This topic describes how to access API Gateway from Function Compute over a VPC.
Overview
API Gateway can be integrated with Function Compute to build a serverless architecture. You may need to call APIs published on API Gateway when you use Function Compute. For security purposes, we recommend that you access API Gateway over an internal network when you use Function Compute. This topic focuses on access to API Gateway over an internal network in the following scenarios:
Scenario 1: API Gateway and Function Compute are deployed in the same region.
Scenario 2: API Gateway and Function Compute are deployed in different regions.
Follow these configuration principles in the two scenarios:
Configure a VPC to access API Gateway. For more information, see Access API Gateway over a VPC.
Configure a VPC to access Function Compute. For more information, see Configure network settings
Scenario 1
Build an architecture similar to the following figure.
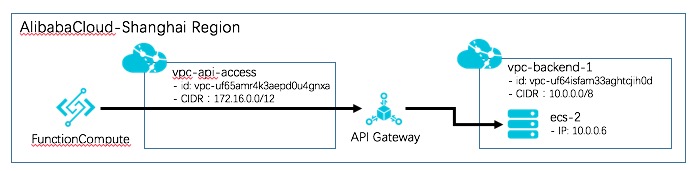
Two VPCs named vpc-api-access and vpc-backend-1 are created in the China (Shanghai) region.
One dedicated API Gateway instance is created in the China (Shanghai) region.
In vpc-backend-1, an Elastic Compute Service (ECS) instance is created as the backend service of API Gateway. This ECS instance provides an API over HTTP. The HTTP service address is http://localhost:8080/web/cloudapi. A security group is configured to allow API Gateway to access this ECS instance.
Create an API, with VPC as the backend service type.
For more information, see Use a resource in a VPC as the backend service of an API operation. Take note of the following points:
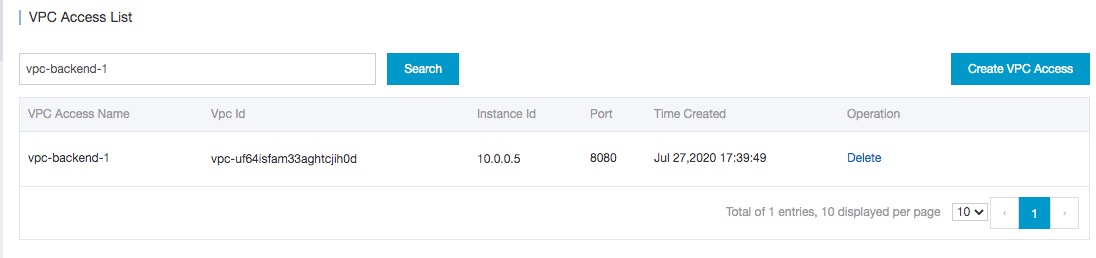
Create a VPC authorization. The created VPC authorization is displayed on the VPC Access List page.
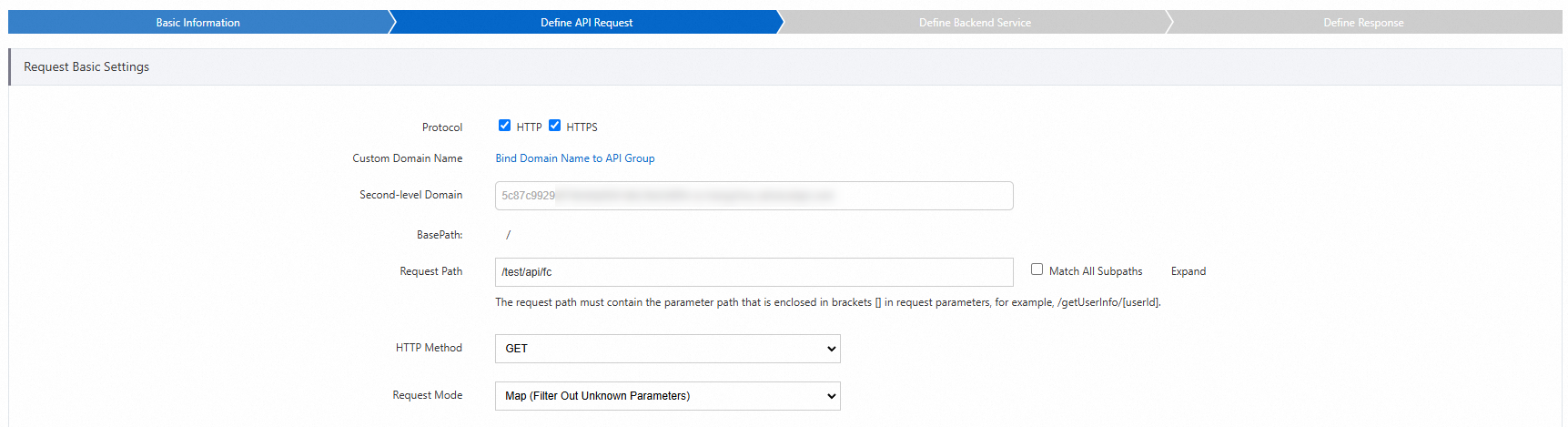
Set Backend Service Type to VPC. Set Security Certification to No Certification to facilitate subsequent API call testing.
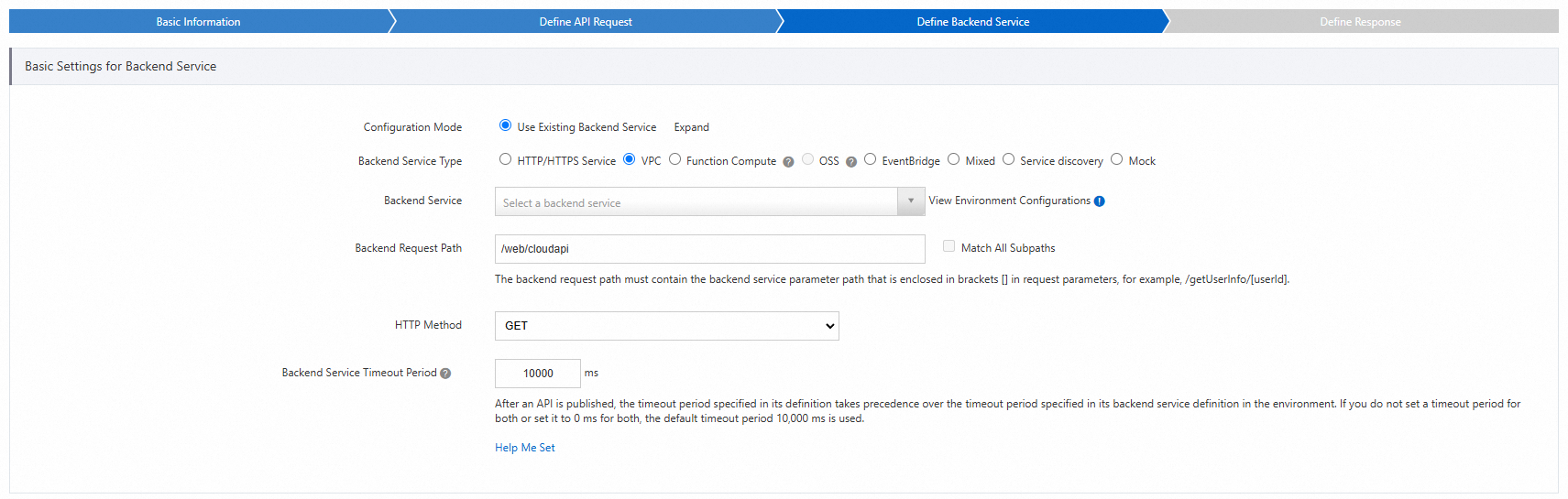
Save the settings and publish the API to the production environment.
Configure permissions on access to API Gateway over a VPC.
In the Dedicated Instance (VPC) section of the Instance list page in the API Gateway console, click Bind to VPC on the right of the Client VPC field. In the dialog box that appears, select the ID of vpc-api-access from the Vpc Id drop-down list and click Confirm. You can access API Gateway over vpc-api-access.

Enable a VPC subdomain for an API group.
On the Group Details page, click Enable VPC Second-level Domain on the right of the VPC Domain Name field. In the Enable VPC Second-level Domain message, click Confirm. A VPC second-level domain name is assigned to this API group. You can use this domain name to call APIs in this API group.
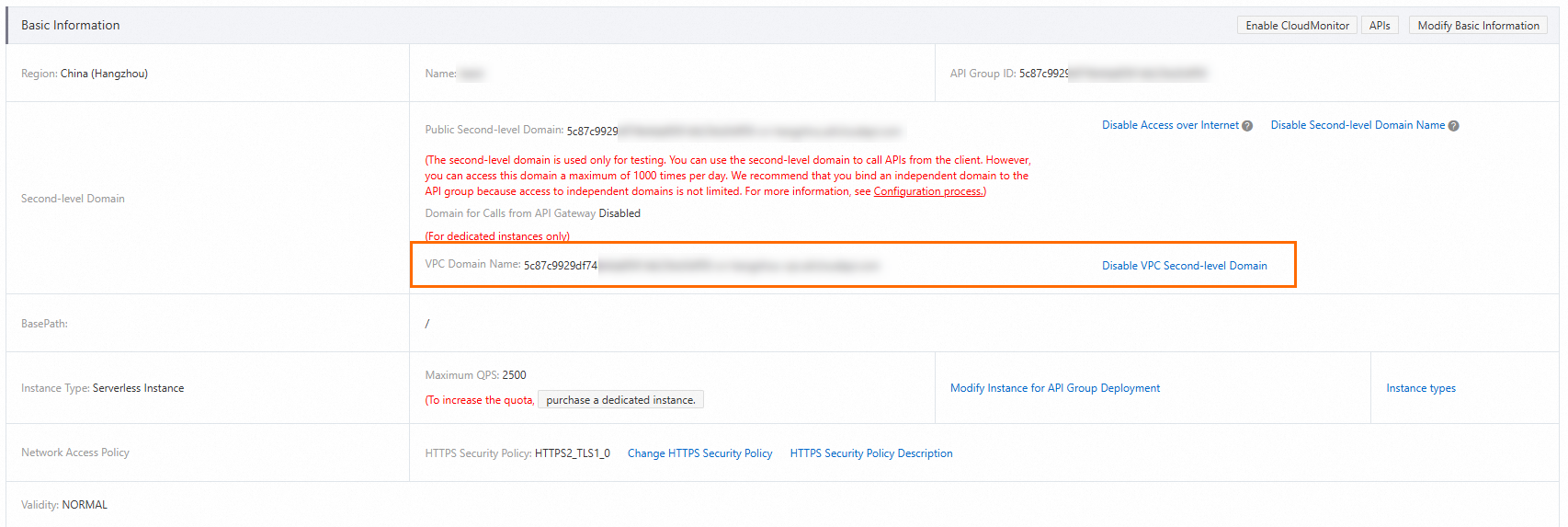
Internet access is enabled for the API group by default. You can click Disable Access over Internet to disable Internet access based on your business requirements. If Internet access is disabled, you cannot perform online debugging in the API Gateway console.
Create a function.
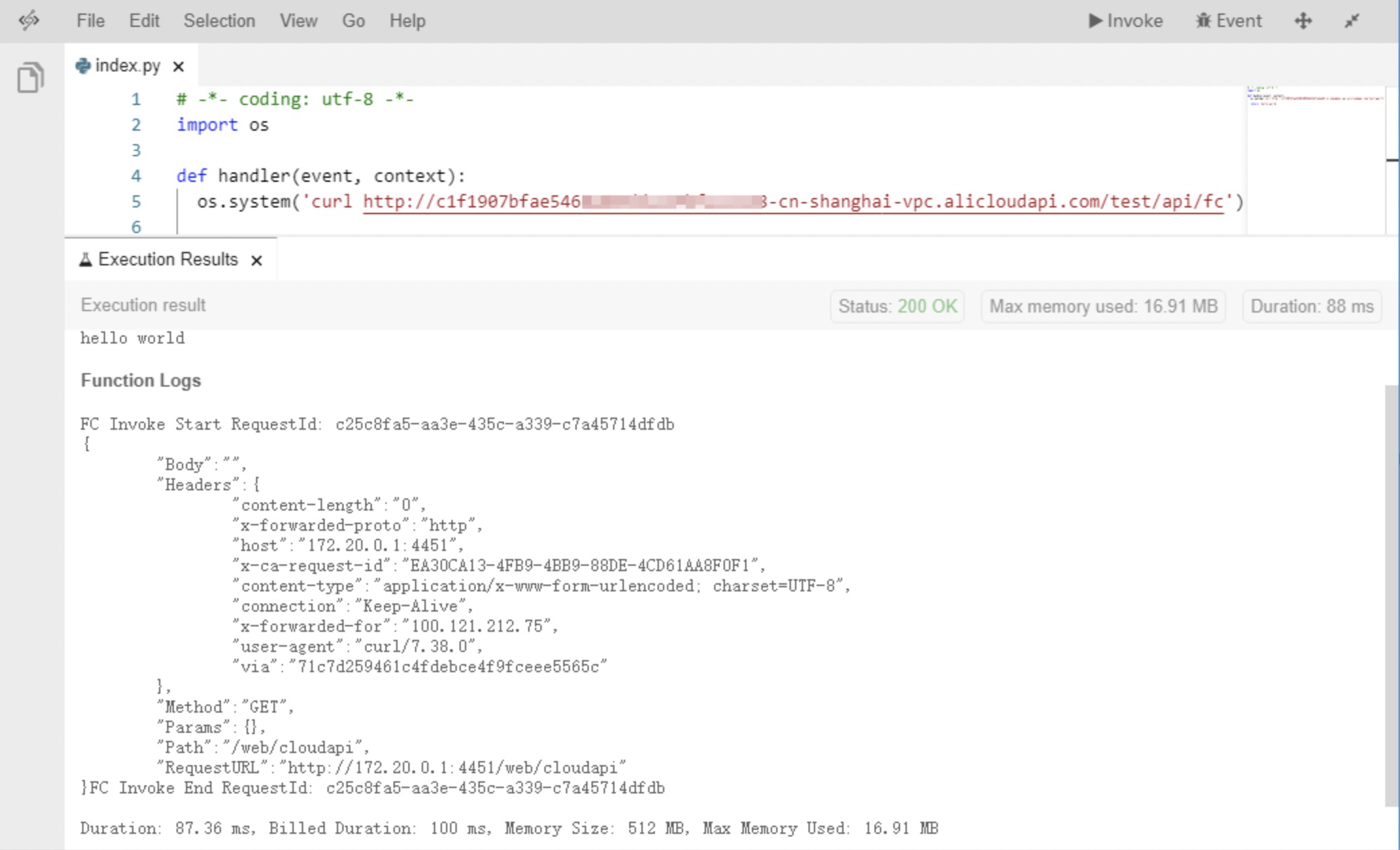
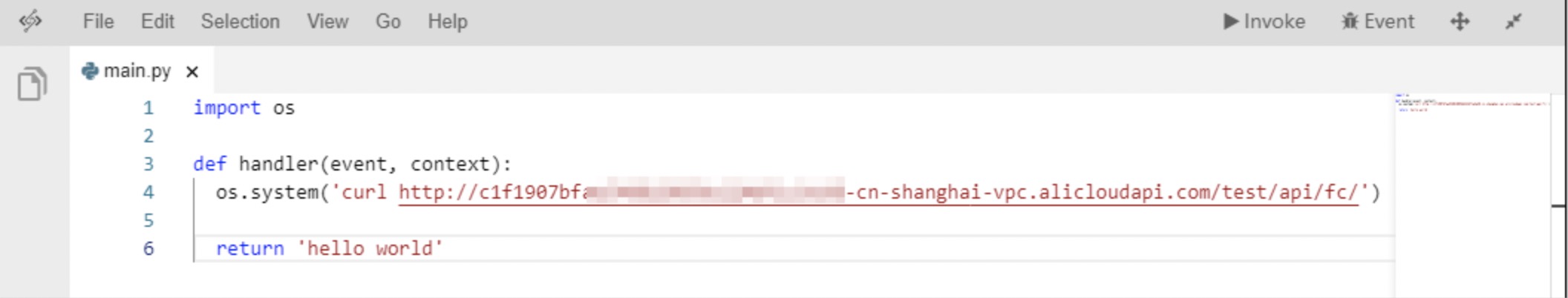
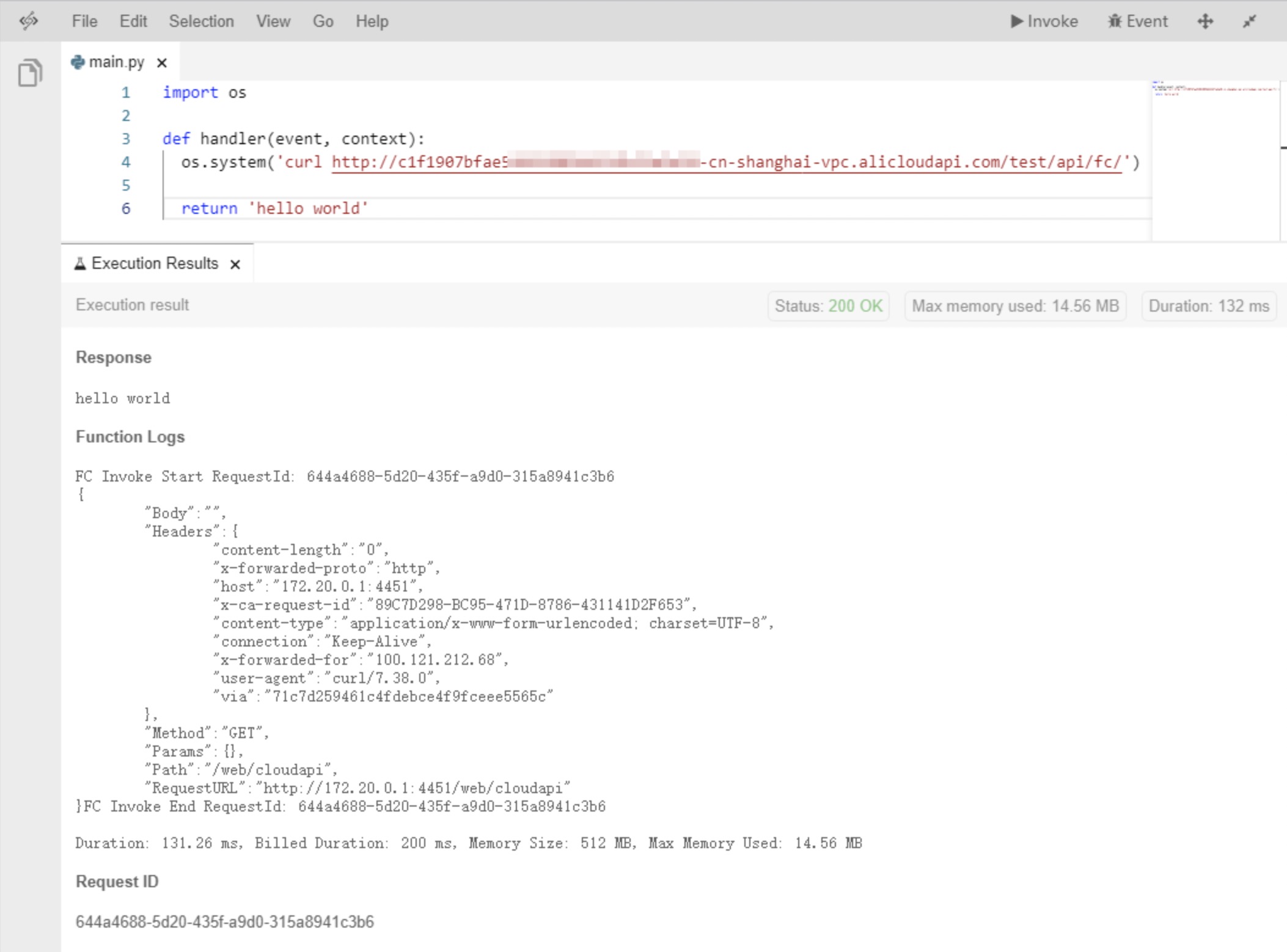
In Function Compute, create an application and create a function that runs in the Python environment. The following figure shows the content of this function.
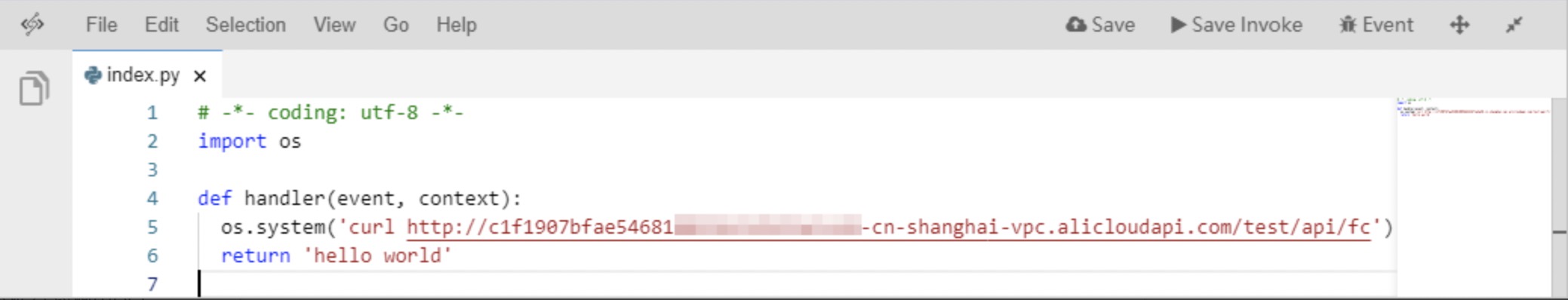
In this function, only the curl command is run to call APIs under a VPC subdomain. If you run the curl command to call APIs bound to the VPC subdomain, the API call fails.
Create a vSwitch in vpc-api-access to connect to Function Compute.
Log on to the Function Compute console and perform the following configurations. For more information, see Configure network settings
In the Network Config section of the Configure Service page, select vpc-api-access from the VPC drop-down list and select the created vSwitch from the Vswitches drop-down list.
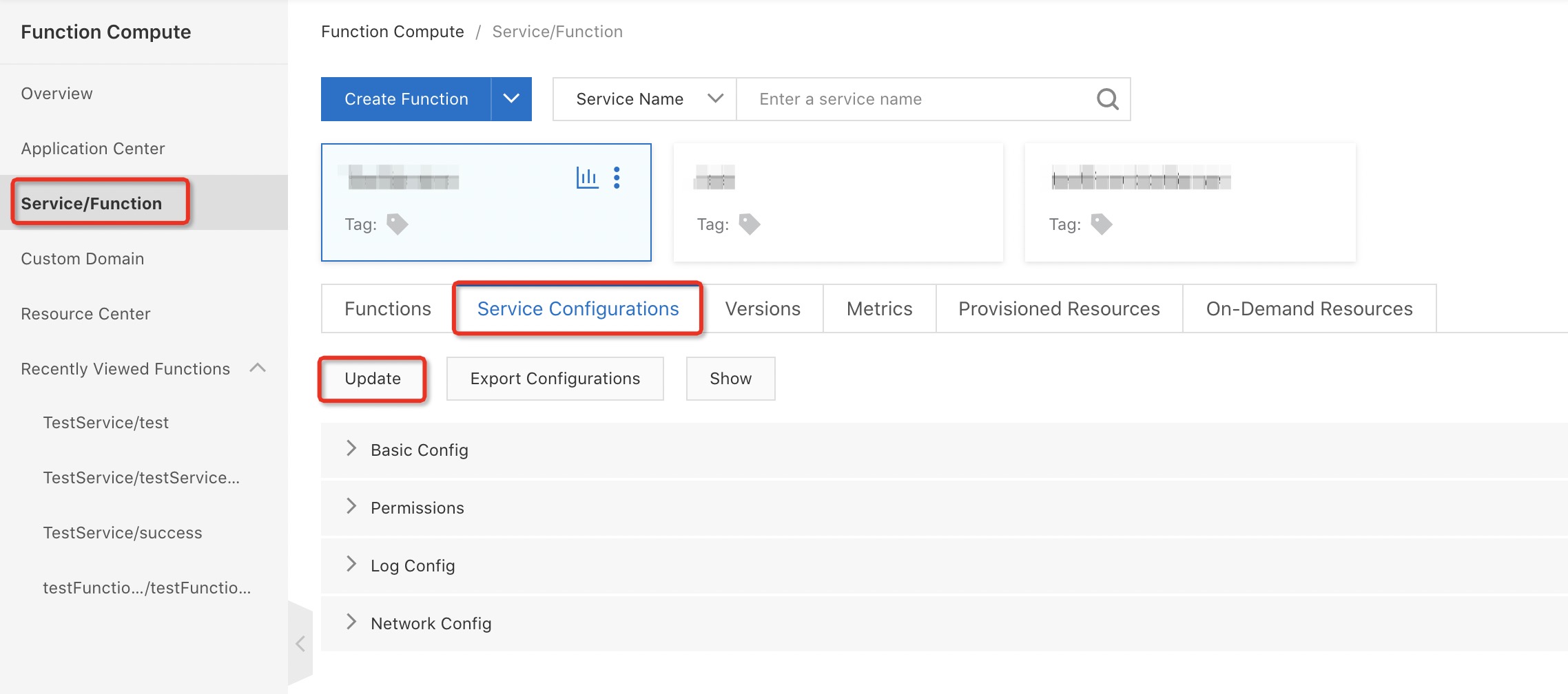
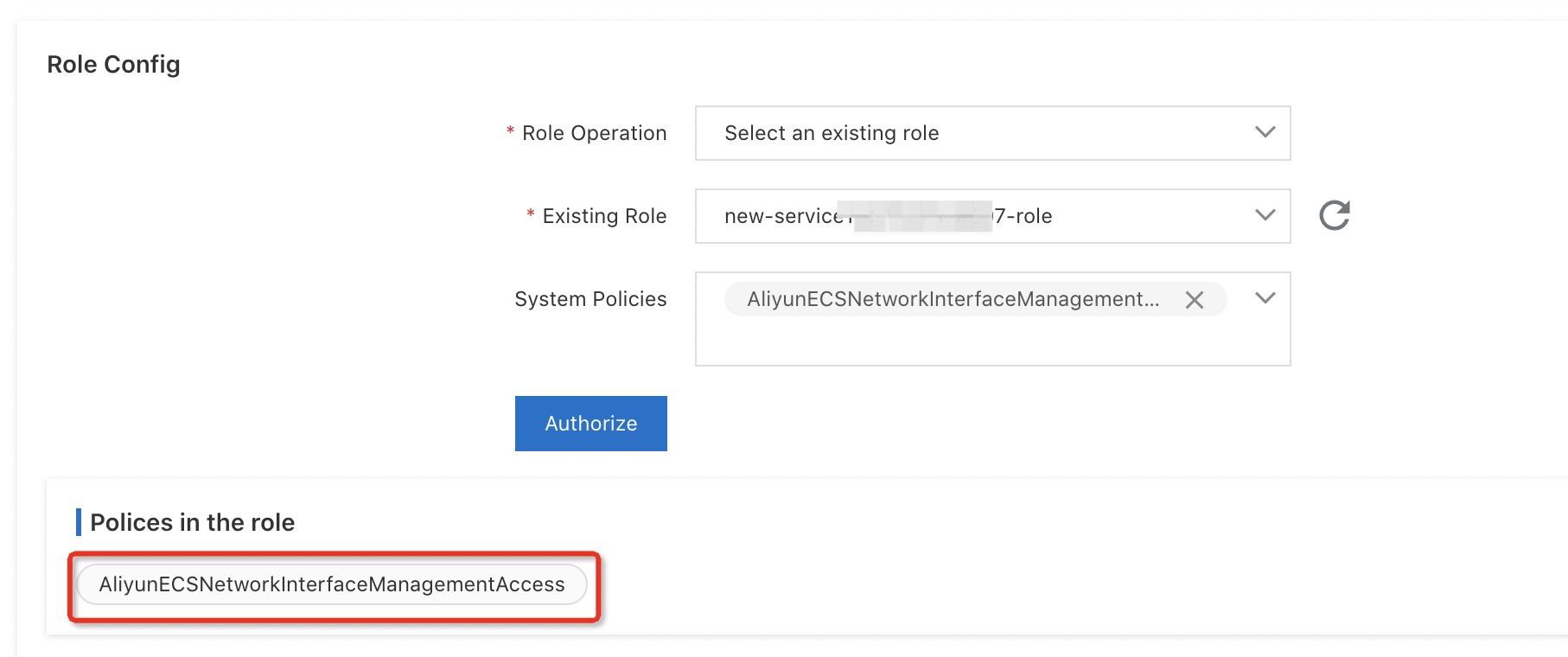
In the Role Config section of the Configure Service page, select Create new role from the Role Operation drop-down list, select AliyunECSNetworkInterfaceManagementAccess from the System Policies drop-down list, click Authorize, and then click Submit.
Execute the function for a test.
After you execute this function, you can use this VPC subdomain to access APIs published on API Gateway.
Scenario 2
Build an architecture similar to the following figure.
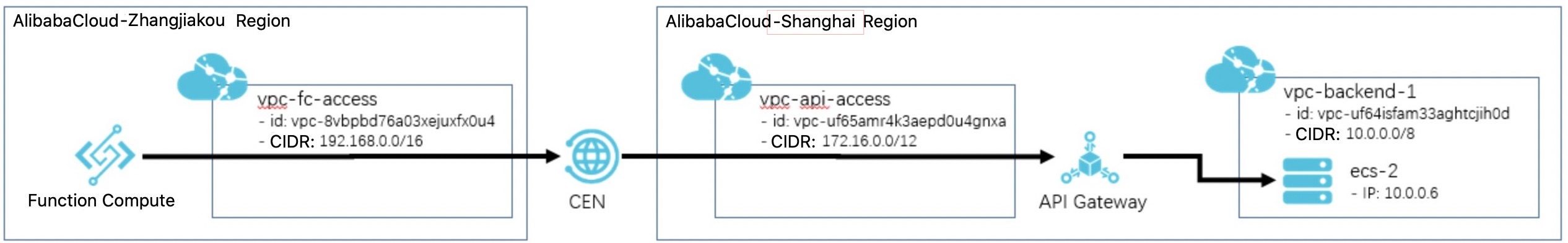
In the China (Zhangjiakou-Beijing Winter Olympics) region, an application is created for Function Compute to initiate API calls. A VPC named vpc-fc-access is created. Function Compute can connect to the Cloud Enterprise Network (CEN) over this VPC.
In the China (Shanghai) region, a dedicated API Gateway instance and a VPC named vpc-api-access are connected. API Gateway can connect to the CEN over this VPC.
In the China (Shanghai) region, another VPC named vpc-backend-1 is created. An ECS instance is created as the backend service of API Gateway. This ECS instance provides an API over HTTP. The HTTP service address is http://localhost:8080/web/cloudapi. A security group is configured to allow API Gateway to access this ECS instance.
Create a CEN.
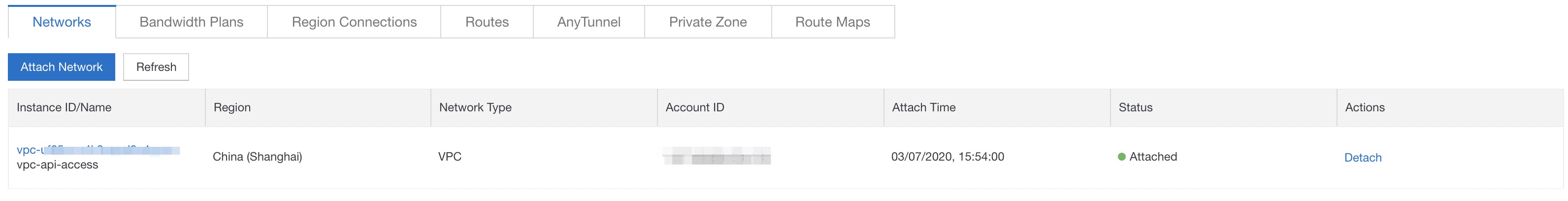
Create a CEN to interconnect vpc-api-access and vpc-fc-access, so Function Compute can communicate with API Gateway over an internal network. For more information about how to configure a CEN, see What is CEN?. Log on to the CEN console and create a CEN instance. Associate vpc-api-access and vpc-fc-access with the CEN instance.
Configure the bandwidth.
Purchase a bandwidth plan used for communication within the CEN instance. In this example, a bandwidth plan of 2 Mbit/s is purchased. You can purchase a bandwidth plan based on your business requirements.
On the Region Connections tab of the CEN page, configure the bandwidth for the regions of the CEN instance. You can configure the bandwidth size for each pair of connected regions based on the bandwidth plan.
Configure cross-VPC routes.
Submit a ticket to the CEN product team to configure the routes. Provide the configuration parameters required by the ResolveAndRouteServiceInCen API operation. These routes enable communication between API Gateway and the VPC in the China (Zhangjiakou-Beijing Winter Olympics) region.
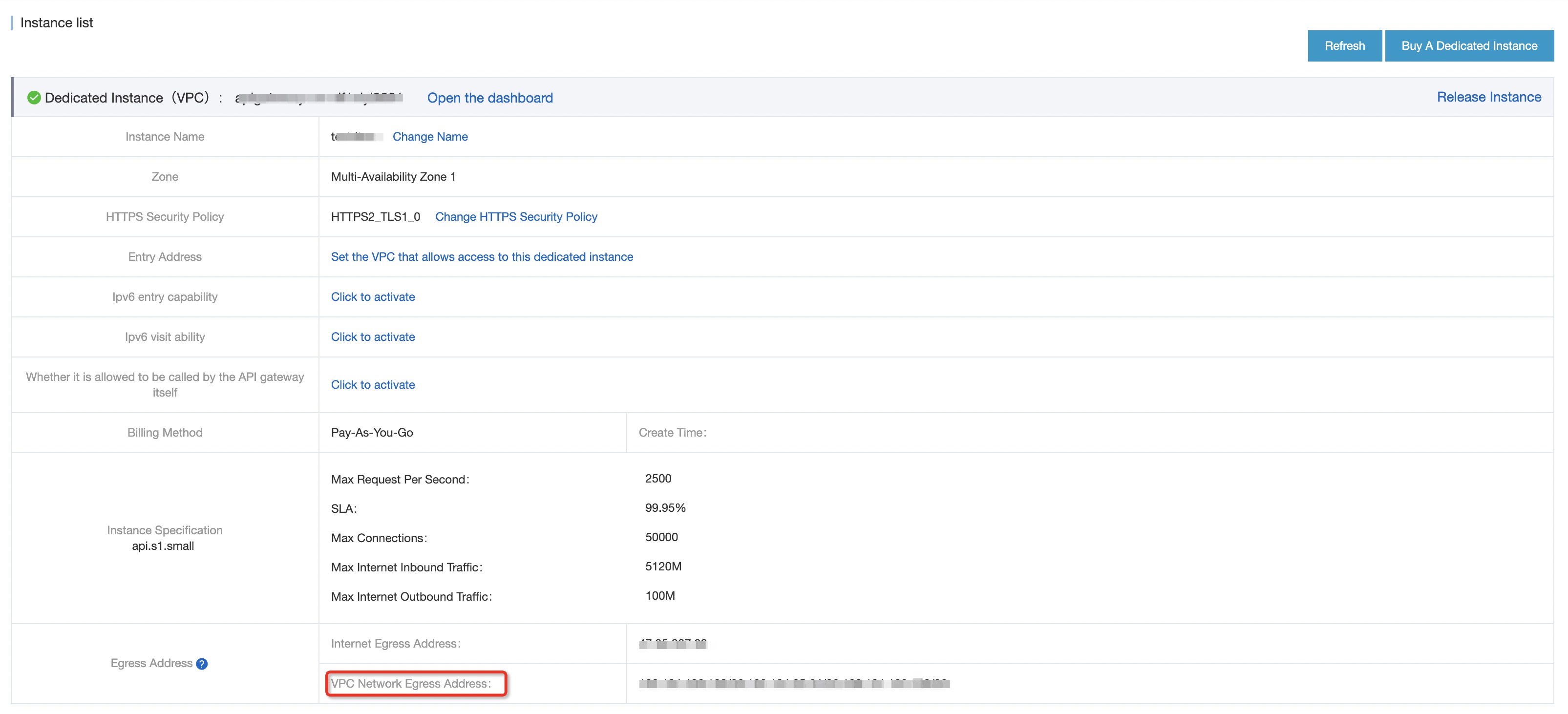
AccessRegionIds.1=cn-zhangjiakou AccessRegionIds.2=cn-shanghai CenId=cen-uggzcthgz7cwsl7prr #The ID of the CEN instance. Host=100.104.255.128/26 #The VPC egress address of the dedicated API Gateway instance. HostRegionId=cn-shanghai HostVpcId=vpc-uf65amr4k3aepd0u4gnxa #The ID of vpc-api-access. API Gateway deployed in the China (Shanghai) region can connect to the CEN over this VPC.
To obtain the VPC egress address of the dedicated API Gateway instance, go to the Instances page in the API Gateway console.
After your ticket is processed, you can view the routes configured for the China (Shanghai) and China (Zhangjiakou-Beijing Winter Olympics) regions in the CEN console. The custom routes are added based on the configuration parameters that you provided.
Create an API, with VPC as the backend service type.
Follow the operations described in Step 2 in scenario 1.
Configure permissions on access to API Gateway over a VPC.
Follow the operations described in Step 3 in scenario 1.
Enable a domain name for an API group on the VPC.
Follow the operations described in Step 4 in scenario 1.
Create a function.
In the Function Compute instance deployed in the China (Zhangjiakou-Beijing Winter Olympics) region, create an application and create a function that runs in the Python environment. The following figure shows the content of this function.
Configure VPC access for Function Compute.
Create a vSwitch in vpc-fc-access. Then, log on to the Function Compute console and perform the required configurations. The operations are similar to those described in Step 6 in scenario 1.
Execute the function for a test.
After you execute this function, you can use this VPC subdomain to access APIs published on API Gateway.
Limits
You can only use a dedicated API Gateway instance.