All OpenSearch applications that are created within your Alibaba Cloud account belong to the account. By default, an Alibaba Cloud account has full permissions on resources that belong to the account. OpenSearch allows you to use Resource Access Management (RAM) to grant RAM users the permissions to access and manage OpenSearch resources within your Alibaba Cloud account.
Take note of the following items:
Different from the old OpenSearch console, the new OpenSearch console refines the permission granularity of RAM users. To use the new OpenSearch console as a RAM user, you must re-configure the RAM policy for the RAM user.
To grant RAM users permissions, you must use OpenSearch API or OpenSearch SDK V3 or later. This feature is not supported by V2 or earlier versions of OpenSearch API or OpenSearch SDK.
If you use a third-party service as the data source of an OpenSearch application, you must comply with the rules of the RAM permission system to grant RAM users the permissions on the third-party service. You cannot grant RAM users the permissions on MaxCompute. The reason is that a RAM user that is authorized to access a MaxCompute project of the corresponding Alibaba Cloud account may fail to access other resources that belong to the Alibaba Cloud account. As a result, the RAM user may fail to reference the project as the data source to connect to OpenSearch. We recommend that you use an Alibaba Cloud account to configure a MaxCompute project as the data source of an application, and then manage the application as a RAM user.
If you want to configure an ApsaraDB RDS instance as the data source of an application in the OpenSearch console as a RAM user, you must grant the RAM user the required permissions on the instance. Otherwise, an error message appears, indicating that the connection to ApsaraDB RDS fails. For more information about how to grant a RAM user the permissions on an ApsaraDB RDS instance, see the "Permissions to access an ApsaraDB RDS instance" section of this topic.
Actions that start with Search, such as SearchApp and SearchSuggest, do not support IP address-based conditional authorization. If you configure IP-based conditional authorization for such actions, an error occurs.
Effective time
After you grant permissions to a RAM user or update the permissions of a RAM user, the granted or updated permissions take effect in 5 minutes.
Common minimum permission set
If you want to use the OpenSearch console as a RAM user, you must grant the RAM user the required permissions. A common minimum permission set contains the permissions that are required to search for data in an application, view the application list, view application details, configure monitoring and alerting, and access an ApsaraDB RDS instance. The following sections describe these permissions for your reference.
Permissions to search for data in an application
If you want to use OpenSearch SDK to initiate a search request or test the document retrieval feature for an application as a RAM user, the RAM user must have the permissions to search for data in the application. The following sample code provides an example on the policy that grants the permissions required to retrieve documents from the application named app_schema_demo:
{
"Statement": [
{
"Effect": "Allow",
"Action": "opensearch:SearchApp",
"Resource": "acs:opensearch:*:*:apps/app_schema_demo"
}
],
"Version": "1"
}Permissions to view the application list
If you want to view applications after you log on to the OpenSearch console as a RAM user, the RAM user must have the permissions to view the list of applications.
{
"Statement": [
{
"Action": [
"opensearch:ListAppGroup",
"opensearch:DescribeAppStatistics",
"opensearch:ListAppGroupErrors"
],
"Effect": "Allow",
"Resource": "acs:opensearch:*:*:app-groups/*"
}
],
"Version": "1"
}Permissions to view application details
The OpenSearch console provides the monitoring and alerting feature on the details pages of applications. If you want to view the details of an application in the OpenSearch console as a RAM user, the RAM user must have the permissions to view application details. The following sample code provides an example on the policy that grants the permissions required to view the details of the application named app_schema_demo:
{
"Statement": [
{
"Effect": "Allow",
"Action": [
"opensearch:DescribeAppGroup",
"opensearch:ListApp",
"opensearch:DescribeApp"
],
"Resource": "acs:opensearch:*:*:app-groups/app_schema_demo"
},
{
"Action": "opensearch:ListUserAnalyzers",
"Effect": "Allow",
"Resource": "acs:opensearch:*:*:user-analyzers/*"
}
],
"Version": "1"
}Permissions to configure monitoring and alerting
OpenSearch provides the monitoring and alerting feature based on the CloudMonitor service of Alibaba Cloud. The system policy AliyunCloudMonitorReadOnlyAccess grants the read-only permissions on CloudMonitor. You can search for this policy in the RAM console.
{
"Version": "1",
"Statement": [
{
"Action": [
"cms:Get*",
"cms:List*",
"cms:Query*",
"cms:BatchQuery*"
],
"Resource": "*",
"Effect": "Allow"
},
{
"Action": "opensearch:DescribeApp",
"Resource": "acs:opensearch:*:*:app-groups/*",
"Effect": "Allow"
}
]
}Permissions to access an ApsaraDB RDS instance
OpenSearch can obtain data from an ApsaraDB RDS instance based on tables or fields. ApsaraDB RDS uses whitelists to implement access control. If you want to use OpenSearch to obtain data from an ApsaraDB RDS instance, you must grant the RAM user the permissions to configure a whitelist for the ApsaraDB RDS instance. Otherwise, when OpenSearch connects to the ApsaraDB RDS instance, an error occurs, indicating that the RAM user is not authorized to configure an IP address whitelist for the ApsaraDB RDS instance. You can grant permissions to a RAM user in the RAM console by performing the following steps: Follow the instructions on the Overview page to create a custom policy and a RAM user. Then, attach the policy to the RAM user on the Users page. For more information, see Use RAM to manage ApsaraDB RDS permissions. The following sample code provides an example on the policy that grants the permissions required to access an ApsaraDB RDS instance in OpenSearch:
For information about the variables, such as $regionid, $accountid, and $dbinstanceid, in the Resource parameters, see Use RAM for resource authorization.
You can use the wildcard (
*) to set the variables in the Resource parameters.{ "Version": "1", "Statement": [ { "Action": "rds:DescribeDBInstanceAttribute", "Resource": "acs:rds:$regionid:$accountid:dbinstance/$dbinstanceid", "Effect": "Allow" }, { "Action": "rds:ModifySecurityIps", "Resource": "acs:rds:$regionid:$accountid:dbinstance/$dbinstanceid", "Effect": "Allow" }, { "Action": "rds:DescribeDBInstanceIPArrayList", "Resource": "acs:rds:$regionid:$accountid:dbinstance/$dbinstanceid", "Effect": "Allow" }, { "Action": "rds:DescribeDBInstanceNetInfoForChannel", "Resource": "acs:rds:$regionid:$accountid:dbinstance/$dbinstanceid", "Effect": "Allow" } ] }
Permissions to call API operations
The following sample code provides an example on the policy that grants the permissions required to call API operations to search for data, push data, and access drop-down suggestion models.
{
"Statement": [
{
"Effect": "Allow",
"Action": [
"opensearch:PushDoc",
"opensearch:SearchApp"
],
"Resource": [
"acs:opensearch:$regionId:*:apps/$appGroupName",
"acs:opensearch:$regionId:*:app-groups/$appGroupName"
]
},
{
"Action": "opensearch:SearchSuggest",
"Effect": "Allow",
"Resource": "acs:opensearch:$regionId:*:suggestions/$suggestionIdentity"
}
],
"Version": "1"
}Examples
Before you grant permissions to a RAM user, you must determine which permissions on which applications to grant. In most cases, if you use the OpenSearch console as a RAM user, you must grant the RAM user the permissions to perform the required actions. For example, you can grant the RAM user the permissions to perform the Describe* and List* actions. You can also grant a custom set of permissions to the RAM user as needed.
Example 1
You want to grant all permissions on all OpenSearch applications in all regions to a RAM user that belongs to an Alibaba Cloud account whose ID is 1234. In this case, you can use the Alibaba Cloud account to create a custom policy in the RAM console, and then attach the policy to the RAM user. You can also grant permissions to the RAM user by using RAM SDK. To grant permissions to a RAM user, perform the following steps: 1. Create a custom policy.
{
"Statement": [
{
"Action": "opensearch:*",
"Effect": "Allow",
"Resource": "acs:opensearch:*:1234:apps/*"
}
],
"Version": "1"
}2. Attach the policy to the RAM user.
Example 2
You want to grant all permissions on all OpenSearch applications in the China (Hangzhou) region to a RAM user that belongs to an Alibaba Cloud account whose ID is 1234. In this case, You can use the Alibaba Cloud account to create a custom policy in the RAM console, and then attach the policy to the RAM user. You can also grant permissions to the RAM user by using RAM SDK. To grant permissions to a RAM user, perform the following steps:
1. Create a custom policy.
{
"Statement": [
{
"Action": "opensearch:*",
"Effect": "Allow",
"Resource": "acs:opensearch:cn-hangzhou:1234:apps/*"
}
],
"Version": "1"
}2. Attach the policy to the RAM user.
Take note of the following items:
You can use the wildcard (*) to specify all types of resources in the Resource parameter.
You can specify the name of an application in the Resource parameter. In this case, the authorized RAM users can perform all actions that are specified in the Action parameter only on this application, even if the Action parameter is set to opensearch:*. This limit does not apply to the opensearch:ListApp or opensearch:CreateApp action.
The actions that are specified in the Action parameter apply only to the resources that are specified in the Resource parameter. For example, if you want to authorize RAM users to perform the opensearch:ListApp and opensearch:CreateApp actions, you must use the wildcard (*) to specify all applications in the Resource parameter. These two actions are different from other actions in that you can authorize RAM users to perform other actions only on specified applications.
For example, you have specified application names in all your custom policies. In this case, if you also want to authorize a RAM user to perform the opensearch:ListApp and opensearch:CreateApp actions, you must create another custom policy with the Action parameter set to opensearch:* for the two actions and attach this policy to the RAM user.
Solution to failed RAM user authentication in the OpenSearch console
When you use the OpenSearch console as a RAM user, an error message of failed RAM user authentication may appear, as shown in the following figure. 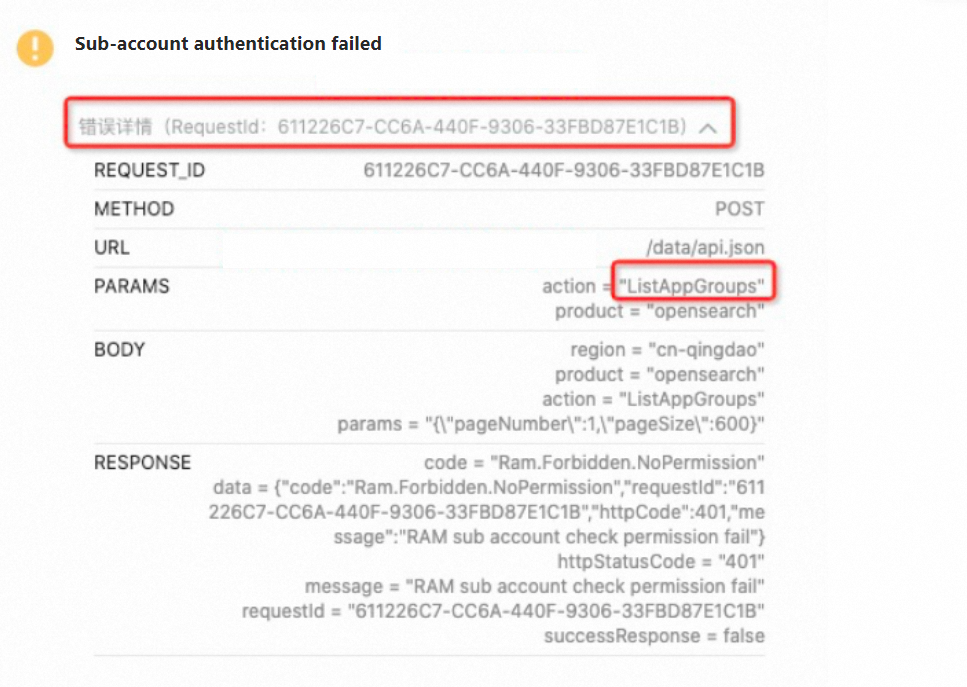 To resolve this error, perform the following steps:
To resolve this error, perform the following steps:
View the details of the error message to find the POP action in the request. In this example, the POP action is ListAppGroups. If the POP action ends with DryRun, ignore DryRun. For example, if the POP action is CreateAppDryRun, the actual action is CreateApp.
In the Authorization rules of applications topic, find the RAM action and the value format of the Resource parameter that correspond to the ListAppGroups POP action.
In most cases, the RAM action is different from the POP action.
Configure a custom policy to grant the required permissions on the RAM action to the RAM user.