By Alexandru Andrei, Alibaba Cloud Community Blog author.
If you look up on the Internet "how to connect to a Linux server from Windows," you will almost always find a tutorial that revolves around installing and using PuTTY. It's not the only SSH client compatible with Microsoft's operating system, but it has been so popular, that pretty much everyone was recommending it. It's certainly a good utility, but nowadays, there's a much simpler solution available, readily available in any modern Windows edition. And since it's relatively new, you won't find it mentioned in most tutorials.
In 2018 Microsoft has added the OpenSSH client into Windows 10. It has been available for some time before that, but as an optional install. Nowadays, it's preinstalled on any (non-pirated) Windows 10 system that is up-to-date. So, instead of having to download PuTTY, install it, configure it, you can now just open Command Prompt and connect to your Linux server with a simple command such as
ssh root@203.0.113.5
Compare this to all the extra steps you have to go through, when using the "old way" of connecting with PuTTY.
We could actually end the tutorial here, as that is all you have to do to connect to any existing Alibaba Cloud ECS instances. However, you may notice that this article is relatively long, which might create the illusion that this process is complicated. That's because the instructions here aim to be a complete guide, from start to finish, covering the following steps:
Not that passwords logins themselves are insecure, but they are more susceptible to being used wrong (weak passwords), something that scanning bots (software robots) on the Internet continuously try to exploit. Most servers usually get compromised (hacked) because of this reason, for example a root account has the password "trustno1" and a bot tries to log in with this passphrase, succeeds and then automatically sets up malicious software on the machine to add it to a botnet. True story: at a workplace, the business owner bought and configured a new server and set up a weak password for the root account. Just a few hours later he laughed as he noticed that the server was already compromised and the attacker set up a game server and there were already players that joined the game.
If you already have a server and only intend to use password-based logins, you can skip to the section titled "How to Log In to Linux Servers from Windows", near the end of this article. That is the core of the guide and will take you less than two minutes to follow if you don't have time to go through all of the steps here, to enable key-based logins.
If you are reading this, congratulations! It seems you are interested in going that extra mile to keep your servers safe. SSH logins are the main doors to your ECS instances and the better you lock them, the better it is for the overall security of your infrastructure.
But if it's the first time you hear about public and private keys, you may be confused. How do you log in with a private key on a server that has your public key? Why do you have to add the public key to it?
Don't worry though, you don't have to understand the math behind how they work, or all that they can do (encrypt messages, sign them, verify signatures, decrypt, etc.). You only have to understand how they allow you to log in, since that's the only part you'll visibly use here. And you only have to go through these steps once. After you set up your keys, Alibaba Cloud lets you launch all future ECS instances, secured with the public key, with just a few clicks, taking no more than a few seconds to set up the login mechanism.
With a utility preinstalled on your Windows 10 computer, you can generate a public and private key pair. These are mathematically linked in such a way that messages encrypted with the public key can only be decrypted with your private key. What is "locked" with the public key can be "unlocked" only with the private key. You might wonder, "But if the public key locked that message, can't it also unlock it?" And the answer is "No," oddly enough. Encryption is done in such a way, that it cannot be reversed with the same key, it can only be reversed by its counterpart. Think of it as a sort of destructive action: you can take an orange and turn it into juice, with pulp, but you can't take the juice and turn it back into an orange. Although, in this case, with your unique, magic key, you can indeed turn juice back into the same original orange. In a sense, you then say to the server "Is this the orange that you crushed?" The server takes a look at it and says "Indeed, this is the exact same orange! It means that you must have the right key to know this."
Hopefully this is easier to understand than saying that the server generates a random code, encrypts it, sends it to you, you decrypt it, send it back to the server and if it's the same code, you passed the challenge-response phase.
Of course, all of these examples are over-simplifications and approximations of the process, to keep things simple and easier to understand, otherwise, we would have to write a short book here. The core concept to take home is that this is how you can prove to any server that has your public key, that you indeed have the corresponding private key. You can also sign messages with the private key, that can be verified only with the corresponding public key, but we won't get into that as it's not useful in this scenario. You can read more about asymmetric cryptography, here, if you are interested. Even that article just barely scratches the surface of how all of this works.
As the name suggests, the public key can be shared with the entire world, without compromising your security. In this case, it won't be shared with the whole world, just saved to your server(s). Used this way, you can log in through SSH with the corresponding private key. Here, you can see another advantage of using SSH keys instead of passwords. Presume you have one or more teammates that need to access this same server (and same user, say "root"). Instead of sharing your password, they can each generate their own private keys, give you their public keys, you add them to the server and they can each log in with their own credential (private key) instead of using the same secret (some password).
To generate SSH keys on Windows, first open up Command Prompt. Click on the Start Menu and type "cmd" or "command" then launch the Command Prompt utility.
Here, type the command
ssh-keygen
At the first prompt
Enter file in which to save the key (C:\Users\your_user/.ssh/id_rsa):
Press ENTER to save the private key in its default location.
The next line of text will prompt you to choose a password.
Enter passphrase (empty for no passphrase):
This is an optional security measure that allows you to encrypt the private key with a password. Such a thing is useful in scenarios like:
If you don't want to use a password, simply press ENTER without entering anything beforehand then do the same at the next prompt:
Enter same passphrase again:
Obviously, if you want to use a password type it at the first prompt and press ENTER then type it again at the second prompt and press ENTER.
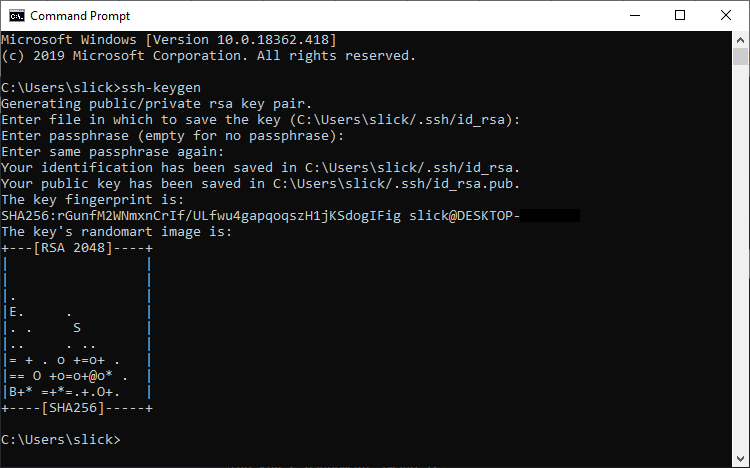
When you log in to servers with this private key, if you encrypted it, you will be required to enter the password each time, which makes it seem like you send the password to the server itself. But it's not what happens. The password is used to decrypt the private key, locally (on your computer), and then temporarily copy it to memory where it is used to perform the necessary cryptographic operations to prove to the server that you are authorized to log in.
At this point the job is done and the private and public keys are saved in your user's directory in a folder called .ssh. The private key is saved in the file "id_rsa" and the public key in "id_rsa.pub" which you will need to add to a file on your Linux (or BSD) server (Alibaba Cloud can do this for you, through its web interface).
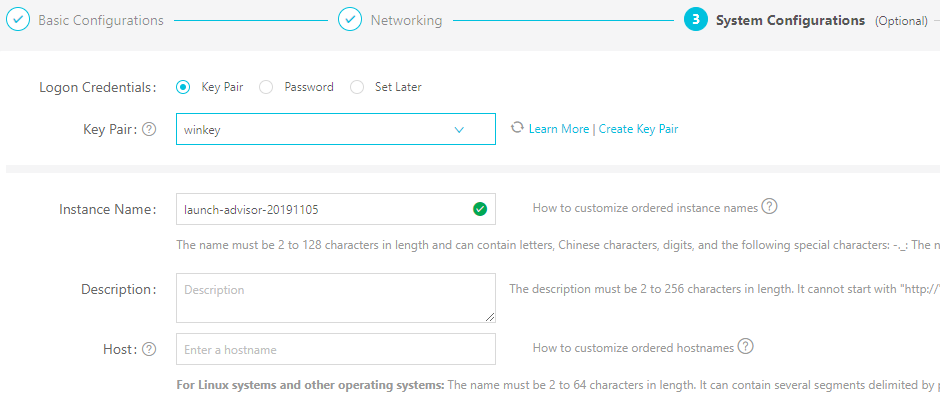
Normally, you would have to create a file on your server, set appropriate permissions and then add the key there, after which you may also have to change SSH daemon configuration and restart it. You can see the procedure in this article, at Step 5 - Creating Authentication Key Pair for Logging onto Your Ubuntu 16.04 Server and Step 6. However, it would be tedious to have to do this every time you launch a server. And it would also mean that you would initially have to use password logins and then disable them entirely. Alibaba Cloud lets you avoid all this by adding your public key to your account. Afterward, when you create a server, in the third configuring step (System Configurations), you can select the logon credential type you want to use on the server and pick your previously saved public key. Alibaba Cloud will then automatically configure the server to use SSH key logins exclusively (passwords disabled) and your public key will be added to the respective file. Here is an example of how this configuration step will look like:
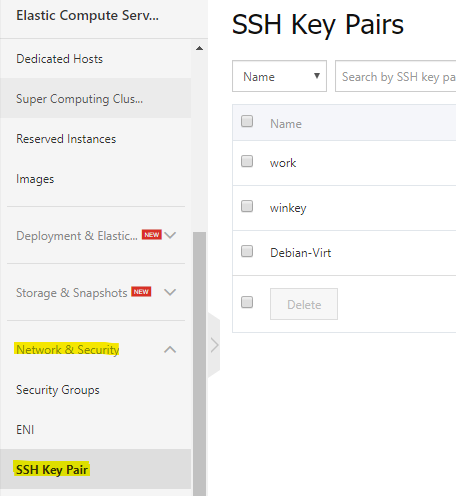
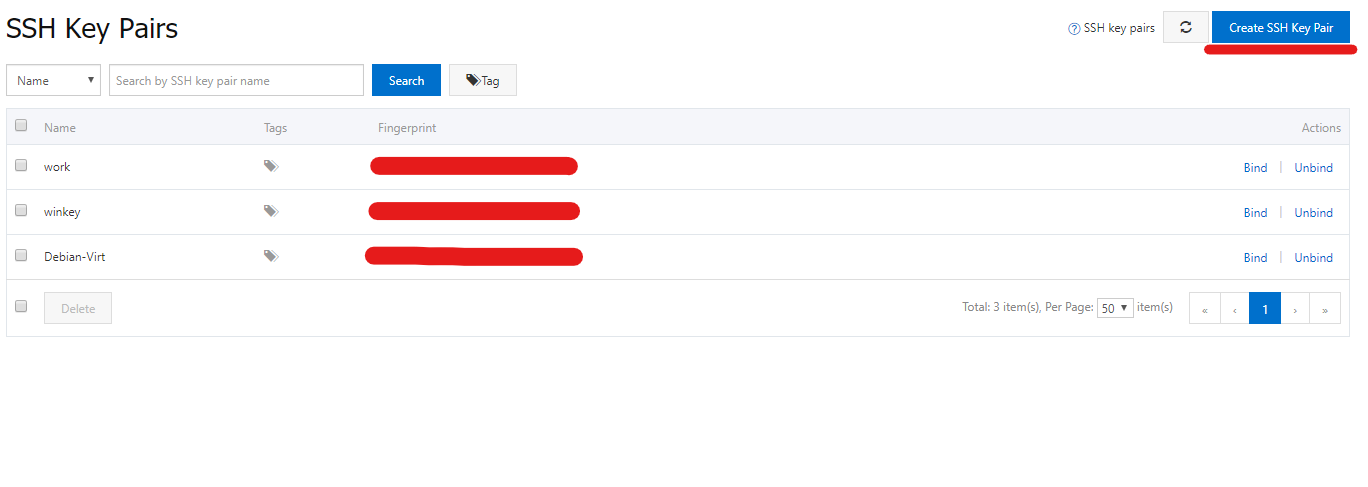
To add your public key to your Alibaba account, first log in to your ECS console and then in the left-side menu look for Network & Security and under it (after you expand menu) click on SSH Key Pair.
Here, click on the button titled Create SSH Key Pair (located in the top-right corner, at the time of writing this article; interface may change in the future).
Next, under Creation Type, click on the Import SSH Key Pair radio button. This will open up the Public Key field where you have to paste the key you previously generated on your Windows computer.
Go back to the Command Prompt window on your computer or reopen it if you closed it. Here, paste this command:
notepad %userprofile%\.ssh\id_rsa.pub
This will open up the public key contents in the Notepad application. Select all the text in Notepad (with the mouse or by pressing CTRL+A). Next, right-click on the selected text and choose Copy. Afterwards, go back to the Alibaba Cloud interface, and paste the key contents in the Public Key field. The final result should look similar to the following picture.
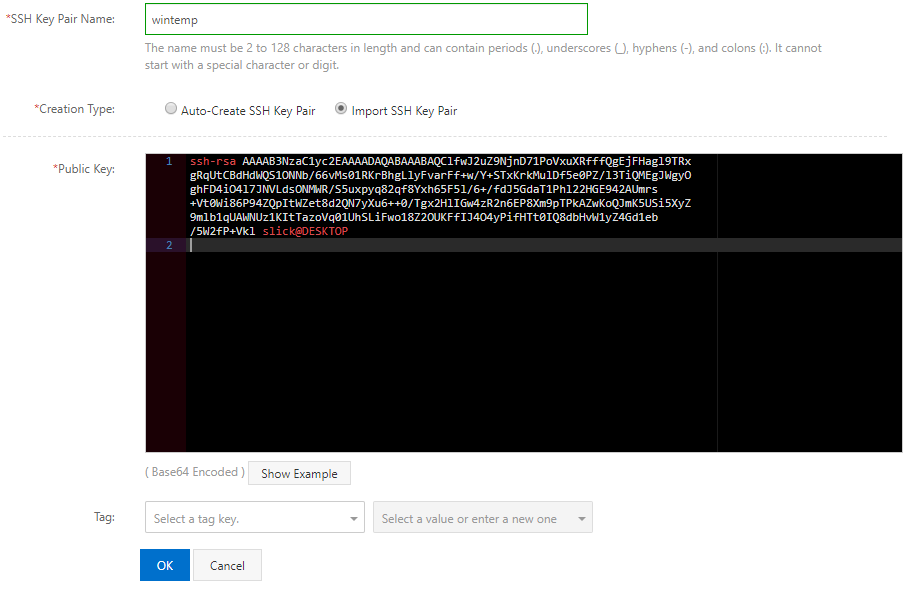
Choose a name for this entry in the first field, SSH Key Pair Name. Just use something to easily remember later on, for example "work-laptop".
Click the OK button and you're done with this step.
If you already have a server that is running and you want to associate this key with it, in the SSH Key Pairs web page, you can click on the Bind link, next to your preferred entry. You will then be able to easily log in with your private key.
Although the previous steps were optional, congratulations if you followed them! You eliminated the possibility of having your ECS instance compromised because of a weak password. And now, you got to the easiest part.
After you create your servers and optionally associate the public key with them (or bind the key to previously existing servers), all you have to do to log in to these is follow these three steps:
ssh root@IP_OF_YOUR_SERVER
Of course, you replace "IP_OF_YOUR_SERVER" with the actual IP you previously copied. For example, the command with an actual IP address might look like this:
ssh root@203.0.113.5
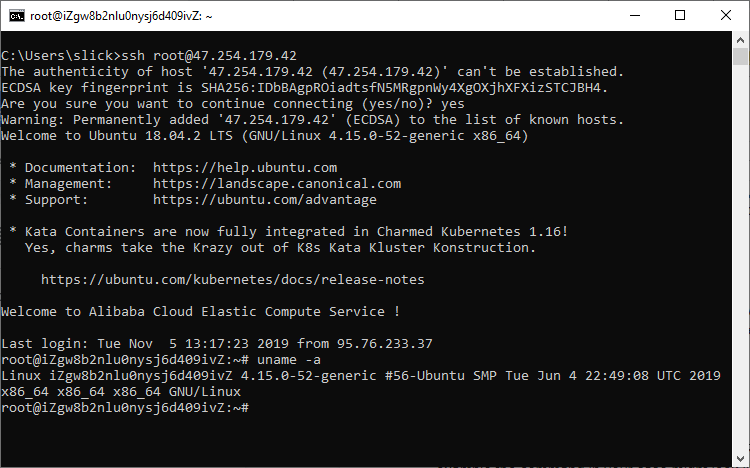
The first time you log in to a server, you get a prompt where its fingerprint is displayed. You have a choice to type "yes" to trust this server and add its fingerprint to a list. Consequently, as long as the fingerprint is found in that list in the future, you won't be asked the question again, when you log in to it, from the same machine.
Type yes and press ENTER.
The command prompt will change to "root@your_server_hostname", indicating that you are logged in and currently entering commands on your server.
If your server uses password-based logins instead of keys, or your private key is encrypted with a password, you will also be prompted to type this password. As you type it, you will notice that no text is being output (not even the usual ****** you see when you log in to other sites/applications). That's normal and your key input is being recorded, just not displayed.
The only drawback of logging in with Windows' built-in SSH tool instead of PuTTY is that PuTTY saved connections and you could then easily launch them from a menu, without having to fetch the IP of the server again. You can do the same Windows' utility though.
Open Notepad. Here, type the command you used to log in to your server, for example
ssh root@203.0.113.5
Save the file to your Desktop and make sure to end its name in .bat. For example, you might name it My Alibaba Database Server.bat
Now, when you double click on it, you will automatically initiate an SSH connection to your server.
Furthermore, if you have a domain name and configure DNS entries to point to your instance, you can log in without using IP addresses, and instead using your domain name. For example:
ssh root@example.com
where example.com points to your instance's public IP address.
Since the utility included in Windows is the OpenSSH client that Linux users have had on their computers, out-of-the-box, for years, most of the instructions you will find in this help manual for the SSH client included in Debian apply to Microsoft's utility too.
For example, a command line switch like -p allows you to instruct your client to connect to a different port than the default 22, if your server has the OpenSSH daemon listening on a different port. Just add the necessary command line switches before the "user@IP_Address" part. Example:
ssh -p 1234 root@203.0.113.5
to connect to port 1234.
You can combine multiple switches. For example, you can add -v to display more status messages, helping you debug certain problems and also connect to a different port:
ssh -v -p 1234 root@203.0.113.5
Specifying -v multiple times (maximum is 3) shows you even more debug messages.
ssh -v -v -v -p 1234 root@203.0.113.5
But this can also be typed as
ssh -vvv -p 1234 root@203.0.113.5
We hope you find Windows' version of the OpenSSH utility as useful as Linux users found their also included-by-default OpenSSH client for years; it's basically (almost) the same one.
How to Manage Files Visually on Linux with Midnight Commander

2,593 posts | 793 followers
FollowAlibaba Clouder - April 16, 2018
Alibaba Clouder - February 20, 2020
Alibaba Clouder - June 18, 2019
Alibaba Clouder - September 29, 2018
Alex - June 21, 2019
Alibaba Clouder - June 13, 2019

2,593 posts | 793 followers
Follow ECS(Elastic Compute Service)
ECS(Elastic Compute Service)
Elastic and secure virtual cloud servers to cater all your cloud hosting needs.
Learn More OSS(Object Storage Service)
OSS(Object Storage Service)
An encrypted and secure cloud storage service which stores, processes and accesses massive amounts of data from anywhere in the world
Learn MoreMore Posts by Alibaba Clouder