A sidecar proxy is used to improve the network security, reliability, and observability of service calls. However, in scenarios where traffic is not required to pass through sidecar proxies, you can configure settings by using different methods to allow traffic to bypass sidecar proxies. This topic describes how to configure settings to allow inbound and outbound traffic or the traffic forwarded to a specific CIDR block to bypass sidecar proxies.
Prerequisites
An ASM instance is created. For more information, see Create an ASM instance.
A Container Service for Kubernetes (ACK) managed cluster is created. For more information, see Create an ACK managed cluster.
The cluster is added to the ASM instance. For more information, see Add a cluster to an ASM instance.
An ingress gateway is deployed. For more information, see Create an ingress gateway.
Configure settings to allow inbound and outbound traffic to bypass sidecar proxies
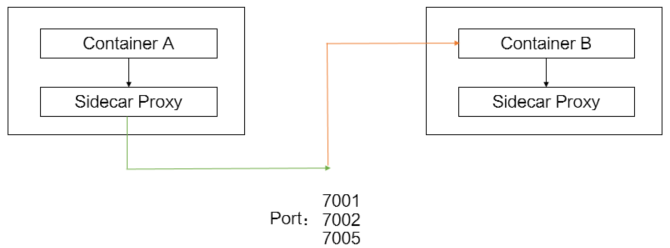
In some scenarios, high performance is required, and the security authentication such as mutual transport layer security (mTLS) authentication and tracing analysis features provided by Service Mesh (ASM) are unnecessary. In such scenarios, you can specify whether to allow the inbound and outbound traffic to bypass sidecar proxies. In this example, settings are configured to allow the inbound traffic over ports 7001, 7002, and 7005 to bypass sidecar proxies, and the outbound traffic to pass through sidecar proxies. This way, the specific inbound traffic can bypass the sidecar proxy. This reduces the resources required by the istio-proxy sidecar proxy and improves overall performance. The outbound traffic is required to pass through the sidecar proxy. Therefore, you can use the capabilities such as load balancing of ASM.
Method 1: Configure a blocking policy for sidecar proxies in the ASM console
In this example, the default namespace is used. You can configure a blocking policy for sidecar proxies in the default namespace by specifying the following parameters: Ports on Which Outbound Traffic Redirected to Sidecar Proxy and Ports on Which Inbound Traffic Not Redirected to Sidecar Proxy.
Log on to the ASM console.
In the left-side navigation pane, choose .
On the Mesh Management page, find the ASM instance that you want to configure. Click the name of the ASM instance or click Manage in the Actions column.
On the details page of the ASM instance, choose in the left-side navigation pane.
On the Sidecar Proxy Setting page, click the Namespace tab.
Select default from the Namespace drop-down list, click the
 icon on the left side of Enable/Disable Sidecar Proxy by Ports or IP Addresses, select and configure the parameters described in the following table, and then click Update Settings.
icon on the left side of Enable/Disable Sidecar Proxy by Ports or IP Addresses, select and configure the parameters described in the following table, and then click Update Settings.Parameter
Description
Ports on Which Outbound Traffic Redirected to Sidecar Proxy
The ports over which you want the outbound traffic to pass through sidecar proxies. In this example, set this parameter to 7001,7002,7005.
Ports on Which Inbound Traffic Not Redirected to Sidecar Proxy
The ports over which you want the outbound traffic to pass through sidecar proxies. In this example, set this parameter to 7001,7002,7005.
Restart a pod for the settings of sidecar proxies to take effect.
Log on to the ACK console. In the left-side navigation pane, click Clusters.
On the Clusters page, find the cluster that you want to manage and click its name. In the left-side pane, choose .
On the Pods page, find the pod that you want to delete and choose in the Actions column.
In the dialog box that appears, click OK.
Wait until the pod restarts. The settings take effect after the pod restarts.
Method 2: Configure a blocking policy for sidecar proxies in the ACK console
A Deployment is used in this example. Annotations are added to the YAML file of a pod to configure a blocking policy for sidecar proxies. For more information, see Configure a sidecar proxy by adding resource annotations.
Log on to the ACK console. In the left-side navigation pane, click Clusters.
On the Clusters page, find the cluster you want to manage and click its name. In the left-side pane, choose .
On the Deployments page, find the application that you want to manage and click the Details in the Actions column.
In the upper-right corner of the application details page, click View in YAML.
In the Edit YAML dialog box, add the following content to the spec.template.metadata parameter and click Update.
annotations: traffic.sidecar.istio.io/excludeInboundPorts: '7001,7002,7005' traffic.sidecar.istio.io/includeOutboundPorts: '7001,7002,7005'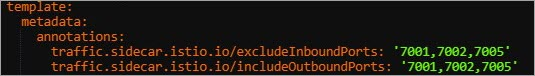
Restart a pod for the settings of sidecar proxies to take effect.
Log on to the ACK console. In the left-side navigation pane, click Clusters.
On the Clusters page, find the cluster that you want to manage and click its name. In the left-side pane, choose .
On the Pods page, find the pod that you want to delete and choose in the Actions column.
In the dialog box that appears, click OK.
Wait until the pod restarts. The settings take effect after the pod restarts.
Configure settings to allow the traffic forwarded to a specific CIDR block to bypass sidecar proxies
In this example, the traffic forwarded to the CIDR block 47.XX.XX.144/32 is allowed to bypass sidecar proxies. You can use the following methods as needed:
Method 1: Configure a blocking policy for sidecar proxies in the ASM console
Log on to the ASM console.
In the left-side navigation pane, choose .
On the Mesh Management page, find the ASM instance that you want to configure. Click the name of the ASM instance or click Manage in the Actions column.
On the details page of the ASM instance, choose in the left-side navigation pane.
Configure a blocking policy for sidecar proxies at the global or namespace level.
Global level
On the Sidecar Proxy Setting page, click the global tab.
Click the
 icon on the left side of Enable/Disable Sidecar Proxy by Ports or IP Addresses, set the Addresses to Which External Access Is Not Redirected to Sidecar Proxy parameter to 47.XX.XX.144/32, and then click Update Settings.
icon on the left side of Enable/Disable Sidecar Proxy by Ports or IP Addresses, set the Addresses to Which External Access Is Not Redirected to Sidecar Proxy parameter to 47.XX.XX.144/32, and then click Update Settings.
Namespace level
On the Sidecar Proxy Setting page, click the Namespace tab.
On the Namespace tab, select default from the Namespace drop-down list. Click the
 icon on the left side of Enable/Disable Sidecar Proxy by Ports or IP Addresses, set the Addresses to Which External Access Is Not Redirected to Sidecar Proxy parameter to 47.XX.XX.144/32, and then click Update Settings.
icon on the left side of Enable/Disable Sidecar Proxy by Ports or IP Addresses, set the Addresses to Which External Access Is Not Redirected to Sidecar Proxy parameter to 47.XX.XX.144/32, and then click Update Settings.
Restart a pod for the settings of sidecar proxies to take effect.
Log on to the ACK console. In the left-side navigation pane, click Clusters.
On the Clusters page, find the cluster that you want to manage and click its name. In the left-side pane, choose .
On the Pods page, find the pod that you want to delete and choose in the Actions column.
In the dialog box that appears, click OK.
Wait until the pod restarts. The settings take effect after the pod restarts.
Method 2: Configure a blocking policy for sidecar proxies in the ACK console
A Deployment is used in this example. Annotations are added to the YAML file of a pod to configure a blocking policy for sidecar proxies. For more information, see Configure a sidecar proxy by adding resource annotations.
Log on to the ACK console. In the left-side navigation pane, click Clusters.
On the Clusters page, find the cluster you want to manage and click its name. In the left-side pane, choose .
On the Deployments page, click the name of the application that you want to manage.
In the upper-right corner of the application details page, click View in YAML.
In the Edit YAML dialog box, add the following content to the spec.template.metadata parameter and click Update.
annotations: traffic.sidecar.istio.io/excludeOutboundIPRanges: 47.XX.XX.144/32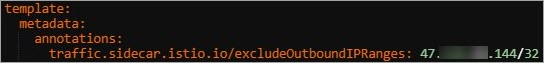
Restart a pod for the settings of sidecar proxies to take effect.
Log on to the ACK console. In the left-side navigation pane, click Clusters.
On the Clusters page, find the cluster that you want to manage and click its name. In the left-side pane, choose .
On the Pods page, find the pod that you want to delete and choose in the Actions column.
In the dialog box that appears, click OK.
Wait until the pod restarts. The settings take effect after the pod restarts.
Verify the result
You can select REGISTRY_ONLY as Outbound Traffic Policy on the Sidecar Proxy Setting page. This way, you can check whether the traffic passes through sidecar proxies. In REGISTRY_ONLY mode, if the traffic passes through sidecar proxies, the access to the destination CIDR block is blocked. If the traffic bypasses sidecar proxies, the access is successful.
Log on to the ASM console. Go to the Sidecar Proxy Setting page and click the global tab.
Click the
 icon on the left side of Outbound Traffic Policy, select REGISTRY_ONLY as Outbound Traffic Policy, and then click Update Settings.
icon on the left side of Outbound Traffic Policy, select REGISTRY_ONLY as Outbound Traffic Policy, and then click Update Settings. Run the following command to access the http://47.XX.XX.144/productpage URL:
curl -I http://47.XX.XX.144/productpageExpected output:
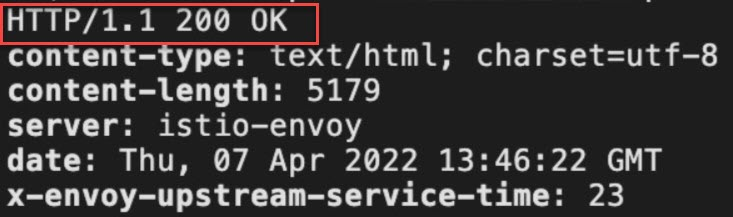 After you configure settings to allow the traffic forwarded to the CIDR block 47.XX.XX.144/32 to bypass sidecar proxies, the access to the http://47.XX.XX.144/productpage URL is successful. You can specify a CIDR block to which the traffic is forwarded to bypass sidecar proxies based on your business requirements.
After you configure settings to allow the traffic forwarded to the CIDR block 47.XX.XX.144/32 to bypass sidecar proxies, the access to the http://47.XX.XX.144/productpage URL is successful. You can specify a CIDR block to which the traffic is forwarded to bypass sidecar proxies based on your business requirements.