ESA provides SSL/TLS protocol configurations to encrypt your network traffic. This prevents data theft and tampering.
Terms
SSL/TLS protocol and certificates
Secure Sockets Layer (SSL) is a security protocol that operates between the TCP/IP protocol and application-layer protocols. It is used to authenticate server identities and encrypt communication data. The Internet Engineering Task Force (IETF) standardized this protocol and named it Transport Layer Security (TLS). SSL and TLS are often referred to collectively as SSL/TLS.
SSL/TLS certificates are digital certificates issued by a certificate authority (CA). They are used for website identity authentication and data encryption to ensure the confidentiality and integrity of data transfer.
HTTPS is a secure extension of the HTTP protocol. It uses SSL/TLS certificates to enable encrypted transmission, which ensures website identity authentication and data security.
Use cases
Improved security: HTTPS encrypts data transmission to prevent eavesdropping, tampering, and hijacking. This protects sensitive user information, such as session IDs and cookies, from being disclosed.
Optimized user experience: The HTTP protocol can cause end-user devices to display an "insecure" warning, which significantly reduces user trust in a website. Using HTTPS prevents this issue.
Search engine optimization: Major search engines prioritize HTTPS websites, which helps improve search rankings.
End-to-end data transfer over HTTPS
SSL/TLS configurations are divided into two parts: the access link and the origin fetch link.
Access
The access link is the encrypted connection between the client and the ESA point of presence (POP). You can configure the related features in Edge Certificate and Client Certificate.
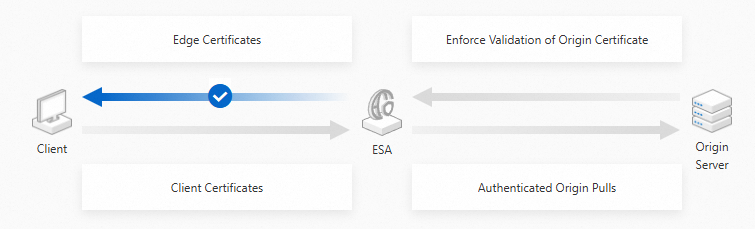
Edge Certificate: This is used for one-way authentication of the ESA POP by the client. After you configure the certificate on the ESA POP and enable the SSL/TLS feature, clients can access your service over an encrypted HTTPS connection.
The following figure shows the encryption flow for edge certificates:
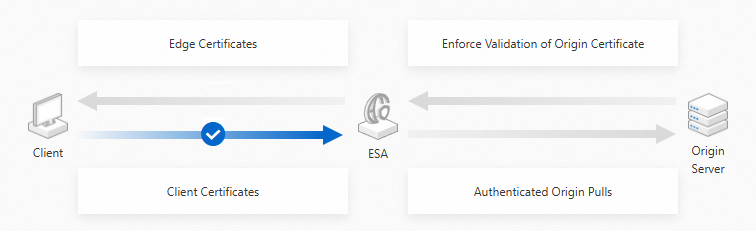
Client Certificate: This is used for mutual authentication (mTLS) scenarios. When you enable mTLS, you must install a digital certificate issued by ESA on the client and enable the verification feature. After this feature is enabled, ESA enforces client certificate validation to ensure mutual identity authentication.
The following figure shows the encryption flow for client certificates:
Origin fetch
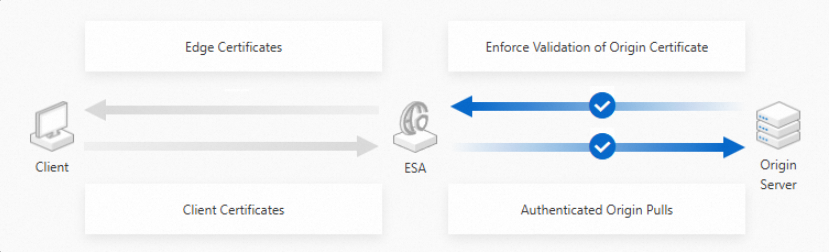
The origin fetch link is the encrypted connection between the origin server and the ESA POP. You can configure the origin protocol and port, origin certificate verification, and mutual authentication for origin fetch.
Origin protocol and port: Specifies the origin fetch protocol (HTTP or HTTPS) and the corresponding port.
: When you enable origin certificate verification, ESA validates the certificate's effectiveness, such as whether it has expired or passed CA verification, and disconnects invalid connections.
Mutual authentication for origin fetch: When you enable mutual authentication for origin fetch, ESA sends its certificate to the origin server. The origin server then uses this certificate to authenticate the identity of ESA.
The following figure shows the encryption flow for origin fetch:
Features
Feature | Description | |
Edge Certificate | Add a CNAME record to your site's authoritative DNS. This lets you host the Domain Control Validation (DCV) check required for free certificate applications on ESA. ESA then automatically issues and renews your free certificates. | |
You can use the Always Use HTTPS feature to force redirect client requests to ESA points of presence (POPs) from HTTP to HTTPS. | ||
When a client sends an HTTPS request to an Edge Security Acceleration (ESA) edge node, the node responds and starts the Transport Layer Security (TLS) handshake. The client and the node negotiate a compatible cipher suite and protocol version to ensure secure bidirectional data transmission. You can adjust the TLS cipher suite and protocol version as needed. | ||
OCSP is a protocol provided by CAs for clients to verify the legitimacy and validity of certificates in real time. Each time a client initiates a request, the client sends an OCSP query to the CA to verify the certificate. Frequent OCSP queries lower the efficiency of the Transport Layer Security (TLS) handshake and reduce access speed. | ||
Opportunistic encryption enables browsers to access HTTP links over an encrypted TLS connection. This enhances security for websites that have not fully migrated to HTTPS. | ||
Enable HTTP Strict Transport Security (HSTS) to force clients, such as browsers, to connect to Edge Security Acceleration (ESA) points of presence (POPs) using HTTPS. This improves connection security. | ||
Client Certificate | You can use the Certificate Authority (CA) provided by ESA to create client certificates. You can then deploy the generated client certificates on your mobile applications. ESA generates a unique CA for each account. By default, nodes trust all client certificates issued by ESA. | |
By binding a client certificate to a specific domain name, you can implement mutual authentication (mTLS). This ensures that only users with valid client certificates can access specific services or resources. | ||
Configure Web Application Firewall (WAF) rules to block requests that fail client certificate authentication. | ||
Origin Certificate | If configured, ESA POPs request resources using your specified origin protocol and port. | |
By default, ESA does not validate the origin certificate when origin fetch is over the HTTPS protocol. To prevent malicious hijacking of the origin fetch traffic, enable the origin certificate verification feature when you want a higher security for your website. Once enabled, ESA checks the origin server's certificate details such as the expiration time, domain name, and root verification. If the verification fails, the back-to-origin handshake fails, and a 502 status code is returned to the client. | ||
Mutual Transport Layer Security (mTLS) is an extension of the TLS protocol. mTLS requires the client and server to authenticate each other. |
Availability
Certificate | Entrance | Pro | Premium | Enterprise |
Number of free certificates for a single domain name | 10 | 30 | 50 | 100 |
Number of custom certificates | 5 | 10 | 20 | 50 |