This topic describes how Elastic Compute Service (ECS) enhances operating system security through secure access, operating system hardening, and advanced security measures.
Enhance operating system security through secure access
To enhance operating system access security on ECS instances, three main parts are engaged: using key pairs for instance logon, using Session Manager for password-free logon, and restricting access to or from 0.0.0.0/0 over ports.
Use key pairs for instance logon
Key pairs, which consists of a public and a private key, serve as secure credentials for ECS instance authentication, mitigating the risks associated with weak passwords. Alibaba Cloud default key pairs are generated by using the RSA 2048-bit encryption algorithm. Key pair authentication offers a secure and convenient alternative to traditional username and password methods, with the following benefits:
Key pairs prevent brute-force attacks, unlike conventional passwords.
Key pair logon is more convenient, with a one-time configuration and no need to enter a password in the future.
For more information, see Connect to a Linux instance by using a password or key and Connect to a Linux instance by using an SSH key pair.
Use Session Manager for password-free logon
Besides key pair logon, ECS instances can be accessed securely and conveniently through Session Manager, a feature of Cloud Assistant. This method offers several advantages:
The Web Socket Secure (WSS) protocol is used to establish persistent WebSocket connections between Session Manager Client and the Cloud Assistant server as well as between the Cloud Assistant server and Cloud Assistant Agent. The WSS protocol encrypts persistent WebSocket connections by using the SSL protocol to ensure security.
Session Manager uses the authentication based on Resource Access Management (RAM). When you use Session Manager to connect to instances, you do not need to manage the instance passwords, which avoids security risks due to poor password management.
After WebSocket connections are established between Cloud Assistant Agents installed on instances and the Cloud Assistant servers, you can use Session Manager to connect to the instances, without the need to open ports for inbound traffic on the instances. This way, you can improve the security of the instances.
For more information, see Connect to an instance by using Session Manager.
Restrict access to or from 0.0.0.0/0 over ports
Linux systems typically use SSH on port 22, while Windows systems default to RDP on port 3389 for remote connections. Unrestricted access (0.0.0.0/0 authorization) poses a security threat by allowing potential unauthorized logons. Alibaba Cloud's security groups act as a virtual firewall at the instance level, enabling network access control and providing essential security isolation. For more information, see Overview of security groups and Manage resources associated with security groups.
Operating system hardening
Use OOS patch baseline to automatically update security patches
Alibaba Cloud CloudOps Orchestration Service (OOS) automates task management and execution. The OOS patch baseline feature allows you to scan or install patches for ECS instances based on default or custom patch baselines. You can also select updates such as security-related updates to automatically install patches for ECS instances. For more information, see Overview.
Kernel Live Patching of Alibaba Cloud Linux
Alibaba Cloud Linux provides the Kernel Live Patching (KLP) feature for fixing the common vulnerabilities and exposures (CVEs) and critical bugs of a kernel. KLP can update hotfixes for CVEs or critical bugs of a kernel in a smooth and quick manner without compromising server security and stability. You do not need to restart servers or other business-related task processes, wait until time-consuming tasks are completed, log off, or migrate business. For more information, see Kernel Live Patching.
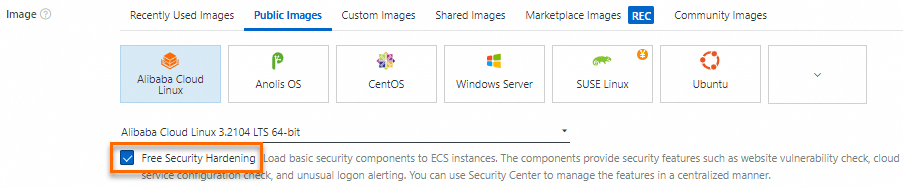
Use free basic security services
Alibaba Cloud provides a suite of basic security services with new ECS instances using public images, including Security Center Basic Edition. This edition offers essential security hardening features such as server vulnerability scanning and abnormal login alerts. While it is optional, enabling this service is highly recommended. If you have advanced security needs, Security Center Advanced Edition and Enterprise Edition are available. For more information, see Basic security services.
Enhance operating system security
ECS further enhances system security in compliance and audit scenarios through log auditing and adherence to standards.
Log audit
Enable logon audit
We recommend that you use Session Manager for instance logon and enable the Session Record Delivery feature of Session Manager. This allows for persistent storage, querying, analysis, and auditing of session records in Simple Log Service (SLS) or Object Storage Service (OSS). For more information, see Use the Session Record Delivery feature.
Enable ActionTrail
ECS is integrated with the ActionTrail service, allowing you to query management events triggered by ECS operations. ActionTrail facilitates the delivery of these events to either SLS Logstores or OSS buckets, providing solutions for real-time auditing and troubleshooting analysis. For more information, refer to Audit events of ECS.
Enable Log Audit Service
In addition to logon audit and ActionTrail, we recommend that you enable the Log Audit Service. This service builds upon the capabilities of Simple Log Service (SLS), offering support for real-time, automated, and centralized log collection from various cloud products across multiple accounts for auditing purposes. Additionally, it facilitates the necessary storage, querying, and aggregation of information for audit compliance.
Compliance
Level 3 compliance images
Alibaba Cloud offers images that meet national Level 3 compliance standards for Multi-Level Protection Scheme (MLPS) 2.0. These images inherently fulfill requirements for identity authentication, access control, and intrusion prevention.
Compliance check
Security Center provides the features of classified protection compliance check and ISO 27001 compliance check. You can use the features to check whether your system meets the requirements of classified protection and ISO 27001. ISO 27001 is an international standard on how to manage information security. For more information, see Use the security check feature.