By Chenglong Zhang
BabaSSL is an open-source cryptographic library product. As one of the core components of the Anolis commercial cryptography OS, it is open-source on GitHub. Also,it has been added to the SIG group of the commercial cryptographic software stack of OpenAnolis.
With the construction of the 5G network, the development of mobile Internet applications has been accelerated, including short videos, online education, the Internet of Things, and other fields. However, there are still scenes of poor network signals, including underground shopping malls, garages, subways, and other places. In weak network environments caused by network congestion, applications are slowly loaded during use, resulting in poor user experiences. At this time, it is necessary to optimize the weak network environment. One of the means is to find ways to reduce network data transmission.
TLS/SSL is usually used for cryptotransmission to ensure data security. When a client accesses the server in the background, the client performs a TLS handshake with the server first. During the TLS handshake, the server sends a certificate chain for identity authentication, and most of the data transferred during the handshake comes from the certificate.
Is there any way to reduce the bandwidth consumption of TLS handshake? If the certificate can be compressed or even disappear, the data transmission can be reduced. RFC 8879 TLS Certificate Compression aims to solve this problem and provide certificate compression during TLS 1.3 handshake.
BabaSSL is an open-source cryptographic library product. It was open-source on GitHub and added to OpenAnolis. It is based on OpenSSL 1.1 and maintains compatibility. Based on OpenSSL, it implements a series of autonomous and controllable security features, including various Chinese cryptographic algorithms, Chinese cryptographic standards, and a large number of features to improve key security.
BabaSSL supports TLS certificate compression, but OpenSSL does not.
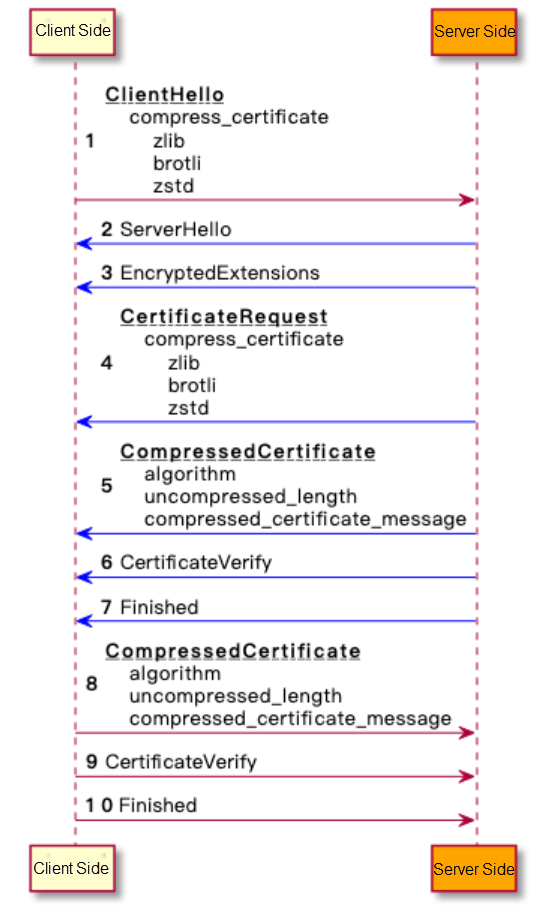
The processing procedure for the server to send a CertificateRequest message and the client to send a CompressedCertificate message is similar to the preceding one.
The compression algorithm defined in the standard:
| Algorithm | Value | Reference Standard |
| zlib | 1 | RFC1950 |
| brotli | 2 | RFC7932 |
| zstd | 3 | RFC8478 |
In addition to the three algorithms defined in RFC, users can use other algorithms, with values 16384 to 65535 for their use.
The open-source BabaSSL cryptographic library supports the TLS certificate compression. You need to enable this feature when building BabaSSL and add enable-cert-compression after configuration.
You can add a certificate compression algorithm when you set SSL_CTX. The following is the example code:
#include <openssl/ssl.h>
#include <zlib.h>
static int zlib_compress(SSL *s,
const unsigned char *in, size_t inlen,
unsigned char *out, size_t *outlen)
{
if (out == NULL) {
*outlen = compressBound(inlen);
return 1;
}
if (compress2(out, outlen, in, inlen, Z_DEFAULT_COMPRESSION) != Z_OK)
return 0;
return 1;
}
static int zlib_decompress(SSL *s,
const unsigned char *in, size_t inlen,
unsigned char *out, size_t outlen)
{
size_t len = outlen;
if (uncompress(out, &len, in, inlen) != Z_OK)
return 0;
if (len != outlen)
return 0;
return 1;
}
int main() {
const SSL_METHOD *meth = TLS_client_method();
SSL_CTX *ctx = SSL_CTX_new(meth);
/* Configure the certificate and private key... */
/* For example, set the compression algorithm to zlib */
SSL_CTX_add_cert_compression_alg(ctx, TLSEXT_cert_compression_zlib,
zlib_compress, zlib_decompress);
SSL *con = SSL_new(ctx);
/* Handshake... */
return 0;
}You can also use the s_client and s_server provided by BabaSSL to use the TLS certificate compression feature:
# Server
/opt/babassl/bin/openssl s_server -accept 127.0.0.1:34567 -cert server.crt -key server.key -tls1_3 -cert_comp zlib -www -quiet
# Client
/opt/babassl/bin/openssl s_client -connect 127.0.0.1:34567 -tls1_3 -cert_comp zlib -ign_eof -traceThe server configures the certificate chain, such as CA certificate + intermediate CA + domain name certificate. TLS 1.3 handshake enables certificate compression. Comparing the compression rates of each compression algorithm, the following chart shows the results:
| Compression Algorithm | Before Compression (Byte) | After Compression (Byte) | Compression Rate | Remarks |
| zlib | 2666 | 1959 | 73.48% | Use default compression level 6 |
| brotli | 2666 | 1889 | 70.86% | Use default compression level 11 |
| zstd | 2666 | 1951 | 73.18% | Use default compression level 3 |
| zstd + dictionary | 2666 | 18 | 0.68% | Dictionary based on Certificate messages |
Some compression algorithms support setting dictionaries, such as brotli and zstd. The dictionary content can be calculated in advance, embedded in the client and server, and used when compressing and decompressing, so the certificate chain can disappear. For example, when the zstd + dictionary is used in the preceding table, the Certificate message of 2666 bytes before compression becomes 18 bytes after compression.
If the certificate compression feature is enabled, the transfer during handshake can be reduced, especially when using dictionaries, such as zstd + dictionaries.
Disable certificate compression, handshake co-transmission: 3331 bytes
Open certificate compression: handshake co-transmission: 698 bytes
Compression Rate: 698/3331 * 100% = 20.95%. The handshake bandwidth is reduced by nearly 80%.
The certificate is not needed when a TLS session is reused, so certificate compression can optimize the complete handshake.
Client authentication is enabled on the server in the scenario of mutual authentication. If the client and server enable the TLS certificate compression, the compression effect is clear, which can save more than 80% bandwidth in the TLS handshake. BabaSSL will support Compact TLS, the pocket version of TLS 1.3, which occupies the minimum bandwidth while maintaining the protocol isomorphism. You are welcome to use BabaSSL.
BabaSSL website: https://github.com/BabaSSL/BabaSSL
Chenglong Zhang is a technical expert of Ant Group, one of the core developers of BabaSSL project, a contributer to multiple open source projects, including OpenSSL, Tengine, etc. And he is also one of the members of SIG of the ShangMi cryptographic software stack of OpenAnolis.
Cloud Application Performance Diagnosis of System O&M Tool SysAK

85 posts | 5 followers
FollowWilliam Pan - February 6, 2020
William Pan - February 6, 2020
Alibaba Cloud Native - November 9, 2022
Alibaba Container Service - July 28, 2021
Alibaba Clouder - August 27, 2020
Alibaba Cloud Community - December 2, 2024

85 posts | 5 followers
Follow Accelerated Global Networking Solution for Distance Learning
Accelerated Global Networking Solution for Distance Learning
Alibaba Cloud offers an accelerated global networking solution that makes distance learning just the same as in-class teaching.
Learn More Networking Overview
Networking Overview
Connect your business globally with our stable network anytime anywhere.
Learn More Content Delivery Solution
Content Delivery Solution
Save egress traffic cost. Eliminate all complexity in managing storage cost.
Learn More Managed Service for Prometheus
Managed Service for Prometheus
Multi-source metrics are aggregated to monitor the status of your business and services in real time.
Learn MoreMore Posts by OpenAnolis