API Gateway can be accessed from the Internet or virtual private clouds (VPCs). This topic describes how to access API Gateway by using a VPC.
Overview
To access API Gateway by using a VPC, you must obtain the second-level domain name for VPC of the API group that you want to access. A second-level domain name for VPC has the following characteristics:
The second-level domain name for VPC of an API group can be used only in VPCs. By using this domain name, you can make as many API calls in the API group as you want every day.
The second-level domain name for VPC of an API group supports HTTP and HTTPS access.
The method and scope for enabling VPC private domain names vary by instance type. For more information, see Enable VPC access for a dedicated instance and a serverless instance.
If you want to access API Gateway by using a VPC on a hybrid cloud, such as a hybrid cloud that is built based on Cloud Enterprise Network (CEN) or a virtual private network with Internet Protocol security (IPsec), we recommend that you purchase and configure a dedicated instance in the API Gateway console. You can bind your VPC on the hybrid cloud to an API group on the dedicated instance. Then, you can access the API group by using its second-level domain name for VPC in your VPC. This makes it convenient for you to configure local routing. The second-level domain name for VPC of each API group on a serverless instance is an IP address in the
100.x.x.xformat and cannot be a private IP address.For more configurations in hybrid cloud scenarios, see Centralized API management for hybrid clouds.
Enable VPC-based access for a serverless instance
After you enable VPC-based access for a serverless instance, all users of the instance can access the instance from their VPCs that are in the same region as the instance. 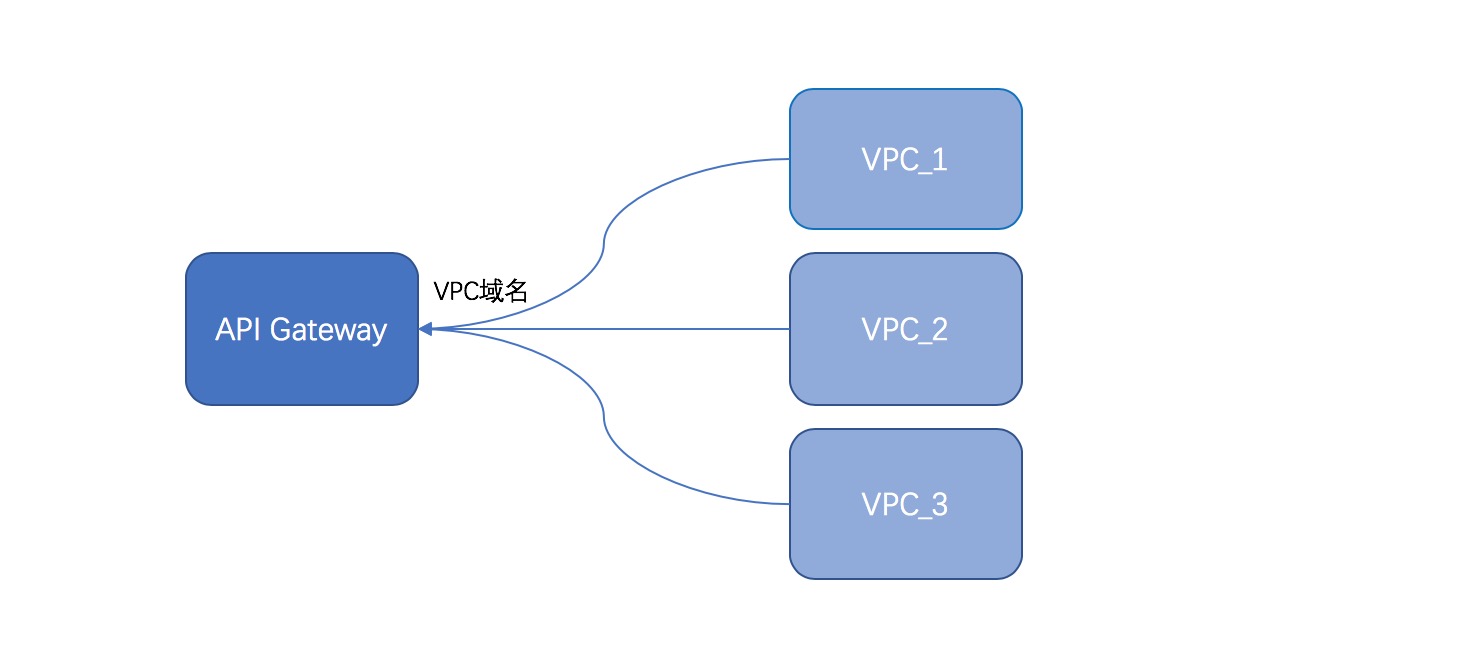
Procedure:
Log on to the API Gateway console. In the left-side navigation pane, choose Manage APIs > API Groups.
On the API Groups page, click the group that you want to manage. On the Group Details page, click Enable VPC Second-level Domain. In the message that appears, click Confirm.
NoteAPI Gateway automatically assigns a second-level domain name for VPC to this API group. This domain name can be used to call APIs in the API group.
Enable VPC access for a dedicated instance
When you enable VPC access for a dedicated instance, you can authorize only one VPC in the same region to access the dedicated instance. Other VPCs in the same region cannot access APIs on this instance. This enhances security. 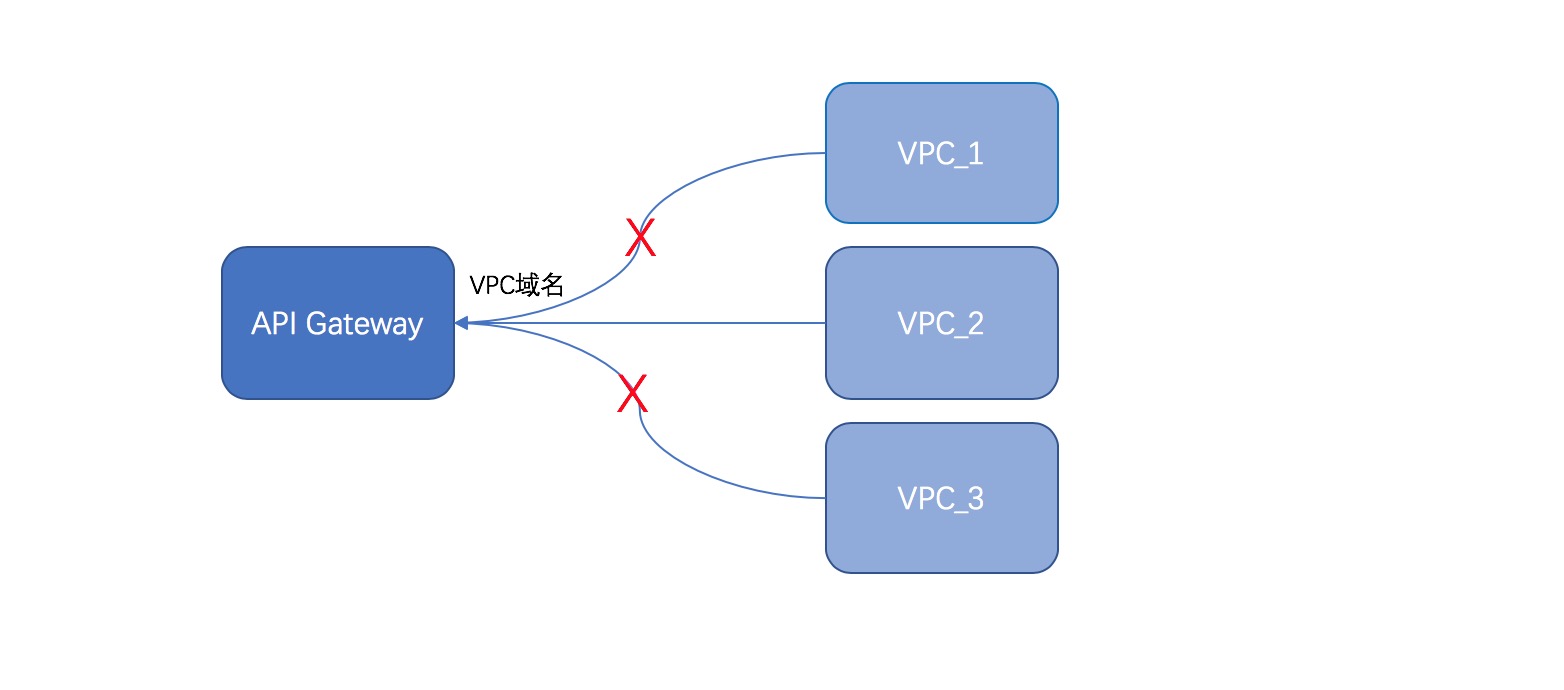
Procedure:
Log on to the API Gateway console. In the left-side navigation pane, choose Instances and Clusters > Dedicated Instances.
On the Dedicated Instances page, find the dedicated instance that you want to manage and click Bind to VPC.
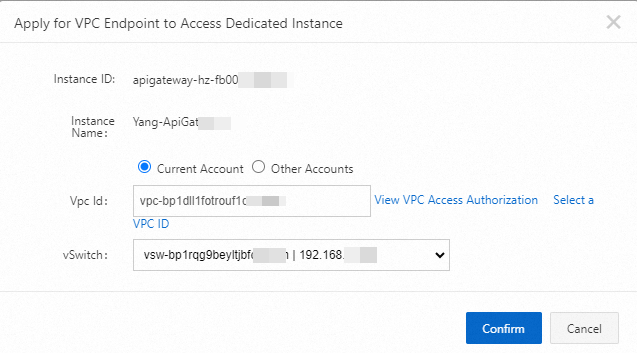
In the Apply for VPC Endpoint to Access Dedicated Instance dialog box, set the Vpc Id and vSwitch parameters and click Confirm. You can select only one vSwitch on a VPC.
In the left-side navigation pane, choose Manage APIs > API Groups. On the API Groups page, click the group that you want to manage to go to the Group Details page. Then, click Enable VPC Second-level Domain. In the message that appears, click Confirm. API Gateway automatically assigns a second-level domain name for VPC to this API group. You can also add a CNAME record for your own domain name to the second-level domain name for VPC. This way, you can use your own domain name to access the API group.
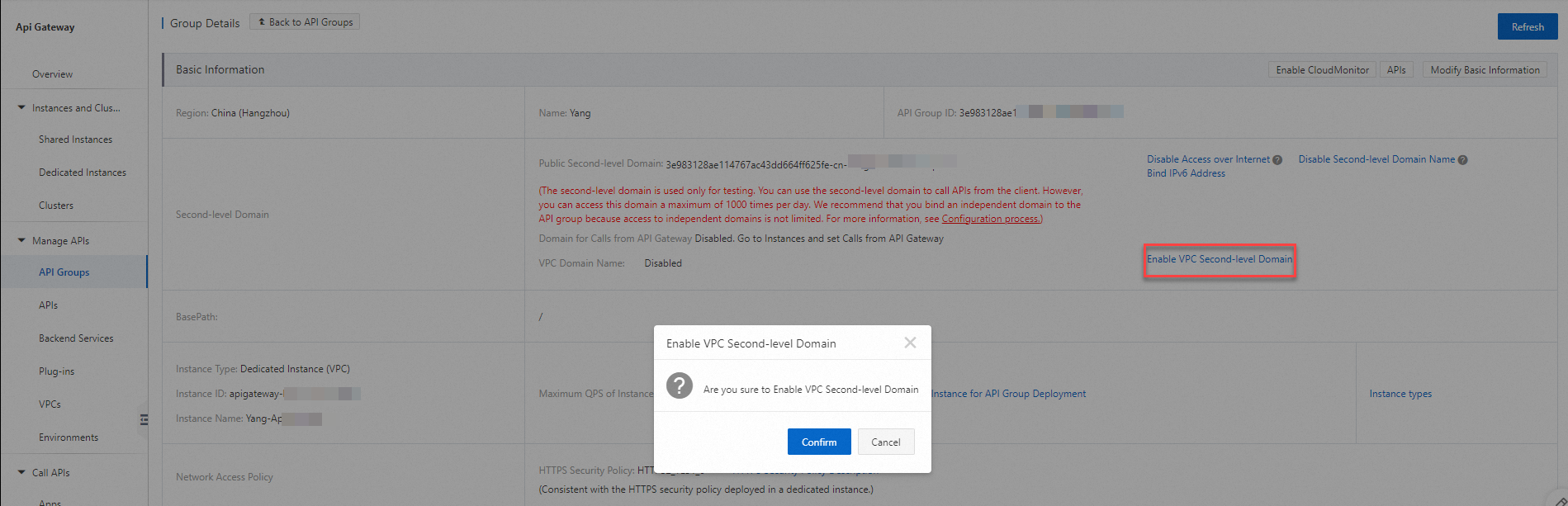
If you do not bind the instance to a VPC, you cannot enable VPC second-level domain name for the API group.
After you change a VPC that is bound to a dedicated instance to another VPC, the second-level domain name for VPC of each API group on this instance can be accessed only by the new VPC and not by the original VPC.
If the second-level domain name for VPC is enabled for an API group on a serverless instance and you want to move the API group to a dedicated instance, you must make sure that a VPC has been bound to the dedicated instance. Note that after you move the API group to the dedicated instance, the API group can be accessed only over the VPC that is bound to the dedicated instance.