After a Cloud Connect Network (CCN) instance is connected to a transit router, the on-premises network associated with the CCN instance can access the Private Zone service through the transit router. You must grant permissions to the CCN instance before the on-premises network can access the Private Zone service. This topic describes how to grant permissions to a CCN instance in different scenarios.
Case 1: Instances in the same account
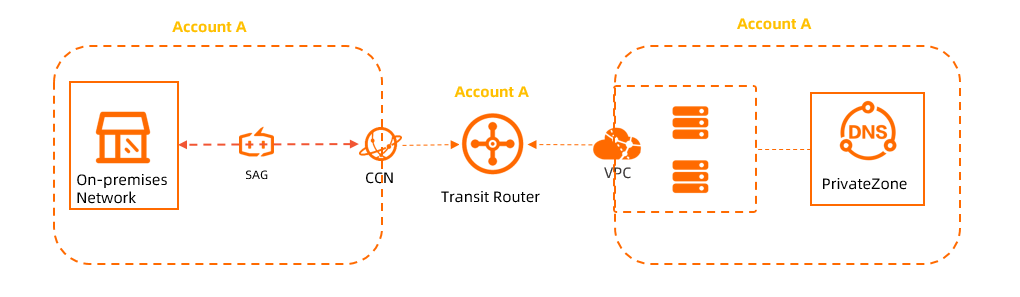
As shown in the figure, the CCN instance, the virtual private cloud (VPC) instance where Private Zone is deployed, and the transit router all belong to the same Alibaba Cloud account. In this scenario, you can grant permissions to the CCN instance directly in the Cloud Enterprise Network (CEN) console. The following table lists the account IDs for each instance.
Resource | Account ID |
transit router | 253460731706911258 |
VPC instance | 253460731706911258 |
CCN instance | 253460731706911258 |
Log on to the CEN console.
On the Instances page, click the ID of the CEN instance that you want to manage.
On the tab, find the transit router in the same region as the VPC associated with Private Zone and click its ID.
On the details page of the transit router, click the Private Zone tab and click Authorize Now. On the quick authorization page of Resource Access Management (RAM), click Authorize.
NoteGrant permissions to Smart Access Gateway (SAG) only when you configure access to Private Zone for the first time. After you grant the permissions, the CCN instance that is connected to the transit router can access Private Zone. The CCN instance is a component of SAG.
After you grant the permissions, a RAM role named AliyunSmartAGAccessingPVTZRole is automatically created for the current account. Go to the RAM console and on the page, search for the role to view its information.
Case 2: CCN in a different account
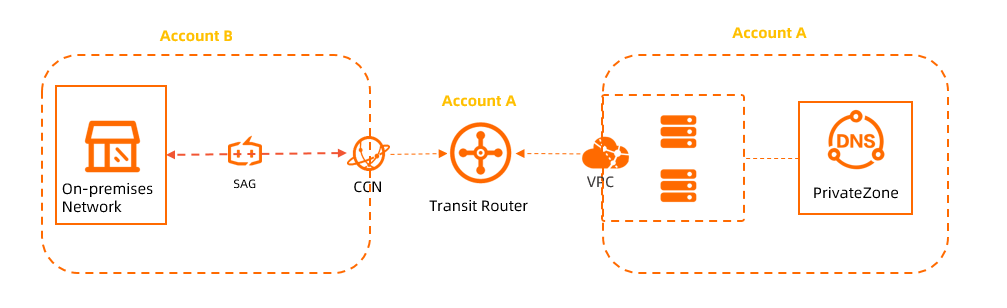
The transit router and the VPC where Private Zone is deployed belong to one Alibaba Cloud account, and the CCN instance belongs to another Alibaba Cloud account. In this case, you must modify the trust policy of the account that owns the VPC. The following table lists the account IDs for each instance.
Resource | Account ID |
transit router | 253460731706911258 |
VPC instance | 253460731706911258 |
CCN instance | 271598332402530847 |
In the account that owns the VPC, grant permissions to allow CCN instances within that account to access Private Zone.
Log on to the CEN console using the account that owns the VPC.
On the Instances page, find the CEN instance that you want to manage and click its ID.
On the tab, find the transit router in the same region as the VPC associated with Private Zone and click its ID.
On the details page of the transit router, click the Private Zone tab and then click Authorize Now. On the quick authorization page of Resource Access Management (RAM), click Authorize.
NoteGrant permissions to Smart Access Gateway (SAG) only when you configure access to Private Zone for the first time. After you grant the permissions, the CCN instance that is connected to the transit router can access Private Zone. The CCN instance is a component of SAG.
Modify the trust policy of the AliyunSmartAGAccessingPVTZRole role in the account that owns the VPC to allow the cross-account CCN instance to access Private Zone.
Log on to the RAM console using the account that owns the VPC.
In the navigation pane on the left, choose .
On the Roles page, enter AliyunSmartAGAccessingPVTZRole in the search box to find the role, and then click the role name.
On the role details page, click the Trust Policy tab and then click Edit Trust Policy.
In the Service section, add the following record:
"Alibaba Cloud account ID of the CCN instance@smartag.aliyuncs.com". Then, click OK.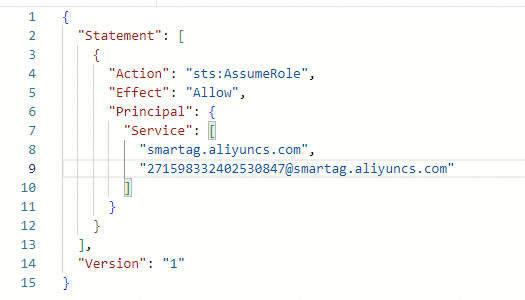
Case 3: TR in a different account
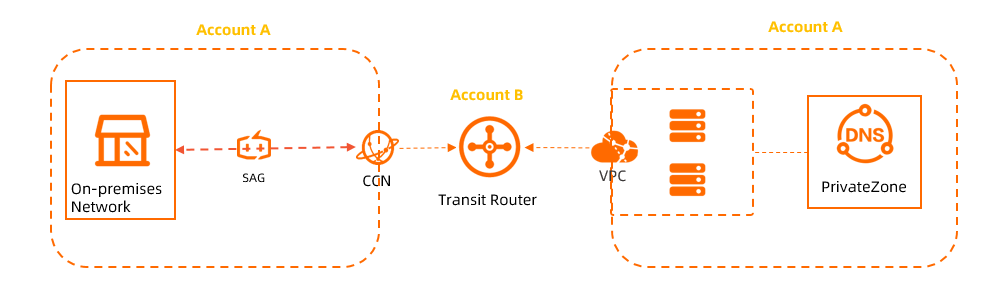
The CCN instance and the VPC where Private Zone is deployed belong to one Alibaba Cloud account, and the transit router belongs to another Alibaba Cloud account. In this case, you must create an access policy in the account that owns the VPC. The following table lists the account IDs for each instance.
Resource | Account ID |
transit router | 271598332402530847 |
VPC instance | 253460731706911258 |
CCN instance | 253460731706911258 |
Log on to the RAM console using the account that owns the VPC.
In the navigation pane on the left, choose .
On the Roles page, click Create Role.
In the Create Role panel, create a role based on the following information.
For Principal Type, select Cloud Service.
For Principal Name, select Smart Access Gateway.
Click OK. Enter
AliyunSmartAGAccessingPVTZRolefor Role Name and click OK.Return to the Roles page.
On the Roles page, search for the
AliyunSmartAGAccessingPVTZRolerole that you created and click the role name.On the Permissions tab, click Grant Permission to open the Grant Permission panel.
In the search box under Policy, enter the keyword pvtz. Select the AliyunPvtzReadOnlyAccess policy and click Grant Permission.
In the Grant Permission panel, click Close to return to the role details page.
On the role details page, click the Trust Policy tab to view the authorization information.
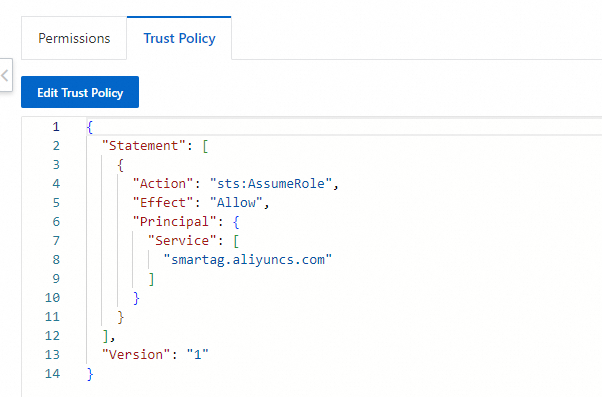
Case 4: Each instance in a separate account
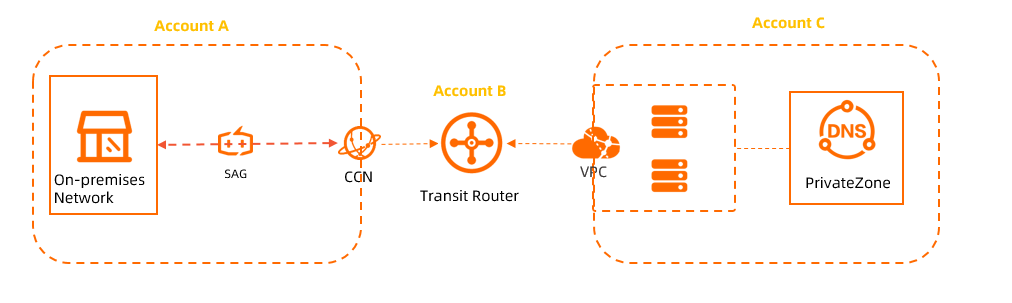
The CCN instance, the VPC where Private Zone is deployed, and the transit router all belong to different Alibaba Cloud accounts. In this case, you must complete two authorization tasks. The following table lists the account IDs for each instance.
Resource | Account ID |
transit router | 253460731706911258 |
VPC instance | 283117732402483989 |
CCN instance | 271598332402530847 |
Follow the steps in Scenario 3 to create a role and grant permissions in the account that owns the VPC.
Follow the steps in Scenario 2 to grant permissions to the CCN instance in the account that owns the VPC.
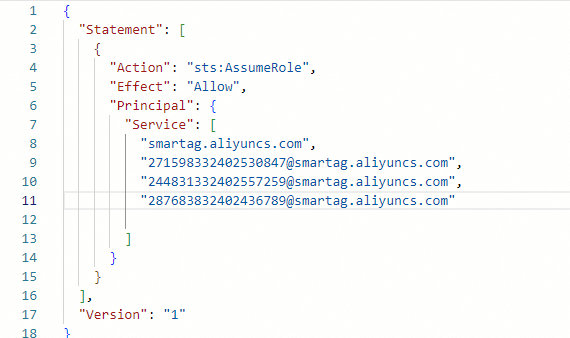
If you have multiple CCN instances that belong to different Alibaba Cloud accounts, you can add all CCN instances that need to access Private Zone to the trust policy, as shown in the following figure.
Resource | Account ID |
transit router | 253460731706911258 |
VPC instance | 283117732402483989 |
CCN instance 1 | 271598332402530847 |
CCN instance 2 | 244831332402557259 |
CCN instance 3 | 287683832402436789 |