If you want to audit and monitor operations on Service Mesh (ASM) resources, you can enable the audit feature for your ASM instance and configure alerts in Simple Log Service to enable audit alerts for changes of ASM resources such as virtual services and destination rules. This way, alerts are sent to alert contacts in a timely manner for changes of important resources. This ensures the security and compliance of ASM. This topic describes how to configure an alert rule for the deletion of a virtual service and verify the configuration. Specifically, a text message is sent to notify the alert contact when a virtual service is deleted.
Prerequisites
Simple Log Service is activated. For more information about the billing of Simple Log Service, see Billing overview.
Step 1: Enable audit for the ASM instance
After you enable audit for an ASM instance, the operation logs of the Kubernetes API of the ASM instance are collected to Simple Log Service as the data source for subsequent alert configurations.
Log on to the ASM console. In the left-side navigation pane, choose .
On the Mesh Management page, click the name of the ASM instance. In the left-side navigation pane, choose .
On the page that appears, select Enable Mesh Audit and click OK.
If the page shown in the following figure is displayed, mesh audit is enabled successfully.
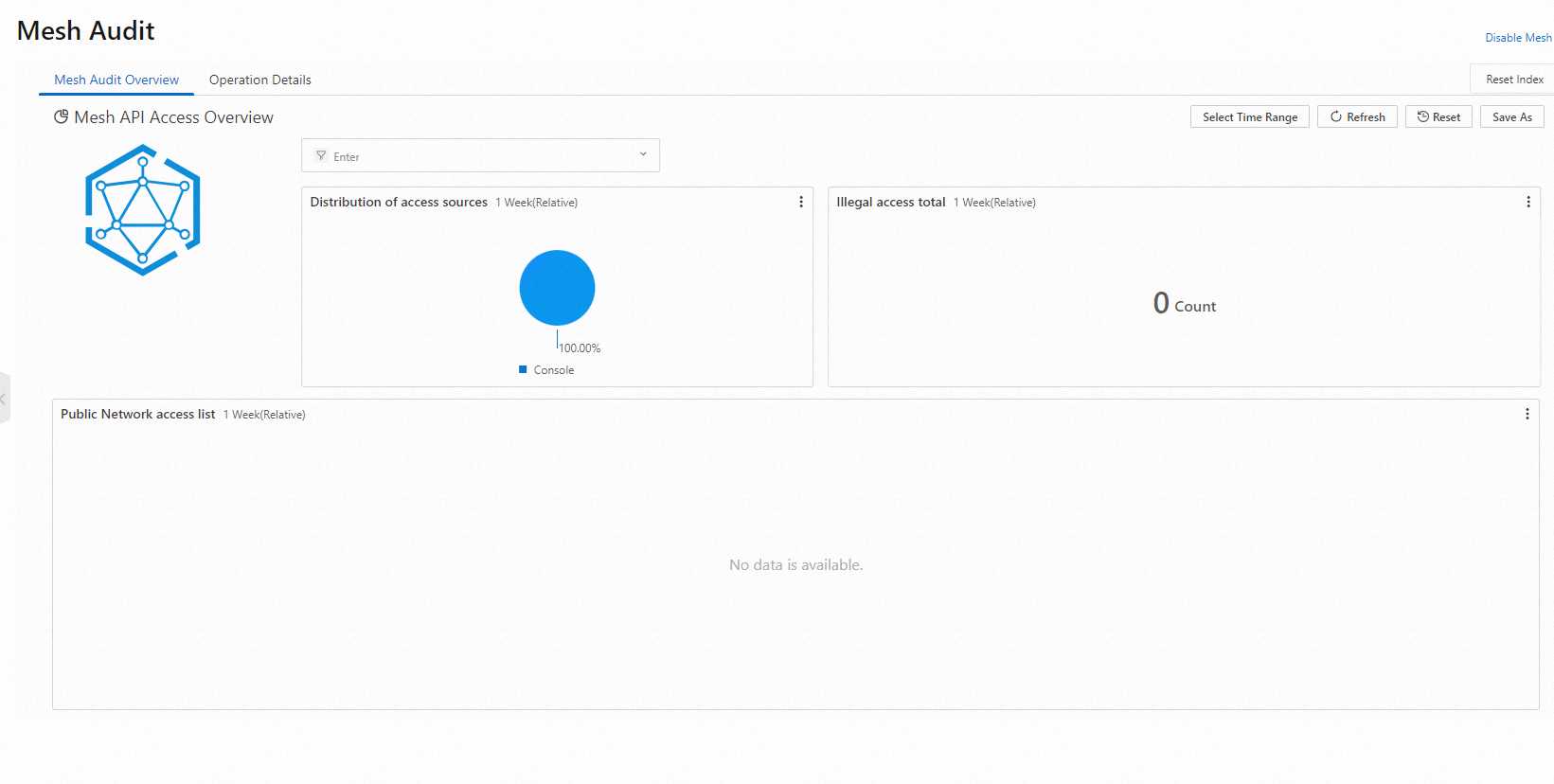
Step 2: Add an alert recipient
In this example, the generated alert will be sent to the built-in ASM user group in Simple Log Service. Therefore, you must add a test user that can receive the notification to the user group.
Make sure that a mobile phone number is added to the test user and the mobile phone number can receive text messages. For more information, see Create users.
Add the test user to the user group.
Log on to the Simple Log Service console.
In the Projects section, click the name of the desired project. In the left-side navigation pane, click Alerts.
If you need to create a new project (you do not select an existing project when you create the ASM instance or enable the audit feature), the project name is in the
mesh-log-<Mesh ID>format.If an existing project is used, click the name of the project.
On the Alert Center page, choose .
On the User Group Management tab, find sls.app.asm.builtin and click Edit in the Actions column.
In the Edit User Group dialog box, add the test user and click OK.
Step 3: Configure an audit alert rule
Configure alert notifications via text messages for the deletion of a virtual service.
Log on to the Simple Log Service console.
In the Projects section, click the name of the desired project. In the left-side navigation pane, click Alerts.
On the Alert Rule tab of the Alert Center page, click Create Alert.
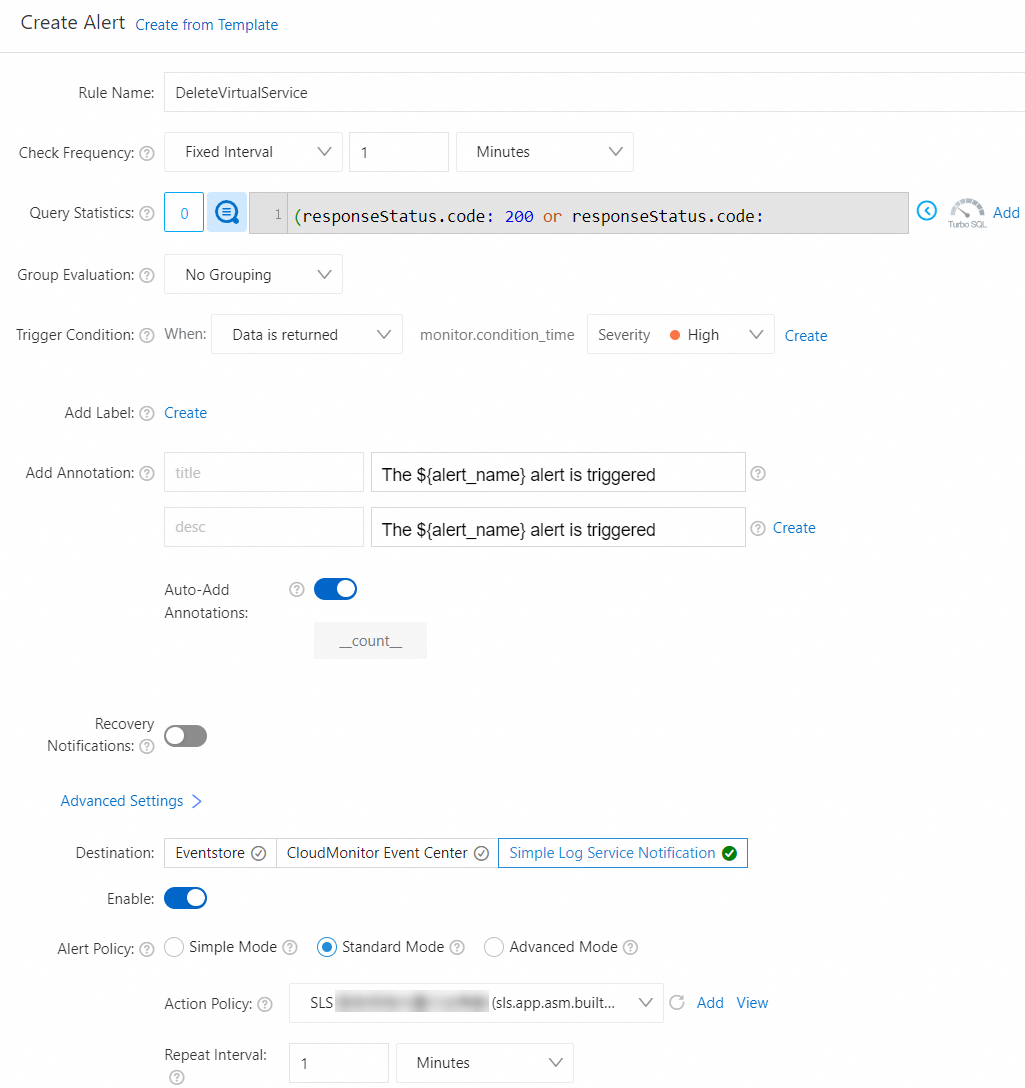
In the Create Alert panel, configure the parameters and click OK.
The following table describes some of the parameters. For more information about the parameters, see Create an alert rule.
Parameter
Description
Rule Name
For this example, set the value to DeleteVirtualService.
Check Frequency
To quickly verify whether the configuration in this example takes effect, set the value to 1 minute for this example.
Query Statistics
Click Create. In the Query Statistics dialog box, click the Advanced Settings tab and select the Logstore whose name starts with audit.
Set Time Range to 1 Minute(Relative), which is the same as the value of Check Frequency. This prevents repeated alerts and missed alerts.
In the Query field, enter
(responseStatus.code: 200 or responseStatus.code: 201) and objectRef.resource: virtualservices and objectRef.apiGroup: "networking.istio.io" and ( verb: delete ). Then, click Preview. After you confirm the information, click Confirm.
Trigger Condition
For this example, set When to Data is returned and set Severity to High. This way, an alert is triggered when data is returned, and the severity is high.
Add Annotation
You can modify the title and desc fields based on your business requirements to customize the title and content of the alert. For more information, see Variables in alert templates (new version).
Destination
Select Simple Log Service Notification, turn on the Enable switch, and then set Action Policy to sls.app.asm.builtin.
Step 4: Verify the audit alert rule
Delete a virtual service to verify the audit alert rule configured in Step 3.
Create a virtual service and then delete it.
Log on to the ASM console. In the left-side navigation pane, choose .
On the Mesh Management page, click the name of the ASM instance. In the left-side navigation pane, choose . On the page that appears, click Create from YAML.
On the Create page, select default from the Namespace drop-down list, select HTTP basic routing from the Template drop-down list, and then click Create.
On the VirtualService page, find the reviews-route virtual service that you created and click Delete in the Actions column. In the Submit message, click OK.
Check whether an audit alert is generated.
Log on to the Simple Log Service console.
In the Projects section, click the name of the desired project. In the left-side navigation pane, choose .
In the Dashboard list, click Alert History Statistics to view the execution records of each alert and whether an alert is generated.
After you delete a virtual service in substep 1, an alert is generated in the Alert History section.
In the left-side navigation pane, click Log Storage. On the page that appears, search for and click the internal-alert-history Logstore. Then, click Search & Analyze in the right pane.
You can view an alert log whose AlertDisplayName is DeleteVirtualService. The Fired field of the log is true.
Check whether the mobile phone number bound to the test user receives an alert notification message.
Related information
Alert notification methods of the built-in ASM action policy
Alert severity | Alert notification method |
Critical | Voice calls |
High | Text messages |
Others | Email notifications |
Common alert conditions
Query statement for alert generation when an Istio gateway is created, modified, or deleted:
(responseStatus.code: 200 or responseStatus.code: 201) and objectRef.resource: istiogateways and objectRef.apiGroup: "istio.alibabacloud.com" and ( verb: create or verb: delete or verb: update )Query statement for alert generation when a gateway is deleted:
(responseStatus.code: 200 or responseStatus.code: 201) and objectRef.resource: gateways and objectRef.apiGroup: "networking.istio.io" and ( verb: delete )Query statement for alert generation when an ASM credential is deleted:
(responseStatus.code: 200 or responseStatus.code: 201) and objectRef.resource: asmcredentials and objectRef.apiGroup: "istio.alibabacloud.com" and ( verb: delete )Query statement for alert generation when a virtual service is deleted:
(responseStatus.code: 200 or responseStatus.code: 201) and objectRef.resource: virtualservices and objectRef.apiGroup: "networking.istio.io" and ( verb: delete )Query statement for alert generation when a destination rule is deleted:
(responseStatus.code: 200 or responseStatus.code: 201) and objectRef.resource: destinationrules and objectRef.apiGroup: "networking.istio.io" and ( verb: delete )Query statement for alert generation when a Telemetry resource is deleted:
(responseStatus.code: 200 or responseStatus.code: 201) and objectRef.resource: telemetries and objectRef.apiGroup: "telemetry.istio.io" and ( verb: delete )Query statement for alert generation when an authorization policy is deleted:
(responseStatus.code: 200 or responseStatus.code: 201) and objectRef.resource: authorizationpolicies and objectRef.apiGroup: "security.istio.io" and ( verb: delete )Query statement for alert generation when an Envoy filter is deleted:
(responseStatus.code: 200 or responseStatus.code: 201) and objectRef.resource: envoyfilters and objectRef.apiGroup: "networking.istio.io" and ( verb: delete )
References
For more information about how to grant the read-only and management permissions on alerts to a RAM user, see Grant a RAM user the permissions to manage alerts.
You can configure zero trust security capabilities such as workload identity, peer authentication, request authentication, and authorization policies in ASM to manage mesh resources in a more fine-grained manner and improve mesh security. For more information, see Overview of zero trust security.