ESA monitors traffic in real time to detect attack patterns, such as SYN floods, ACK floods, and CC attacks. When ESA detects unusual traffic, it responds quickly to block malicious data and allow legitimate traffic to pass through, ensuring business continuity and stability.
How to protect against DDoS attacks
During a DDoS attack, an attacker floods a web server with fake access requests. This exhausts server resources and prevents the server from responding to legitimate users. To effectively defend against these attacks, you must intercept and manage requests before they reach the server.
ESA uses Anti-DDoS, WAF rules, and smart cache policies to build a multilayer defense system. This system effectively blocks malicious requests, reduces server load, and ensures legitimate traffic passes through efficiently.

Defend against attacks with Anti-DDoS
ESA has built-in DDoS mitigation capabilities and offers two protection levels based on the subscription plan: Basic DDoS Protection and Best-effort protection.
DDoS basic protection
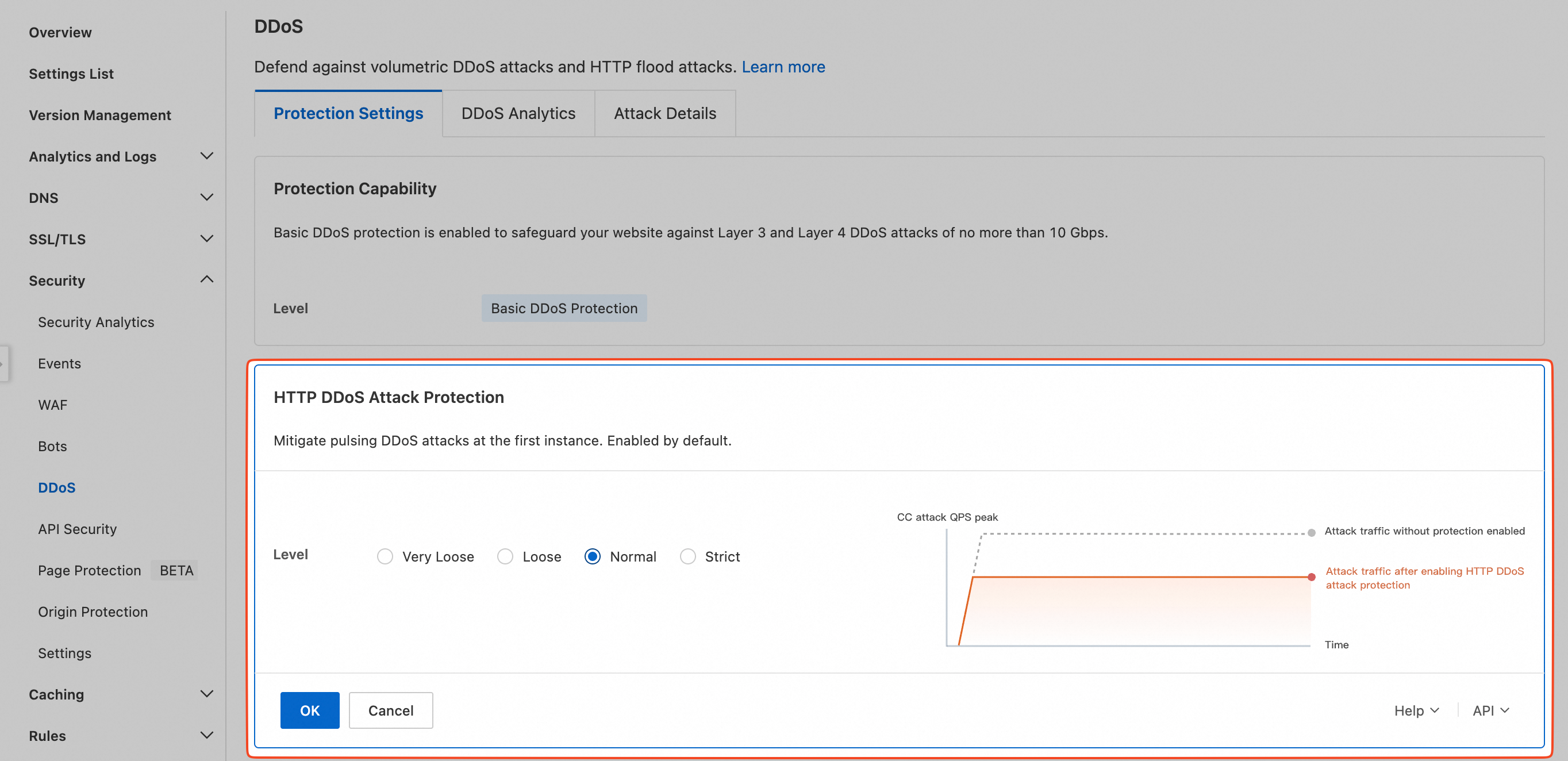
ESA enables DDoS mitigation capabilities by default for users of the Entrance, Pro, Premium, and Enterprise plans. No configuration is required. ESA automatically defends against DDoS attacks of up to 10 Gbps and CC attacks of up to 100,000 queries per second (QPS). (In this context, CC attacks refer to requests to your site that are intercepted by ESA, based on your configured rules and the built-in security rules of ESA.) When an attack occurs, ESA provides best-effort defense at its points of presence (POPs). However, the attack may affect acceleration performance. Basic DDoS Protection does not guarantee a specific time frame for mitigating the attack's impact.
If a site is at high risk of DDoS attacks or requires stable protection, contact us to upgrade to the Enterprise plan.
Best-effort protection
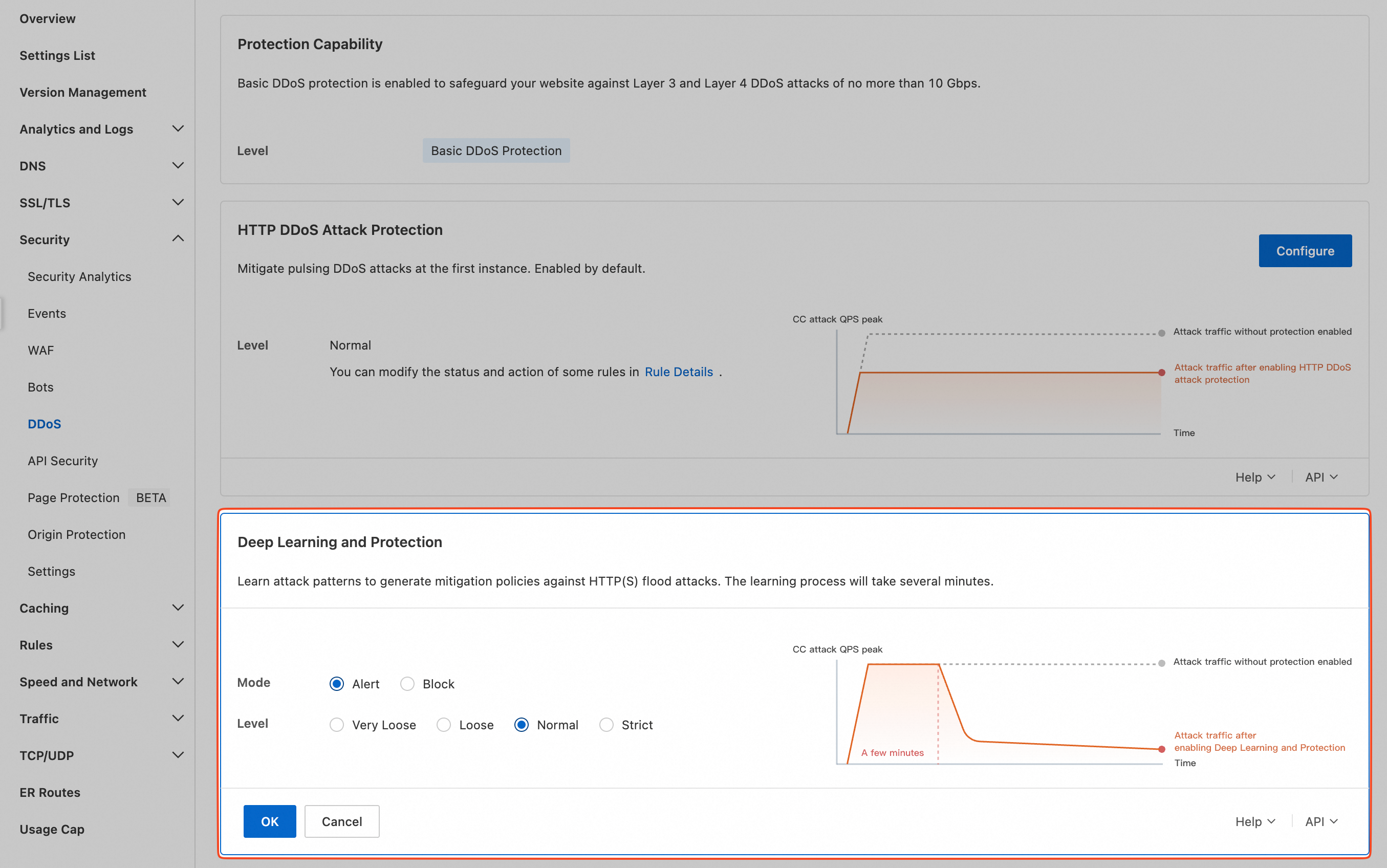
Enterprise users can purchase the Best-effort Protection add-on. With Best-effort Protection, ESA enables the HTTP DDoS Attack Protection and Deep Learning and Protection features by default. The HTTP DDoS Attack Protection feature takes effect in real time. It uses built-in general mitigation rules, which are based on extensive historical attack and defense data, to block sudden surges in HTTP attacks. This prevents many HTTP requests from reaching the origin server and consuming its resources. The Deep Learning and Protection feature continually learns attack patterns during an attack and intelligently generates dynamic mitigation policies to further enhance protection.
If false positives occur or if the protection needs to be strengthened, you can adjust the levels and modes of HTTP DDoS Attack Protection and Deep Learning and Protection based on business feedback during an attack.
In the ESA console, choose Websites, and then click the target site in the Website column.
In the navigation pane on the left, choose .
On the Protection Settings tab, in the HTTP DDoS Attack Protection section, click Configure. Set the protection level as needed, and then click OK.
In the Deep Learning and Protection section, click Configure. Set the protection level and mode as needed, and then click OK.
Protect web applications with WAF rules
A Web Application Firewall (WAF) acts as a line of defense between a web application and the Internet. It analyzes access requests in real time and filters out malicious traffic to prevent many common network attacks, ensuring application stability.
ESA provides WAF protection features at its global POPs. ESA uses various mitigation policies, such as smart rate limiting, security analysis, rule templates, and custom rules, to scrub and filter traffic. It then returns clean traffic to the server, ensuring the data security of your site.

Reduce origin requests with a cache policy
ESA's cache policy caches website content on globally distributed POPs. When a user requests a resource, the content is served from the nearest POP instead of directly from the origin server.
During a DDoS attack, the cache policy intercepts repeated requests and serves them from POPs. This greatly reduces the traffic that reaches the origin server and effectively mitigates the risk of server overload.

Feature support by plan
Feature | Entrance | Pro | Premium | Enterprise |
Protection level | Basic protection | Basic protection | Basic protection | Best-effort Protection |