This topic describes how to integrate Nagios with Alert Management.
Step 1: Create a Nagios integration
- Log on to the ARMS console. In the left-side navigation pane, choose .
- On the Alert Integration tab, click Nagios.
- In the Create Nagios Integration dialog box, enter a name and a description for the Nagios integration, specify the
automatic recovery time of alert events, and then click Save.
Note If an alert event is not triggered again within the specified period of time, the
alert event is automatically cleared.
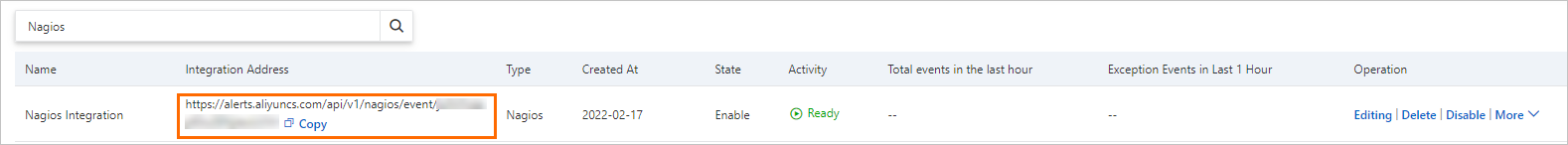
- On the Alert Integration tab, find the Nagios integration that you created and copy the URL in the Integration
Address column.
Step 2: Configure a Nagios alert template
- Create an alert notification script.
- Log on to the server where Nagios is located and enter the following path:
cd /usr/local/nagios/libexec/
- Create a script file named nagios-alert.py. Add the following content to the file:
Note The
integration_url in the script file must be replaced with the integration address obtained in
Step 1.
#!/usr/bin/python
# -*- coding: utf-8 -*-
import requests
import json
import sys
import os
headers = {'Content-Type': 'application/json;charset=utf-8'}
api_url = "integration_url" // Replace the integration_url with the integration address obtained in Step 1.
def parse(sys):
object_type = str(sys.argv[1])
notification_type = str(sys.argv[2])
host_name = str(sys.argv[3])
host_ip = str(sys.argv[4])
state = str(sys.argv[5])
time = str(sys.argv[6])
info = str(sys.argv[7])
if object_type == 'host':
description = "[{}] {} alert: {} is {}".format(notification_type, object_type, host_name, state)
service = ""
else:
service = str(sys.argv[8])
description = "[{}] {} alert: {}/{} is {}".format(notification_type, object_type, host_name, service, state)
content_dict = {'service':""}
content_dict['object_type'] = object_type
content_dict['notification_type'] = notification_type
content_dict['host_name'] = host_name
content_dict['host_ip'] = host_ip
content_dict['state'] = state
content_dict['time'] = time
content_dict['info'] = info
content_dict['service'] = service
content_dict['description'] = description
print(content_dict)
return content_dict
def msg(text):
result = requests.post(url=api_url, data=json.dumps(text), headers=headers)
print(result)
if __name__ == '__main__':
text = parse(sys)
msg(text)
- Run the following command to install the Requests library:
- Configure the Commands file.
- Run the following command to modify the commands.cf file:
vim /usr/local/nagios/etc/objects/commands.cf
- Add the following content to the commands.cf file:
define command{
command_name notify-host-by-alert
command_line python /usr/local/nagios/libexec/nagios-alert.py "host" "$NOTIFICATIONTYPE$" "$HOSTALIAS$" "$HOSTADDRESS$" "$HOSTSTATE$" "$LONGDATETIME$" "$HOSTOUTPUT$"
}
define command{
command_name notify-service-by-alert
command_line python /usr/local/nagios/libexec/nagios-alert.py "service" "$NOTIFICATIONTYPE$" "$HOSTALIAS$" "$HOSTADDRESS$" "$SERVICESTATE$" "$LONGDATETIME$" "$SERVICEOUTPUT$" "$SERVICEDESC$"
}
- Enter
:wq to save the changes to the commands.cf file.
- Specify the contact information.
- Run the following command to modify the contacts.cfg file:
vim /usr/local/nagios/etc/objects/contacts.cfg
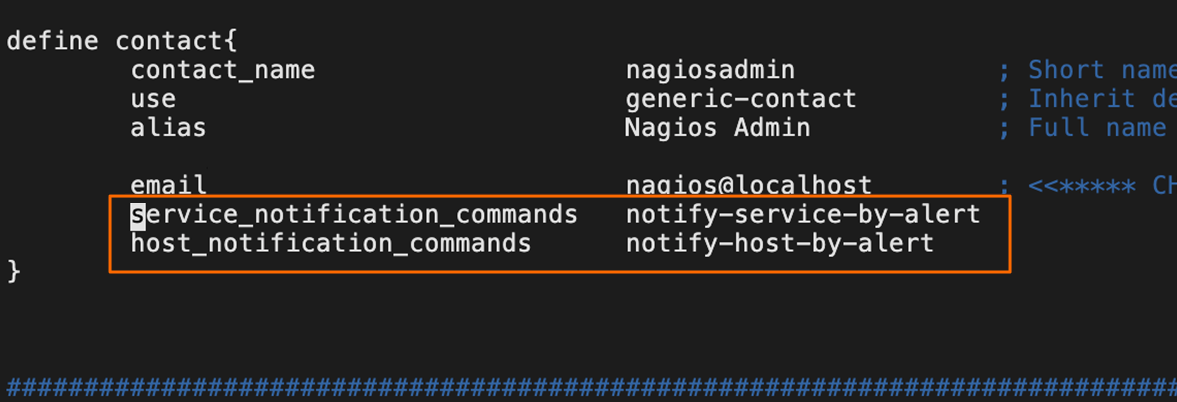
- Add the following content to the contacts.cfg file:
service_notification_commands notify-service-by-alert
host_notification_commands notify-host-by-alert
- Enter
:wq to save the changes to the contacts.cfg file.
- Run the following command to restart Nagios:
(Optional) Step 3: Modify the integration
Alert Management provides field mappings between Nagios alert sources and ARMS alert
events. You can also add or modify the mappings between fields on the Edit Integration page.
Sample alert source:
{
"info":"SWAP CRITICAL - 0% free (0 MB out of 0 MB) - Swap is either disabled, not present, or of zero size.",
"description":"[PROBLEM] service alert: localhost/Swap Usage is CRITICAL",
"service":"Swap Usage",
"host_ip":"127.0.0.1",
"state":"CRITICAL",
"object_type":"service",
"time":"Tue Sep 14 10:46:49 CST 2021",
"notification_type":"PROBLEM",
"host_name":"localhost"
}
- On the Alert Integration tab, find the integration that you want to manage and click Edit in the Actions column.
- In the Event Mapping section, click Send Test Data.
- In the Send Test Data dialog box, enter the alert content of a third-party alert source in the JSON format
and click Send.
Note
- If the message Uploaded. No events are generated. Configure mappings based on the original data. appears, the fields of the alert source are not mapped to the fields of ARMS alert
events. The data that is sent is displayed in the left-side box. This allows you to
select the source fields when you configure mappings.
- If the message Uploaded. appears, the alert content is reported to the Alert Event History page. For more
information, see View historical alert events.
- In the Send Test Data dialog box, click Disable.
- In the left part of the Event Mapping section, click the data records for which you want to configure mappings to view
the details.
- In the right part of the Event Mapping section, configure field mappings between the alert source and ARMS.
- Optional:In the Select Root Node section, specify whether to enable batch processing.
If an array node exists in the alert data, you can specify the array node as the root
node. The data that belongs to the root node is processed in a batch.
After you select Use Batch Processing, select the array node to be processed as the root node.
Note If multiple array nodes exist in the alert data, you can select only one of the array
nodes for batch processing.
- In the Map Source Fields to Target Fields section, map the fields of the alert source to the fields of ARMS alerts.
Click the Map icon to change the field mapping method.
- Direct: The specified field of the alert source is mapped to the specified alert field
of ARMS.
- Series: You can use delimiters to concatenate multiple fields of the alert source
into one field, and then map this field to the specified alert field of ARMS. Only
special characters can be used as delimiters.
- Condition: The specified fields of the alert source are mapped to the alert fields
of ARMS only if the field values meet the specified conditions.
- Mapping table: You must configure a mapping table that maps the severity levels of
the alert source to the severity levels of ARMS alerts. You need to configure a mapping
table only for the severity field.
The following table describes the alert fields of ARMS.
| Alert field |
Description |
| alertname |
The name of the custom alert. |
| severity |
The alert level. You must configure mappings for this field. The mapping method must
be set to Direct.
|
| message |
The description of the alert. The description is used as the content of the alert
message. The description cannot exceed 15,000 characters in length.
|
| value |
The sample value of a metric. |
| imageUrl |
The URL of the line chart that contains Grafana metrics. The URL is used to map the
line chart.
|
| check |
The check item of the alert. Examples: CPU, JVM, Application Crash, and Deployment.
|
| source |
The source of the alert. |
| class |
The type of the object that triggers the alert event, for example, host. |
| service |
The source service of the alert. Example: Login Service. |
| startat |
The timestamp that represents the start time of the event. |
| endat |
The timestamp that represents the end time of the event. |
| generatorUrl |
The URL of the event details. |
- Configure field deduplication for alert events.
To reduce duplicate data, the system uses relevant fields as the basis for deduplication.
ARMS Alert Management allows you to preview the deduplication grouping results of
historical event data that is displayed in the
Event Mapping section. You can change the fields to be deduplicated.
Note You can configure deduplication only for events that are not cleared.
- In the Event Deduplication section on the Integration Details page, select the fields that are used for deduplication.
If multiple events have the same value for a specified field, the events are merged
into one alert notification.
- Click Deduplication Test to preview the alert group after deduplication.
Note The deduplication test takes effect only on the latest 10 data records that are uploaded
in the left part of the Event Mapping section.
- After you configure the settings, click Save.
View the details about an alert event
- In the left-side navigation pane of the ARMS console, choose .
- On the Alert Event History page, click the name of the alert event to view the event details. For more information,
see View historical alert events.
Manage the integration
In the left-side navigation pane, choose . On the Alert Integration tab, you can perform the following operations on the integrations that you created:
- View the details of an integration: Find the integration and then click the row. On
the Integration Details page, view the integration details.
- Update a key: Find the Grafana integration and then choose in the Actions column. In the message that appears, click OK.
- Modify an integration: Find the integration and then click Edit in the Actions column. On the Integration Details page, modify the integration information and then click Save.
- Enable or disable an integration: Find the integration and then click Disable or Enable in the Actions column.
- Delete an integration: Find the integration and then click Delete in the Actions column. In the message that appears, click OK.
- Add an event processing flow to an integration: Find the integration and click Add Event Processing Flow in the Actions column. For more information, see Work with event processing flows.
- Create a notification policy: Find the integration for which you want to create a
notification policy, and click More in the Actions column. In the list that appears, click Create Notification Policy. For more information, see Create and manage a notification policy.
What to do next
After you create a notification policy, the system generates alerts and sends alert
notifications for reported alert events based on the notification policy that you
created. For more information, see Create and manage a notification policy. On the Alert Sending History page, you can view the alerts that are generated based on the configured notification
policy. For more information, see View historical alerts.