By default, when you mount a File Storage NAS (NAS) file system on an Elastic Compute Service (ECS) instance, the NAS file system and the ECS instance must reside in the same virtual private cloud (VPC) in the same region and belong to the same Alibaba Cloud account. If you want to mount a NAS file system across VPCs, you can use PrivateLink to establish a private connection between the VPCs. You do not need to use an Internet egress such as a network address translation (NAT) gateway or an elastic IP address (EIP). Data is not transmitted over the Internet, providing higher security and network quality. This topic describes how to use PrivateLink to mount and access a NAS file system across VPCs in the same region.
Feature description
PrivateLink allows you to use VPCs of Alibaba Cloud for service interaction. PrivateLink provides one-way access to services deployed in other VPCs over private connections. You do not need to create an Internet egress such as an NAT gateway or an EIP. PrivateLink provides higher data security and network quality because data is not transmitted over the Internet.
Network Load Balancer (NLB) instances can be used as service resources by the endpoint services of PrivateLink. NLB instances receive requests from clients and forward the requests to backend servers based on the forwarding rules configured for listeners. After you specify an NLB instance as a service resource of an endpoint service, the NLB instance can provide services across multiple zones. You do not need to configure an NLB instance for each zone.
Scenarios
This topic describes how to use ECS instances in VPC 1 to access a General-purpose Network File System (NFS) file system in VPC 2. VPC 1 and VPC 2 reside in the same region and belong to the same Alibaba Cloud account. You must create an NLB instance in VPC 2. The NLB instance is deployed across two zones. Create backend server groups S1 and S2 for the NLB instance, and add the two access ports 111 and 2049 of the NFS file system to S1 and S2. Create an endpoint service and add the NLB instance as a service resource of the endpoint service. Create an endpoint in VPC 1 and connect the endpoint to the endpoint service. If the status of the connection is normal, the ECS instances in VPC 1 can access the NFS file system in VPC 2.
For a Server Message Block (SMB) file system, you need to create only one backend server group and add port 445 to the backend server group for the NLB instance.
The following table describes the planning of the two VPCs. The CIDR blocks of the two VPCs can overlap with each other without affecting each other.
Item | VPC 1 | VPC 2 |
Region | China (Chengdu) | China (Chengdu) |
CIDR block |
|
|
vSwitch zone |
|
|

Limits
When you create an endpoint service, select a region that supports both PrivateLink and NLB instances. For more information about the regions that support PrivateLink and NLB instances, see Regions and zones that support PrivateLink and Regions and zones in which NLB is available.
A connection can be established between an endpoint and an endpoint service only if they are deployed in the same zone. The zones where endpoints are deployed must be a subset of the zones where the service resources of endpoint services are deployed. Therefore, we recommend that you select all zones or as many zones as possible in a region when you deploy the service resources of endpoint services. This way, different endpoints can access the service resources.
By default, PrivateLink cannot be accessed over IPv6. If you need to access PrivateLink over IPv6, contact your account manager.
You can use PrivateLink to mount only General-purpose NAS file systems across VPCs in the same region.
Prerequisites
VPC 1 and VPC 2 in the China (Chengdu) region are created. vSwitches are created in Zone A and Zone B in both VPC 1 and VPC 2. For more information, see Create a VPC with an IPv4 CIDR block.
An ECS instance is created as the mount client in Zone A in VPC 1. A General-purpose NAS file system is created in Zone A in VPC 2. For more information, see Create an instance on the Custom Launch tab and Create a file system.
A security group is created in VPC 1. You can configure security group rules based on your requirements for business and security. For more information, see Create a security group.
Step 1: Create an internal-facing NLB instance
Log on to the NLB console.
In the top navigation bar, select the region in which the NLB instance is deployed.
On the Instances page, click Create NLB.
On the NLB (Pay-As-You-Go) International Site page, configure the parameters and then click Create Now. The following table describes the parameters.
Parameter
Description
Region
Select the region where you want to create an NLB instance. In this example, select China (Chengdu).
Network Type
Select a network type for the NLB instance. In this example, select Internal-facing.
VPC
Select a VPC where you want to deploy the NLB instance. In this example, select VPC 2.
Zone
Select the zones where you want to deploy the NLB instance. You must select at least two zones. In this example, select Chengdu Zone A and Chengdu Zone B and the vSwitches in both zones.
IP Version
Select an IP version for the NLB instance.
IPv4: If you select this option, the NLB instance can be accessed only by IPv4 clients.
Dual-stack Networking: If you select this option, the NLB instance can be accessed by IPv4 and IPv6 clients.
Instance Name
Enter a name for the NLB instance.
Resource Group
Select the resource group to which the NLB instance belongs. In this example, select Default Resource Group.
Service-linked Role
When you create an NLB instance for the first time, you must click Create Service-linked Role to create a service-linked role.
Step 2: Create a backend server group for the NLB instance
In the left-side navigation pane, choose NLB > Server Groups.
In the top navigation bar, select a region.
On the Server Groups page, click Create Server Group.
In the Create Server Group dialog box, configure the parameters and then click Create. The following table describes the parameters.
Parameter
Description
Server Group Type
Select the type of the server group that you want to create. In this example, select IP.
Server Group Name
Enter a name for the server group. In this example, enter
S1.VPC
Select the VPC to which the backend server group belongs. In this example, select VPC 2.
Backend Server Protocol
Select a backend protocol. In this example, select TCP.
Scheduling Algorithm
Select a scheduling algorithm. Weighted Round-Robin is selected by default. In this example, retain the default setting.
IPv6 Support
Specify whether to enable IPv6.
If you enable IPv6, you can add IPv4 and IPv6 backend servers to the server group.
If you do not enable IPv6, you can add only IPv4 backend servers to the server group.
NoteIf IPv6 is disabled for the VPC that you select for the server group, IPv6 is disabled for the server group by default.
Enable Connection Draining
After connection draining is enabled, connections to backend servers remain open during the specified timeout period even if the backend servers are removed or if they fail health checks.
Connection Draining Timeout Period: If you enable connection draining, you must specify a timeout period.
The feature is disabled by default. In this example, retain the default setting.
Client IP Preservation
Specify whether to enable client IP preservation. You cannot enable client IP preservation for a server group of the IP type. If you want the server group to retrieve client IP addresses, enable Proxy Protocol for the associated listener.
Enable All-port Forwarding
Specify whether to enable all-port forwarding. After all-port forwarding is enabled, you do not need to specify a port when you add a backend server. The NLB instance forwards requests to a backend server based on the frontend port.
NoteIf you enable all-port forwarding for your listener, you must enable this feature for the backend server group.
The feature is disabled by default. In this example, retain the default setting.
Enable Health Check
Specify whether to enable the health check feature. The feature is enabled by default. In this example, retain the default setting.
After the health check feature is enabled, you can click Modify to modify the related configurations. In this example, retain the default settings.
After you create the server group, find S1 on the Server Groups page and click its ID.
Click the Backend Servers tab, and then click Add IP Address.
In the Add Backend Server panel, enter the virtual IP address (VIP) of the mount target for the NAS file system and click Next.
You can ping the mount target on the ECS instance to obtain the VIP of the mount target. Example:
Command:
ping 19f04a4****-i****.cn-chengdu.nas.aliyuncs.comSample command output:
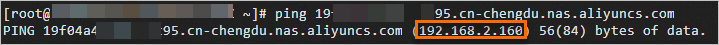
Set the port number and weight of the added NAS file system and click OK.
Set the port number to
111and retain the default value of the weight.After backend server group S1 is created, repeat the preceding steps to create backend server group S2. When you add backend servers, set the port number to
2049.NoteFor an SMB file system, you need to create only one backend server group and set the port number to
445.
Step 3: Configure a listener
In the left-side navigation pane, choose .
On the Instances page, click the ID of the NLB instance that you want to manage.
Click the Listener tab. On the Listener tab, click Create Listener.
On the Configure Listener wizard page, configure the parameters and then click Next. The following table describes the parameters.
Parameter
Description
Listener Protocol
Select a listener protocol. In this example, select TCP.
Listen by Port Range
Specify whether to enable listening by port range. If you enable this feature, the NLB instance listens on all ports in a specific port range, and redirects requests destined for the ports to the backend servers. The feature is disabled by default. In this example, retain the default setting.
Listener Port Range
Specify the listening port that is used to receive and process requests. In this example, select
111.NoteFor an SMB file system, select
445.Listener Name
Enter a name for the listener.
Advanced Settings
You can click Modify to modify the advanced settings. In this example, use the default advanced settings.
In the Server Group step, select backend server group S1 created in Step 2 and click Next.
ImportantThe selected backend server group must match the listening port. Otherwise, the NAS file system cannot be mounted.
On the Configuration Review wizard page, confirm the configurations and click Submit.
In the NLB Configuration Wizard message, click OK. Then, return to the Instances page.
If the health check status of the listener is Healthy, the backend server (VIP of the NAS file system) can process the requests forwarded by the NLB instance.
Repeat Step 4 to Step 7. Set the listening port to
2049and set Server Group to S2.NoteFor an SMB file system, you only need to configure listening port 445.
Step 4: Create an endpoint service
Log on to the endpoint service console.
In the top navigation bar, select the region where you want to create an endpoint service. In this example, select China (Chengdu).
On the Endpoint Service page, click Create Endpoint Service.
On the Create Endpoint Service page, configure the parameters and then click OK. The following table describes the parameters.
Parameter
Description
Service Resource Type
Select the type of the service resource that you want to add to the endpoint service. In this example, select NLB.
Select Service Resource
Select the zones where the service resource is deployed and then select the service resource.
In this example, select Chengdu Zone A and click +Add Service Resource to select Chengdu Zone B. Select the NLB instance created in Step 1 as the service resource for Chengdu Zone A and Chengdu Zone B.
Automatically Accept Endpoint Connections
Specify whether the endpoint service automatically accepts connection requests from endpoints. In this example, select No.
Enable Zone Affinity
Specify whether to first resolve the domain name of the nearest endpoint that is associated with the endpoint service. In this example, select No.
Resource Group
Select the resource group to which the endpoint service belongs.
Description
Enter a description for the endpoint service.
Step 5: Create an endpoint
Log on to the endpoint console.
In the top navigation bar, select the region where you want to create an endpoint. In this example, select China (Chengdu).
On the Endpoints page, click the Interface Endpoint tab and then click Create Endpoint.
On the Create Endpoint page, configure the parameters for the endpoint and then click OK. The following table describes the parameters.
Parameter
Description
Endpoint Name
Enter a name for the endpoint.
Endpoint Type
Select a type for the endpoint. In this example, select Interface Endpoint.
Endpoint Service
Select the endpoint service.
In this example, click Select Service and select the endpoint service created in Step 4: Create an endpoint service.
VPC
Select the VPC to which the endpoint belongs. In this example, select VPC 1.
Security Groups
Select the security group that you want to associate with the elastic network interface (ENI) of the endpoint. The security group is used to control data transfer from VPC 1 to the endpoint ENI.
NoteMake sure that the rules in the security group allow clients to access the endpoint ENI.
Zone and vSwitch
Select the zone where the endpoint service is deployed and select a vSwitch in the zone. The system automatically creates an endpoint ENI and attaches it to the vSwitch.
In this example, select Chengdu Zone A and a vSwitch in Chengdu Zone A. Then, click +Add vSwitch, select Chengdu Zone B, and then select a vSwitch in Chengdu Zone B.
Resource Group
Select the resource group to which the endpoint belongs.
Description
Enter a description for the endpoint.
After you create the endpoint, you can view the domain names and IP addresses of the zones.
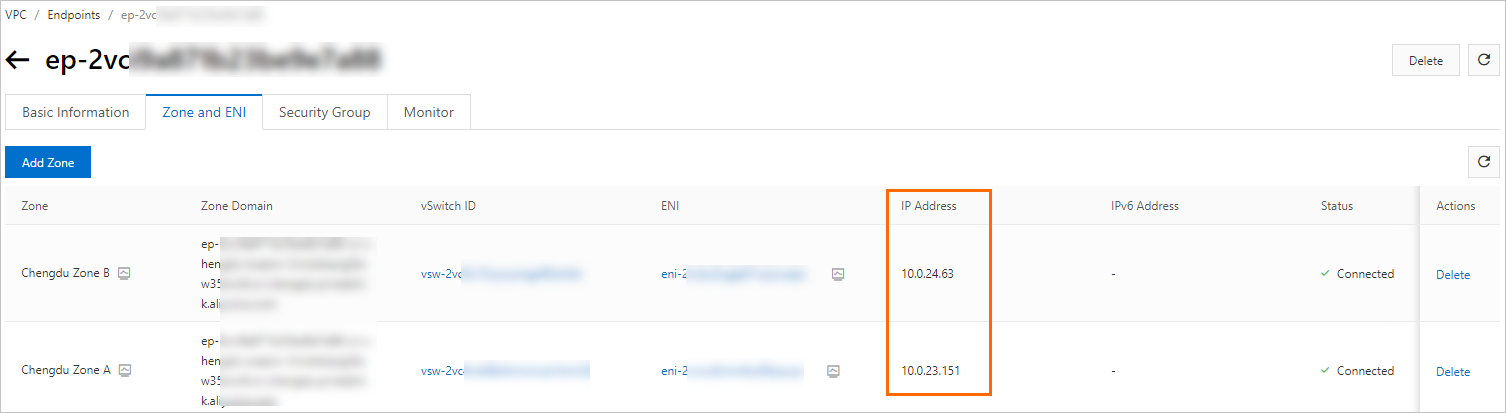
Step 6: Accept connection requests
To establish an endpoint connection, the endpoint service must accept the connection requests from the associated endpoint. Then, VPC 1 can use the endpoint to access the endpoint service.
Skip this step if you set the Automatically Accept Endpoint Connections parameter to Yes in Step 4.
Log on to the endpoint service console.
In the top navigation bar, select the region where the endpoint service is created. In this example, select China (Chengdu).
On the Endpoint Service page, find the endpoint service that you created in Step 4 and click its ID.
On the details page of the endpoint service, click the Endpoint Connections tab, find the endpoint that you want to manage, and then click Allow in the Actions column.
After the connection requests are accepted, the state of the endpoint connection changes from Disconnected to Connected. Then, the endpoint service can process requests from the endpoint. You can use the domain names and IP addresses of the zones that are generated in Step 5 to access the endpoint service.
Step 7: Mount the file system
Connect to the ECS instance. For more information, see Methods for connecting to an ECS instance.
Test the network connectivity between VPC 1 and VPC 2.
In this example, Telnet is used to test the network connectivity. Make sure that Telnet is installed. Make sure that the IP addresses of the endpoint generated in Step 5 can be pinged. Run the following command. Replace the IP address and port number of the endpoint based on your business requirements.
telnet 10.0.23.151 2049If no error message is returned after you run the command, the network between VPC 1 and VPC 2 is connected.
Mount the file system.
Install an NFS client. For more information, see Step 1: Install an NFS client.
NoteFor more information about how to mount a file system on Windows, see Mount an SMB file system on a Windows ECS instance.
Mount the file system.
Use an IP address of the endpoint generated in Step 5 to mount the file system. Run the following command:
sudo mount -t nfs -o vers=3,nolock,proto=tcp,rsize=1048576,wsize=1048576,hard,timeo=600,retrans=2,noresvport 10.0.23.117:/ /mntNoteTo mount a file system on Windows, run the following command:
net use Z: \\10.0.23.151\myshare
What to do next
If you no longer use the NAS file system on the ECS instance, unmount the file system before you delete resources such as the NLB instance and endpoint. If you delete resources such as the NLB instance and endpoint before you unmount the file system, the operating system may give a slow response or does not respond.
Release the file system
For more information about how to unmount a file system, see Unmount a file system by running a command.
If you no longer use NAS to store data or want to suspend the NAS service, release the NAS file system. For more information, see Release a NAS file system.
Release the NLB instance
For more information, see Release an NLB instance.
Release the endpoint
For more information, see Delete an endpoint service.
References
You can also use Cloud Enterprise Network (CEN) to mount a file system across VPCs in the same region. For more information, see Use CEN to mount a file system across VPCs in the same region.
For more information about how to mount a file system across regions or accounts, see Use CEN to mount a file system across accounts and regions.
For more information about how to mount a file system in an on-premises data center, see Access file systems in on-premises data centers.
For more information about how to migrate data from an on-premises storage system or OSS bucket to a NAS file system, see Data migration.