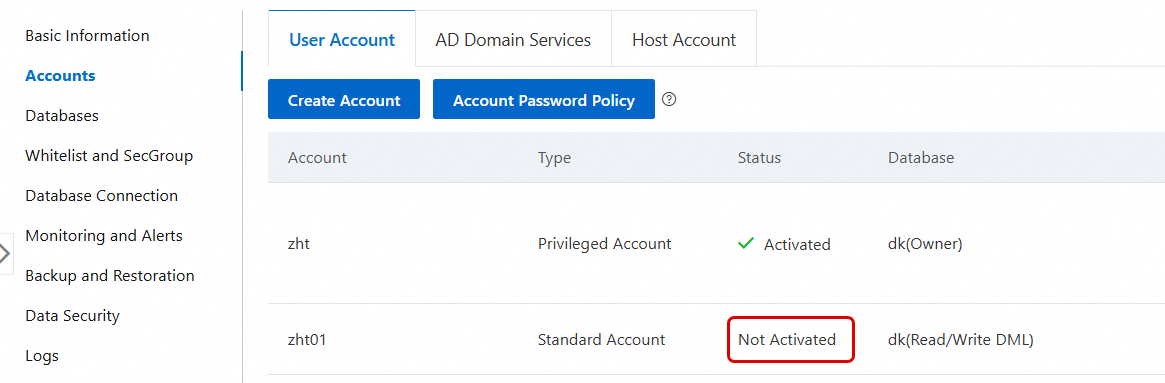
In the navigation pane on the left, click Accounts.
Click Create Account and set the following parameters.
NoteThe first account for an ApsaraDB RDS for SQL Server instance must be a privileged account or a superuser account. You can create a standard or global read-only account only after you create a privileged or superuser account.
Privileged account
Parameter
Description
Database Account
Enter a database account name. The name must start with a letter and end with a letter or a digit. It can contain lowercase letters, digits, and underscores (_). The account name cannot be a keyword.
Account Type
Select Privileged Account. Each instance supports only one privileged account.
New Password
Enter a password for the account. The password must meet the following requirements:
8 to 32 characters in length.
Contains at least three of the following character types: uppercase letters, lowercase letters, digits, and special characters.
Special characters are
!@#$%^&*()_+-=.
Confirm Password
Enter the same password again to confirm it.
Apply password policy
Applying a password policy lets you control the password validity period and enhance account security. Before you apply a policy, you must first set a password policy for the account.
Description
Enter a description. The description can be up to 256 characters in length.
Standard account
Parameter
Description
Database Account
Enter a database account name. The name must start with a letter and end with a letter or a digit. It can contain lowercase letters, digits, and underscores (_). The account name cannot be a keyword.
Account Type
Select Standard Account. An instance can have multiple standard accounts.
Authorize Database:
You can grant a Standard Account permissions on one or more databases and set different permissions for each. If no database has been created, you can leave this field empty and grant permissions to the account later. To grant permissions:
In the Unauthorized Databases list, select the databases that you want to authorize.
Click
 to add the databases to the Authorized Databases list.
to add the databases to the Authorized Databases list.Set permissions on the databases for the account. The permissions can be Read/Write (DML), Read-Only, or Owner. For more information about permissions, see Account permissions.
New Password
Enter a password for the account. The password must meet the following requirements:
8 to 32 characters in length.
Contains at least three of the following character types: uppercase letters, lowercase letters, digits, and special characters.
Special characters are
!@#$%^&*()_+-=.
Confirm Password
Enter the same password again to confirm it.
Apply password policy
Applying a password policy lets you control the password validity period and enhance account security. Before you apply a policy, you must first set a password policy for the account.
Description
Enter a description. The description can be up to 256 characters in length.
Global read-only account
Parameter
Description
Database Account
Enter a database account name. The name must start with a letter and end with a letter or a digit. It can contain lowercase letters, digits, and underscores (_). The account name cannot be a keyword.
Account Type
Select Global Read-Only Account. After this account is created, it is automatically granted read-only permissions on all existing databases in the instance. These permissions also apply to any new databases.
New Password
Enter a password for the account. The password must meet the following requirements:
8 to 32 characters in length.
Contains at least three of the following character types: uppercase letters, lowercase letters, digits, and special characters.
Special characters are
!@#$%^&*()_+-=.
Confirm Password
Enter the same password again to confirm it.
Apply password policy
Applying a password policy lets you control the password validity period and enhance account security. Before you apply a policy, you must first set a password policy for the account.
Description
Enter a description. The description can be up to 256 characters in length.
Click OK. After the page refreshes, you can view the created account.
References
Use the console to create a database account with SA permissions.
Create different types of database accounts by calling the CreateAccount API operation.
Delete different types of database accounts by calling the DeleteAccount API operation.