Open Policy Agent (OPA) allows you to define access control policies after you inject an OPA sidecar proxy into an application. If you want to implement fine-grained authorization and access control on applications in specific namespaces, you can enable the feature of controlling the injection scope of OPA sidecar proxies. OPA sidecar proxies are injected into only pods in namespaces that contain the opa-istio-injection=enabled label.
Prerequisites
A Container Service for Kubernetes (ACK) cluster is added to a Service Mesh (ASM) instance whose version is 1.12.4.19 or later. For more information, see Add a cluster to an ASM instance.
Two namespaces named default and develop are created. For more information, see Manage namespaces and resource quotas.
An NGINX application is deployed in the default namespace and a sleep application is deployed in the develop namespace. For more information, see Create a stateless application by using a Deployment.
Step 1: Enable the OPA plug-in and the feature of controlling the injection scope of OPA sidecar proxies
In this example, after you enable the OPA plug-in and the feature of controlling the injection scope of OPA sidecar proxies, add the opa-istio-injection=enabled label to the default namespace and do not add the opa-istio-injection=enabled label to the develop namespace. Verify that the injection scope of OPA sidecar proxies is controlled by checking whether OPA sidecar proxies are injected into both the NGINX application and the sleep application.
Log on to the ASM console. In the left-side navigation pane, choose .
On the Mesh Management page, click the name of the ASM instance. In the left-side navigation pane, choose .
On the OPA Policy page, select Enable Open Policy Agent (OPA) Plug-in and Enable OPA Injection Range Control, and then click Enable OPA. In the Note message, click OK.
Step 2: Add the required label to a namespace
The following section describes how to add the opa-istio-injection=enabled label to the default namespace in the ACK console. You can also use kubectl to connect to the ACK cluster and run the kubectl label namespace default opa-istio-injection=enabled --overwrite command to add the opa-istio-injection=enabled label to the default namespace. For more information about how to connect to a cluster, see Obtain the kubeconfig file of a cluster and use kubectl to connect to the cluster.
Log on to the ACK console. In the left-side navigation pane, click Clusters.
On the Clusters page, click the name of the cluster that you want to manage and click Namespaces and Quotas in the left-side navigation pane.
On the Namespace page, click Edit in the Actions column of the default namespace.
In the Edit Namespace dialog box, set label name to opa-istio-injection, set label value to enabled, click Add, and then click OK.
Step 3: Restart applications
In this step, restart applications by deleting pods. After an application is restarted, an OPA sidecar proxy is automatically injected into the application if the namespace to which the application belongs has the required label.
Log on to the ACK console. In the left-side navigation pane, click Clusters.
On the Clusters page, click the name of the cluster that you want to manage and choose in the left-side navigation pane.
In the upper part of the Pods page, set Namespace to default and choose in the Actions column of the pod on which the NGINX application is deployed. In the Note dialog box, click OK.
If the application has multiple pods, you need to delete all these pods to restart the application. If the state of a pod is Running, the pod is restarted.
Repeat the preceding operations in this step to restart the pod of the sleep application in the develop namespace.
Step 4: Check whether the control on the injection scope is successful
Log on to the ACK console. In the left-side navigation pane, click Clusters.
On the Clusters page, click the name of the cluster that you want to manage and choose in the left-side navigation pane.
On the Pods page, check whether OPA sidecar proxies are injected into the NGINX and sleep applications.
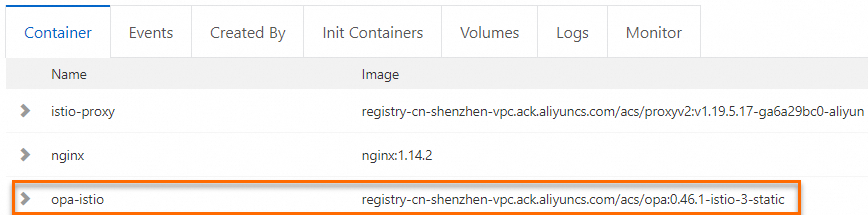
Set Namespace to default and click the pod name of the NGINX application. opa-istio is displayed on the Container tab, which indicates that an OPA sidecar proxy is injected into the NGINX application.
Set Namespace to develop and click the pod name of the sleep application. opa-istio is not displayed on the Container tab, which indicates that no OPA sidecar proxy is injected into the sleep application.
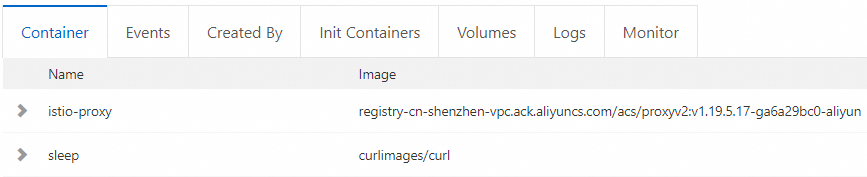
The verification results show that after you enable the feature of controlling the injection scope of OPA sidecar proxies, an OPA sidecar is injected into only an application that is in a namespace with the
opa-istio-injection=enabledlabel. This means that you have controlled the injection scope of OPA sidecar proxies.