Before you can use Key Management Service (KMS) keys to encrypt Elastic Compute Service (ECS) resources, such as disks, snapshots, and images, you must grant ECS the permissions to access KMS keys. Before you can share encrypted images or snapshots with other Alibaba Cloud accounts, you must grant ECS of the sharee accounts the permissions to access the KMS keys of the sharer account.
Encrypt ECS resources
ECS and KMS are deeply integrated. If you want to encrypt ECS resources, such as disks, snapshots, and images, you can use KMS keys and the envelope encryption technology provided by KMS to encrypt data of the ECS resources. You can use a service key provided by KMS or a customer master key (CMK) that you created. For information about encryption keys, see the Encryption keys section of the "Encrypt cloud disks" topic.
Use service keys
KMS provides service keys that are created and managed by cloud services free of charge for the cloud services to encrypt data. You can select ECS service keys to encrypt specific resources of an ECS instance. The service keys are created by ECS. Therefore, ECS can use the keys without the need to obtain permissions.
Use CMKs
If you do not want to use service keys, you can use self-created or self-managed CMKs. In this case, you must grant ECS the permissions to use the CMKs. To grant ECS the preceding permissions, perform the following steps:
After you confirm to grant ECS the permissions to use the CMKs, Alibaba Cloud creates a system default Resource Access Management (RAM) role named
AliyunECSDiskEncryptDefaultRolefor your account. The role has the permissions to access KMS resources.ECS assumes the RAM role to access the CMKs in KMS.
To confirm the grant of permissions for ECS to use the CMKs, perform the following steps:
The first time you select a CMK in KMS to encrypt ECS resources, such as when you create an encrypted disk, the If you want to select more keys, grant permissions to the RAM role message appears.
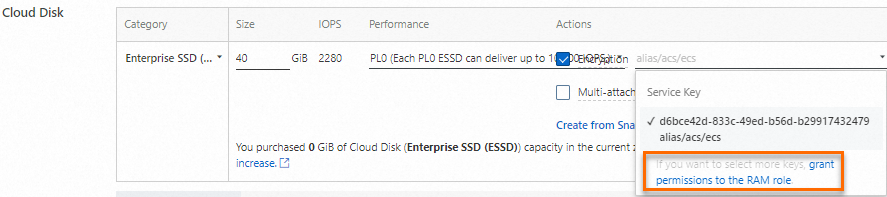
Click Confirm Authorization Policy. The system automatically creates the RAM role named
AliyunECSDiskEncryptDefaultRoleand grants permissions to the RAM role.
After you confirm the authorization, you can select the CMKs that you created in KMS in the ECS console.
Share encrypted resources across accounts
If you want to share an encrypted image or snapshot with another Alibaba Cloud account or a resource directory (sharee), you must grant the sharee the permissions to access the KMS key that encrypts the image or snapshot. The image or snapshot is encrypted by using a KMS key in the current Alibaba Cloud account (sharer). To grant the sharee the preceding permissions, create the default system role in the sharer account, and allow the ECS service of the sharee to assume the default system role of the sharer account and use the KMS service of the sharer account. Perform the following steps:
1. Create a RAM role
Create a RAM role in the Alibaba Cloud account (sharer) that is the trusted entity, in which you want to share resources, such as encrypted snapshots or encrypted images. For more information, see Create a RAM role for a trusted Alibaba Cloud account.
If you want to share an encrypted snapshot, create a RAM role named AliyunECSShareEncryptSnapshotDefaultRole.
If you want to share an encrypted image, create a RAM role named AliyunECSShareEncryptImageDefaultRole.
2. Modify the principal of the RAM role
On the Trust Policy tab, modify the trust policy to specify the account or resource directory with which you want to share the encrypted snapshot or image. For more information, see Edit the trust policy of a RAM role. The following sample code provides examples of the trust policy for the RAM role:
Scenario 1: Share ECS resources with other Alibaba Cloud accounts
{
"Statement": [
{
"Action": "sts:AssumeRole",
"Effect": "Allow",
"Principal": {
"Service": [
"<UID1>@ecs.aliyuncs.com",
"<UID2>@ecs.aliyuncs.com"
]
}
}
],
"Version": "1"
}In the replacement policy, replace <UID1> and <UID2> with the IDs of the Alibaba Cloud accounts with which you want to share ECS resources. If you want to share the encrypted snapshot or image with multiple Alibaba Cloud accounts, specify the ID of each sharee account.
Scenario 2: Share ECS resources with a resource directory
{
"Statement": [
{
"Action": "sts:AssumeRole",
"Effect": "Allow",
"Principal": {
"Service": "*@ecs.aliyuncs.com"
},
"Condition": {
"StringEquals": {
"sts:ServiceOwnerRDId": "<ID of the resource directory>"
}
}
}
],
"Version": "1"
}In the replacement policy, replace <ID of the resource directory> with the ID of the resource directory with which you want to share ECS resources. For information about how to view the ID of a resource directory, see View the basic information about a resource directory.
Scenario 3: Share resources with a folder of a resource directory
{
"Statement": [
{
"Action": "sts:AssumeRole",
"Effect": "Allow",
"Principal": {
"Service": "*@ecs.aliyuncs.com"
},
"Condition": {
"StringLike": {
"sts:ServiceOwnerRDPath": "<ID of the resource directory>/<Root folder ID>/.../<Current folder ID*>"
}
}
}
],
"Version": "1"
}In the trust policy, replace <ID of the resource directory>, <Root folder ID>, and <Current folder ID> with actual values. For information about how to view the resource directory path of a folder, see View the basic information of a folder.
3. Create a custom policy and attach the policy to the RAM role
If the image or snapshot that you want to share is encrypted by using a CMK, you must create a custom policy and attach the policy to the RAM role to allow ECS to access and use the CMK. For more information, see Grant permissions to a RAM role. The following sample code provides an example of a custom policy.
If your image is encrypted by using a service key, you must attach the AliyunKMSFullAccess system policy to the RAM role. For more information, see AliyunKMSFullAccess.
{
"Version": "1",
"Statement": [
{
"Action": "kms:List*",
"Resource": "acs:kms:<ID of the region in which the CMK resides>:<ID of the Alibaba Cloud account to which the CMK belongs>:key",
"Effect": "Allow"
},
{
"Action": [
"kms:DescribeKey",
"kms:TagResource",
"kms:UntagResource",
"kms:Encrypt",
"kms:Decrypt",
"kms:GenerateDataKey"
],
"Resource": "acs:kms:<ID of the region in which the CMK resides>:<ID of the Alibaba Cloud account to which the CMK belongs>:key/<ID of the CMK associated with the ECS resource>",
"Effect": "Allow"
}
]
}Replace <ID of the region in which the CMK resides>, <ID of the Alibaba Cloud account to which the CMK belongs>, and <ID of the CMK associated with the ECS resource> with actual values.
4. Share resources with other Alibaba Cloud accounts
This topic describes the permissions involved in encryption operations. For more information, see the following topics:
