Running commands using the principle of least privilege is a best practice for permission management. You can run Cloud Assistant commands as a regular user instead of a root or system user. This topic describes how to use Resource Access Management (RAM) access control to allow a regular user to run Cloud Assistant commands.
Prerequisites
You have created a regular user on the Elastic Compute Service (ECS) instance. This topic uses the regular users user01 and user02 as examples.
Background information
When you run Cloud Assistant commands without specific permissions, they run with the highest permissions on the ECS instance by default. For example, commands run as the root user on Linux instances and as the system user on Windows instances.
For security reasons, you may need to restrict the use of root or system users on ECS instances. You can use a RAM user and configure access policies to prevent root or system users from running Cloud Assistant commands. You can also grant permissions to specific regular users, such as user01 and user02, to run the commands.
Configure a regular user on a Linux instance to run Cloud Assistant commands
To run Cloud Assistant commands only on a Linux instance, follow these steps to prevent a RAM user from running the commands as the root user.
Log on to the Resource Access Management (RAM) console with your Alibaba Cloud account.
Create a RAM user. For more information, see Create a RAM user.
The following table provides an example of the RAM user information.
Name
Example
Logon Name
commandUser
Display Name
commandUser
Access Mode
This topic provides instructions for using Cloud Assistant through the Alibaba Cloud console and OpenAPI. Here, select Console Access and Using permanent AccessKey to access.
NoteSelect an access mode as needed to implement the principle of least privilege.
Set Logon Password
Select Automatically Regenerate Default Password.
Password Reset
Select Required at Next Logon.
Enable MFA
Select Not Required.
After you create the RAM user, save the username, password, and AccessKey.
Create an access policy for Cloud Assistant. For more information, see Create a custom policy.
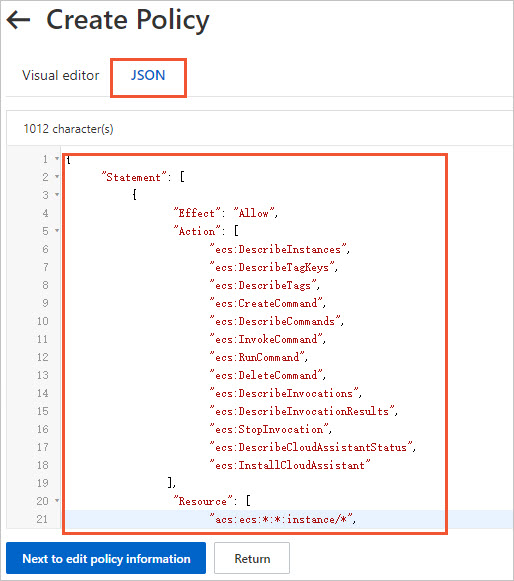
Create a custom policy named commandUserPolicy to specify which users on an ECS instance can run Cloud Assistant commands. The following are two policy examples. You can modify them as needed.
RAM policy to allow specific regular users (user01 and user02) on an ECS instance to run Cloud Assistant commands:
{ "Statement": [ { "Effect": "Allow", "Action": [ "ecs:InvokeCommand", "ecs:RunCommand" ], "Resource": [ "acs:ecs:*:*:instance/*", "acs:ecs:*:*:command/*" ], "Condition": { "StringEquals": { "ecs:CommandRunAs": [ "user01", "user02" ] } } } ], "Version": "1" }NoteTo allow other users, modify or add usernames in the Condition block.
RAM policy to prevent specific users (root and system) on an ECS instance from running Cloud Assistant commands:
{ "Statement": [ { "Effect": "Allow", "Action": [ "ecs:InvokeCommand", "ecs:RunCommand" ], "Resource": [ "acs:ecs:*:*:instance/*", "acs:ecs:*:*:command/*" ], "Condition": { "StringNotEqualsIgnoreCase": { "ecs:CommandRunAs": [ "system", "root" ] } } } ], "Version": "1" }NoteTo restrict other users, modify or add usernames in the Condition block.
Grant the RAM user read-only permissions for ECS and the required permissions for Cloud Assistant. For more information, see Grant permissions to a RAM user.
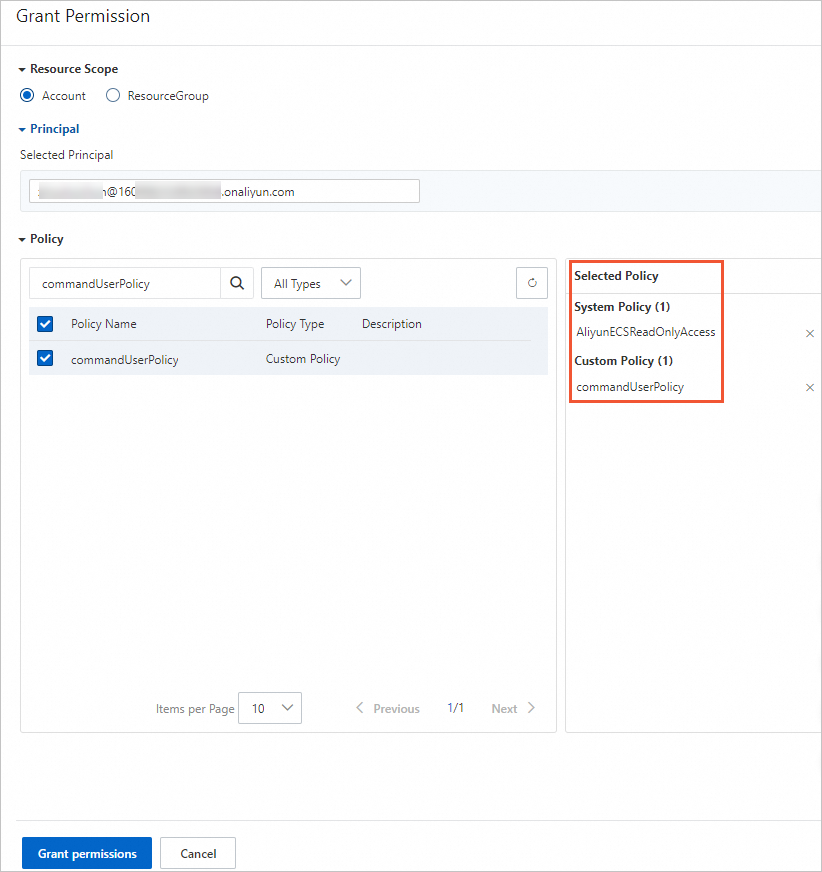
For ECS read-only permissions, select AliyunECSReadOnlyAccess.
For Cloud Assistant permissions, select the commandUserPolicy that you created in the previous step.
Log on to the Alibaba Cloud Management Console as the RAM user.
Run a Cloud Assistant command to verify the configuration. For more information, see Create and run a command.
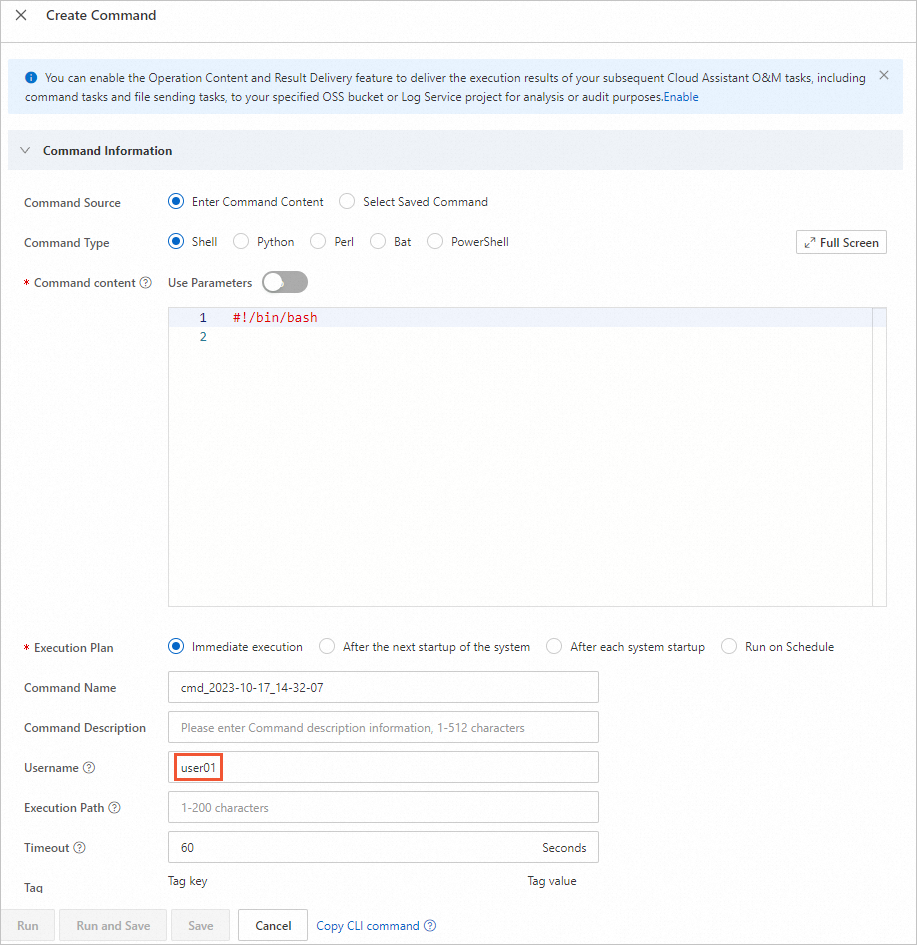
To verify the configuration in the console, specify the user to run the command as shown in the following figure.
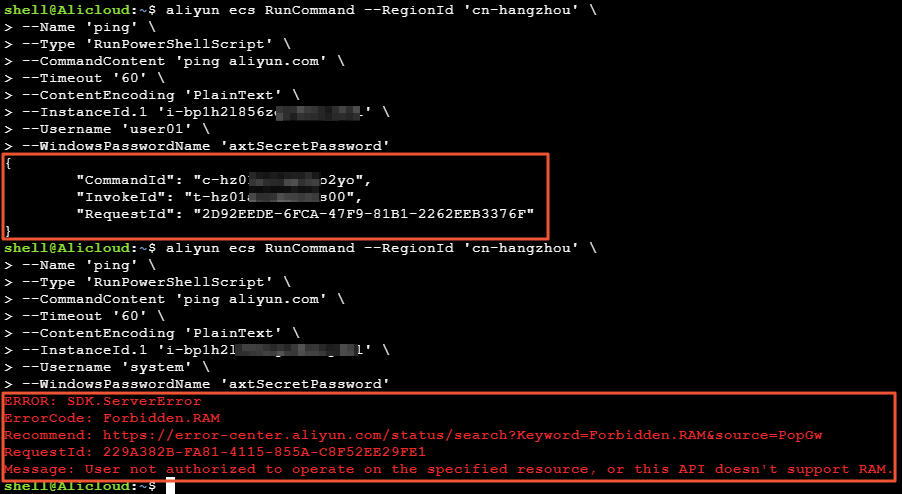
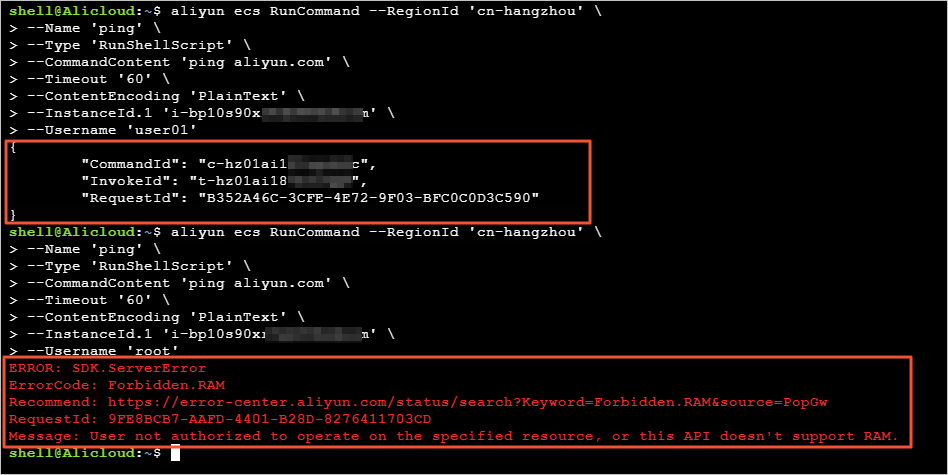
The user user01 can run the Cloud Assistant command, but the root user cannot.
To verify using the command-line interface (CLI), run the command as shown in the following figure. The user user01 can run the Cloud Assistant command, but the root user cannot.
Configure a regular user on a Windows instance to run Cloud Assistant commands
To run Cloud Assistant commands on a Windows instance, you must provide a username and password. For data security, store your Windows logon password in CloudOps Orchestration Service and encrypt it with Key Management Service (KMS). For more information, see What is CloudOps Orchestration Service? and What is Key Management Service?.
Follow these steps to prevent a RAM user from running Cloud Assistant commands as the root or system user.
Log on to the Resource Access Management (RAM) console with your Alibaba Cloud account.
Create a RAM user. For more information, see Create a RAM user.
The following table provides an example of the RAM user information.
Name
Example
Logon Name
commandUser
Display Name
commandUser
Access Mode
This topic provides instructions for using Cloud Assistant through the Alibaba Cloud console and OpenAPI. Here, select Console Access and Using permanent AccessKey to access.
NoteSelect an access mode as needed to implement the principle of least privilege.
Set Logon Password
Select Automatically Regenerate Default Password.
Password Reset
Select Required at Next Logon.
Enable MFA
Select Not Required.
After you create the RAM user, save the username, password, and AccessKey.
Create access policies for Cloud Assistant and KMS. For more information, see Create a custom policy.
Cloud Assistant permissions:
Create a custom policy named commandUserPolicy to specify which users on an ECS instance can run Cloud Assistant commands. The following are two policy examples. You can modify them as needed.
RAM policy to allow specific regular users (user01 and user02) on an ECS instance to run Cloud Assistant commands:
{ "Statement": [ { "Effect": "Allow", "Action": [ "ecs:InvokeCommand", "ecs:RunCommand" ], "Resource": [ "acs:ecs:*:*:instance/*", "acs:ecs:*:*:command/*" ], "Condition": { "StringEquals": { "ecs:CommandRunAs": [ "user01", "user02" ] } } } ], "Version": "1" }NoteTo allow other users, modify or add usernames in the Condition block.
RAM policy to prevent specific users (root and system) on an ECS instance from running Cloud Assistant commands:
{ "Statement": [ { "Effect": "Allow", "Action": [ "ecs:InvokeCommand", "ecs:RunCommand" ], "Resource": [ "acs:ecs:*:*:instance/*", "acs:ecs:*:*:command/*" ], "Condition": { "StringNotEqualsIgnoreCase": { "ecs:CommandRunAs": [ "system", "root" ] } } } ], "Version": "1" }NoteTo restrict other users, modify or add usernames in the Condition block.
KMS permissions:
Create a custom policy named kmsPolicy. The following is an example policy. For more information, see Examples of common authorization policies.
{ "Version": "1", "Statement": [ { "Effect": "Allow", "Action": [ "kms:List*", "kms:Describe*", "kms:Encrypt", "kms:Decrypt", "kms:GenerateDataKey" ], "Resource": [ "*" ] } ] }
Grant the RAM user the required permissions for ECS, OOS, Cloud Assistant, and KMS. For more information, see Grant permissions to a RAM user.
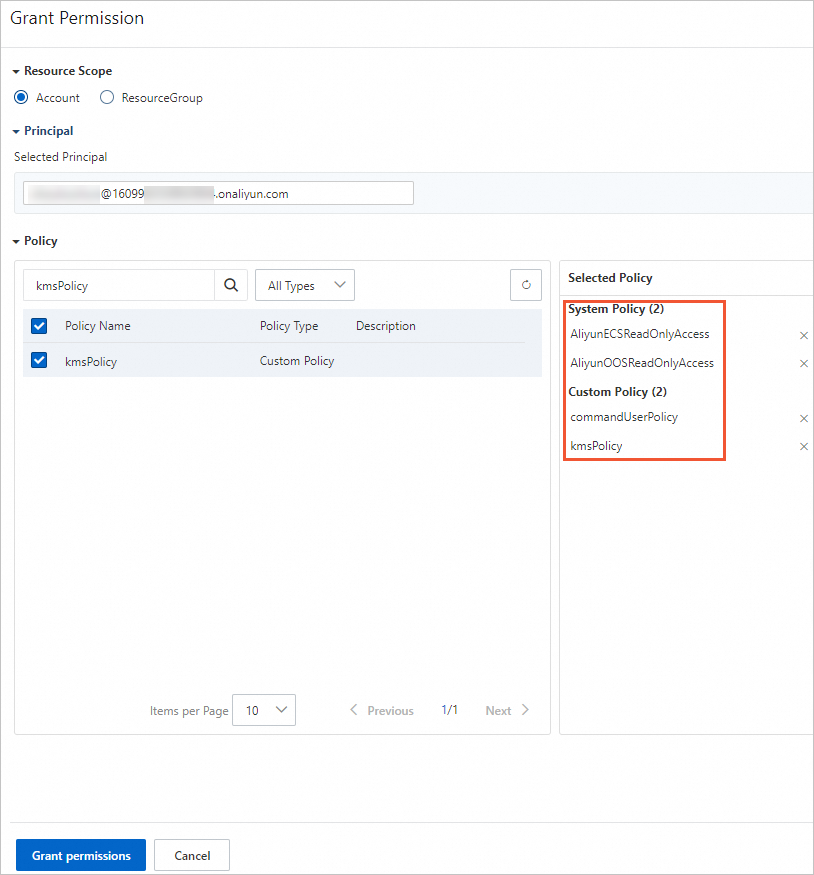
For ECS read-only permissions, select AliyunECSReadOnlyAccess.
For OOS read-only permissions, select AliyunOOSReadOnlyAccess.
For Cloud Assistant permissions, select the commandUserPolicy that you created in the previous step.
For KMS permissions, select the kmsPolicy that you created in the previous step.
Configure a RAM role for the Windows instance.
Create the required permissions for the RAM role. For more information, see Create a custom policy.
The policy is as follows:
{ "Version": "1", "Statement": [ { "Action": [ "kms:GetSecretValue" ], "Resource": "*", "Effect": "Allow" }, { "Action": [ "oos:GetSecretParameter" ], "Effect": "Allow", "Resource": "*" } ] }Create a RAM role. For more information, see Create a RAM role for a trusted Alibaba Cloud service.
The following table provides an example of the configuration.
Name
Example
Principal Type
Select Cloud Service.
Principal Name
From the drop-down list, select Elastic Compute Service / ECS.
Role Name
AxtSecretRamRole
Grant permissions to the RAM role. For more information, see Grant permissions to a RAM role.
Attach the RAM role to the ECS instance. For more information, see Attach an instance RAM role.
Create an encrypted parameter in OOS to store the Windows logon password. For more information, see Create an encrypted parameter.
NoteThe OOS encrypted parameter and the ECS instance must be in the same region. Otherwise, the ECS instance cannot access the stored password.
The following table shows example values for storing the password of the user user01.
Name
Example
Parameter Name
axtSecretPassword
KMS Key ID
Use the default Default Service CMK.
Value
The logon password for the Windows instance. Enter the logon password for the user user01.
Log on to the Alibaba Cloud Management Console as the RAM user.
Run a Cloud Assistant command to verify the configuration. For more information, see Create and run a command.
Run a Cloud Assistant command on a Windows instance to verify that the permission settings are effective.
To verify the configuration in the console, specify the user to run the command and the OOS encrypted parameter that stores the password, as shown in the following figure.
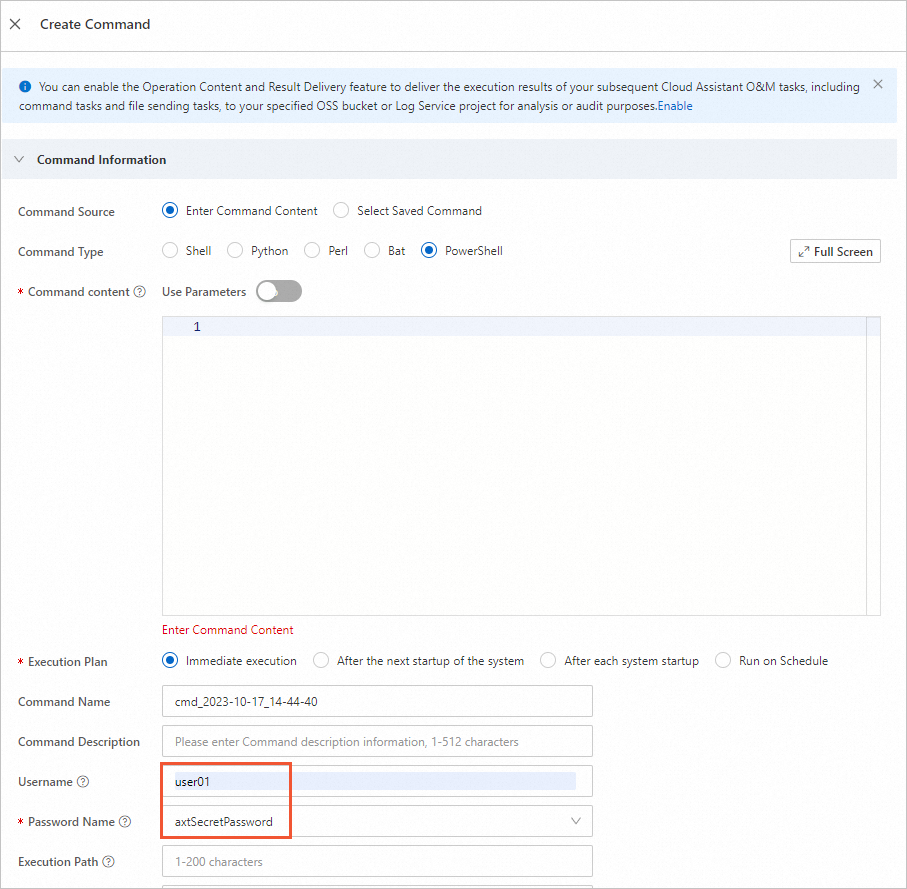
The user user01 can run the Cloud Assistant command, but the system user cannot.
To verify using the CLI, run the command as shown in the following figure. The user user01 can run the Cloud Assistant command, but the system user cannot.