Causes
Application monitoring is suspended.
The ARMS agent is not loaded as expected at the pod where the application resides.
Solution
Step 1: Check whether application monitoring is suspended
Log on to the ARMS console. In the left-side navigation pane, choose .
On the Application List page, select a region in the top navigation bar and click the name of the application.
If the application is not found, proceed to Step 2: Check whether the ARMS agent is loaded as expected.
If you are using the new Application Real-Time Monitoring Service (ARMS) console, choose in the top navigation bar of the application details page. In the Probe switch settings section, check whether application monitoring is suspended.
If Pause application monitoring is turned on, turn off the switch and click Save.
If Pause application monitoring is turned off, proceed to Step 2: Check whether the ARMS agent is loaded as expected.
If you are using the old ARMS console, click Application Settings in the left-side navigation pane of the application details page. On the page that appears, click the Custom Configuration tab. In the Agent Switch Settings section, check whether Probe Master Switch is turned on.
If Probe Master Switch is turned off, turn on Probe Master Switch and click Save in the lower part of the page.
If Probe Master Switch is turned on, proceed to Step 2: Check whether the ARMS agent is loaded as expected.
Step 2: Check whether the ARMS agent is loaded as expected
Log on to the ACK console. In the left-side navigation pane, click Clusters. On the Clusters page, click the name of the cluster to go to the cluster details page.
In the left-side navigation pane, choose .
On the Pods page, select the namespace in which your application resides, find the application, and then click Edit YAML in the Actions column.
In the Edit YAML dialog box, check whether the YAML file contains initContainers.
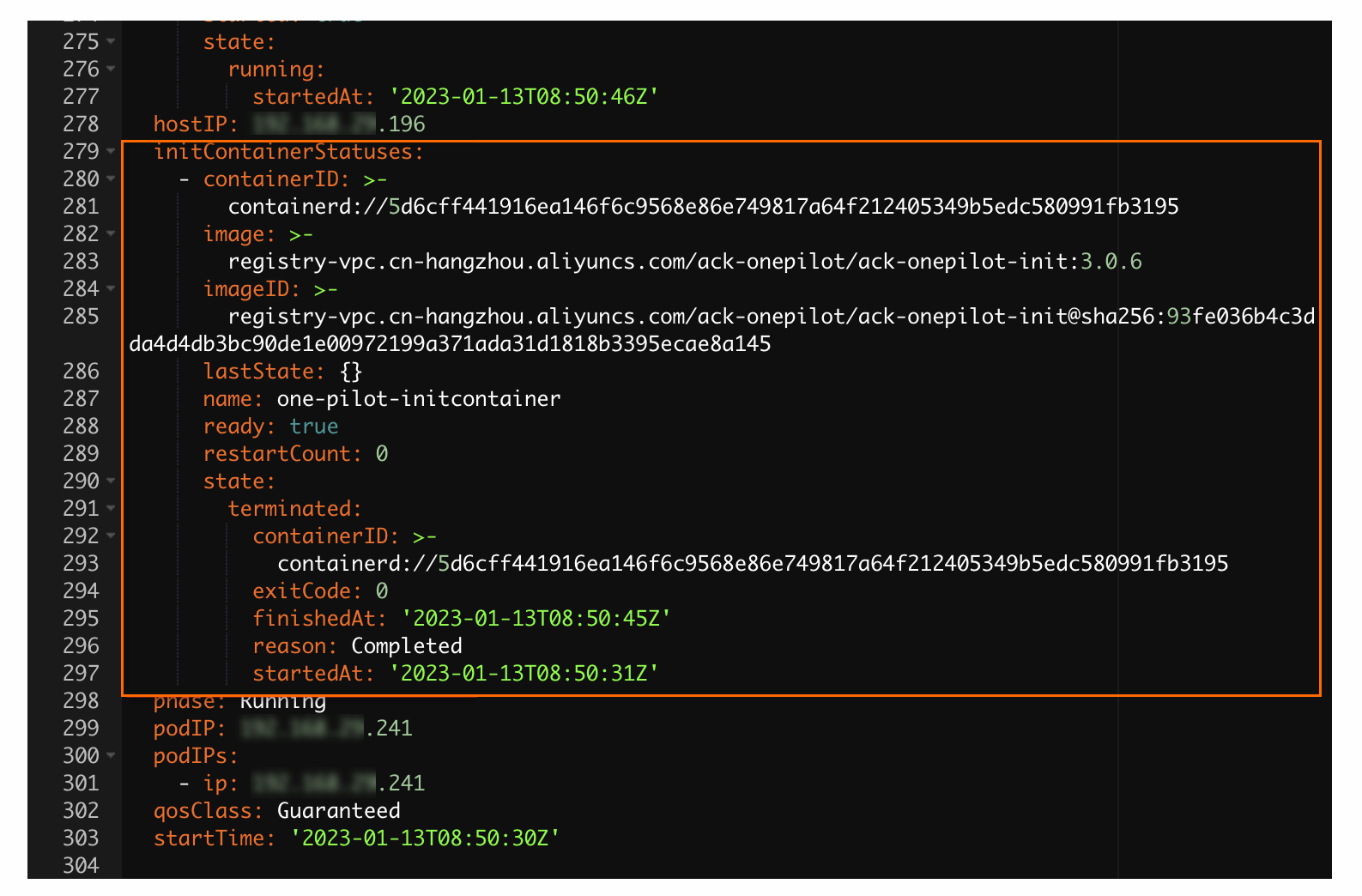
In the left-side navigation pane of the cluster details page, choose . On the page that appears, set the Namespace parameter to ack-onepilot. Check if any pod named
ack-onepilot-*with completed rolling updates exists in the pod list.If the specified pod exists, perform Step 6.
If the specified pod does not exist, install the ack-onepilot component from the application market. For more information, see How do I install ack-onepilot and uninstall arms-pilot?
In the left-side navigation pane of the cluster details page, choose Workloads > Deployments or StatefulSets. On the page that appears, find the application and choose in the Actions column. In the Edit YAML dialog box, check whether the YAML file contains the following labels in the spec.template.metadata section:
labels: armsPilotAutoEnable: "on" armsPilotCreateAppName: "<your-deployment-name>" # Replace <your-deployment-name> with the actual application name. armsSecAutoEnable: "on" # If you want to connect the application to Application Security, you must configure this parameter.If the YAML file contains the labels, perform Step 7.
If the YAML file does not contain the labels, perform the following operations: In the Edit YAML dialog box, add the labels to the spec > template > metadata section and replace <your-deployment-name> with the actual application name. Then, click Update.
In the left-side navigation pane of the cluster details page, choose . On the page that appears, find the pod and choose in the Actions column to check whether the pod logs of ack-onepilot report a Security Token Service (STS) error in the
"Message":"STS error"format.If the error is reported, authorize the cluster of the application and restart the pod of the application. For more information, see Install the ARMS agent for Java applications deployed in ACK.
If the error is not reported, submit a ticket.
In the left-side navigation pane of the cluster details page, choose , find the pod and click Edit YAML in the Actions column. In the Edit YAML dialog box, check whether the YAML file contains the following javaagent parameter:
-javaagent:/home/admin/.opt/ArmsAgent/aliyun-java-agent.jarNoteIf you use an ARMS agent earlier than 2.7.3.5, replace aliyun-java-agent.jar in the preceding code with arms-bootstrap-1.7.0-SNAPSHOT.jar. We recommend that you upgrade the agent to the latest version at the earliest opportunity.
If the YAML file contains the parameter, find the pod on the Pods page and click Terminal in the Actions column to go to the command line page. Run the following command to check whether the logs file contains a log file with the .log file extension. Then, submit a ticket.
cd /home/admin/.opt/ArmsAgent/logsIf the YAML file does not contain the parameter, submit a ticket.
 > Edit YAML
> Edit YAML