ApsaraVideo Live supports HTTPS secure acceleration and force redirect. This topic describes how secure acceleration works, its benefits, usage, and important notes.
Background
Because the Hypertext Transfer Protocol (HTTP) transmits content in plaintext and does not provide data encryption, data can be easily intercepted and read during transmission.
Overview
ApsaraVideo Live supports HTTPS secure acceleration and force redirect. To use force redirect, you must first configure an HTTPS certificate.
HTTPS:
Hypertext Transfer Protocol Secure (HTTPS) is a secure version of HTTP. Unlike HTTP, which transmits content in plaintext, HTTPS uses the Secure Sockets Layer (SSL)/Transport Layer Security (TLS) protocol for encapsulation. The security of HTTPS is based on SSL/TLS.
HTTPS provides identity verification and encrypted communication. It is widely used for secure communications over the World Wide Web. According to a 2017 report from the Electronic Frontier Foundation (EFF), more than half of all web traffic worldwide is now encrypted using HTTPS.
Force redirect:
This feature redirects client requests to points of presence (POPs) over HTTP or HTTPS.
If you enable HTTPS secure acceleration for your accelerated domain name, you can configure custom settings to force redirect requests from end users. For example, after you enable Enable HTTPS, if an end user initiates an HTTP request, the server returns an HTTP 301 status code to redirect the request to HTTPS, as shown in the following figure.
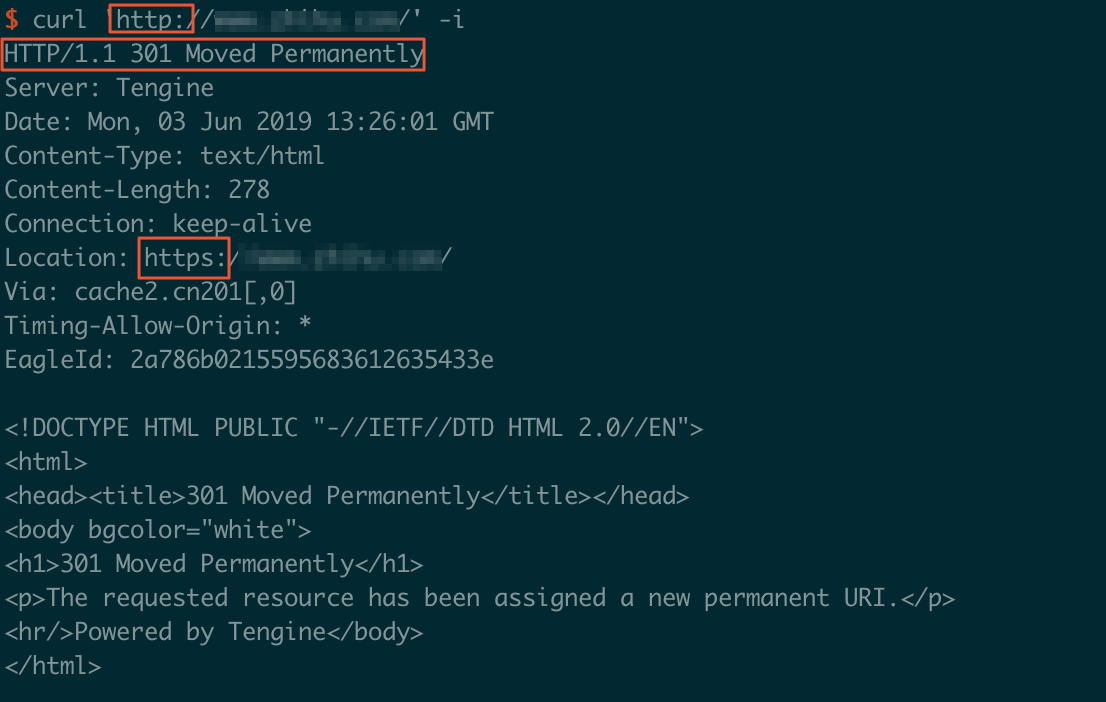
How it works
When you enable HTTPS in the ApsaraVideo Live console, requests between clients and ApsaraVideo Live nodes are encrypted using HTTPS. When an ApsaraVideo Live node retrieves a resource from the origin server to return to a client, the protocol used for the connection to the origin server depends on the origin server's configuration. We recommend that you configure and enable HTTPS on your origin server to implement end-to-end HTTPS encryption.
The following figure shows the HTTPS encryption flow.

The client initiates an HTTPS request.
The server generates a public key and a private key. You can create the key pair yourself or obtain it from a professional organization.
The server sends the public key certificate to the client.
The client verifies the certificate.
If the certificate is valid, the client generates a random number (key). The client then uses the public key to encrypt the random number and sends it to the server.
If the certificate is invalid, the SSL handshake fails.
NoteCorrectness includes the following:
The certificate has not expired.
The certificate authority (CA) that issued the server certificate is trusted.
The issuer's public key can correctly decrypt the digital signature on the server certificate.
The domain name on the server certificate matches the actual domain name of the server.
The server uses its private key to decrypt the message and obtain the random number (key).
The server uses the key to encrypt the data for transmission.
The client uses the key to decrypt the encrypted data from the server to read the content.
Benefits
Secure transmission: HTTPS secures data transmission and effectively prevents risks such as eavesdropping, tampering, impersonation, and hijacking that are associated with plaintext HTTP.
Information encryption: Critical information is encrypted during data transmission. This prevents sensitive information leaks that can occur if a session ID or cookie is captured.
Data integrity: Data integrity is verified during transmission to prevent man-in-the-middle (MITM) attacks, such as DNS or content hijacking and tampering.
Industry standard: Major browsers mark HTTP as insecure, which affects user experience and access security. HTTPS is the industry standard. It supports HTTP/2, improves search engine ranking, and enhances user experience.
We strongly recommend that you upgrade your access protocol to HTTPS to improve security and user experience.
How to use
HTTPS secure acceleration
To access resources over HTTPS and enable secure acceleration, you must configure an HTTPS certificate. For more information about certificates, see Certificate formats.
You can configure HTTPS secure acceleration in the ApsaraVideo Live console or by calling an API operation.
To use the console, see Configure HTTPS secure acceleration.
To use an API, call the SetLiveDomainCertificate operation to set the domain name certificate.
Related API operations:
API operation | Description | References |
SetLiveDomainCertificate | Enables or disables the certificate feature for a domain name and modifies certificate information. | |
DescribeLiveCertificateList | Queries a list of certificates. | |
DescribeLiveCertificateDetail | Queries the details of a certificate. | |
BatchDeleteLiveDomainConfigs | Deletes the configurations of multiple domain names at a time. |
Force redirect
Before you configure force redirect, ensure that an HTTPS certificate is configured.
You can configure force redirect in the ApsaraVideo Live console or by calling an API operation.
To use the console, see Configure force redirect.
To use an API, call the BatchSetLiveDomainConfigs operation to set up force redirect.
Related API operations:
API operation | Description | References |
BatchSetLiveDomainConfigs | Configures multiple domain names at a time. You can configure HTTPS force redirect using the https_force record in the Functions parameter. |
Notes
Configuration | Description |
Disable and Enable HTTPS |
|
Upload a certificate/private key |
|
View a certificate | You can view a certificate. However, you cannot view the private key because it contains sensitive information. Keep your certificate information secure. |
Modify or edit a certificate | You can modify or edit a certificate. Note that an updated certificate takes one hour to take effect. Proceed with caution. |