If the system policies of Application Real-Time Monitoring Service (ARMS) do not meet your business requirements, you can create custom policies to implement the principle of least privilege. You can use custom policies to manage permissions in a fine-grained manner and improve resource access security. This topic describes how to attach a custom policy to a RAM user.
What is a custom policy?
Resource Access Management (RAM) policies are classified into system policies and custom policies. You can manage custom policies based on your business requirements.
After you create a custom policy, you must attach the policy to a RAM user, RAM user group, or RAM role. This way, the permissions that are specified in the policy can be granted to the principal.
You can delete a RAM policy that is not attached to a principal. If the RAM policy is attached to a principal, before you can delete the RAM policy you must detach the RAM policy from the principal.
Custom policies support version control. You can manage custom policy versions based on the version management mechanism provided by RAM.
References
Prerequisites
By default, Alibaba Cloud accounts that activate ARMS after 00:00 on April 1, 2022 can attach custom policies to RAM users. Other Alibaba Cloud accounts must submit a ticket.
You have a basic knowledge of policy elements, structure, and syntax before you create a custom policy. For more information, see Policy elements.
The ReadOnlyAccess or AliyunARMSReadOnlyAccess system policy is attached to the RAM user. This ensures that the RAM user can log on to the ARMS console.
ImportantTo grant the read-only permissions on all ARMS features to a specific resource group, you must attach the AliyunARMSReadOnlyAccess policy to and grant the ReadTraceApp permission to the resource group. Otherwise, ARMS cannot display the application list that belongs to the authenticated resource group.
The AliyunARMSFullAccess system policy is not attached to the RAM user.
Background information
The system policies provided by ARMS are coarse-grained. If the system policies cannot meet your requirements, you can create custom policies to implement fine-grained access control. For example, if you need to grant the operation permissions on a specific application to a RAM user, you must create a custom policy to meet this requirement.
Step 1: Create a custom policy
Log on to the RAM console as a RAM user who has administrative rights.
In the left-side navigation pane, choose .
On the Policies page, click Create Policy.
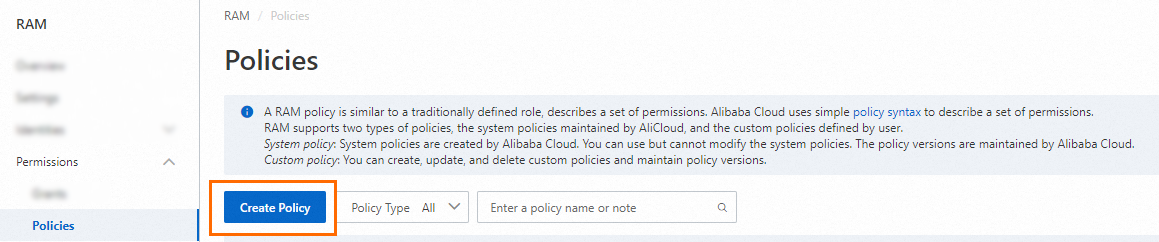
On the Create Policy page, click the JSON tab. Configure a permission policy in the editor.
For more information, see Policy elements.
The following example indicates the read-only permissions on applications that reside in the China (Hangzhou) region and are associated with the
key0: value01orkey0: value02tag.{ "Version": "1", "Statement": [ { "Action": [ "arms:ReadTraceApp" ], "Resource": "acs:arms:cn-hangzhou:*:armsapp/*", "Effect": "Allow", "Condition": { "StringEquals": { "arms:tag/key0":[ "value01", "value02" ] } } } ] }Click Optional advanced optimize in the upper part. In the Optional advanced optimize message, click Perform to optimize the policy.
The system performs the following operations during the advanced optimization:
Split resources or conditions that are incompatible with actions.
Narrow down resources.
Deduplicate or merge policy statements.
On the Create Policy page, click OK.
In the Create Policy dialog box, configure the Name and Description parameters and click OK.
Step 2: Attach the custom policy
Attach the custom policy to the RAM user
Log on to the RAM console as a RAM administrator.
In the left-side navigation pane, choose .
On the Users page, find the required RAM user, and click Add Permissions in the Actions column.
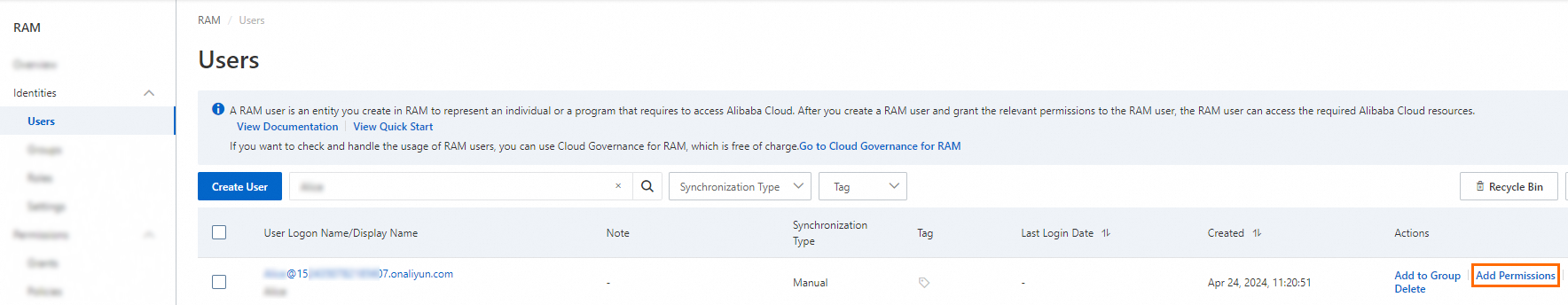
You can also select multiple RAM users and click Add Permissions in the lower part of the page to grant permissions to the RAM users at a time.
In the Grant Permission panel, grant permissions to the RAM user.
Configure the Resource Scope parameter.
Account: The authorization takes effect on the current Alibaba Cloud account.
ResourceGroup: The authorization takes effect on a specific resource group.
ImportantIf you select Resource Group for the Resource Scope parameter, make sure that the required cloud service supports resource groups. For more information, see Services that work with Resource Group. For more information about how to grant permissions on a resource group, see Use a resource group to grant a RAM user the permissions to manage a specific ECS instance.
Configure the Principal parameter.
The principal is the RAM user to which you want to grant permissions. The current RAM user is automatically selected.
Configure the Policy parameter.
A policy contains a set of permissions. Policies can be classified into system policies and custom policies. You can select multiple policies at a time.
System policies: policies that are created by Alibaba Cloud. You can use but cannot modify these policies. Version updates of the policies are maintained by Alibaba Cloud. For more information, see Services that work with RAM.
NoteThe system automatically identifies high-risk system policies, such as AdministratorAccess and AliyunRAMFullAccess. We recommend that you do not grant unnecessary permissions by attaching high-risk policies.
Custom policies: You can manage and update custom policies based on your business requirements. You can create, update, and delete custom policies. For more information, see Create a custom policy.
Click Grant permissions.
Click Close.
Attach the custom policy to a RAM role
Log on to the RAM console as a RAM administrator.
In the left-side navigation pane, choose .
On the Roles page, find the RAM role that you want to manage and click Grant Permission in the Actions column.
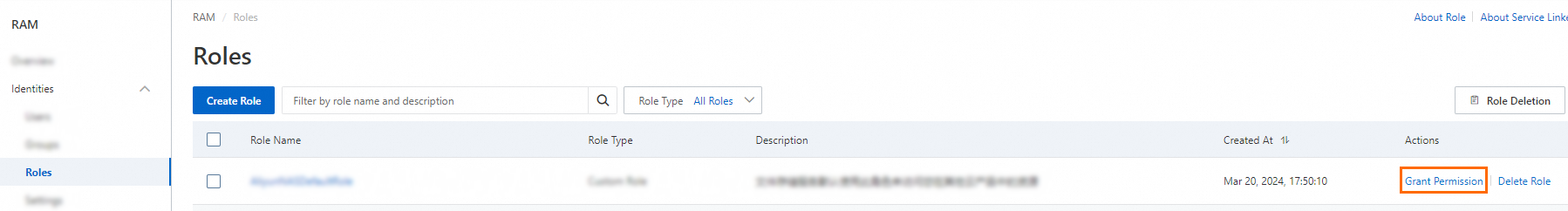
You can also select multiple RAM roles and click Grant Permission in the lower part of the RAM role list to grant permissions to multiple RAM roles at a time.
In the Grant Permission panel, grant permissions to the RAM role.
Configure the Resource Scope parameter.
Account: The authorization takes effect on the current Alibaba Cloud account.
Resource Group: The authorization takes effect on a specific resource group.
NoteIf you select Resource Group for the Resource Scope parameter, make sure that the required cloud service supports resource groups. For more information, see Services that work with Resource Group.
Configure the Principal parameter.
The principal is the RAM role to which you want to grant permissions. The current RAM role is automatically selected.
Configure the Policy parameter.
A policy is a set of access permissions. You can select multiple policies at a time.
System policies: policies that are created by Alibaba Cloud. You can use but cannot modify these policies. Version updates of the policies are maintained by Alibaba Cloud. For more information, see Services that work with RAM.
NoteThe system automatically identifies high-risk system policies, such as AdministratorAccess and AliyunRAMFullAccess. We recommend that you do not grant unnecessary permissions by attaching high-risk policies.
Custom policies: You can manage and update custom policies based on your business requirements. You can create, update, and delete custom policies. For more information, see Create a custom policy.
Click Grant permissions.
Click Close.
After you attach the policy to the RAM role, you can use the RAM role to log on to the ARMS console. For more information, see Assume a RAM role.
Policy elements
Effect
Specifies whether a statement result is an explicit allow or an explicit deny. Valid values: Allow and Deny.
Action
Action | Description |
arms:ReadTraceApp | The read-only permissions on the specified application, including the permissions to view information such as application overview, interface calls, and application diagnostics. |
arms:EditTraceApp | The edit permissions on the specified application, including the permissions to apply custom configurations and set custom parameters. |
arms:DeleteTraceApp | The permissions to delete the specified application. |
Resource
Specifies the resources on which the policy takes effect.
Sample statement:
"Resource": [
"acs:arms:<regionid>:*:armsapp/<appname>"
]Replace
<regionid>with the specified region ID. If you want to grant permissions on resources in all regions, replace <regionid> with*.Replace
<appname>with the specified application name. If you want to grant permissions on all applications, replace <appname> with*. If you want to specify applications that have the same name prefix, replace <appname> withName prefix*. Example:k8s*.
Condition
A condition block contains one or more conditions. Each condition consists of operators, keys, and values. 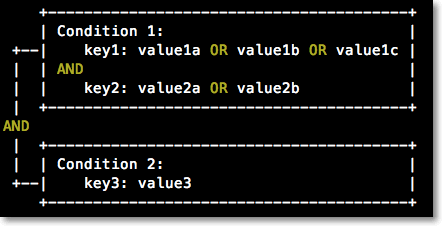
Description
You can specify one or more values for a condition key. If the value in a request matches one of the specified values, the condition is met.
A condition can have multiple keys that are attached to a single conditional operator. This type of condition is met only if all requirements for the keys are met.
A condition block is met only if all conditions are met.
You can specify resources by using key-value pairs. For more information about how to attach tags to an application, see Manage tags.
Key-value pairs support the following operators:
StringEquals
StringNotEquals
StringEqualsIgnoreCase
StringNotEqualsIgnoreCase
StringLike
StringNotLike
Condition key: arms:tag
Condition key value: key-value pairs
The following example demonstrates a condition that matches applications associated with the key0: value01 or key0: value02 tag.
"Condition": {
"StringEquals": { // The operator.
"arms:tag/key0":[ // The condition key.
"value01", // The value of the condition key.
"value02"
]
}
}References
To use a custom policy, you must understand the permission control requirements of your business and the authorization information of ARMS. For more information, see RAM authorization.