When you need to customize an access control policy based on your business requirements, you can configure a Service Mesh (ASM) security policy to implement custom authorization. That is, requests are forwarded to a custom authorization service that you specify. The custom authorization service authenticates the requests. This way, you can implement complex authentication logic, reduce development and maintenance costs, and improve development efficiency.
Prerequisites
Procedure
Log on to the ASM console. In the left-side navigation pane, choose .
On the Mesh Management page, click the name of the ASM instance. In the left-side navigation pane, choose .
On the ASMSecurityPolicy page, click Create. In the Create ASMSecurityPolicy dialog box, click Custom Authorization Service and then click OK.
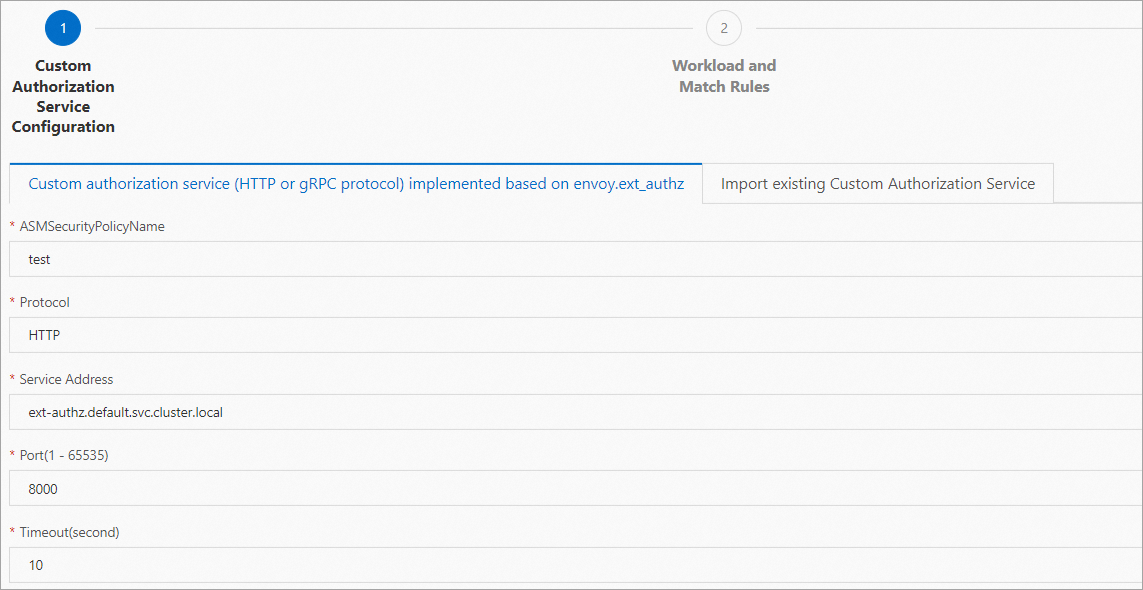
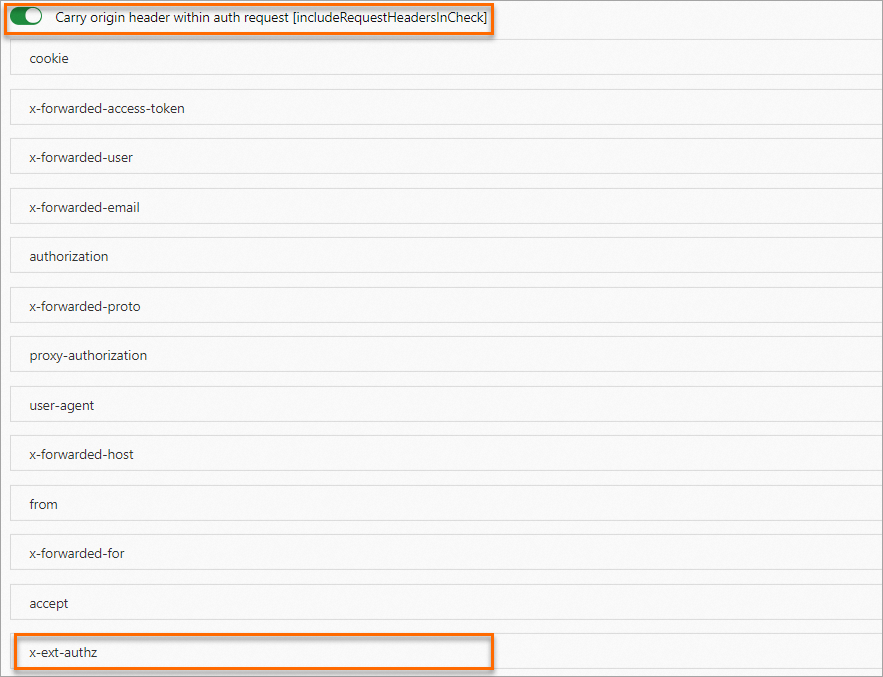
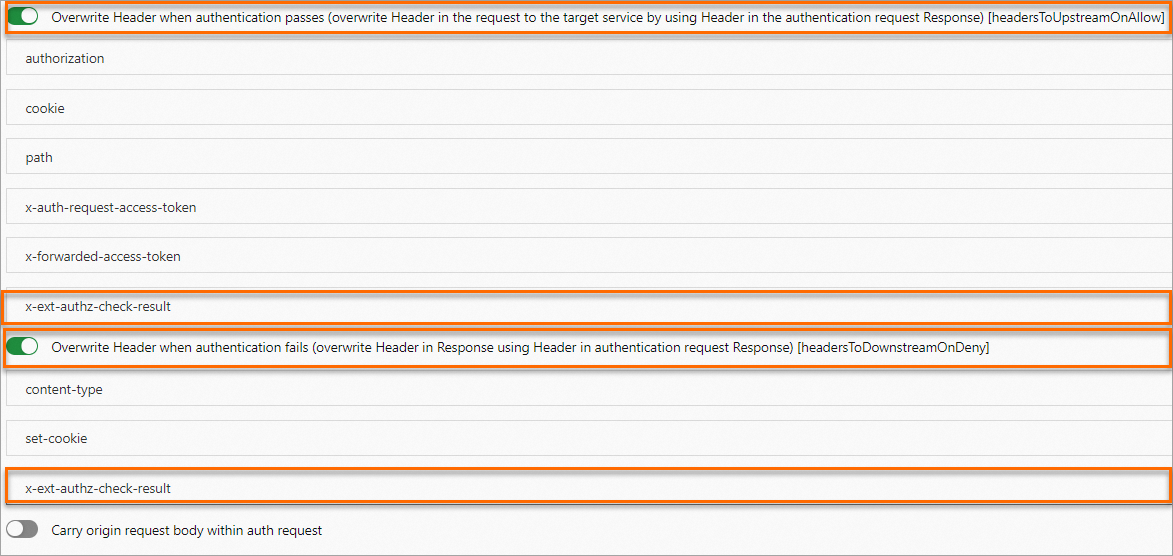
In the Custom Authorization Service Configuration step of the CreateCustom Authorization Service configuration wizard, click the Custom authorization service (HTTP or gRPC protocol) implemented based on envoy.ext_authz tab, configure the parameters, and then click Next.
The following figure shows an example of how to configure the parameters. For more information about the parameters, see Implement custom authorization by using the HTTP protocol.
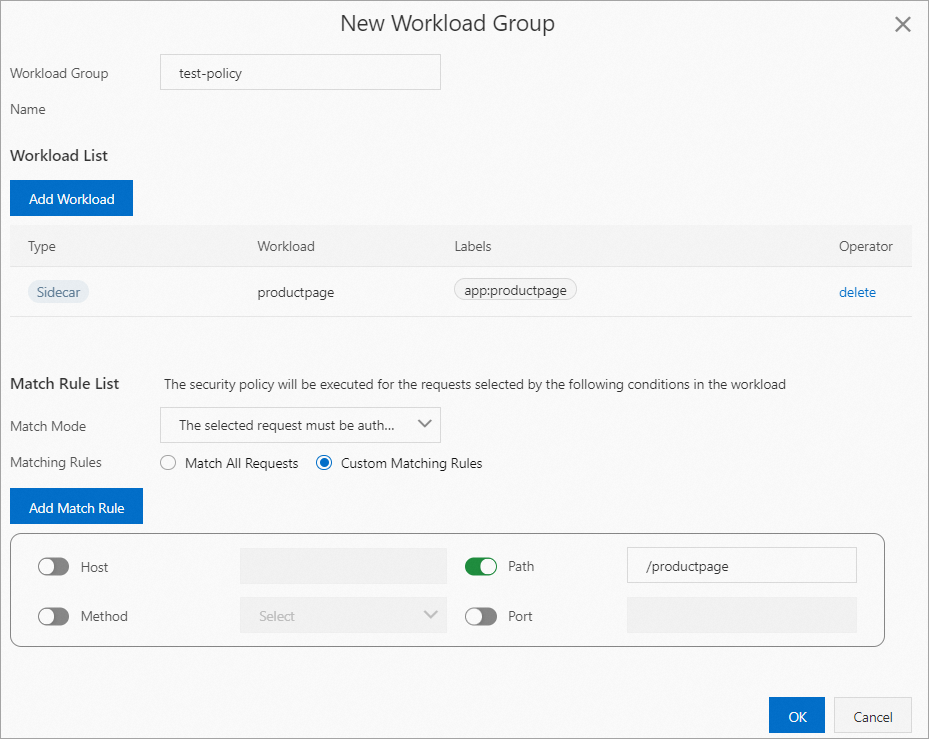
In the Workload and Match Rules step of the configuration wizard, click Add Workload Group. In the New Workload Group dialog box, configure the parameters and click OK.
The following table describes how to configure the parameters in this example.
Parameter
Description
Workload Group Name
Set the name to test-policy.
Workload List
Click Add Workload.
In the Add Workload dialog box, select Workload Scope. Set the Namespace parameter to default and the Workload Type parameter to Service.
In the Select workloads box, select productpage, click the
 icon to add the workload to the selected box, and then click OK.
icon to add the workload to the selected box, and then click OK.
Match Rule List
Set the Match Mode parameter to The selected request must be authenticated. Set Matching Rules to Custom Matching Rules. Turn on the Path switch and set the parameter to /productpage.
In the Complete step of the configuration wizard, the "ASMSecurityPolicy Creation successfully" message appears, indicating that the ASM security policy is created. You can click YAML to view the created resources, or click Complete to go back to the ASMSecurityPolicy page to view the created security policy.
Check whether the custom authorization configuration takes effect.
Run the following command to initiate a request with the
x-ext-authz: allowheader to access the productpage service:curl -I -H "x-ext-authz: allow" http://${IP address of the ingress gateway}/productpageExpected output:
HTTP/1.1 200 OK content-type: text/html; charset=utf-8 content-length: 5288 server: istio-envoy date: Tue, 17 Jan 2023 07:53:14 GMT x-envoy-upstream-service-time: 20The output indicates that custom authorization is triggered and the authentication is successful.
Run the following command to initiate a request with the
x-ext-authz: denyheader to access the productpage service:curl -I -H "x-ext-authz: deny" http://${IP address of the ingress gateway}/productpageExpected output:
HTTP/1.1 403 Forbidden x-ext-authz-check-result: denied date: Tue, 17 Jan 2023 07:55:27 GMT server: istio-envoy x-envoy-upstream-service-time: 2 transfer-encoding: chunkedThe output indicates that custom authorization is triggered but the authentication fails.
The preceding results indicate that the custom authorization configuration takes effect.
References
For more information about the concepts and features of ASM security policies, see Overview of ASM security policies.
You can enable the mesh audit feature to record or trace the daily operations of different users. You can also configure audit alerts for operations on ASM resources and send alert notifications to alert contacts in a timely manner when important resources change. For more information, see Use the KubeAPI operation audit feature in ASM and Configure audit alerts for operations on ASM resources.