You can perform O&M and audit operations on ApsaraDB RDS for MySQL, ApsaraDB RDS for SQL Server, and ApsaraDB RDS for PostgreSQL instances, PolarDB for MySQL, PolarDB for PostgreSQL, and PolarDB for PostgreSQL (Compatible with Oracle) clusters, and self-managed MySQL, SQL Server, PostgreSQL, and Oracle databases. You can enable SSH tunnels and use O&M tokens to perform O&M and audit operations. This topic describes how to use DBeaver to log on to different types of databases and perform O&M operations on the databases from a macOS client.
Prerequisites
A database O&M tool that supports SSH tunnels is installed on the local host. For example, you can install DBeaver, DbVisualizer, Navicat Premium, or Navicat for MySQL.
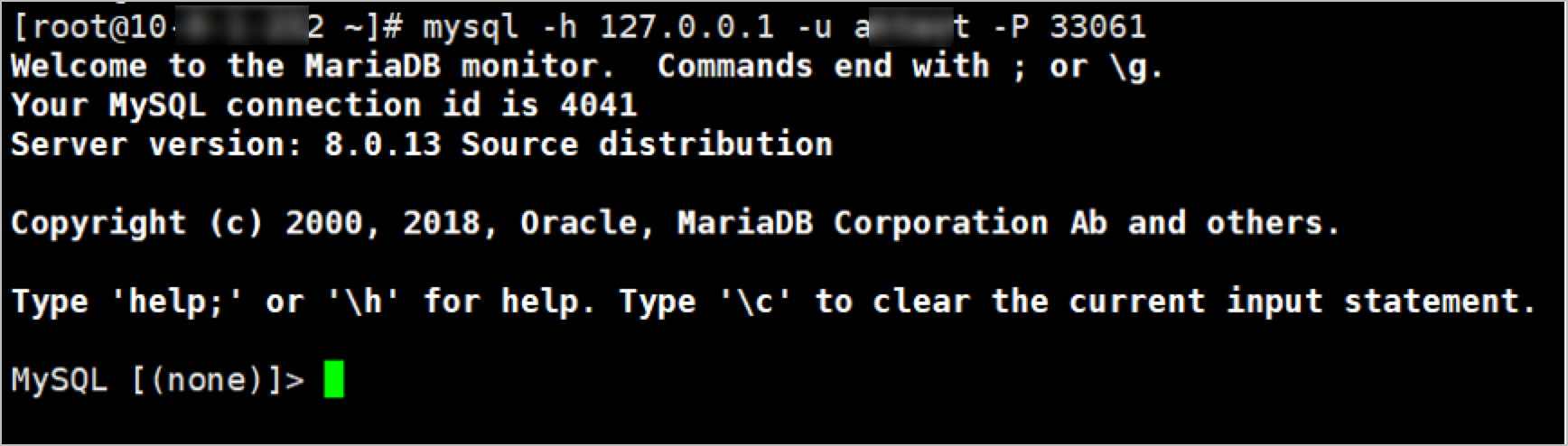
The O&M addresses of the bastion host are obtained. You can obtain the O&M addresses in the Bastion Host Information section on the Overview page in the console of the bastion host. For more information, see Log on to the console of a bastion host.
 Note
NoteBastionhost provides fixed O&M addresses and supports dynamic O&M IP addresses to ensure security. If you use IP addresses to connect to bastion hosts, the connection can fail due to IP address changes. To avoid this issue, we recommend that you use the O&M addresses of bastion hosts to perform O&M operations.
Use a database O&M tool to perform O&M operations over an SSH tunnel
In this topic, DBeaver is used to describe how to log on to different types of databases and perform O&M operations on the databases from a macOS client.
Log on to the console of a bastion host or the O&M portal to obtain an O&M token. For more information, see Obtain an O&M token.
NoteIf the account of the database is not hosted on the bastion host, you must configure the basic information about the O&M token in the O&M Token dialog box before you can obtain the O&M token. For more information about how to create a database account, see Use the database management feature.
You can use an O&M token only within its validity period. A Bastionhost administrator can configure a validity period for O&M tokens in the console of a bastion host. If O&M review is enabled, the validity period of the O&M token that is approved by an administrator takes effect.
If a Bastionhost administrator allows O&M engineers to renew O&M tokens, O&M engineers can renew O&M tokens before the O&M tokens expire. After the O&M tokens expire, the O&M engineers must apply for new O&M tokens. If O&M review is enabled, the O&M engineers cannot renew O&M tokens. After the settings of O&M tokens are modified, an O&M engineer must apply for a new O&M token or update the existing O&M token for the change to take effect.
If an O&M token is valid but the O&M connection fails, the number of concurrent O&M connections may have reached the upper limit or a Bastionhost administrator may have blocked the O&M requests that are sent during the period of time and from the source IP address. In the first case, contact the Bastionhost administrator to upgrade your bastion host or release idle connections. In the second case, contact the Bastionhost administrator to remove the limits.
The O&M engineer information in the audit records contains the information about the users who applied for O&M tokens. The information does not include the usernames and asset accounts that are specified in clients.
Open DBeaver and establish a connection to the database on which you want to perform O&M operations.
On the General tab, configure the following database information and then click Next.
Parameter
Description
Host
The address of the database asset.
Port
The port of the database on which you want to perform O&M operations.
User Name
The username that you use to log on to the database.
Password
MySQL, SQL Server, or PostgreSQL database: If the Bastionhost administrator hosts the account of the database in the bastion host, you can leave this parameter empty. Otherwise, you must configure this parameter.
Oracle database:
If the Bastionhost administrator hosts the account of the database in the bastion host, you can specify the password as 123456 and specify the logon attribute as instructed by the O&M token.
Otherwise, you can enter the logon password of the database and specify the logon attribute as instructed by the O&M token.
On the SSH tab, configure basic O&M information and then click Finish.
Parameter
Description
Use SSH Tunnel
Select Use SSH Tunnel.
Host/IP
Enter the public O&M address of your bastion host.
Port
Enter the O&M port of the bastion host for SSH tunnels. Default value: 60022.
User Name
Enter the username that you use to log on to your bastion host.
Password
Enter the O&M token that is obtained.
In DBeaver, double-click the newly created connection to log on to the database and perform O&M operations.
Use a command line tool (CLI) to perform O&M operations over an SSH tunnel
This example shows how to log on to a database that runs MySQL and perform O&M operations over an SSH tunnel.
This O&M method is not supported for Oracle databases.
Log on to the O&M portal. For more information, see Log on to the O&M portal.
In the left-side navigation pane, click Databases.
On the Databases page, find the database that you want to manage and click O&M Token in the O&M Token column.
In the O&M Token dialog box, select a database account and click Obtain O&M Token.
NoteIf the account of the database is not hosted on the bastion host, you must configure the basic information about the O&M token in the O&M Token dialog box before you can obtain the O&M token. For more information about how to create a database account, see Use the database management feature.
You can use an O&M token only within its validity period. A Bastionhost administrator can configure a validity period for O&M tokens in the console of a bastion host. If O&M review is enabled, the validity period of the O&M token that is approved by an administrator takes effect.
If a Bastionhost administrator allows O&M engineers to renew O&M tokens, O&M engineers can renew O&M tokens before the O&M tokens expire. After the O&M tokens expire, the O&M engineers must apply for new O&M tokens. If O&M review is enabled, the O&M engineers cannot renew O&M tokens. After the settings of O&M tokens are modified, an O&M engineer must apply for a new O&M token or update the existing O&M token for the change to take effect.
If an O&M token is valid but the O&M connection fails, the number of concurrent O&M connections may have reached the upper limit or a Bastionhost administrator may have blocked the O&M requests that are sent during the period of time and from the source IP address. In the first case, contact the Bastionhost administrator to upgrade your bastion host or release idle connections. In the second case, contact the Bastionhost administrator to remove the limits.
The O&M engineer information in the audit records contains the information about the users who applied for O&M tokens. The information does not include the usernames and asset accounts that are specified in clients.
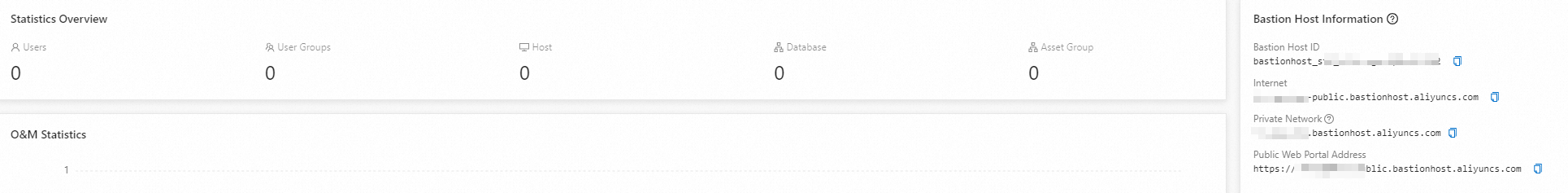
Open the CLI and run the following commands:
ssh -N -L <localport>:<databaseAddress>:<databasePort> <bastionusername>@<bastionAddress> -p <bastionPort>The following table describes the parameters.
Parameter
Description
localport
The custom local listening port that is used after the SSH tunnel is created. Make sure that the local listening port is not occupied.
databaseAddress
The address of the database on which you want to perform O&M operations.
databasePort
The port of the database on which you want to perform O&M operations.
bastionusername
The username of your bastion host.
bastionAddress
The public O&M address of your bastion host.
bastionPort
The O&M port of your bastion host for SSH. Default value: 60022.
In the password authentication step, enter the O&M token and press Enter.
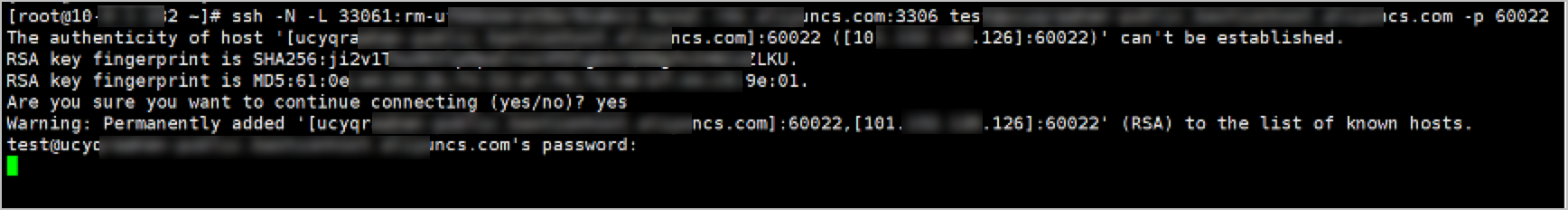
Switch to a new line and check the status of the local listening port that you specify. If LISTEN is displayed, the port is in the listening state.
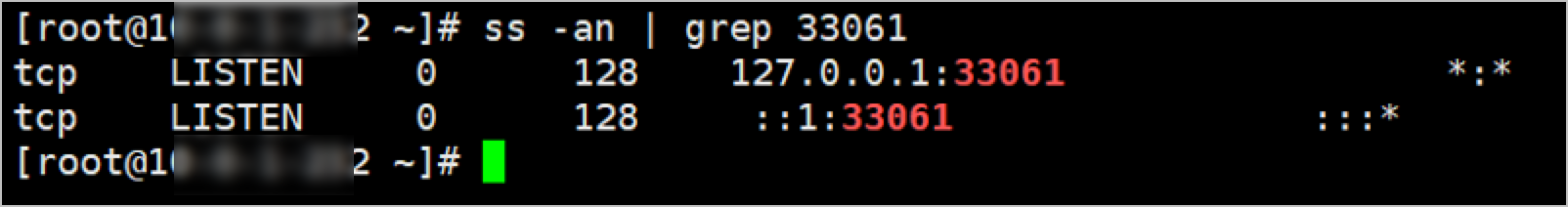
Run the following command to connect to the MySQL database:
mysql -h 127.0.0.1 -u <accountname> -P <localport><accountname> is required. Set
accountnameto the username of the MySQL database on which you want to perform O&M operations.<localport> is required. Set
localportto the local listening port that you specified in Step 5.
After the MySQL database is connected, you can run commands to perform O&M operations on the database.