If you want to access a Container Registry Enterprise Edition instance across regions or from a data center to push or pull images, make sure that the virtual private cloud (VPC) of the access source and the VPC of the Enterprise Edition instance are connected. This topic describes how to obtain the IP address of an Enterprise Edition instance and configure a route to push or pull images from outside the region of the Enterprise Edition instance.
Scenarios
Scenario | Description | Operation |
Access an Enterprise Edition instance from a data center | You can use Virtual Private Network (VPN) gateways, Express Connect circuits, and Smart Access Gateway to connect the data center to the VPC of the Enterprise Edition instance. |
|
Access an Enterprise Edition instance across regions | You can use Cloud Enterprise Network (CEN) to connect the VPC of the access source to the VPC of the Enterprise Edition instance across regions. Note If you want to pull images from multiple regions, we recommend that you create multiple Enterprise Edition instances in these regions and use the global replication capability of Enterprise Edition instances to replicate images. For more information, see Replicate images within the same account. |
|
Description
In this example, an access source in the China (Shanghai) region accesses an Enterprise Edition instance in the China (Hangzhou) region in the same Alibaba Cloud account. Environmental information:
VPC1
Region: China (Hangzhou).
IPv4 CIDR block: 10.0.0.0/16.
CIDR block of vSwitch 1 in Hangzhou Zone J: 10.0.0.0/24.
CIDR block of vSwitch 2 in Hangzhou Zone K: 10.0.1.0/24. vSwitches are created in different zones to implement multi-zone disaster recovery.
IP address of Elastic Compute Service (ECS) Instance 1: 10.0.0.1. The ECS instances in this topic are used to verify connectivity.
VPC2
Region: China (Shanghai).
IPv4 CIDR block: 172.16.0.0/16.
CIDR block of vSwitch 1 in Shanghai Zone M: 172.16.0.0/24.
CIDR block of vSwitch 2 in Shanghai zone N: 172.16.1.0/24.
IP address of ECS Instance 2: 172.16.0.1.
Procedure:
Inter-region connection: Use CEN to connect the VPC of the access source in the China (Shanghai) region to the VPC of the Enterprise Edition instance in the China (Hangzhou) region. For more information, see Connect VPCs in different regions.
Obtain the following domain name information of the Enterprise Edition instance in the China (Hangzhou) region:
NoteThe ECS instance in the same region as the Enterprise Edition instance must access the Enterprise Edition instance over a VPC. For more information, see Configure a VPC ACL.
The domain name of the Enterprise Edition instance. The domain name is accessed by APIs to pull and push images.
The domain name of the authentication service. The domain name is accessed when the system performs identity authentication.
The domain name of the Object Storage Service (OSS) bucket. The OSS bucket is used to store the images on the Enterprise Edition instance.
Configure a route table: Add the IP addresses or CIDR blocks to the route table to ensure that the access source can access the Enterprise Edition instance across regions.
Test access to the Enterprise Edition instance in the China (Hangzhou) region from the access source in the China (Shanghai) region.
Step 1: Create an inter-region connection
Use CEN to connect VPC2 of the access source in the China (Shanghai) region to VPC1 of the Enterprise Edition instance in the China (Hangzhou) region. For more information, see Connect VPCs in different regions.
Step 2: Obtain domain name information
Make sure that the IP addresses of the following domain names do not conflict with the IP addresses of the existing services in the access source. Otherwise, the services in the access source cannot be accessed.
Log on to ECS Instance 1 in the China (Hangzhou) region and perform the following operations to obtain the IP addresses of the OSS bucket, the Enterprise Edition instance, and the authentication service in the VPC:
Obtain the IP address of the Enterprise Edition instance in the VPC.
Log on to the Container Registry console.
In the top navigation bar, select a region.
In the left-side navigation pane, click Instances.
On the Instances page, click the Enterprise Edition instance that you want to manage.
In the left-side navigation pane of the management page of the Enterprise Edition instance, choose .
On the VPC tab, copy the domain name of the Enterprise Edition instance in the VPC. Then, run the
pingcommand on ECS Instance 1 to access the domain name of the Enterprise Edition instance. Obtain and record the IP address of the Enterprise Edition instance.
Obtain the IP address of the authentication service in the VPC.
NoteIf you enable the feature that allows the Enterprise Edition instance to take over the authentication domain name, you can skip this step. For information about how to enable the feature, see Conflict with the CIDR block that is mapped to the domain name of the authentication service.
Run the following command to obtain the domain name of the authentication service in the VPC. In the command, replace
InstanceNamewith the name of the Enterprise Edition instance andRegionIdwith the region ID of the Enterprise Edition instance.curl -vv https://${InstanceName}-registry-vpc.${RegionId}.cr.aliyuncs.com/v2/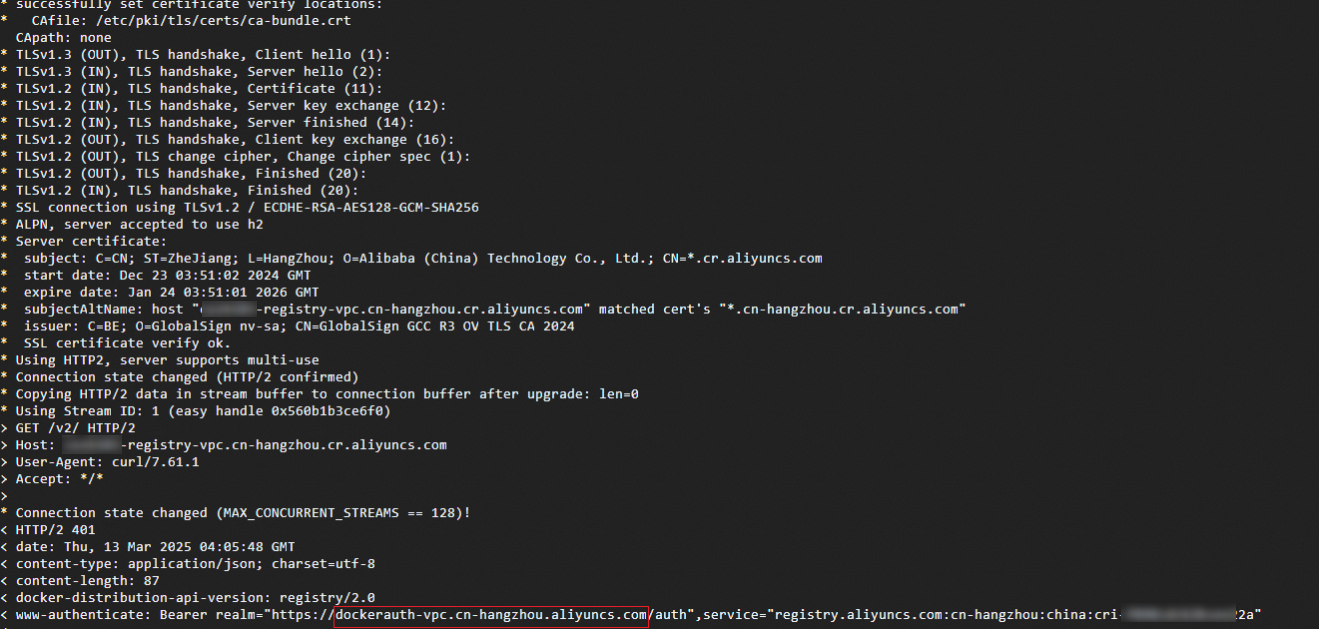
Run the
pingcommand to obtain the IP address of the authentication service and record the IP address.ping dockerauth-vpc.cn-hangzhou.aliyuncs.com
Obtain the IP address of the OSS bucket in the VPC.
NoteIf you use PrivateLink to access the OSS bucket and add a CNAME record to point the domain name of the OSS bucket to the domain name of the PrivateLink connection, you can skip this step. For more information, see Access OSS by using PrivateLink.
Run the
pingcommand to obtain the IP address of the OSS bucket and record the IP address.Obtain the domain name of the OSS bucket in a VPC of the China (Hangzhou) region from the table in Internal OSS endpoints and VIP ranges in the public cloud.
Run the ping command to obtain the IP address of the OSS bucket and record the IP address.
ping oss-cn-hangzhou-internal.aliyuncs.com
NoteIf you use a custom OSS bucket, the domain name of the OSS bucket is
${CustomizedOSSBucket}.oss-${RegionId}-internal.aliyuncs.com.
The following table provides sample IP addresses of the domain names that are related to the Enterprise Edition instance in the China (Hangzhou) region:
Item
Domain name
IP address
Enterprise Edition instance
xxxxxx-registry-vpc.cn-hangzhou.cr.aliyuncs.com
10.94.205.198
Authentication service
dockerauth-vpc.cn-hangzhou.aliyuncs.com
100.103.7.181/32
OSS Bucket
oss-cn-hangzhou-internal.aliyuncs.com
100.118.28.43/32
Step 3: Configure a route table
In VPC 2 of the China (Shanghai) region, perform the following operations to use the IP addresses of the authentication service and the OSS bucket to configure the route table:
Log on to the VPC console.
In the left-side navigation pane, click Route Tables.
On the Route Tables page, find the custom route table that you want to manage and click its ID.
On the details page of the custom route table, choose and click Add Route Entry.
In the Add Route Entry panel, configure the route entry based on the following parameters and click OK.
Parameter
Description
Screenshot
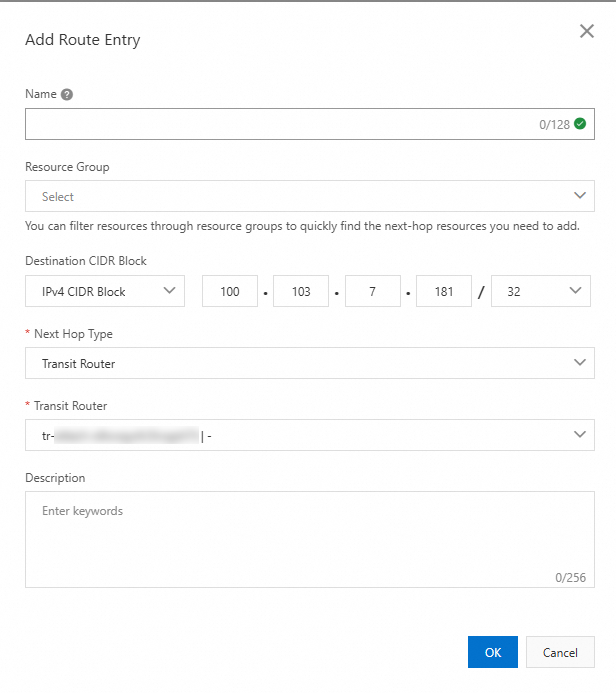
Destination CIDR Block
Enter the destination CIDR blocks.
Select IPv4 CIDR Block and then enter 100.103.7.181/32 and 100.118.28.43/32. Separately configure the IP addresses.
Next Hop Type
Select the type of the next hop.
Select Transit Router. Traffic destined for the destination CIDR block is routed to the specified transit router. For more information about transit routers, see How transit routers work.
Then, select the transit router that you created in Step 1: Create an inter-region connection.
Add a route entry of 100.0.0.0/8 which covers the IP addresses of the authentication service and the OSS bucket to the route table of the CEN route router in the China (Shanghai) region.
Log on to the CEN console.
On the Instances page, click the ID of the CEN instance that you want to manage.
On the tab, find the transit router in the China (Shanghai) region and click its ID.
On the details page of the transit router, click the Route Table tab.
In the left-side section, click the route table ID. On the Route Entry tab of the details page of the route table, click Add Route Entry.
In the Add Route Entry dialog box, configure the parameters and click OK. The following table describes the parameters.
Parameter
Description
Screenshot
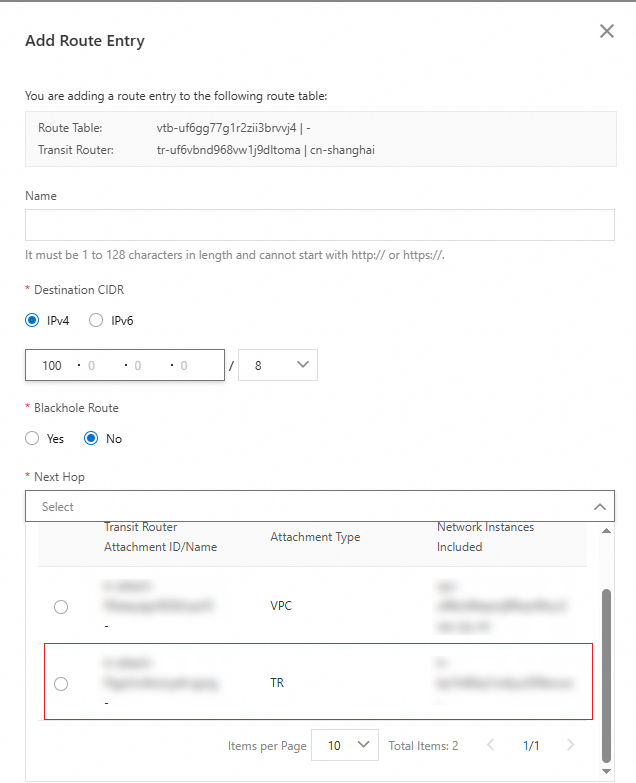
Destination CIDR
Enter a destination CIDR block for the route.
Select IPv4 and then enter 100.0.0.0/8. This CIDR block covers the IP addresses of the authentication service and the OSS bucket.
Blackhole Route
Specify whether the route is a blackhole route.
Select No.
Next Hop
Next Hop
Set Attachment Type to TR and then select the ID of the transit router that you created in Step 1: Create an inter-region connection.
Add a route entry of 100.0.0.0/8 which covers the IP addresses of the authentication service and the OSS bucket to the route table of the CEN route router in the China (Hangzhou) region.
On the tab, find the transit router in the China (Hangzhou) region and click its ID.
On the details page of the transit router, click the Route Table tab.
In the left-side section, click the route table ID. On the Route Entry tab of the details page of the route table, click Add Route Entry.
In the Add Route Entry dialog box, configure the parameters and click OK. The following table describes the parameters.
Parameter
Description
Screenshot
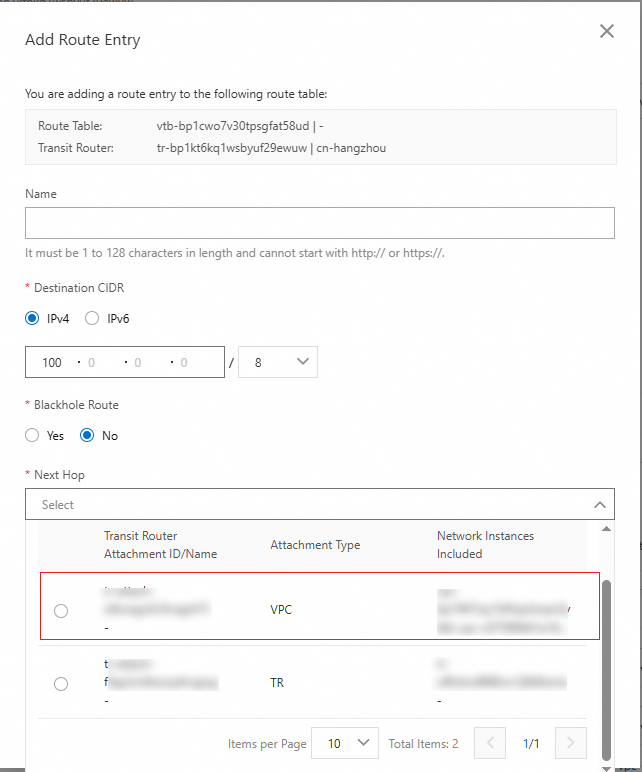
Destination CIDR
Enter a destination CIDR block for the route.
Select IPv4 and then enter 100.0.0.0/8. This CIDR block covers the IP addresses of the authentication service and the OSS bucket.
Blackhole Route
Specify whether the route is a blackhole route.
Select No.
Next Hop
Next Hop
Set Attachment Type to VPC and then select the ID of VPC1 in the China (Hangzhou) region.
Step 4: Test access to the Enterprise Edition instance
Log on to ECS Instance 2 in the China (Shanghai) region. Run the
pingcommand on ECS Instance 2 to test access to the three IP addresses of the Enterprise Edition instance, the authentication service, and the OSS bucket in the China (Hangzhou) region that you obtained in Step 2. Use the three domain names that are related to the Enterprise Edition instance to configure local DNS resolution on ECS Instance 2 and check whether the domain names are resolved to the IP addresses that are related to the Enterprise Edition instance.vim /etc/hosts 10.94.205.198 xxxxxx-registry-vpc.cn-hangzhou.cr.aliyuncs.com 100.103.7.181 dockerauth-vpc.cn-hangzhou.aliyuncs.com 100.118.28.43 ${OSSBucketName}.oss-cn-hangzhou-internal.aliyuncs.comRun the
docker logincommand to log on to an image repository on the Enterprise Edition instance and then run thedocker pullcommand to pull an image from the image repository.NoteFor more information about how to push and pull images, see Use a Container Registry Enterprise Edition instance to push and pull images.
Solutions to 100 CIDR block conflicts
When you configure the routing rule, the domain names of the authentication service and the OSS bucket are mapped to IP addresses that belong to the 100 CIDR block. If the 100 CIDR block is assigned to a VPC in which the Enterprise Edition instance resides, domain name conflicts may occur when you access the Enterprise Edition instance. To prevent the conflicts from occurring, you can use the following solutions:
Conflict with the CIDR block that is mapped to the domain name of the authentication service
You can enable the feature that allows an Enterprise Edition instance to take over the domain name of the authentication service and only need to access the domain name of the Enterprise Edition instance. This solves the conflict with the CIDR block that is mapped to the domain name of the authentication service.
Log on to the Container Registry console.
In the top navigation bar, select a region.
On the Instances page, click the Enterprise Edition instance that you want to manage.
In the left-side navigation pane of the management page of the Enterprise Edition instance, choose . On the Domain page, turn on Instance Taking over Authentication Domain Name.
ImportantIf you want to use the feature that allows the Enterprise Edition instance to take over the authentication domain name, submit a ticket to request to add the Enterprise Edition instance to the whitelist.
In the Confirm to Enable Instance Taking over Authentication Domain Name message, click OK.
Conflict with the CIDR block that is mapped to the domain name of the OSS bucket
To prevent the conflict with the CIDR block that is mapped to the domain name of the OSS bucket from occurring, you can use PrivateLink to access the OSS bucket and add a CNAME record to point the domain name of the OSS bucket to the domain name of the PrivateLink connection. For more information, see Access OSS by using PrivateLink.