This topic describes how to push alert notifications to specified Simple Message Queue (formerly MNS) topics when Cloud Config detects non-compliant configuration changes of resources. If you receive a non-compliance alert, Cloud Config uses the relevant functions in Function Compute to automatically remediate these resources.
Prerequisites
A rule is created based on a managed rule. For more information, see Activate Cloud Config and Create a rule based on a managed rule.
SMQ is activated. For more information, see Activate SMQ and authorize RAM users to access SMQ.
Object Storage Service (OSS) is activated and an OSS bucket is created. For more information, see Activate OSS and Create buckets.
Function Compute is activated. For more information, see Quickly create a function.
Scenario
You create a rule function and associate it with the OSS bucket resource type based on the test-oss-bucket-public-read-prohibited managed rule. Cloud Config evaluates all OSS buckets within your Alibaba Cloud account. One of the OSS buckets is evaluated as Non-compliant, as shown in the following figure.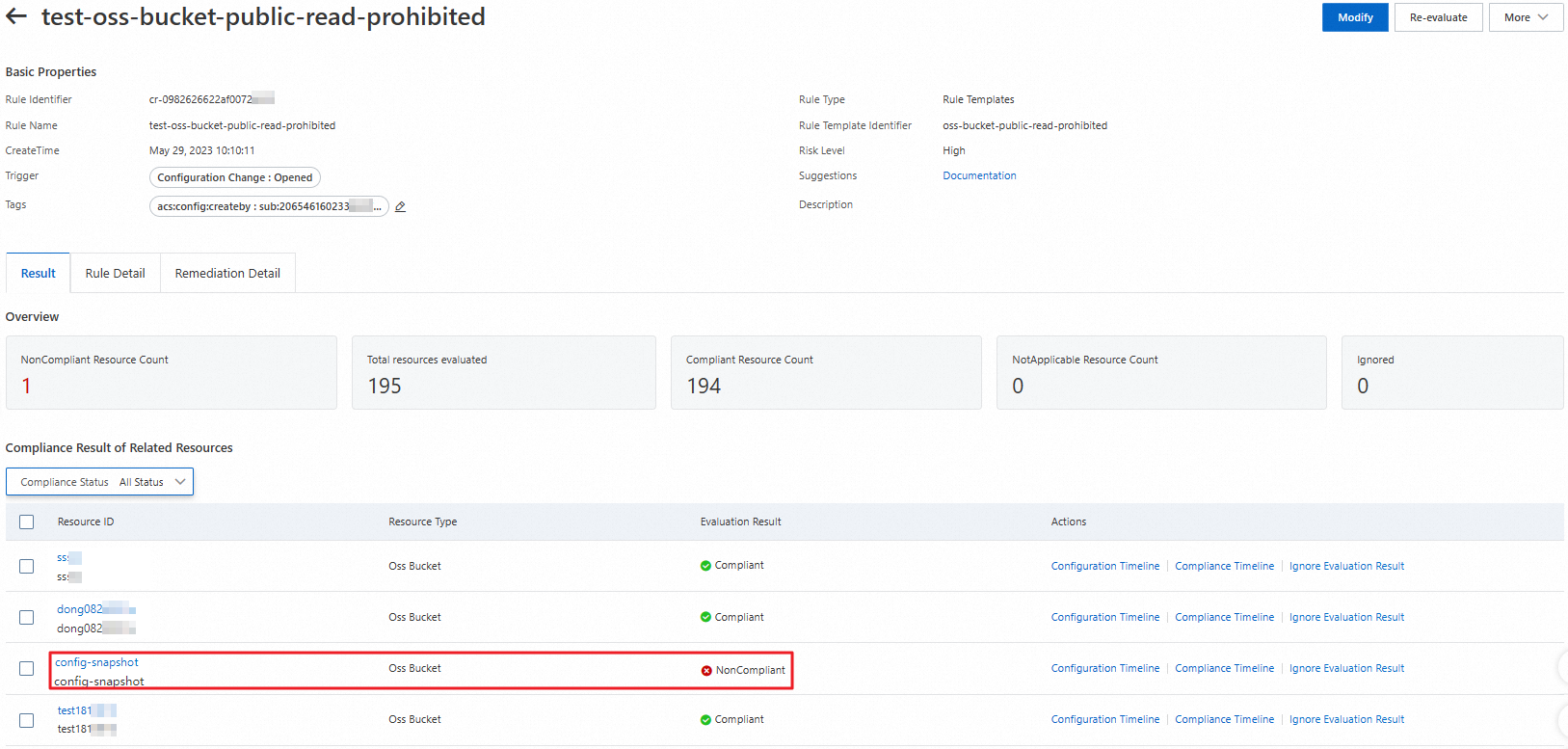
Configuration items
The following sections describe the method to automatically remediate non-compliant resources by using SMQ topics. In this example, the read and write permissions on an OSS bucket are remediated. The following table describes the configuration items that you can specify.
Alibaba Cloud service | Configuration item | Example |
Cloud Config | Managed rule | oss-bucket-public-read-prohibited |
Rule name | test-oss-bucket-public-read-prohibited | |
SMQ | Topic | MNSTestConfig |
Region | Singapore | |
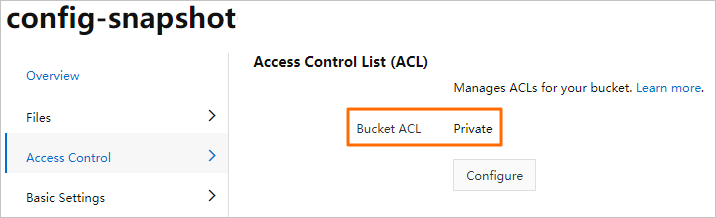
OSS | OSS bucket | config-snapshot |
Bucket ACL | Public read | |
Function Compute | Service | resource_repair |
System policy | AliyunOSSFullAccess | |
Function | oss_repair_acl_trigger | |
Trigger | ConfigRuleNonComplianceMNSTrigger |
Cloud Config is deployed in the Singapore region. To reduce packet loss, we recommend that you specify Singapore as the region for the SMQ topic.
Workflow
The following figure shows how non-compliant resources are automatically remediated by using SMQ topics.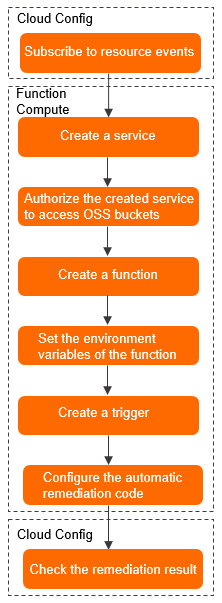
Procedure
Log on to the Cloud Config console. Specify an SMQ topic to which resource non-compliance events are delivered, such as SMQTestConfig.
For more information, see Deliver resource data to an SMQ topic.
Create a service.
Log on to the Function Compute console.
In the left-side navigation pane, click Services & Functions.
In the top navigation bar, select a region. In this example, select Singapore.
On the Services page, click Create Service.
In the Create Service panel, enter resource_repair in the Name field.
Click OK.
Authorize the created service to modify the permissions on the sample non-compliant OSS bucket.
In the left-side navigation pane of the resource_repair service, click Service Details.
In the Role Settings section, click Modify.
Select a role to which the AliyunOSSFullAccess policy is attached.
If no role meets the requirements, click Create Role to create a role in the Resource Access Management (RAM) console. When you create the role, you must set the trusted entity type to Alibaba Cloud Service, set the trusted service to Function Compute, and then attach the AliyunOSSFullAccess policy to the role. For more information, see Create a RAM role for a trusted Alibaba Cloud service.
Click Save.
Create a function.
In the left-side navigation pane of the resource_repair service, click Functions.
Click Create Function.
On the Create Function page, set the Function Name parameter to oss_repair_acl_trigger and the Runtime parameter to Python 3.6. Keep the default settings of other parameters.
Click Create.
Configure the environment variables of the function.
On the details page of the oss_repair_acl_trigger function, click the Configurations tab.
In the Environment Variables section, click Modify.
In the panel that appears, click Add Variable, and specify a name and a value for the environment variable.
Enter prepareRuleName in the Variable field.
The name prepareRuleName is the same as the value of the ENV_RULE_NAME parameter in the automatic remediation code that is used in this example.
Enter test-oss-bucket-public-read-prohibited in the Value field.
The value test-oss-bucket-public-read-prohibited indicates the rule name used in this example.
Click OK.
Create a trigger.
On the details page of the oss_repair_acl_trigger function, click the Triggers tab.
On the Triggers tab, click Create Trigger.
In the panel that appears, Select Simple Message Queue for the Trigger Type parameter.
Configure parameters after you set the Trigger Type parameter to Simple Message Queue.
In this example, use the following settings:
Enter ConfigRuleNonComplianceMNSTrigger in the Name field.
Set the MNS Region parameter to Singapore.
Set the Topic parameter to MNSTestConfig.
Set the Event Format parameter to STREAM.
Set the Role Name parameter to AliyunMNSNotificationRole.
Click OK.
After the trigger is created, notifications of non-compliant events are sent to you when Cloud Config evaluates resource compliance.
Configure the automatic remediation code.
On the details page of the oss_repair_acl_trigger function, click the Code tab.
In the code editor, select the index.py file.
Copy and paste the following code to the index.py file:
# -*- coding: utf-8 -*- import logging import json import os import base64 import binascii import oss2 from aliyunsdkcore.acs_exception.exceptions import ClientException, ServerException IDENTIFIER = 'evaluationResultIdentifier' QUALIFIER = 'evaluationResultQualifier' RULE_NAME = 'configRuleName' ENV_RULE_NAME = 'prepareRuleName' RESOURCE_ID = 'resourceId' REGION_ID = 'regionId' FAIL = 'fail' SUCC = 'success' logger = logging.getLogger() def handler(event, context): logger.info("mns_topic trigger event = {}".format(event)) decoded = None if event: try: decoded = base64.b64decode(event) except binascii.Error as ex: logger.exception('mns_topic trigger event malformed!') return FAIL if not decoded: return FAIL notify_json = json.loads(decoded) if notify_json and IDENTIFIER in notify_json: evaluationResultIdentifier = notify_json.get(IDENTIFIER) if QUALIFIER in evaluationResultIdentifier and RULE_NAME in evaluationResultIdentifier.get(QUALIFIER): evaluationResultQualifier = evaluationResultIdentifier.get(QUALIFIER) configRuleName = evaluationResultQualifier.get(RULE_NAME) # os.environ.get(ENV_RULE_NAME) // Specify the rule name, such as test-oss-bucket-public-read-prohibited. if configRuleName == os.environ.get(ENV_RULE_NAME): if RESOURCE_ID in evaluationResultQualifier and REGION_ID in evaluationResultQualifier: bucket_name = evaluationResultQualifier.get(RESOURCE_ID) region = evaluationResultQualifier.get(REGION_ID) if region and bucket_name: try: remedy_by_fc_assume(context, region, bucket_name) except Exception as ex: logger.exception('remedy fail!') return FAIL def remedy_by_fc_assume(context, region, bucket_name): creds = context.credentials auth = oss2.StsAuth(creds.access_key_id, creds.access_key_secret, creds.security_token) bucket = oss2.Bucket(auth, 'http://oss-' + region + '.aliyuncs.com', bucket_name) bucket.put_bucket_acl(oss2.BUCKET_ACL_PRIVATE) logger.info('bucket {bucket_name} in {region} acl remedy succ.'.format(bucket_name=bucket_name, region=region))NoteThe sample code describes the automatic remediation method of non-compliant resources. The prepareRuleName environment variable is used in this example. For information about how to remediate non-compliant resources by using other parameters, see Examples of resource non-compliance events.
In the code editor, click Deploy in the upper-right corner.
Wait for 10 minutes and view the remediation result.
NoteIf a resource is evaluated as non-compliant based on the rule but no configurations are changed, you must re-evaluate the resource before you perform this step. For more information, see Manually re-evaluate resources.
View the remediation result in the Cloud Config console.
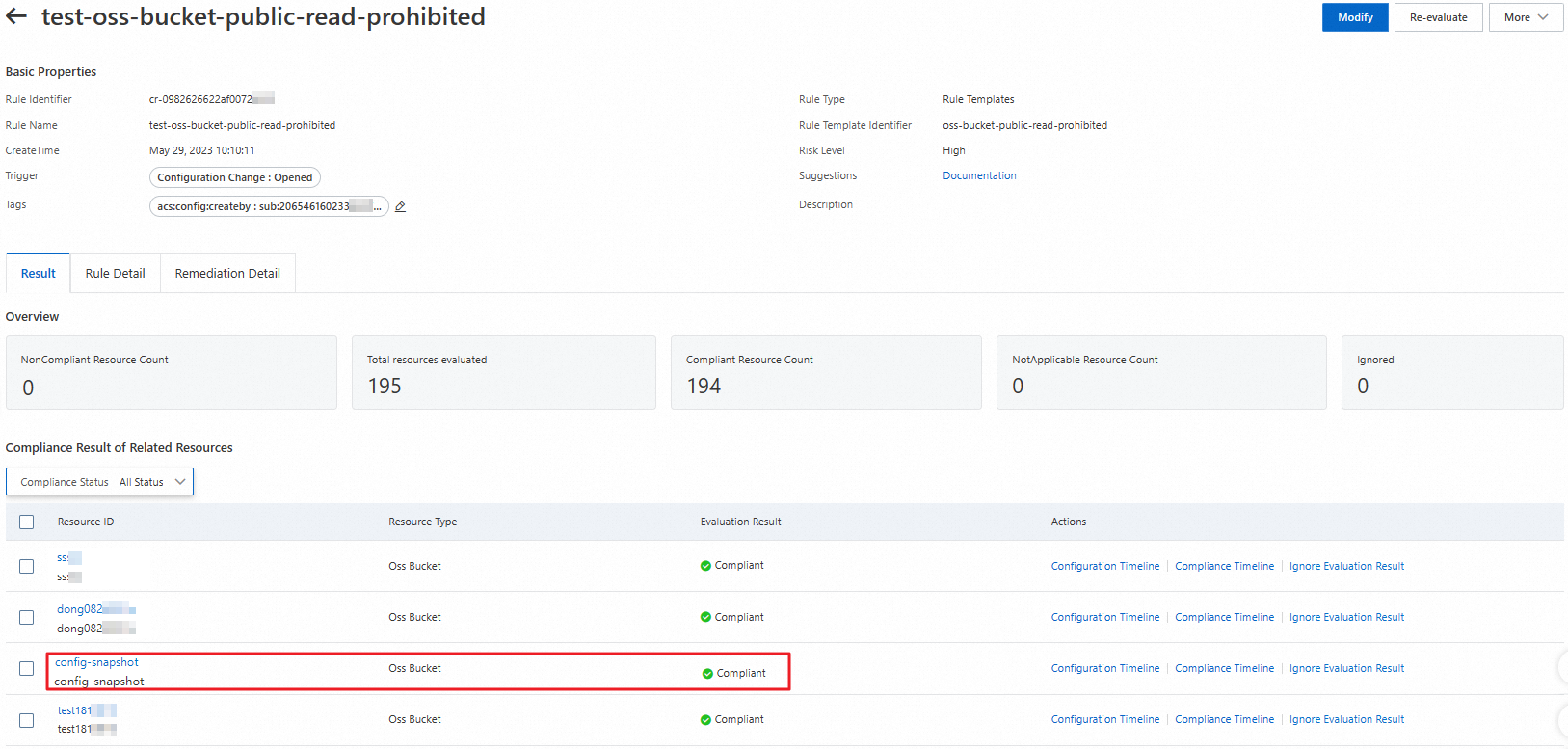
View the remediation result in the OSS console.