This plan is for Alibaba Cloud's international website users. It provides guidance on effectively integrating multiple products for operational maintenance (O&M) and detection. This article will focus on the detection phase, detailing product configurations, FAQs, and providing a brief overview of the theoretical framework. This will help users understand the role of detection in O&M tasks and establish a comprehensive concept.
Organizations are increasingly prioritizing information security management. Common models such as the PDRR model and the Community Gold Standard v2.0 measure security defense systems across four dimensions: protection, detection, recovery, and response. Today, we will focus on detection.
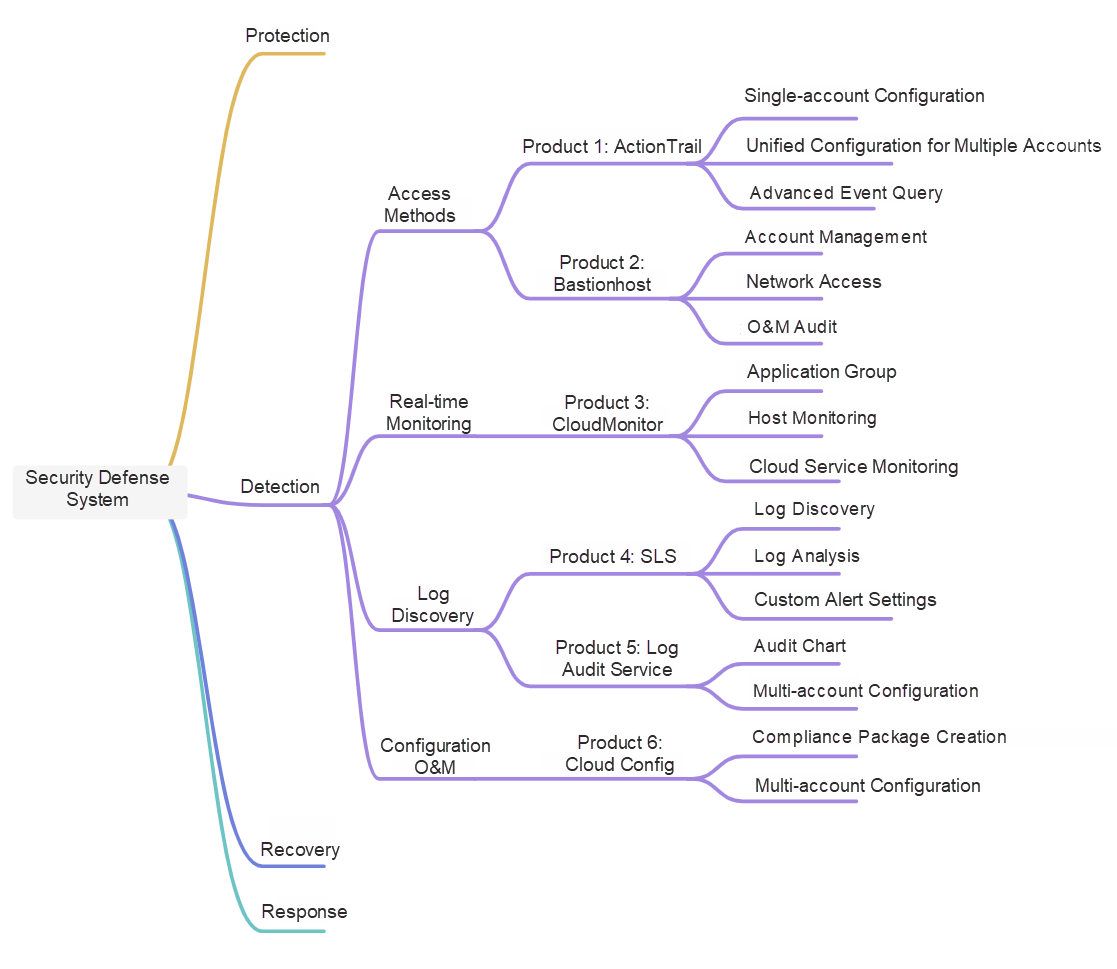
Here is my understanding of these dimensions: Detection offers greater universality and applicability, while protection, recovery, and response are closely tied to the specifics of the business system and require case-by-case analysis. This O&M plan focuses on detection. Let's dive into the details. The diagram below outlines the main products and content involved in this plan.
Protection is the first line of defense in security. It involves deploying measures to secure the system while ensuring high efficiency and availability of IT resources within the business strategy.
Customer Responsibilities:
Customers must pay special attention to three key areas related to their application systems during development and improvement. While we can help identify and address gaps, the primary responsibility lies with the customer.
• Application security: Customers must comply with laws and regulations during application development, follow industry and company standards, minimize the attack surface, fix vulnerabilities, and fully implement the Security Development Lifecycle (SDLC).
• Data security: Customers must ensure security throughout the data lifecycle, including collection, transmission, storage, processing, exchange, and destruction, in compliance with relevant data security laws. Security measures must be taken for data management, data technology, and privacy statements.
• Business security: This relies heavily on the business logic of customers. Customers must establish a robust risk control system, conduct dynamic (real-time) and static (functional flow) analysis of the business logic to prevent risks such as promotion abuse, and test the availability of their business processes.
Protection Provided by Alibaba Cloud:
We rely on security services to provide thorough and precise protection for customers.
• Application security: Services include Security Center, Cloud Firewall, Web Application Firewall (WAF), and Anti-DDoS.
• Data security: Services include Data Security Center (DSC), DBAudit, Data Encryption Service, and Key Management Service (KMS).
• Business security: Services include Content Moderation and Fraud Detection.
Many companies now recognize and use the cloud as the foundation of their IT infrastructure. Unlike traditional, physically isolated data centers, cloud data centers require companies to promptly detect issues and notify relevant personnel when problems arise. Alibaba Cloud offers not only high-performance IaaS services but also excellent PaaS and SaaS services to help companies detect and store relevant logs and traces from various sources.
Customer Responsibilities:
• Effective monitoring and alerting: Ensure that the status of the application system is effectively monitored. Anomalies must be detected immediately so that issues can be resolved promptly.
• Complete logs and traces: Maintain complete logs and traces of all operations. This is essential for troubleshooting, root cause analysis, and deterring malicious actions.
• Proactive detection: Use best practices in cloud configuration to identify areas needing improvement. Services or personnel must be in place to highlight deficiencies and suggest enhancements. (Note: This section focuses on public cloud configuration detection. Intrusion detection, such as vulnerability scans and penetration tests, will be discussed in the response section, as they are closely related to application systems and require developer involvement.)
Services Provided by Alibaba Cloud:
• Effective monitoring and alerting: CloudMonitor, Application Real-Time Monitoring Service (ARMS), Simple Log Service, Log Audit Service, Cloud Config, and ActionTrail.
• Complete logs and traces: ActionTrail, Bastionhost, Simple Log Service, and Log Audit Service
• Proactive detection: Cloud Config
You might wonder why some services, such as Cloud Config, appear multiple times. The reason will be detailed later. Here is a brief explanation: Different services focus on different areas, which is why their observations vary. Let me illustrate this with a few examples:
CloudMonitor focuses on runtime status, monitoring whether services are up or down.
Simple Log Service focuses on the content of collected logs, such as detecting unauthorized logons. It works only when there are logs. For instance, if an action has no logs, such as a sudden spike in CPU usage without any error logs, Simple Log Service will not detect the action, but CloudMonitor will.
Cloud Config focuses on changes in cloud configurations, checking for deviations from security best practices and alerting customers. For example, if you change a configuration but the system remains operational, CloudMonitor will not notice it, but Cloud Config will.
Therefore, we need a comprehensive, multi-dimensional monitoring and detection system to cover all aspects effectively.
Recovery focuses on data backup, data recovery, and system restoration. The primary goal is to get the system back to normal so that business operations can continue. (Remember, business value always comes first. Engineers must not delay business recovery for the sake of debugging or problem reproduction.)
No system is immune to issues. Therefore, it is essential to build a highly available architecture to ensure business continuity and have data backups for quick system restoration. Here is my understanding: High availability and disaster recovery are distinct concepts. High availability relies on the system's own capabilities, such as multi-node setups and load balancing, to maintain stability even if some components fail.
Disaster recovery involves a separate environment designed for geographical redundancy to handle unforeseen events such as power outages, tsunamis, or earthquakes. For traditional data centers, this was often referred to as geo-disaster recovery. This approach offers high system stability but is also very costly.
Customer Responsibilities:
• Application high availability: This is a key consideration during development. If you do not address it during this phase, making improvements later can be very difficult and limited.
• Effectiveness of data backups: Regular backups are crucial for core systems. Ensure you have at least one off-site backup and verify its effectiveness monthly. This guarantees that the system can be recovered when issues occur during system upgrades or failures.
• Disaster recovery redundancy: Disaster recovery is essential for critical applications. While geo-disaster recovery for traditional data centers is costly, the cloud era offers better options with various regions, availability zones, and integrated services. This significantly improves availability. (Note: In Japan, disaster recovery drills involve shutting down the primary data center every six months, switching operations to a secondary data center over a weekend, and then switching operations back to the primary data center. This operation is quite difficult, but ensures high system stability.)
How Alibaba Cloud Can Help:
Alibaba Cloud provides more than just services. We offer foundational building blocks for creating your ideal solution, which is more convenient than traditional data centers. You can use Alibaba Cloud services to achieve your goals.
• Application high availability: multi-zone, load balancing, and multi-node databases, such as PolarDB
• Data validity: snapshot service, object storage, network attached storage, and hybrid cloud storage
• Disaster recovery redundancy: multi-region redundancy, CEN, and Data Transmission Service (DTS)
This section focuses on intrusion analysis, security assessments, and emergency response strategies. When an issue, whether a software bug or an attack, occurs, we must identify the root cause, and have mechanisms in place to prevent the recurrence of such issues.
Customer Responsibilities:
• Problem detection solutions: No system is perfect, especially in today's fast-paced tech environment. Most systems undergo professional vulnerability scans and penetration tests before going live to identify and fix potential security issues. Tools such as cloud security scanner, penetration tests, honeypots, and sandboxes help quickly identify and resolve problems, whether originated from bugs or attacks.
• Disaster drill solutions: When problems arise, we must stay calm and follow emergency procedures. Clear emergency plans and regular drills (2-3 times a year) ensure an effective response during real incidents.
How Alibaba Cloud Can Help:
• Professional enterprise support plan: We make sure that customers have a seamless experience in Alibaba Cloud, with a dedicated technical account manager (TAM) and a dedicated DingTalk enterprise group. We offer immediate assistance to solve your problems and ensure your business stability. The TAM follows up on each issue, and all issues receive an initial response within 15 minutes. For severe failures, the dedicated TAM coordinates with you and the R&D team to provide the most effective solutions. (I am a TAM. We have been helping customers solve all kinds of problems encountered in actual production and have accumulated a lot of experience.)
• Targeted security services: Cloud Security Scanner and Managed Security Service.
This section will introduce the O&M and detection practices of Alibaba Cloud from various aspects, including access methods, real-time monitoring, log discovery, and O&M configuration, to help you improve your cloud-based O&M and detection plan.
Let's start with a question: If you were a customer, how could you access Alibaba Cloud?
Effectively managing and monitoring all access methods can greatly enhance cloud security. Generally, there are three main access methods:
• Console: Typically, the IT architecture or security team of an enterprise logs on to the console as a RAM user. They can use and view integrated SaaS services from Alibaba Cloud, such as CloudMonitor, Cloud Config, and ActionTrail. This helps with the discovery and analysis of O&M issues and is one of the main methods for modifying cloud platform configurations. (If an application outsourcing team needs access, it is recommended to assign a specific RAM account with the appropriate permissions to the responsible person. It is not recommended to create too many accounts.) Operations performed in the console are only recommended for configuring the cloud platform. We recommend that operations on ECS and other services be accessed through a bastionhost, not directly through the console.
• API call: Typically, the automated O&M team or application maintenance team of an enterprise accesses an API by using an AccessKey pair. Alibaba Cloud API supports most service operations, including creating, modifying, and deleting resources. It is also a convenient way to access data. Customers with their own detection platforms can use the API to fetch data for custom analysis. This is also a main method for modifying cloud platform configurations. (Previously, it was difficult to detect changes made by this method, which was a major concern for many customers.)
• Accessing ECS (bastionhost): We recommend using a bastionhost, which is much more powerful than a traditional jump server. It provides complete operation trace recordings, logs, and command storage. You can add account management, access control, command auditing, and operation time restrictions. For ECS instances, the best practice is to close other connection ports and allow logon via the bastionhost only.
Alibaba Cloud provides specialized services to support various O&M and detection practices:
• ActionTrail: ActionTrail records all console operations and API call logs. It supports various predefined alert thresholds based on security best practices and allows exporting logs to SLS for custom alert monitoring. This is an excellent service.
• Bastionhost: The bastionhost is a platform provided by Alibaba Cloud for system maintenance and security auditing. Its use is required for audits of publicly traded companies and is essential for complying with global security regulations.
These recommended best practices cover 99% of use cases.
Here's how to configure ActionTrail:
1. Enable ActionTrail
Search for ActionTrail in the console and enable the service.
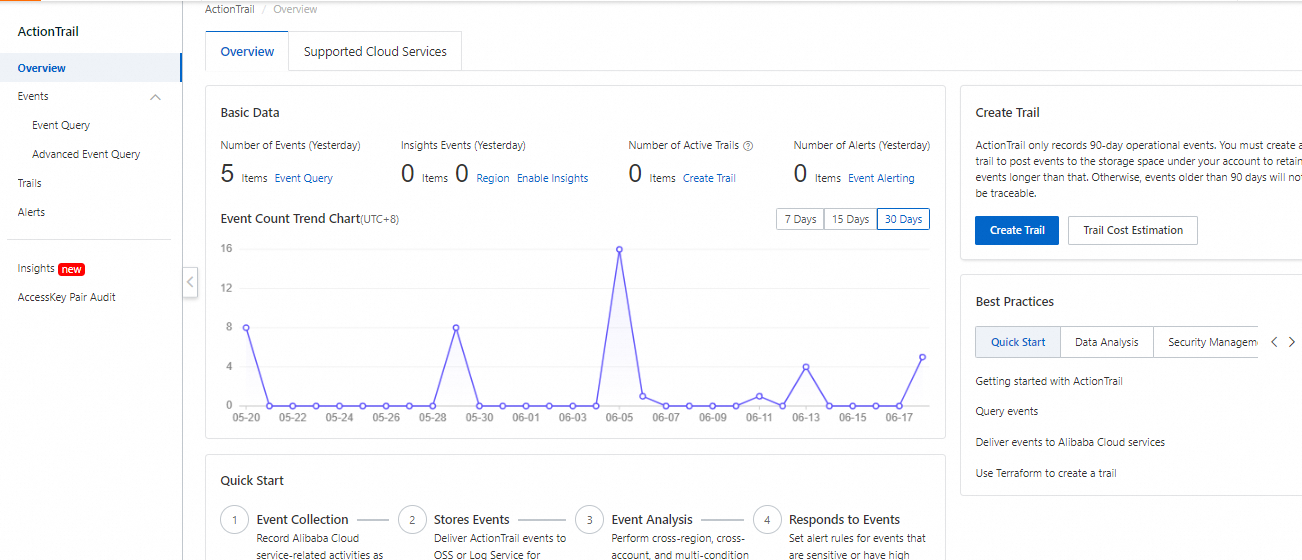
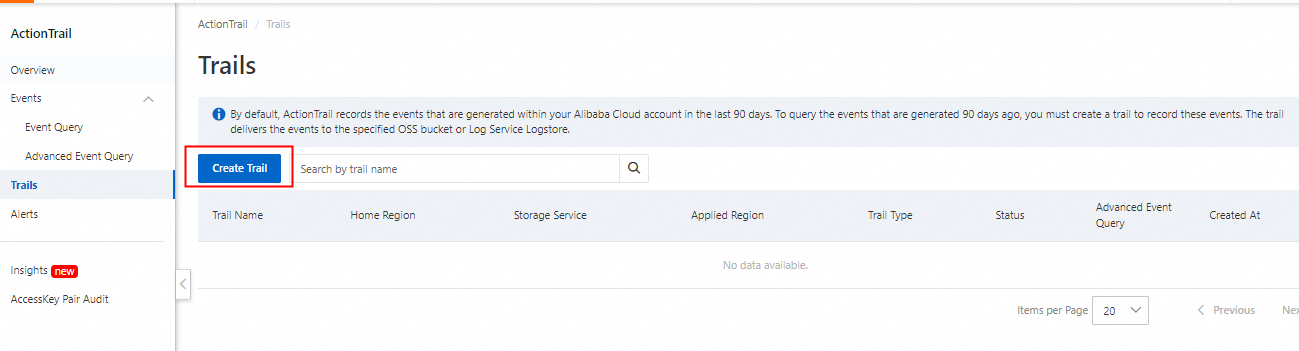
2. By default, you can query events that were generated in the last 90 days. To query events across multiple regions over a longer period of time, you must create a trail.
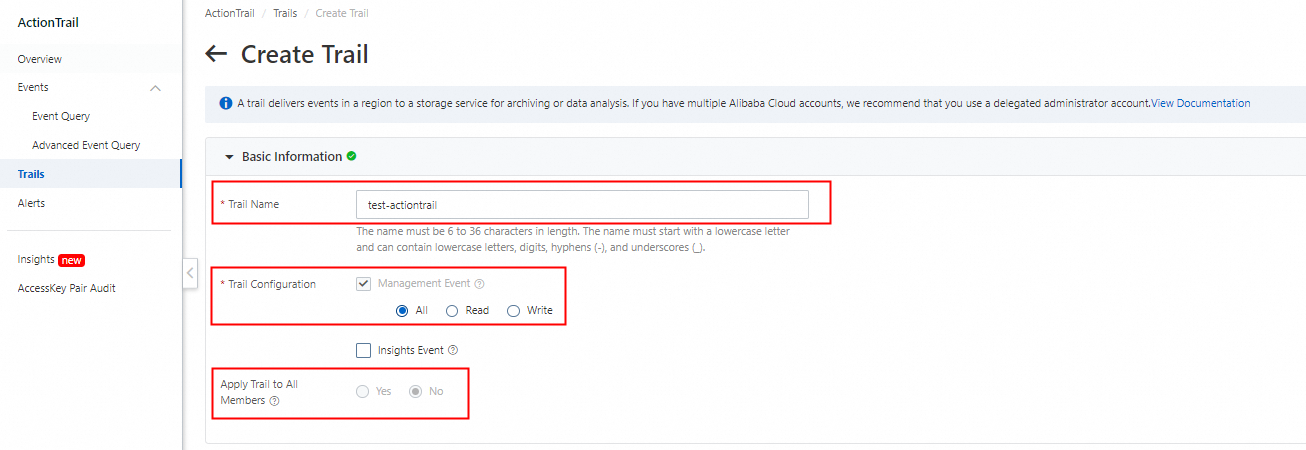
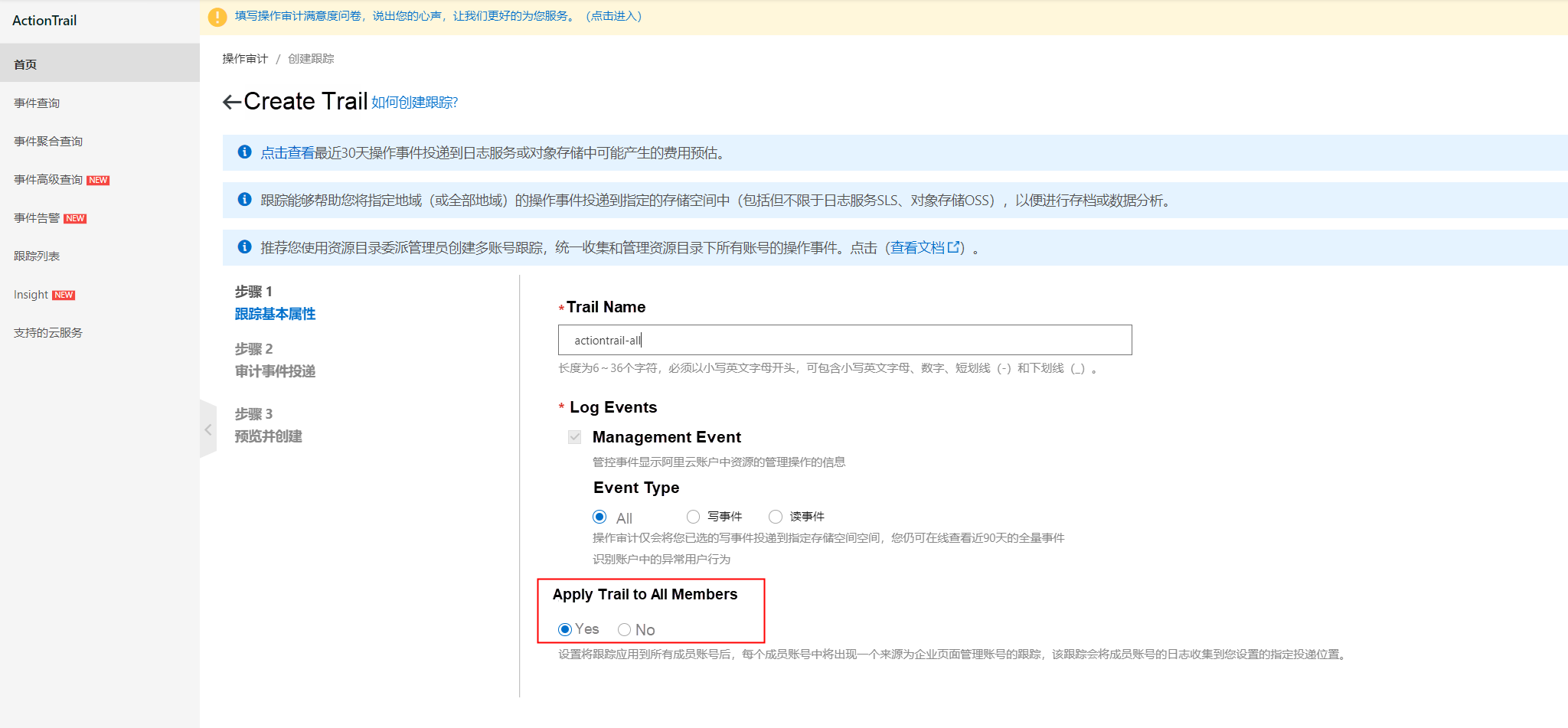
When creating a trail, specify a name and select All for Trail Configuration. Select No for Apply Trail to All Members.
(Note: Multi-account tracking requires a resource directory, which will be detailed in the multi-account section.)
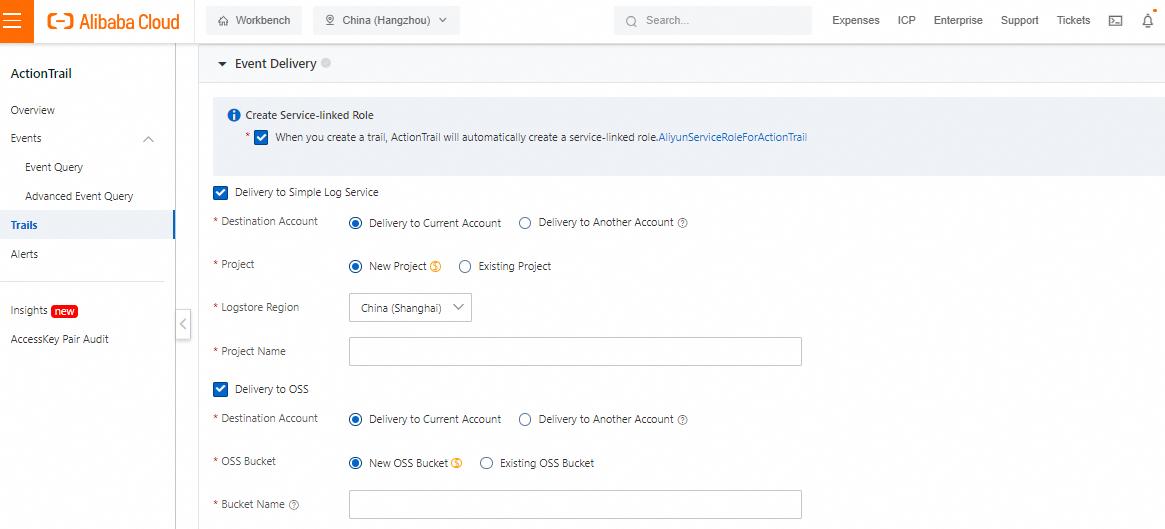
Select a delivery option:
Choose whether to deliver logs to SLS or OSS, or not to deliver logs at all.
Here's a brief comparison of SLS and OSS delivery:
• SLS: Recommended. It allows you to view real-time data and offers a powerful custom module, enabling you to set up alerts and monitor your logs. However, it is more expensive than OSS.
• OSS: Suitable for long-term storage (for example, storage over one year). The files are in compressed format. You need to download and decompress the files to view the content. This makes it inconvenient to view real-time data.
Set up new SLS and OSS instances as needed.
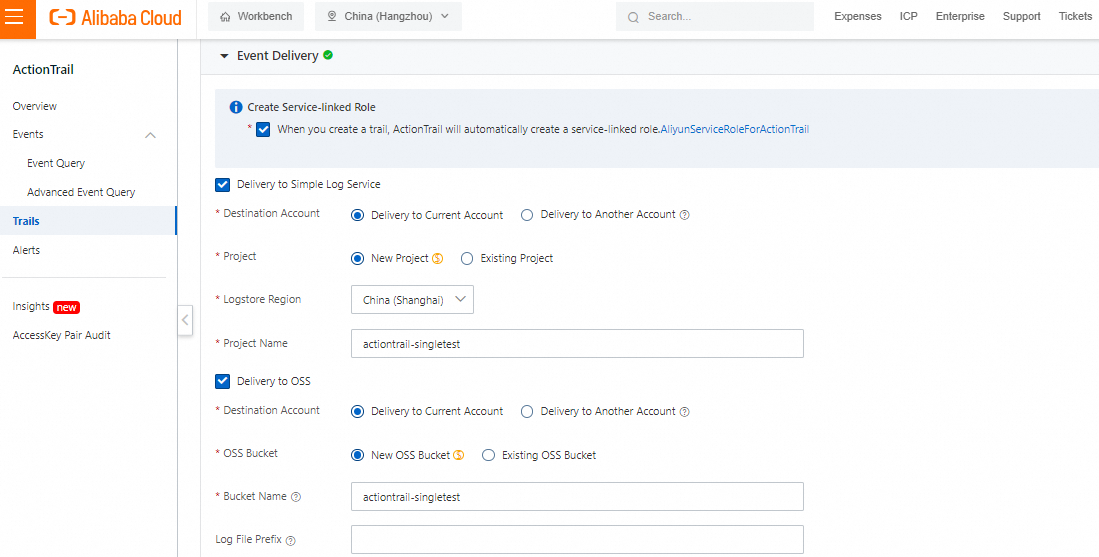
Verify the information, and if everything is correct, create the trail.
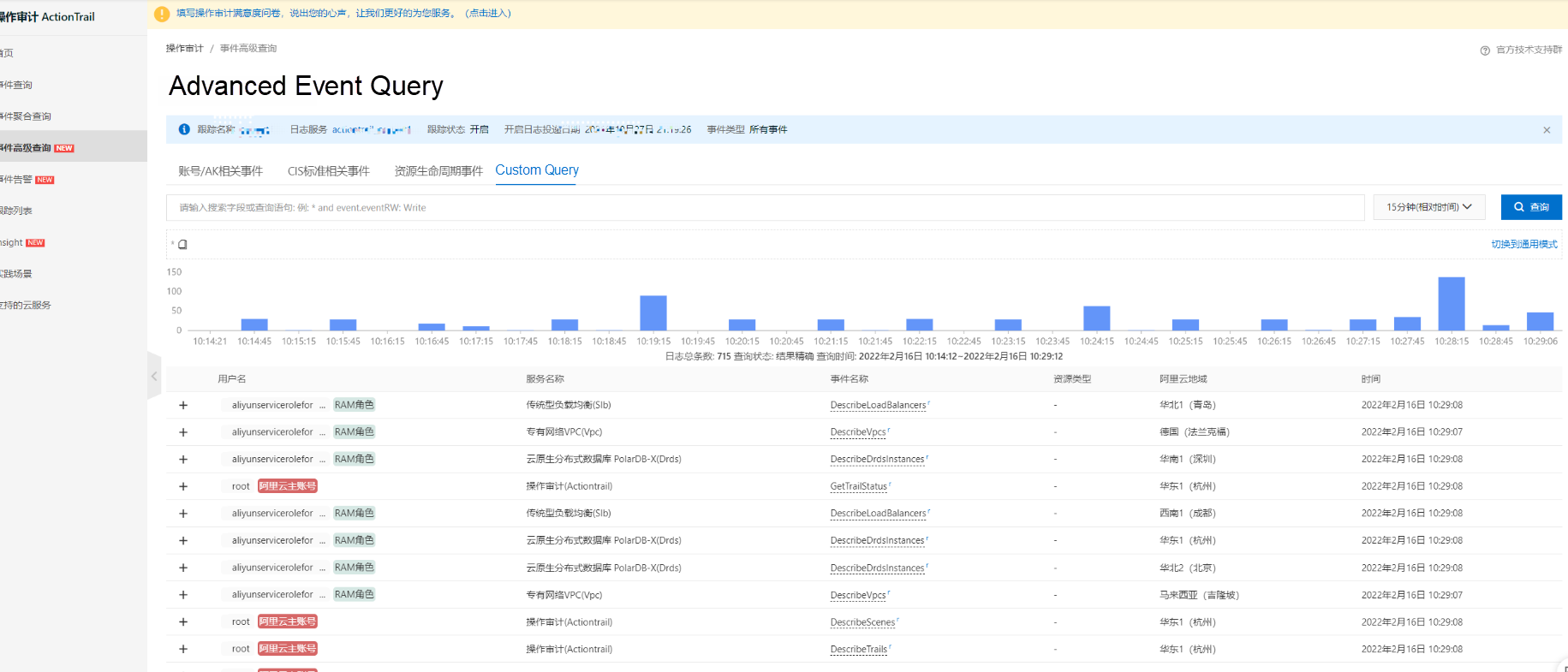
The following figure shows how the SLS interface works:
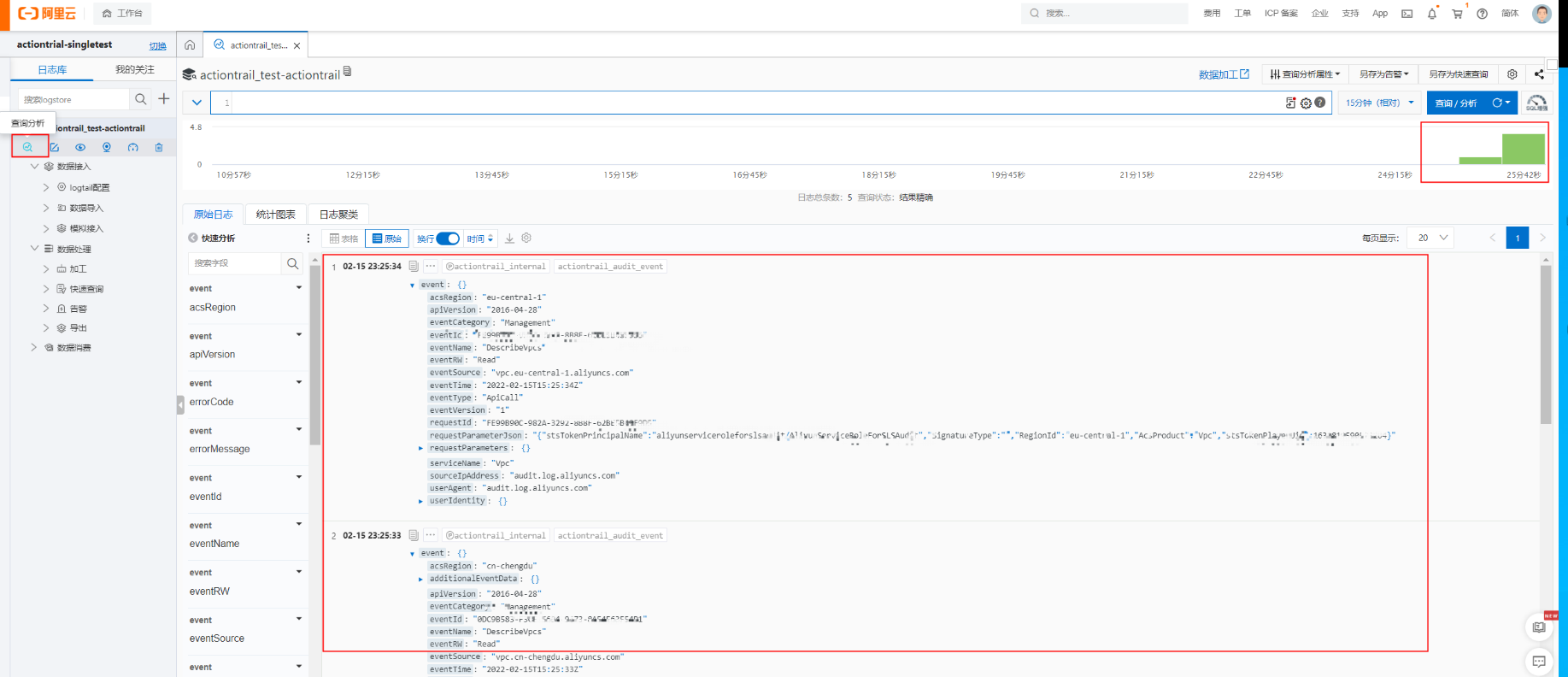
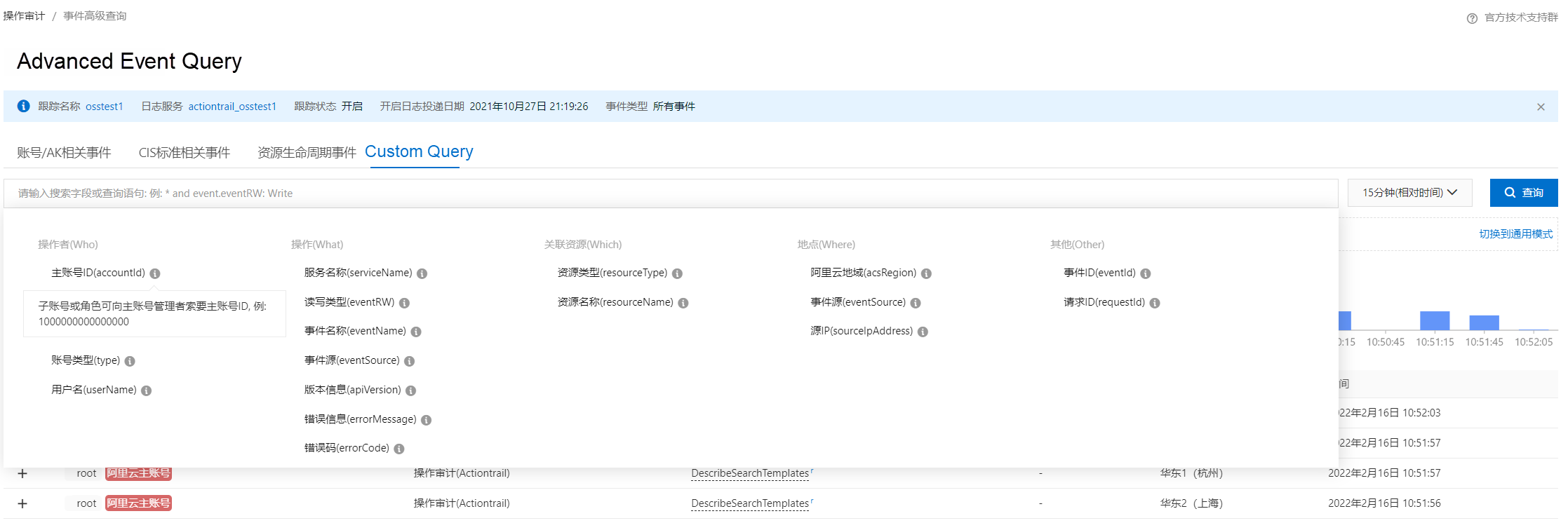
We strongly recommend using the advanced event query feature. It allows you to view data clearly and search for specific information using keywords. The GUI is also user-friendly.
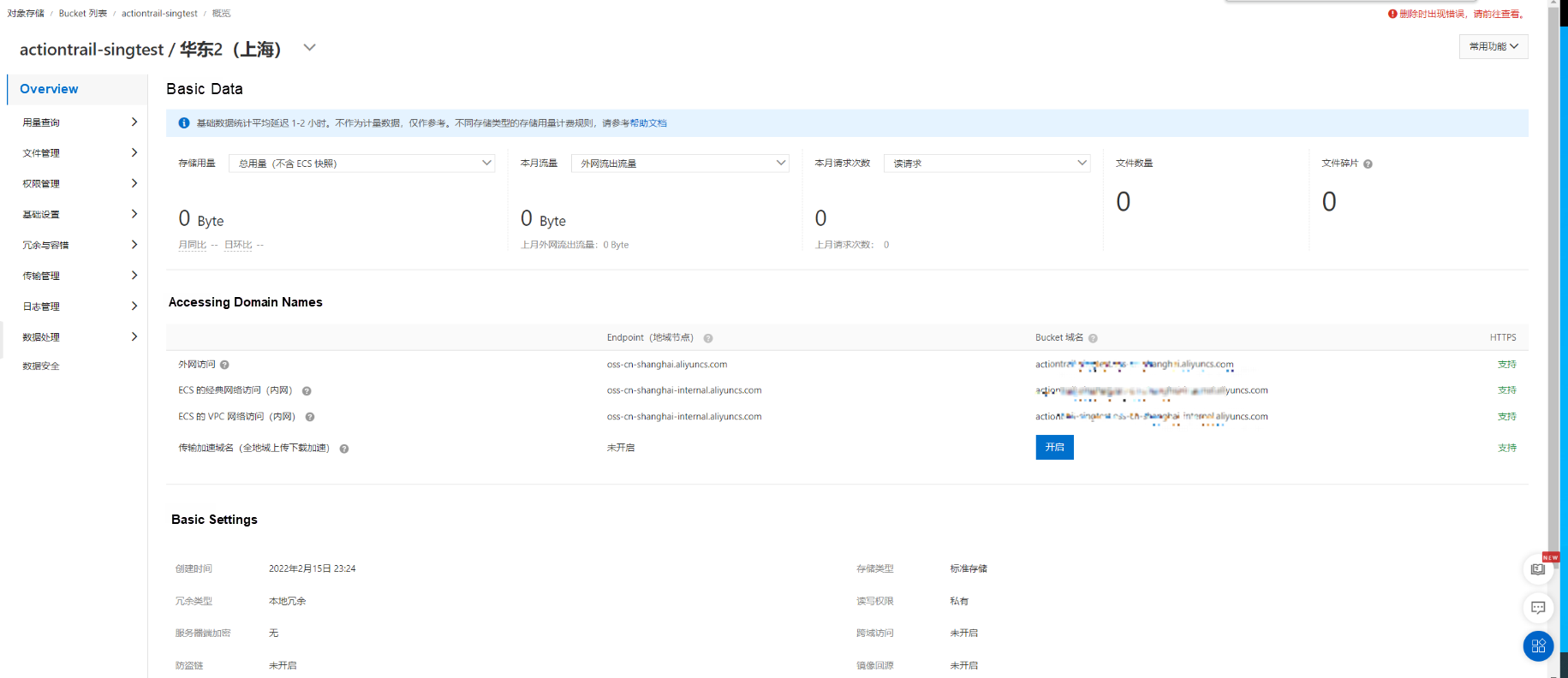
Here's what to expect with OSS:
The storage is newly created and does not contain any files. You will be able to view the files on the Object Management page later.
Multi-account deployment can be handled in two ways.
Scenario 1: All your accounts are in a single resource directory. In this case, when creating the trail, set Apply Trail to All Members to Yes. Logs from all member accounts are collected into a single Logstore, which is convenient and efficient.
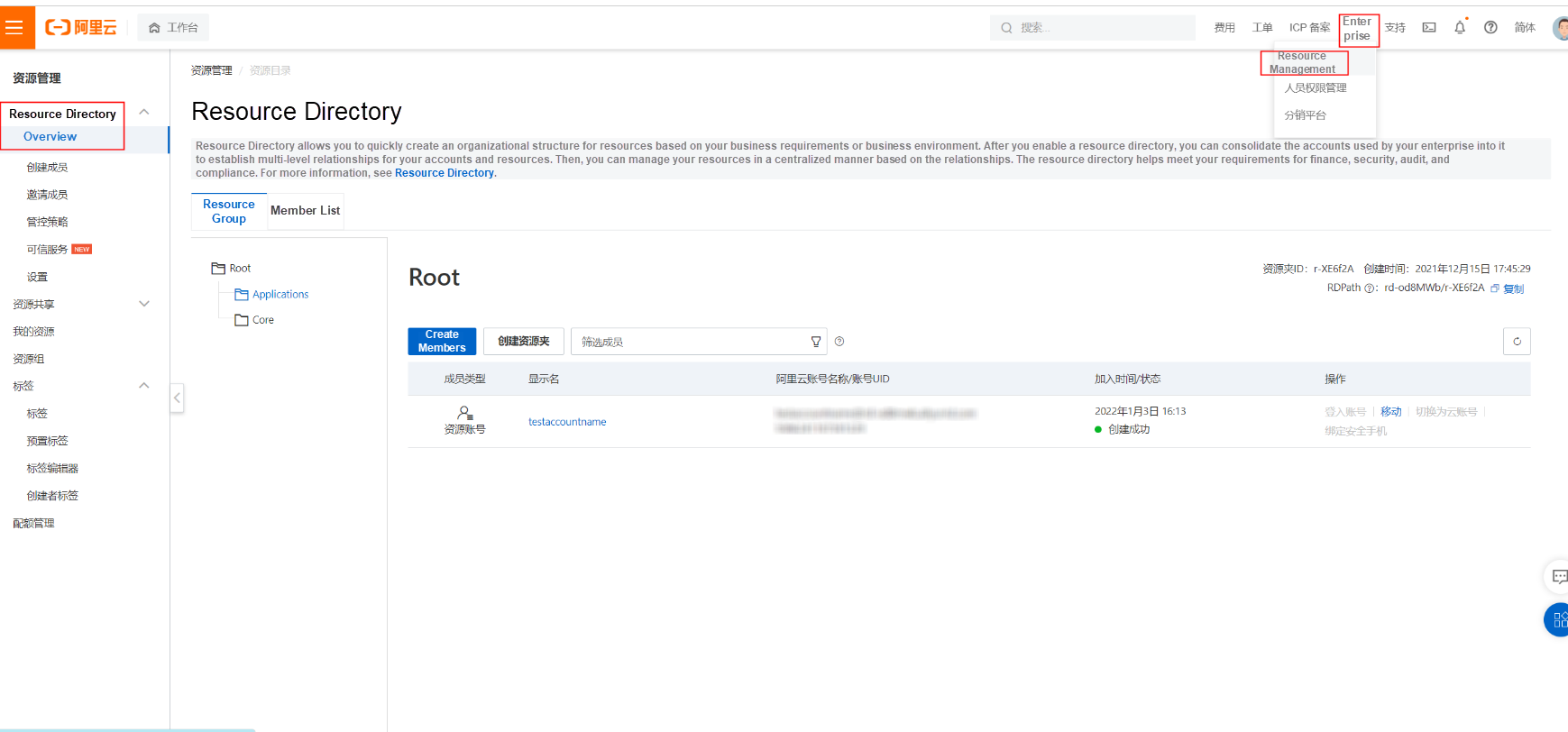
To check the status of your accounts, go to Enterprise > Resource Management > Resource Directory > Overview.
You can see whether all your enterprise accounts are in the same resource directory and the accounts that are automatically tracked.
When creating the trail, set Apply Trail to All Members to Yes.
Note:
You can create only one trail in multi-account deployment.
Scenario 2: Due to historical reasons, such as different enterprise entities, some accounts cannot join the resource directory. In this case, you cannot centralize all logs into one Logstore for analysis. However, you can deliver the operation audit logs of accounts outside the resource directory to a specific SLS Logstore of the specified audit account. This way, auditors can review multiple accounts from one account.
Here's how to configure this:
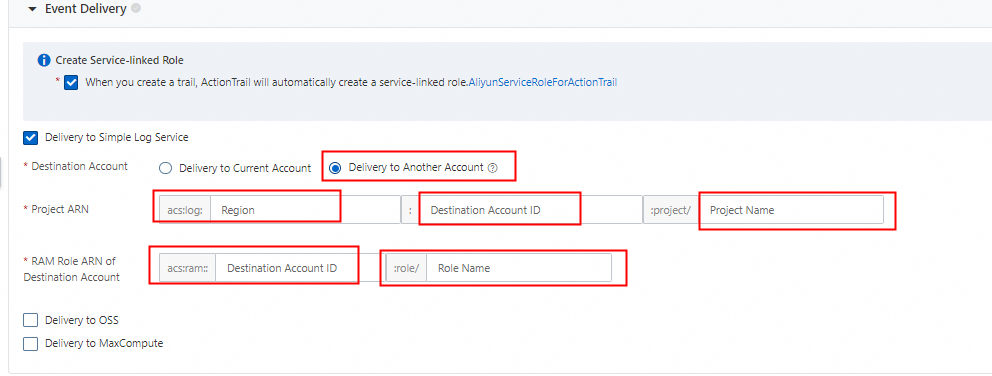
When setting event delivery, set Destination Account to Delivery to Another Account.
Please note the following points:
• You need to create a new SLS project in the original account and fill in the necessary information (ensure that the region is consistent).
• For RAM Role ARN of Destination Account, you must create a new role within the account to which you want to deliver logs and grant the appropriate permissions.
Steps to create a new role and grant permissions:
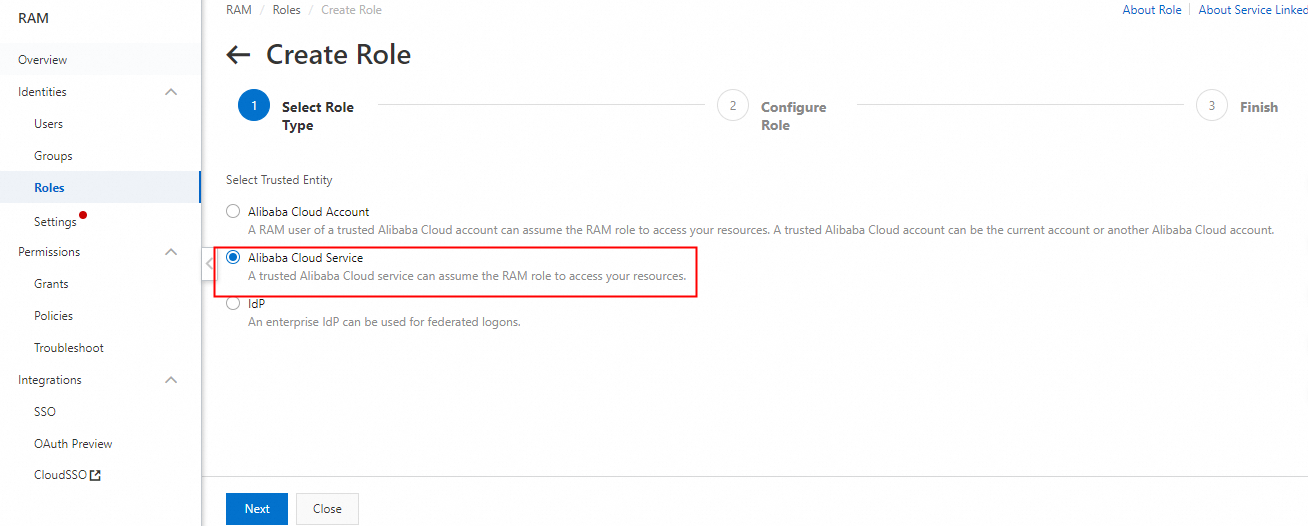
1. Log on to the RAM console by using the destination account and go to the Roles page. Click Create Role and select Alibaba Cloud Service in the wizard that appears.
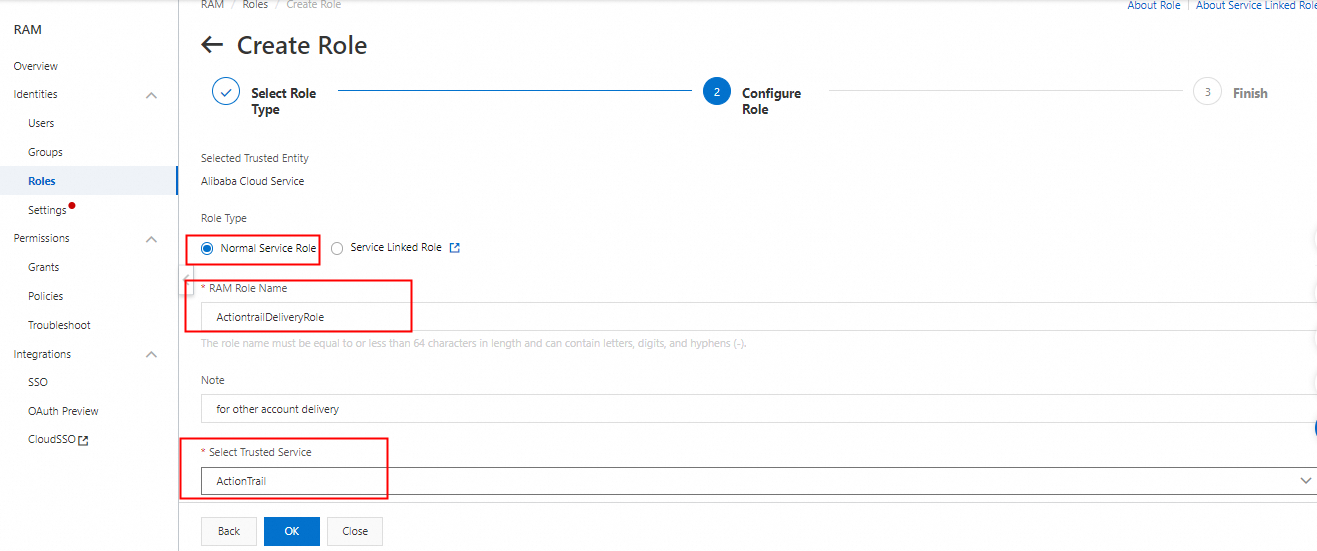
2. Select Normal Service Role as Role Type, name the role based on the naming conventions of your enterprise, and select ActionTrail as the trusted service.
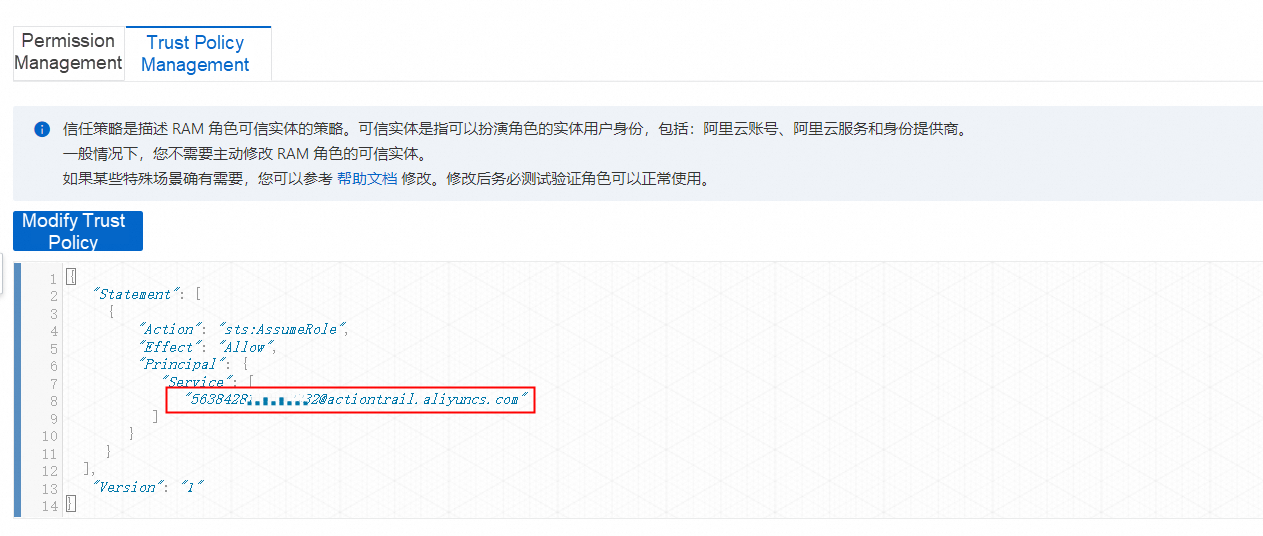
3. On the Permissions tab of the new role, click Precise Permission. In the panel that appears, select System Policy as Type and enter AliyunActionTrailDeliveryPolicy as the policy name.
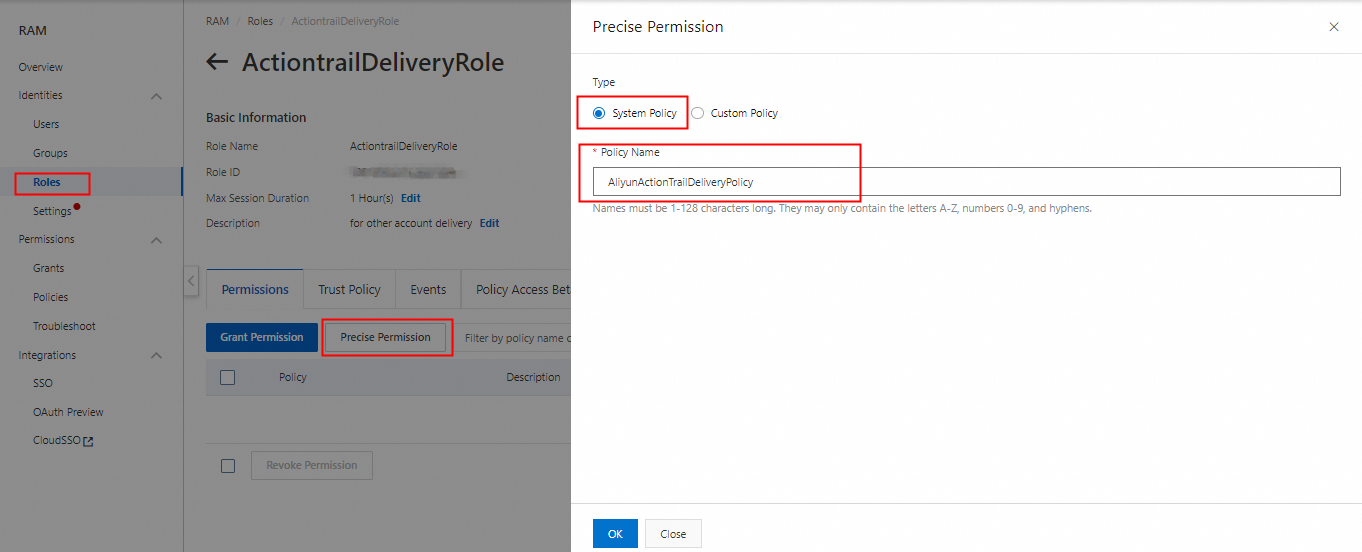
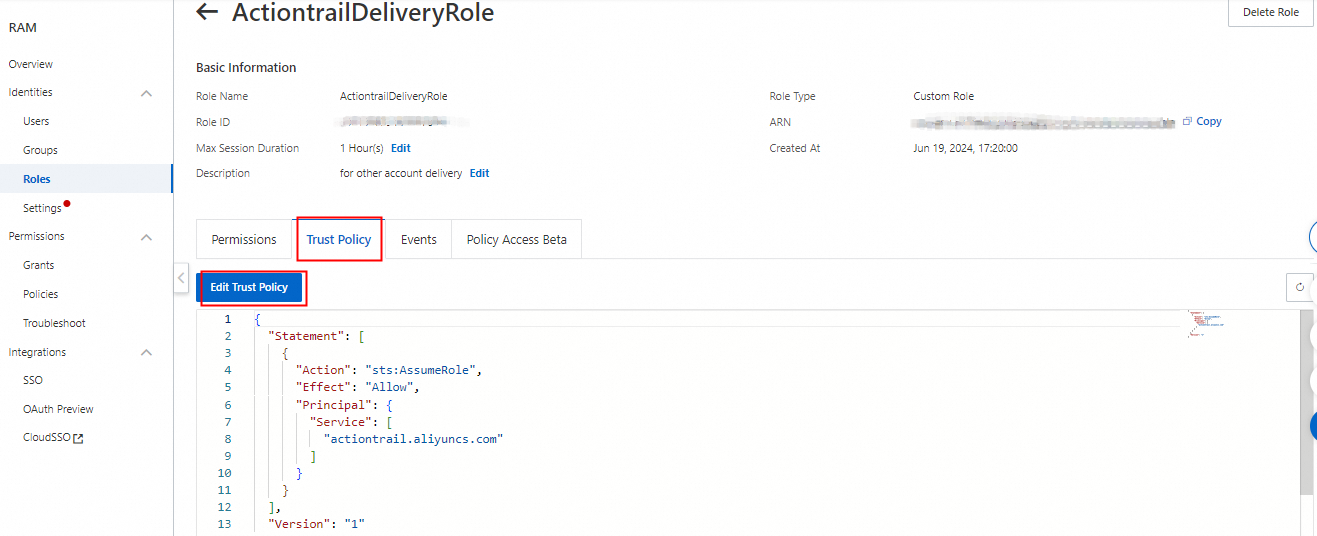
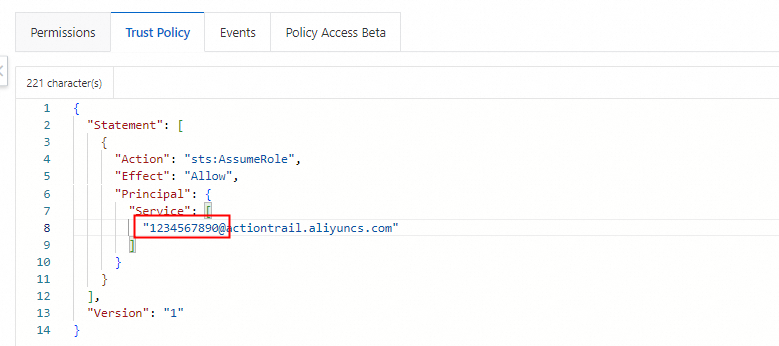
4. Modify the trust policy by adding the UID of the destination account and allowing this role to access the ActionTrail service of the corresponding accounts. Modify the Service section by adding the corresponding UID@ before actiontrail.aliyuncs.com. In this example, the account UID is 1234567890.
Once the configuration is complete, you can use the role for log delivery.
Other configuration details are similar to those for a single account and will not be repeated here.
Initializing a bastionhost involves several steps. For detailed instructions, see the product documentation. This guide will focus on three main aspects: account management, network access, and O&M audit.
If you are new to bastionhosts, you might encounter many concepts such as users (user groups), managed hosts (managed host groups), hosts (host groups), and host accounts.
The logical sequence is: User > Managed Host (which needs to be added to the access list) > Host Account.
1. User (User Group) > Managed Host (Managed Host Group)
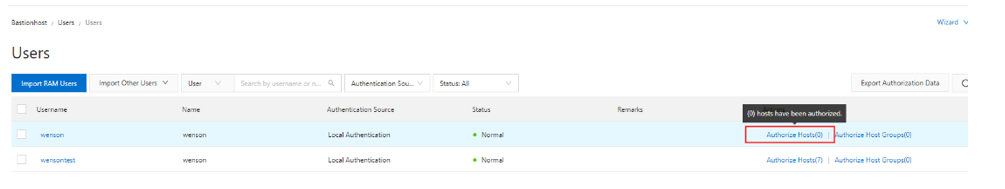
User's role: Users can connect to the bastionhost system. On the bastionhost, you can configure the managed hosts and host groups that specific users can access. They cannot see the hosts that are not added to the access list.
Typically, a RAM user can connect to the bastionhost. You can also configure a user in the bastionhost console.
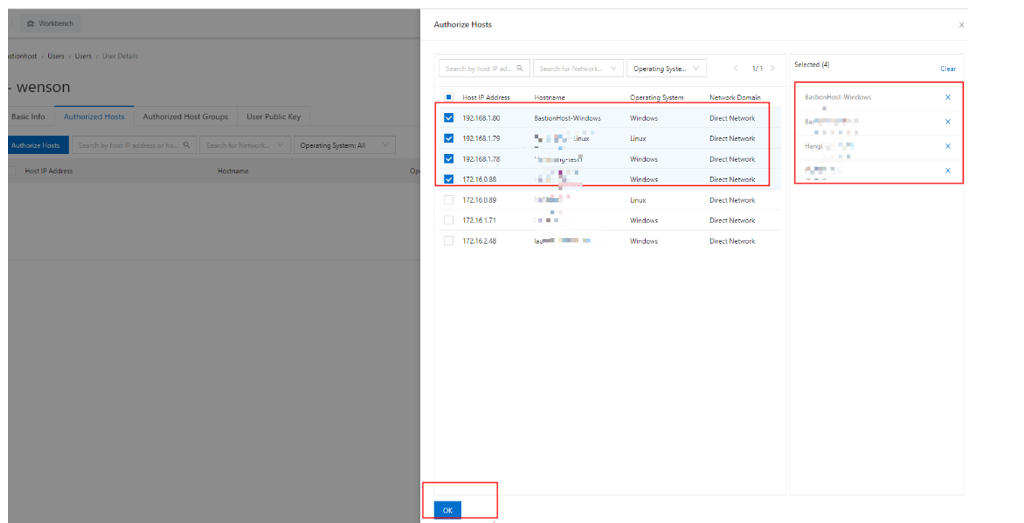
You must add managed hosts for the user; otherwise, the user cannot perform any tasks.
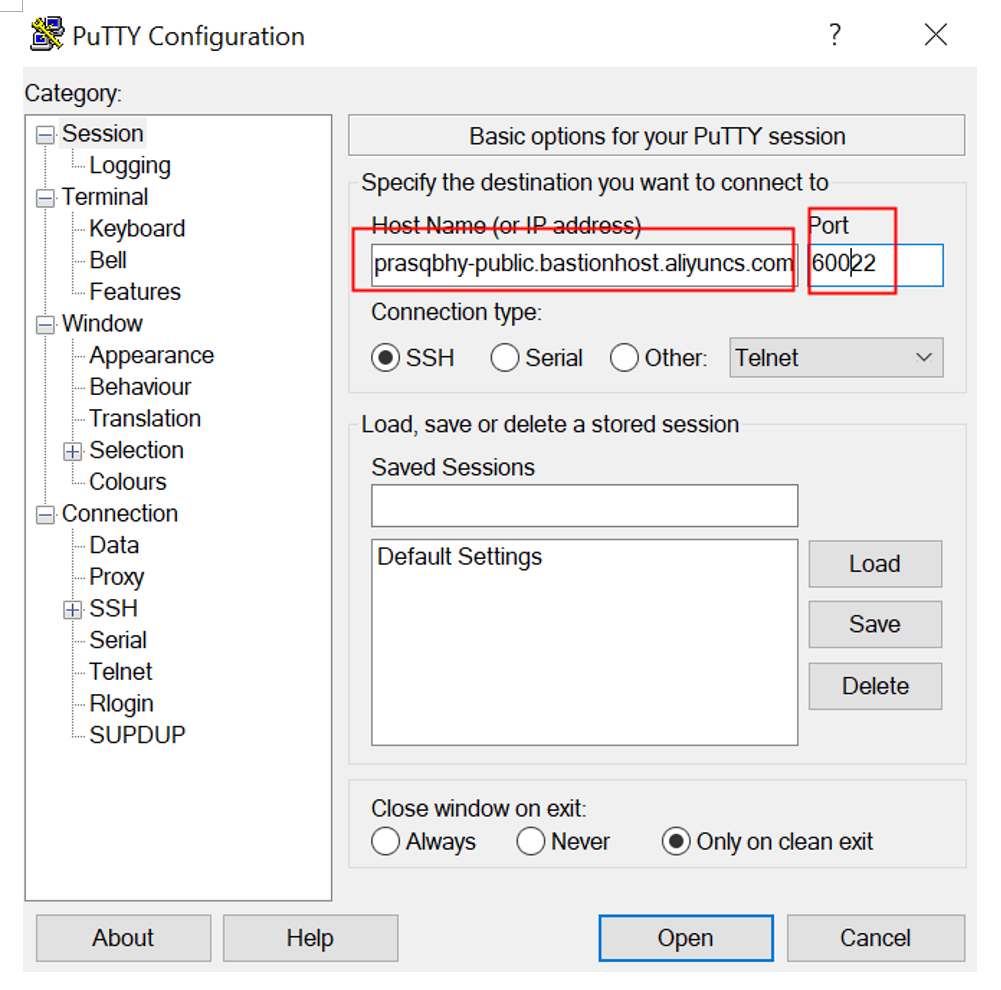
When logging on to the bastionhost, the user performed authentication using the username and password at the first level. For example, in a Linux environment, if a user named "wensontest" logs on, the user must enter the username and password (username and password of the RAM user).
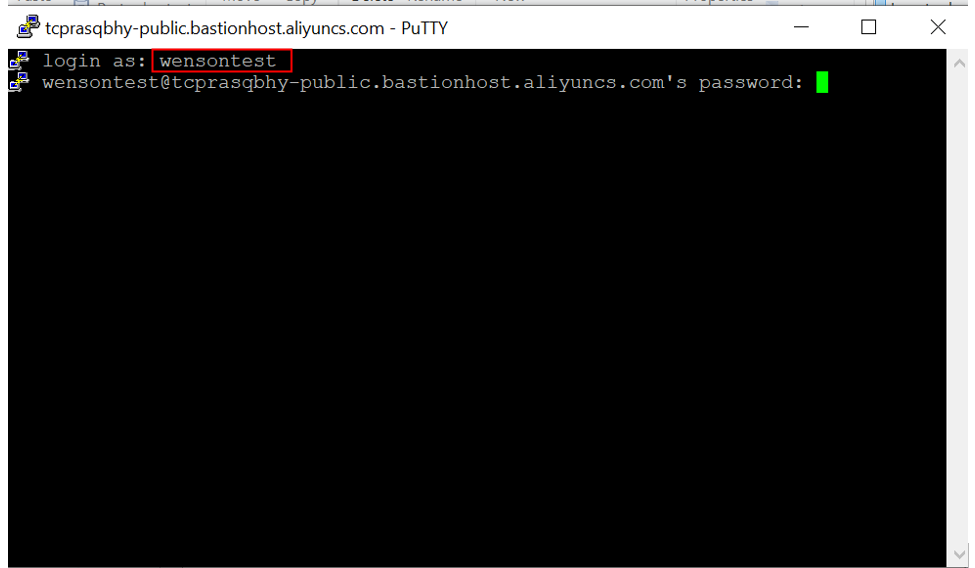
After logging on, the user can see associated hosts. These hosts must be added to the user's managed hosts list to be visible.
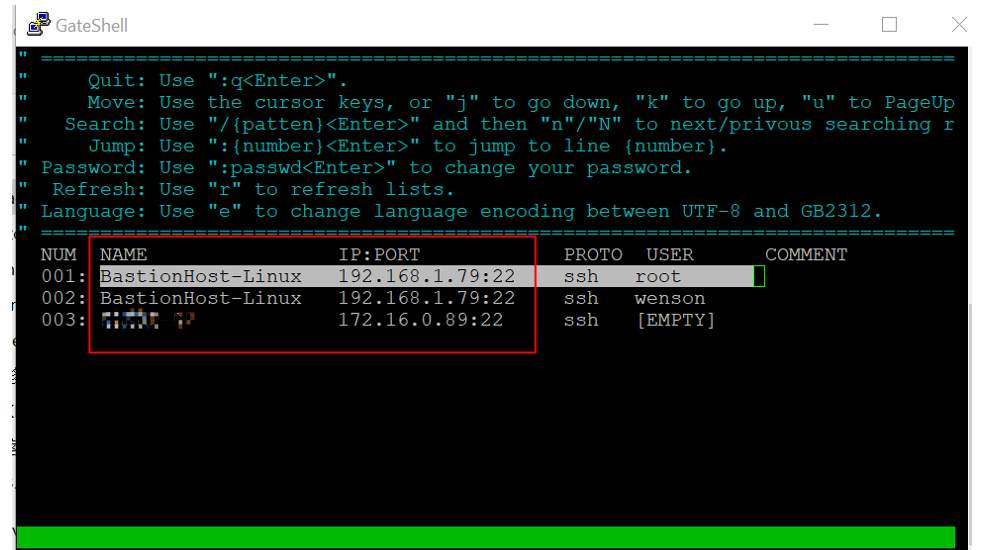
2. Host (Host Group) > Host Account
A host represents a server that needs to be managed, primarily ECS. Alibaba Cloud servers can be easily imported via the console.
Host: refers to an ECS instance.
Host Account: refers to a management account on ECS, which is similar to "administrator" in Windows or "root" in Linux. You can set up various accounts on the server for management purposes.
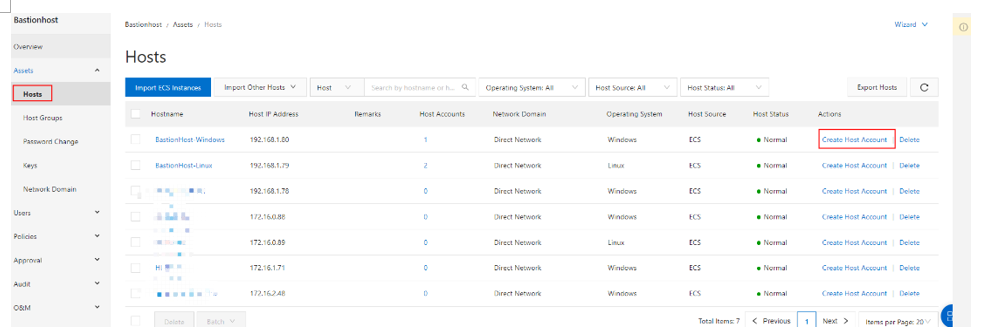
Typically, host accounts are configured directly on the server. These accounts help enterprises manage access to their hosts. By default, only managed host accounts can access the hosts.
You need to create a host account and perform authentication. After the authentication is passed, you can log on to the ECS instance using the host account.
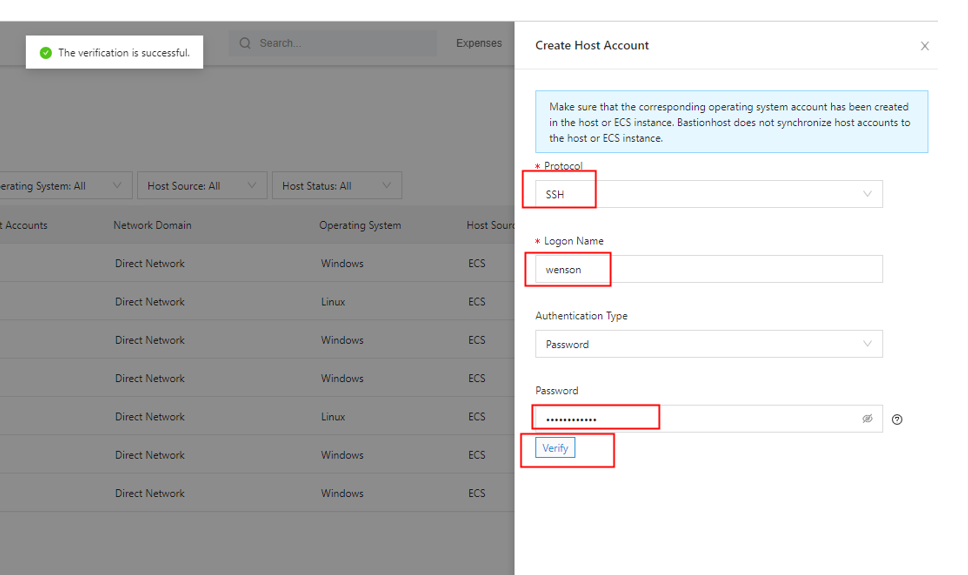
You can add multiple host accounts, such as "wenson" and "root." However, if you have a user "admin" but do not add it as a host account, you will not be able to use "admin" to log on, even if you know the password.
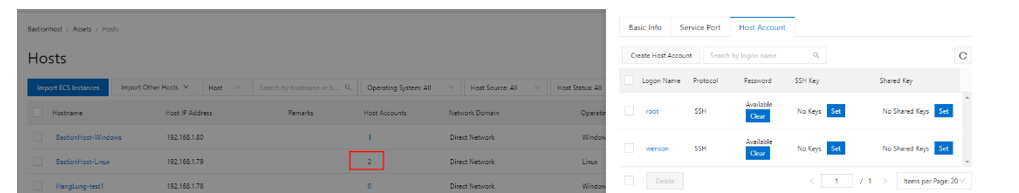
Your logon page will only display the host accounts you have added. For example, if "root" and "wenson" are on the same host, both accounts will appear as options.
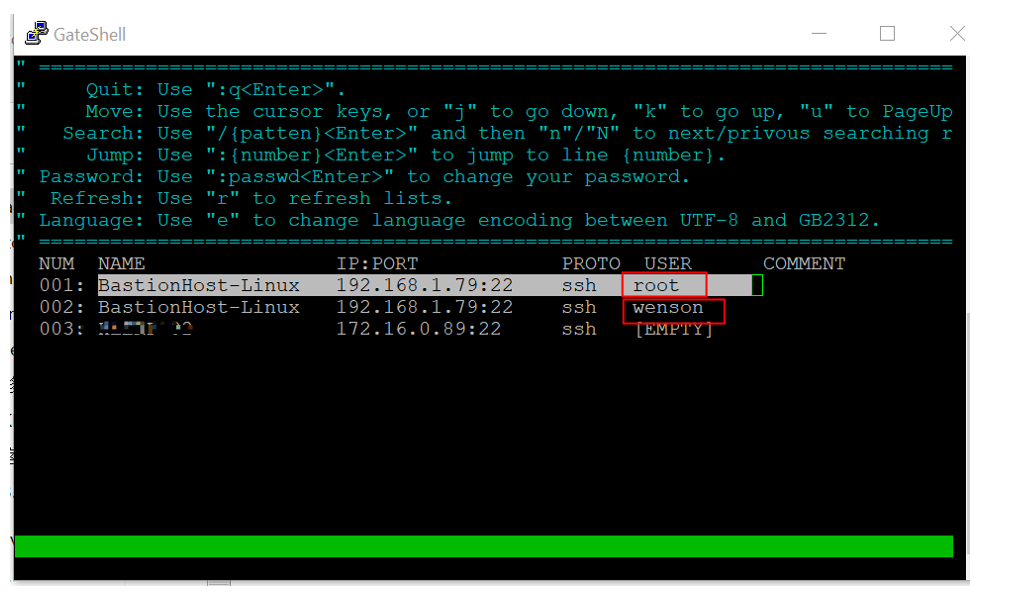
You may also notice an "empty" option. The bastionhost allows users to enter their own username and password, which is useful for scenarios with many outsourced projects. However, this weakens the management capabilities of the bastionhost.
There are corresponding options for this in the system settings.
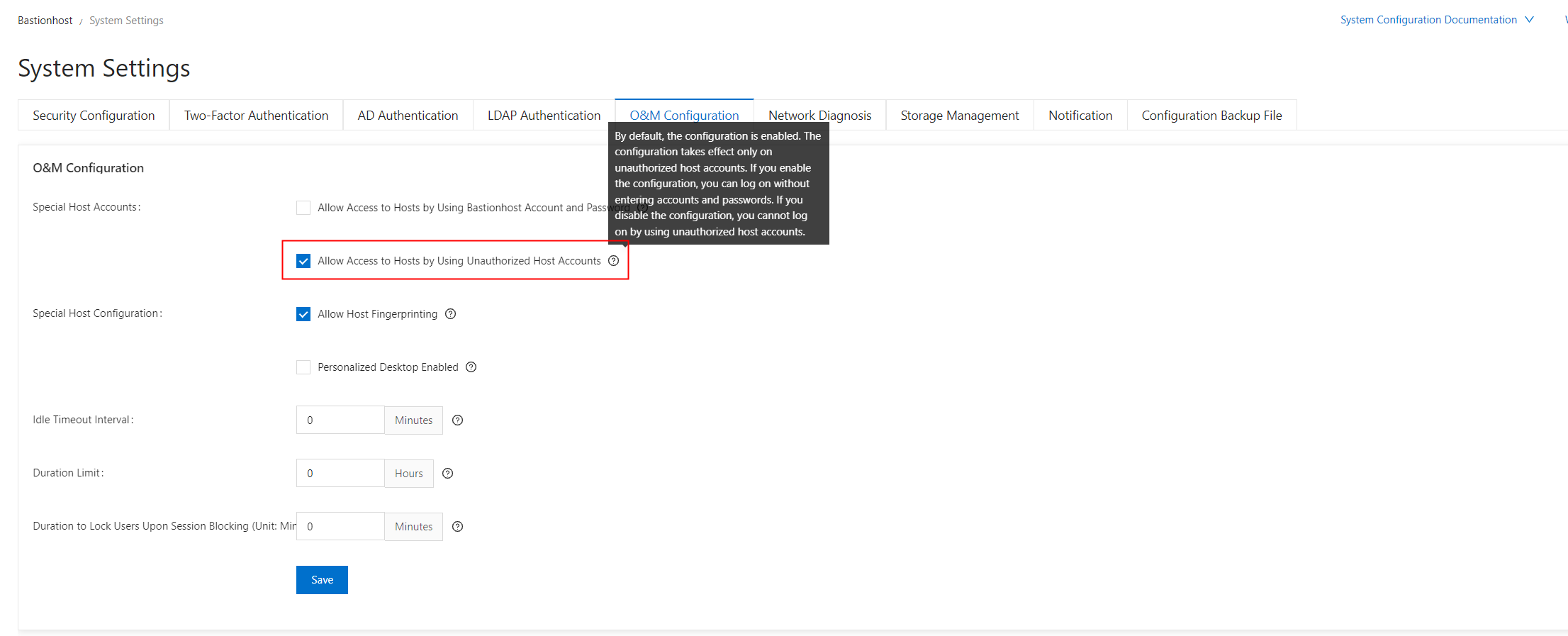
To summarize, remember the logic in account management: User > Managed Host > Host Account. These are the three layers of relationships. Make sure not to mix up usernames and passwords.
When using a bastionhost for the first time, many users encounter network issues. Here is a brief introduction on how to connect the bastionhost to the network.
During initialization, the bastionhost is assigned a specific VPC, VSwitch, and security group. By default, only the ECS instances within this security group can communicate with the bastionhost. For other instances to connect, you need to perform additional configurations, such as using Cloud Enterprise Network (CEN). Remember that not all cloud servers in Alibaba Cloud can directly access the bastionhost.
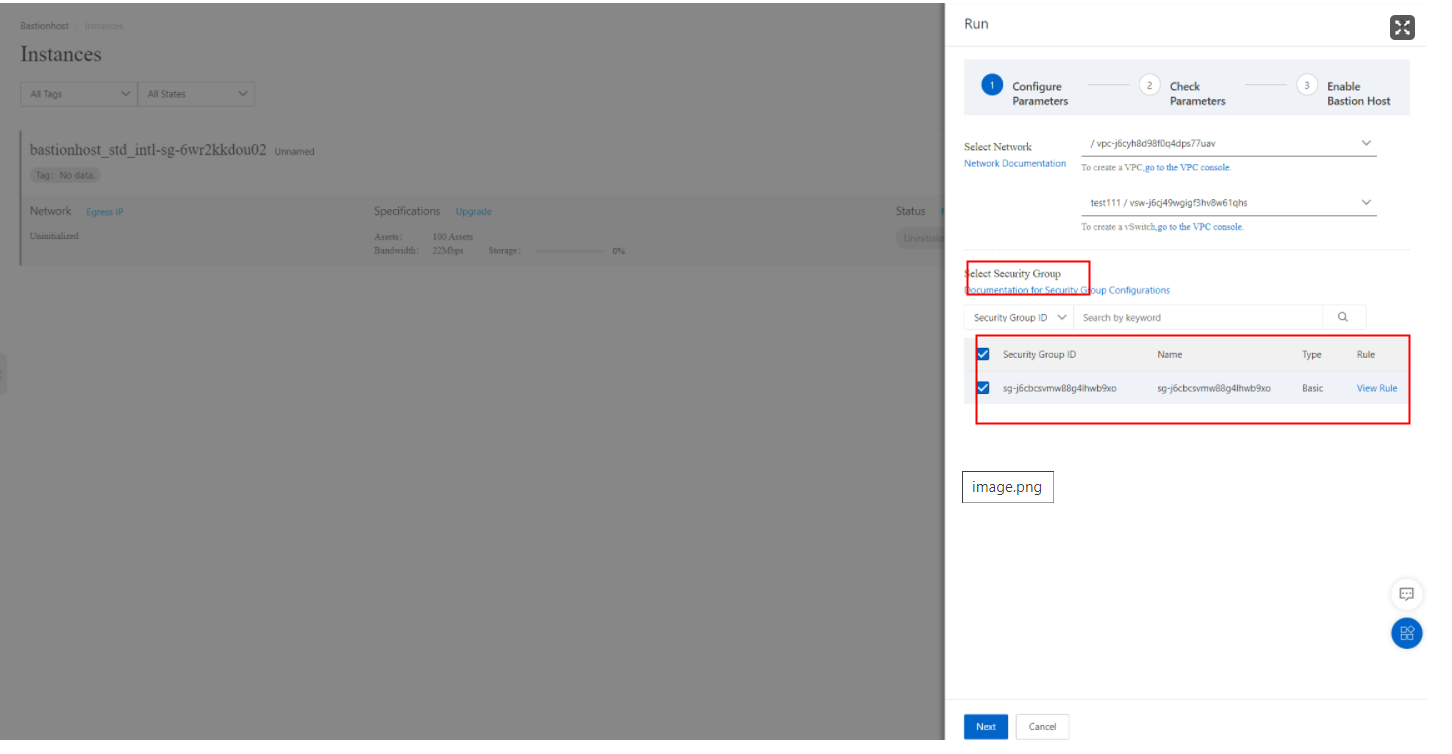
You can add and edit multiple security groups later. However, for connections beyond the VSwitch level, you will need to use CEN.
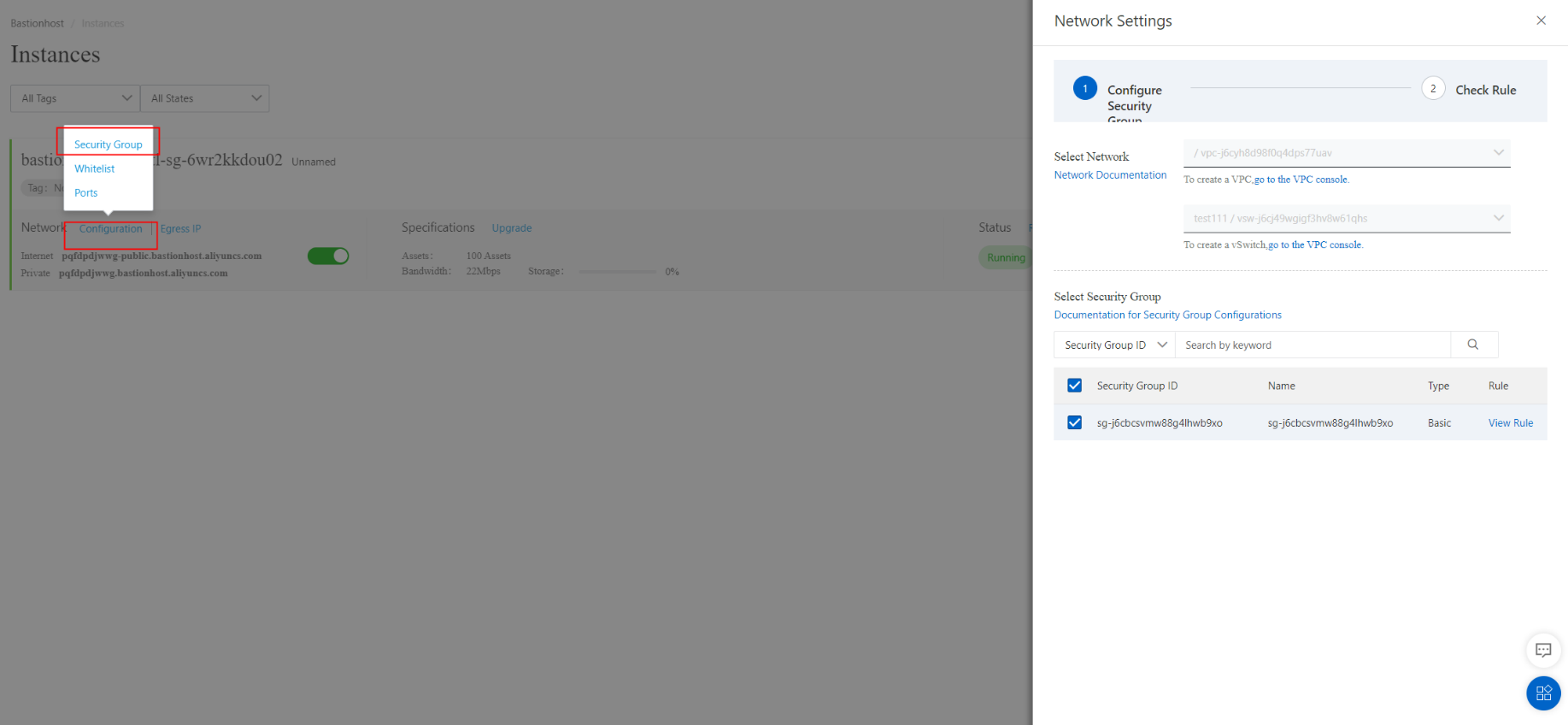
As long as the network is reachable, the bastionhost can connect to it with the proper configuration. For multi-account scenarios, we recommend deploying the bastionhost in a shared resource account for unified management, which is efficient and convenient. We will not go into further details about other network connectivity options here.
This section uses the built-in features of the system, including video auditing, real-time monitoring, and operation logs.
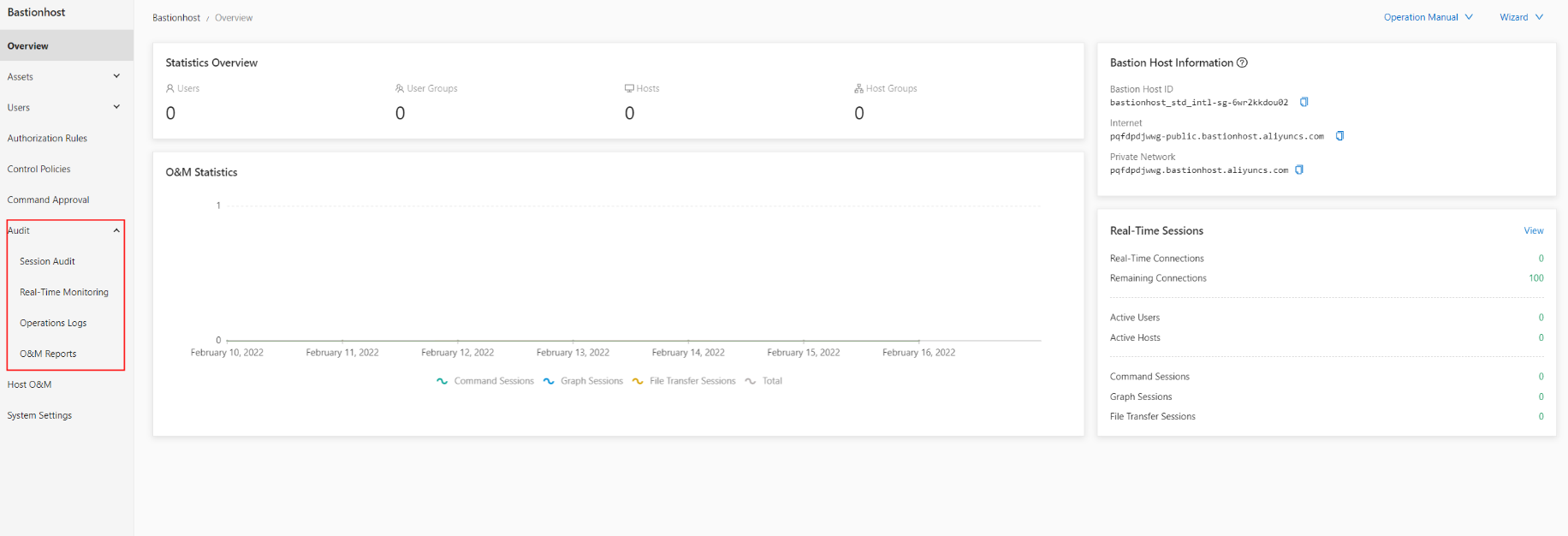
Here are a few screenshots for your reference. All these operations are performed directly in the console.
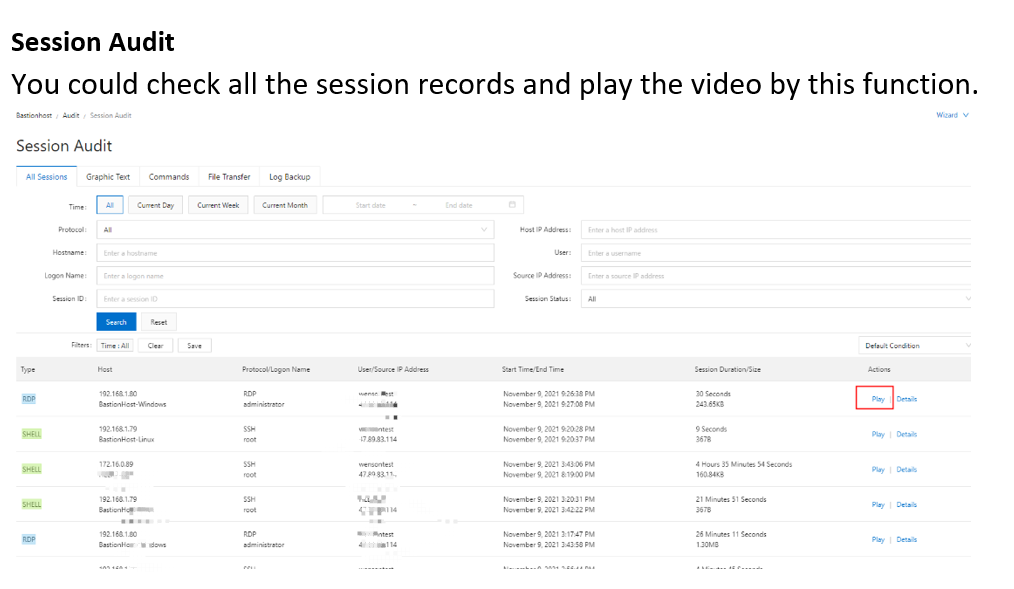
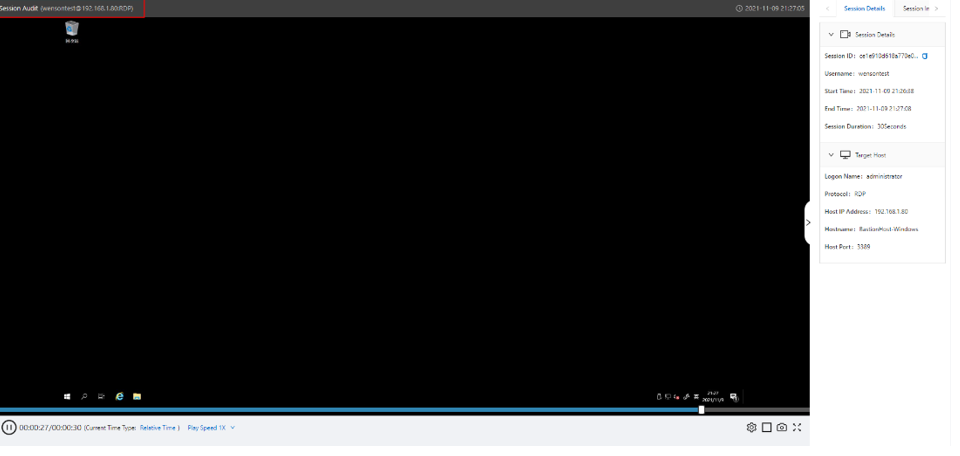
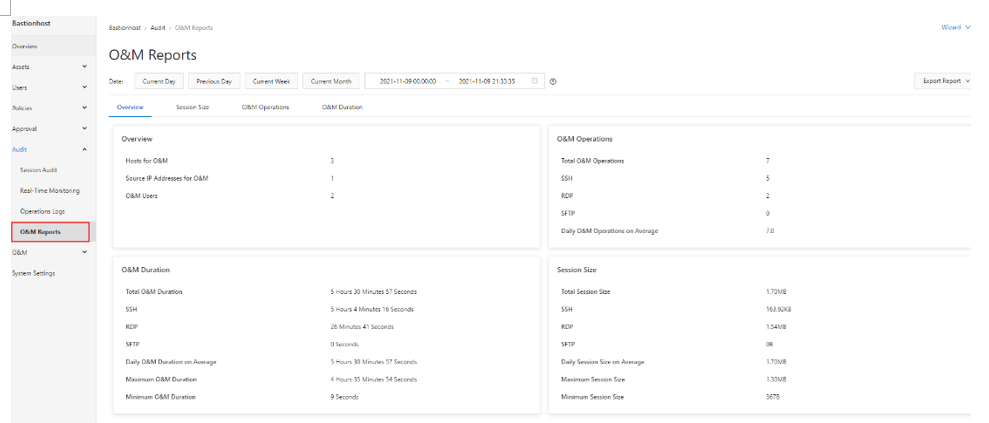
After addressing access issues, the next priority is ensuring that the customer's system runs continuously without interruption. It is essential for customers to monitor the system status in real time and receive timely notifications if any anomalies occur.
Monitoring notifications can be triggered from various sources such as CloudMonitor, SLS, and Cloud Config. In this section, we will focus on real-time performance metrics, such as sudden spikes in CPU utilization or memory usage. We will primarily discuss CloudMonitor here, with SLS and Cloud Config covered in later sections.
CloudMonitor supports the following key features:
This feature allows you to group instances based on tags and rules. We recommend setting the system to automatically include all instances with a specific tag into a group.
This way, new instances are automatically included in the group for monitoring. You just need to monitor the metrics for the group.
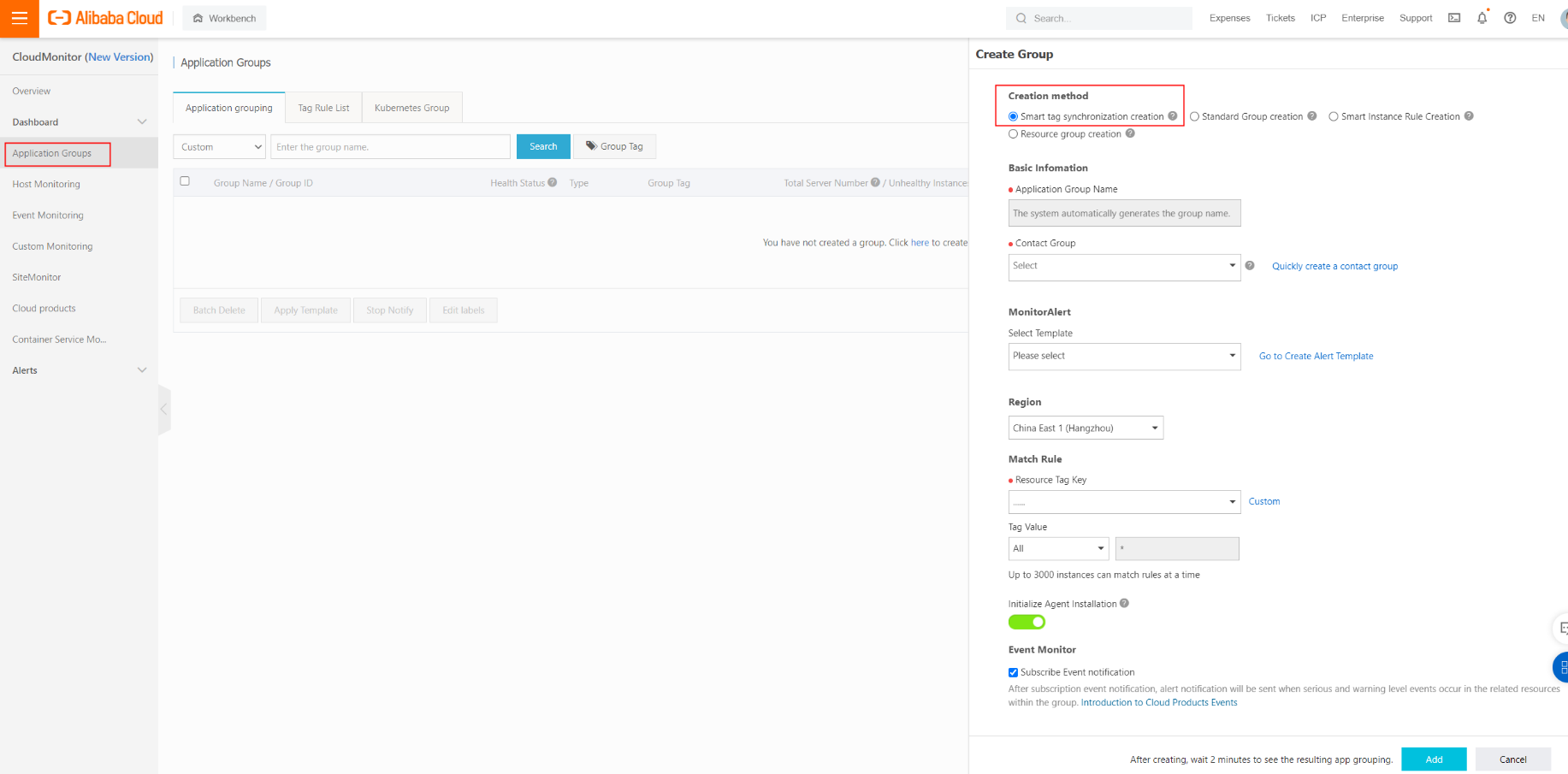
This is one of the most well-known features, focusing on monitoring CPU, memory, and disk usage.
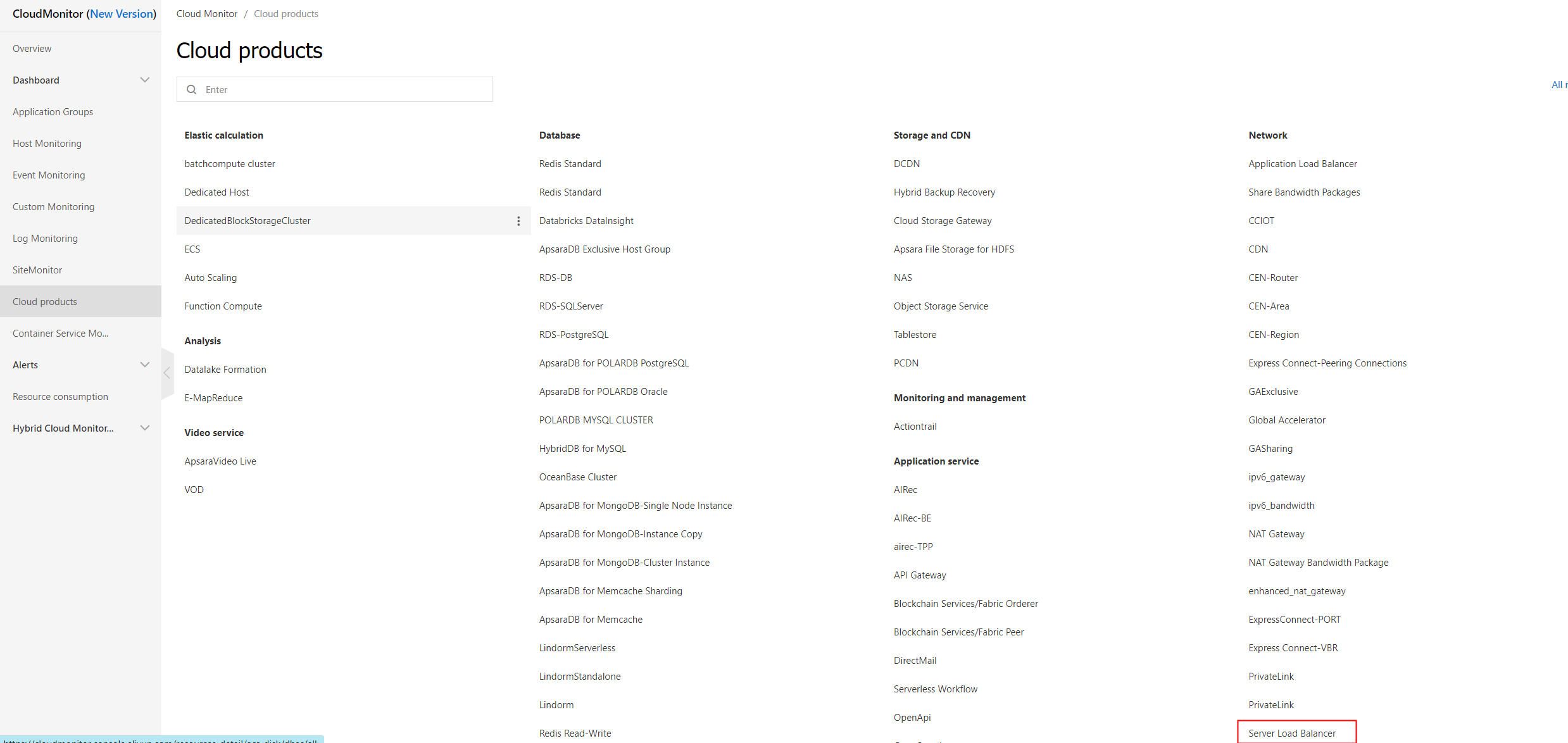
Alibaba Cloud offers many high-quality cloud services. CloudMonitor allows you to customize monitoring for these services.
You must make full use of the cloud service monitoring module, which is extremely helpful. When creating specific monitoring rules, CloudMonitor provides numerous parameters and metrics. You can set thresholds according to your needs, such as 10% or 20%, to effectively monitor the performance of your application.
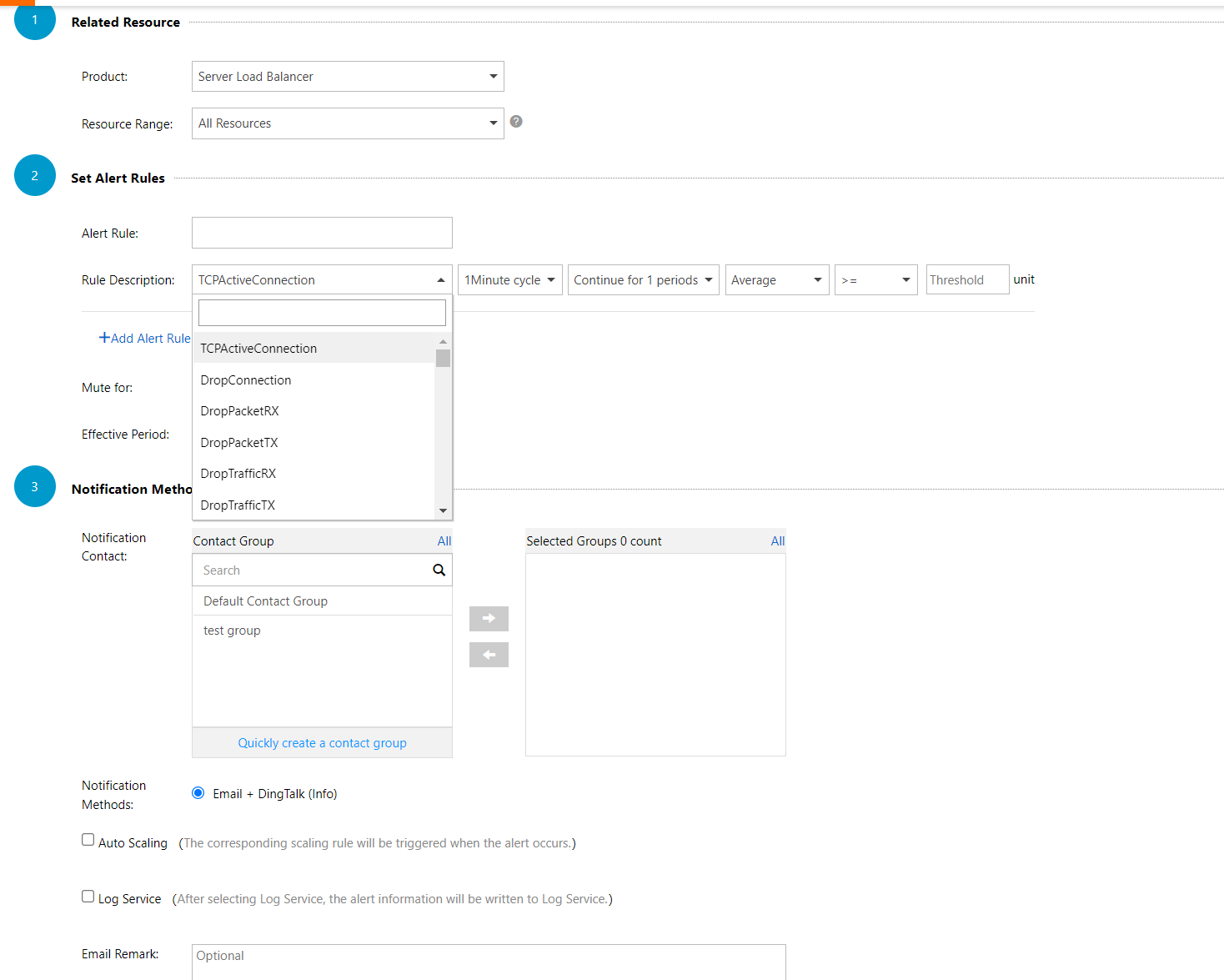
With access and monitoring issues resolved, let's move on to a crucial aspect: logs. Logs have always been critical, with many regulatory requirements specifying clear guidelines for log storage.
Most security operations centers (SOCs) operate by capturing logs from various monitoring points, performing logical analysis, detecting anomalies, and notifying customers.
Therefore, logs are extremely important. Log management consists of two main parts: log storage and log analysis. This section will focus on SLS, though other options such as OSS and NAS can also be used for storage.
You can store logs in a specific Logstore within SLS. This is the simplest and most commonly used method.
For example, a Logstore named application-wenson is created to store application logs.
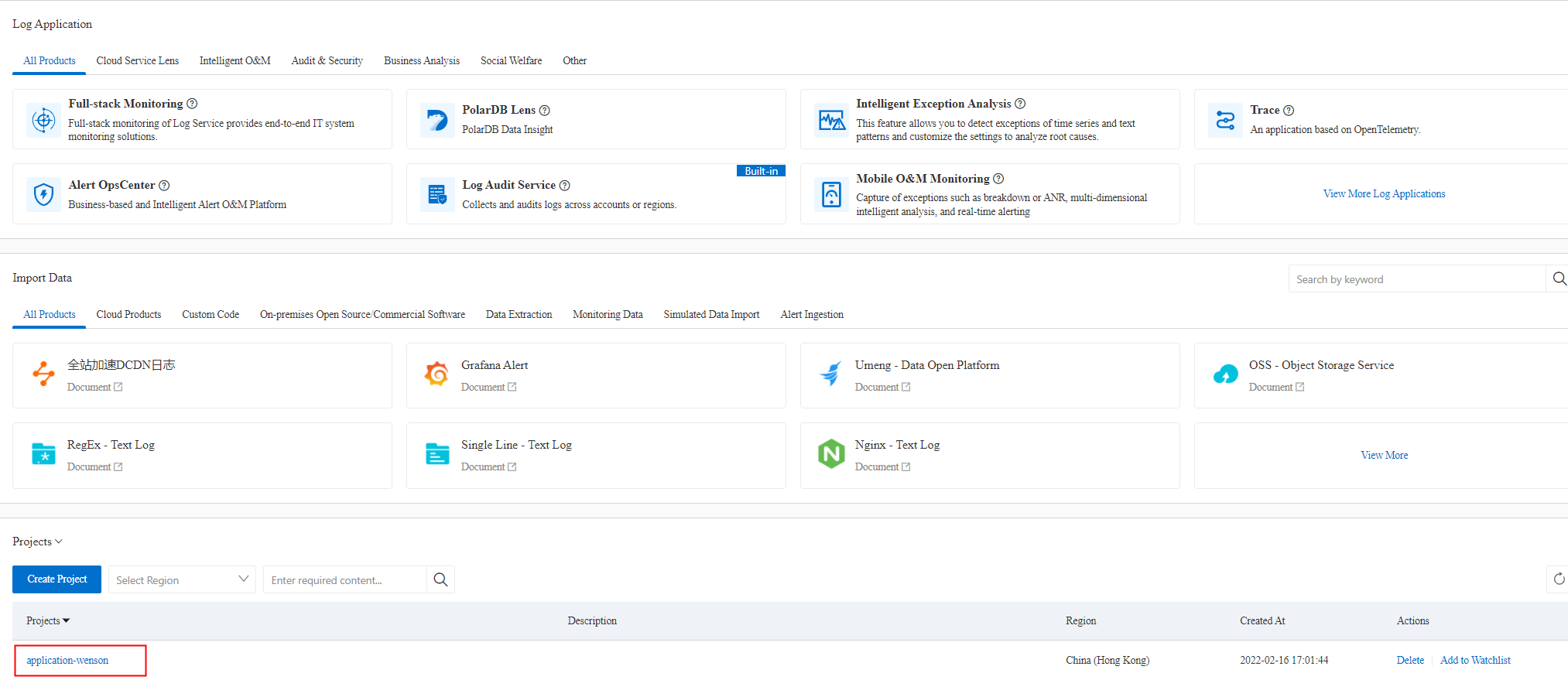
SLS offers many components that allow customers to write custom rules, perform monitoring, and capture logs. It also integrates with big data analysis, providing powerful analytical capabilities. Due to the breadth of this topic, we will not cover all the details here.
Although SLS comes with many default metrics, enterprises often have specific needs. Here is an example of how to set up custom alert rules in SLS.
For instance, no default alert rule is available for newly created users on a bastionhost, but we can create a custom alert rule to detect relevant logs and send notifications:
1. When a new user is created on the bastionhost, you can view the corresponding alert in ActionTrail.
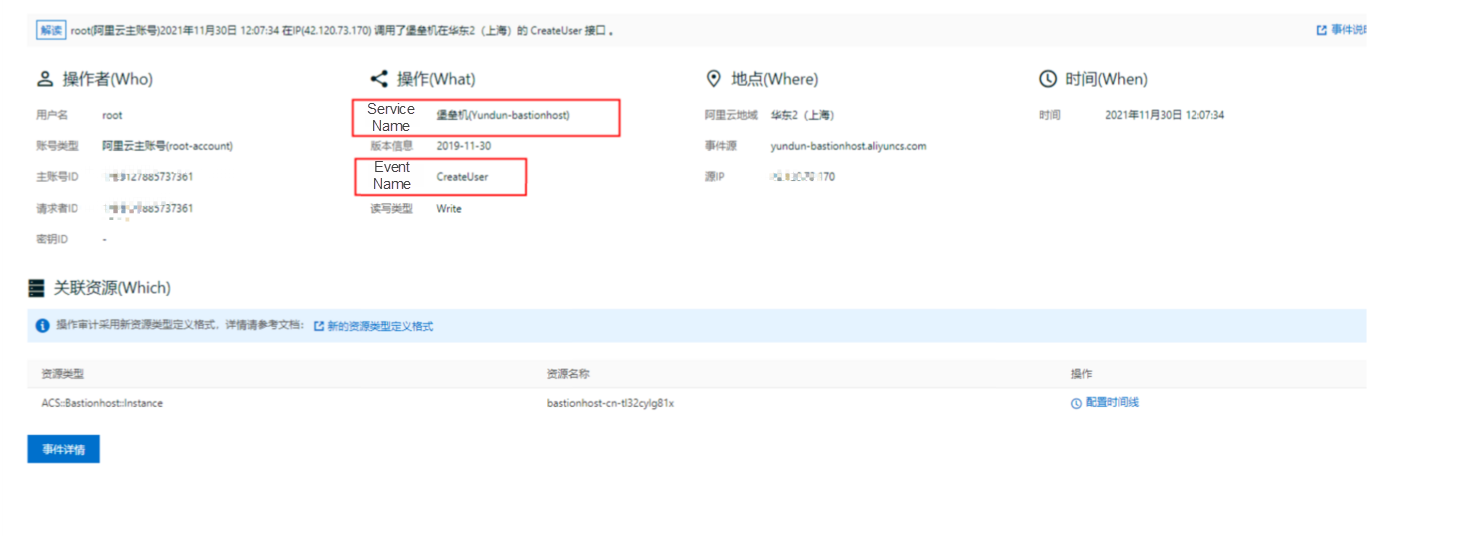
2. Filter the logs in the Logstore for the bastionhost and event type CreateUser, ensuring only the logs for user creation on the bastionhost are visible. The filtering condition is event.eventName: CreateUser and event.eventSource: "yundun-bastionhost.aliyuncs.com".
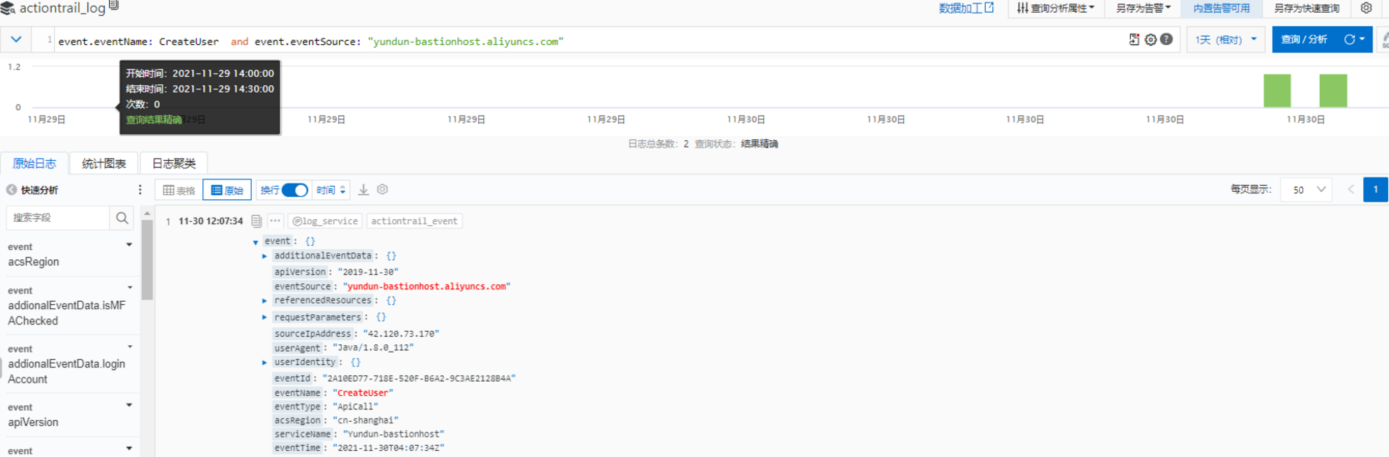
3. Based on this filtering condition, create a custom alert rule. For example, name it "New Bastionhost User Alert" and set the trigger condition to >=1.
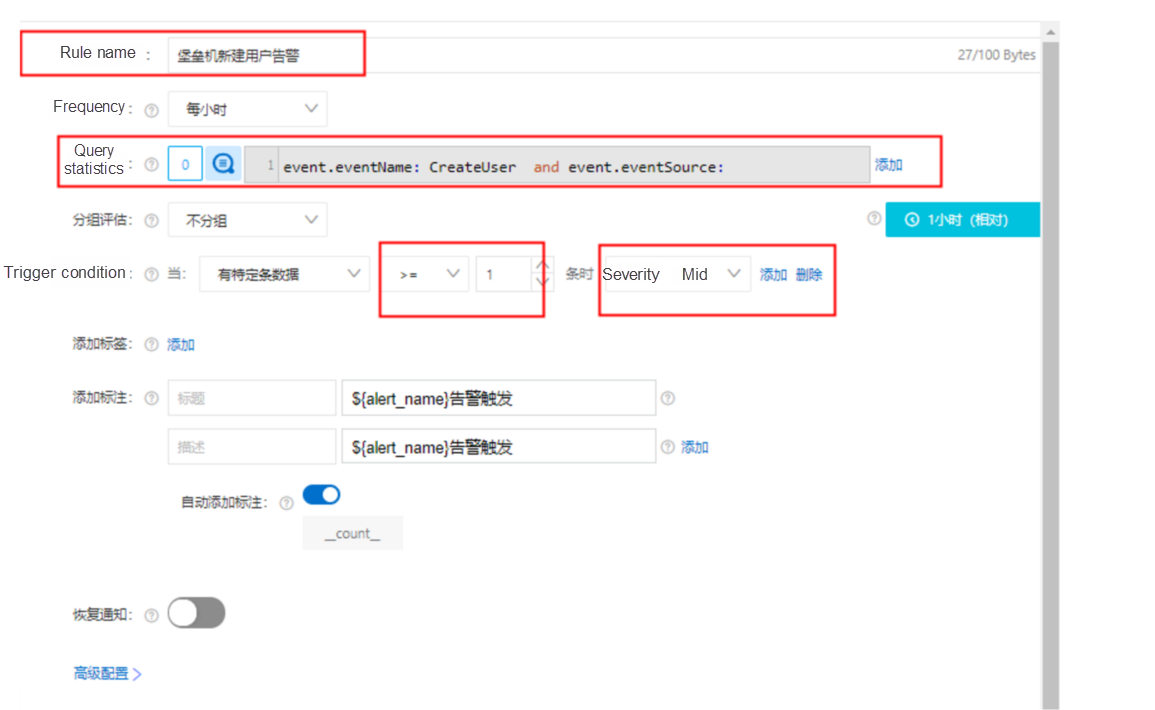
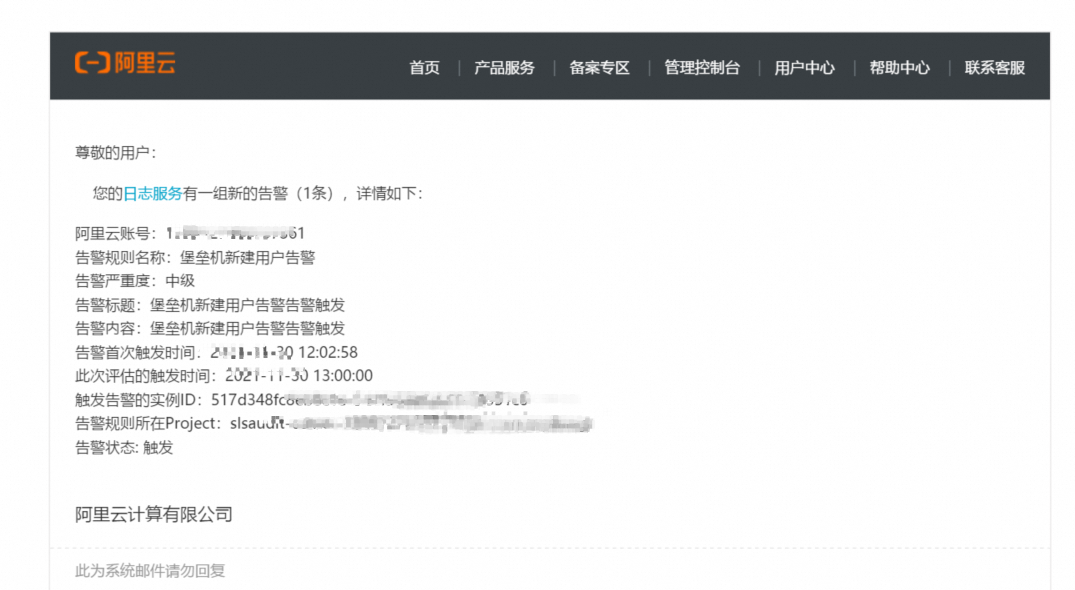
Once the alert rule is configured, you can verify its effectiveness by checking for the corresponding alert notification.
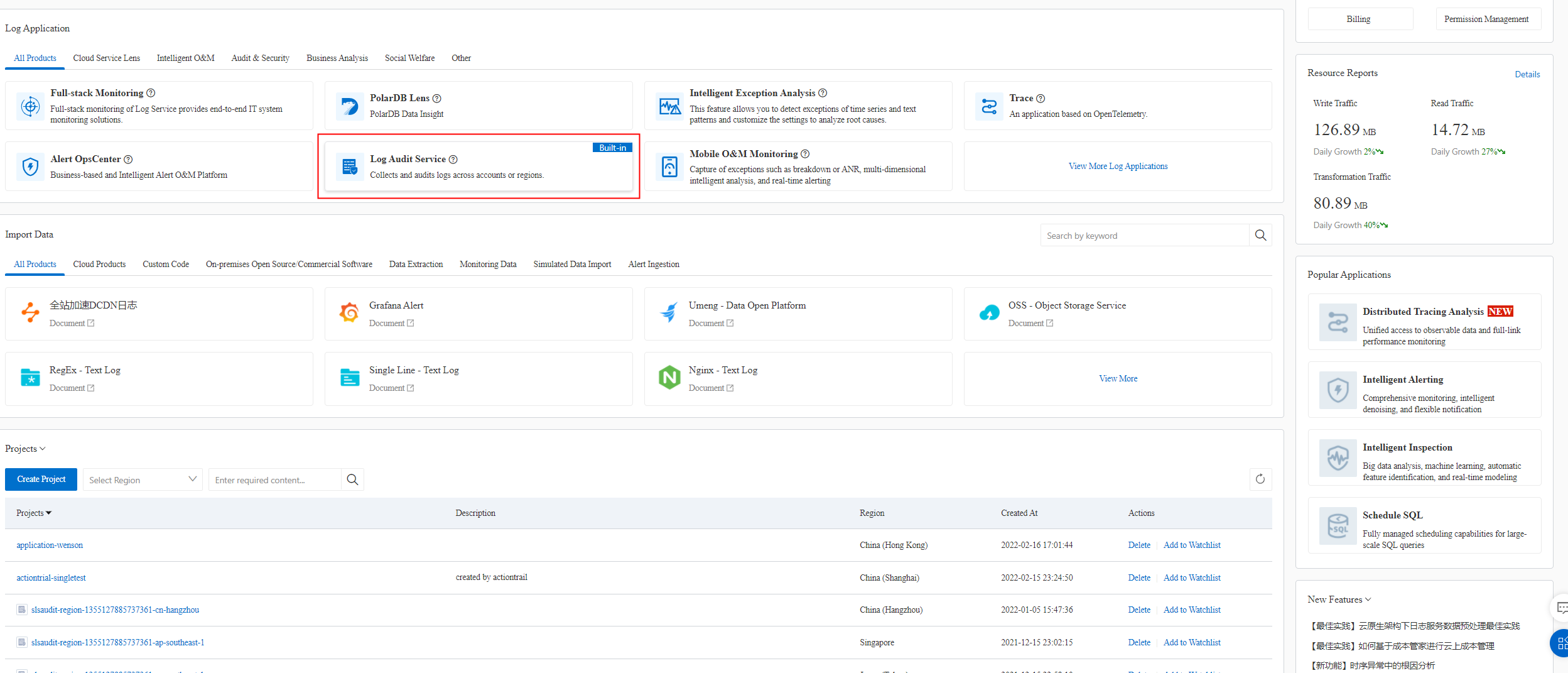
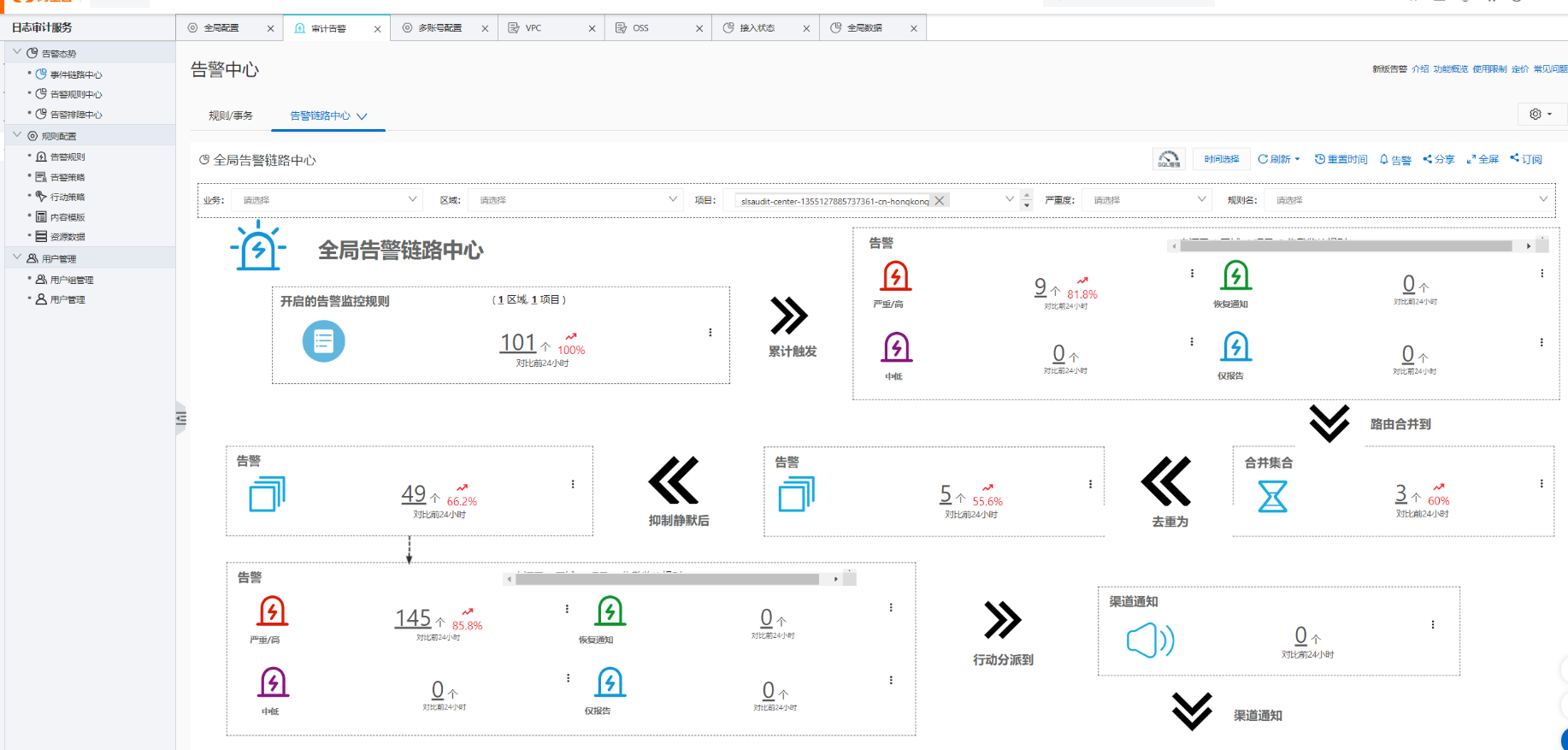
We highly recommend Log Audit Service. It is an excellent tool that can aggregate and audit logs from most of the cloud services you use. (Log Audit Service has its own dedicated Logstore.)
It supports log collection from most cloud services and allows for consolidated collection across multiple accounts. This can address most customer needs.
There is no need for complex configurations—just enable it and start using it.
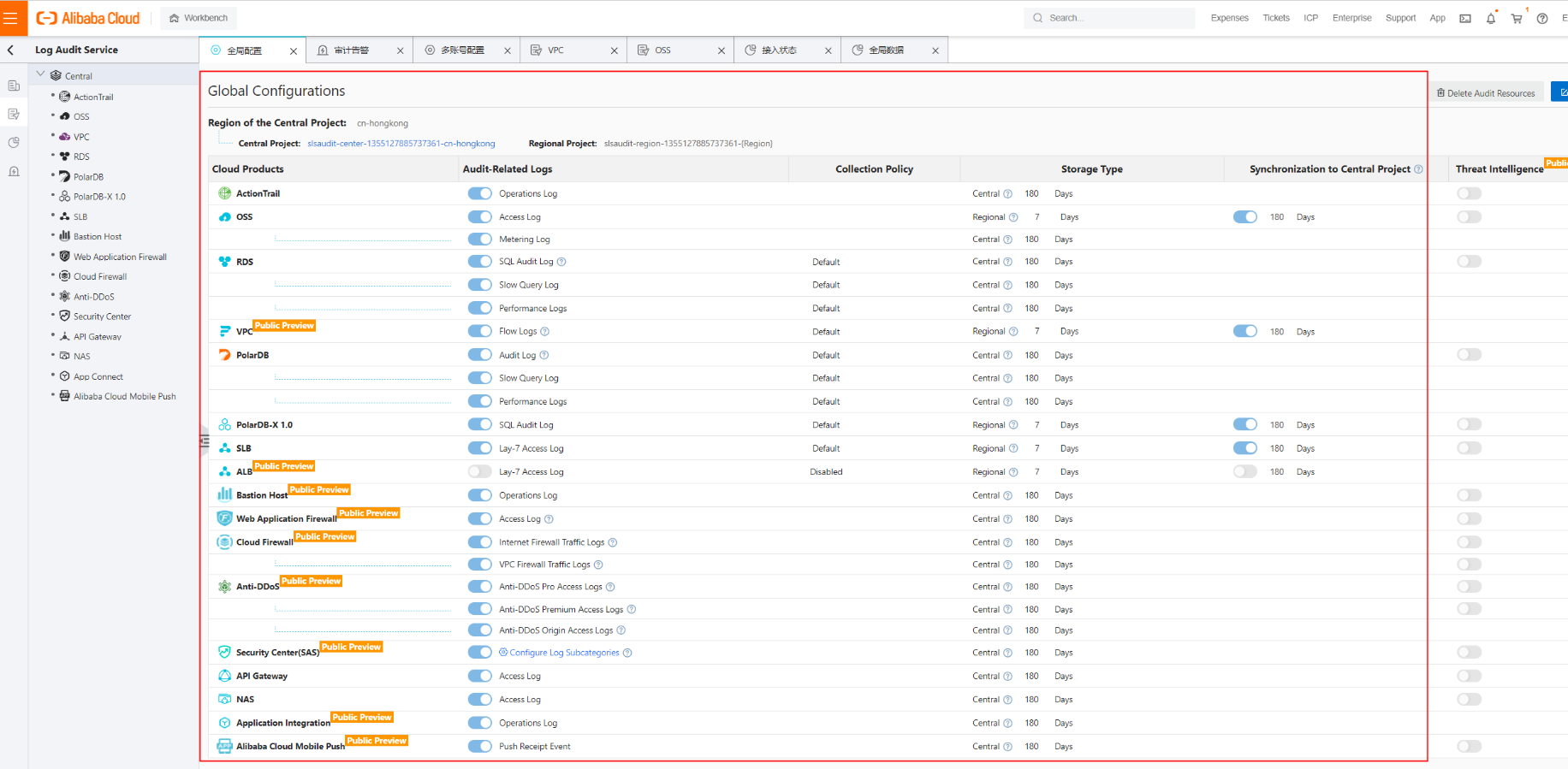
Moreover, Log Audit Service includes many pre-integrated charts and data views.
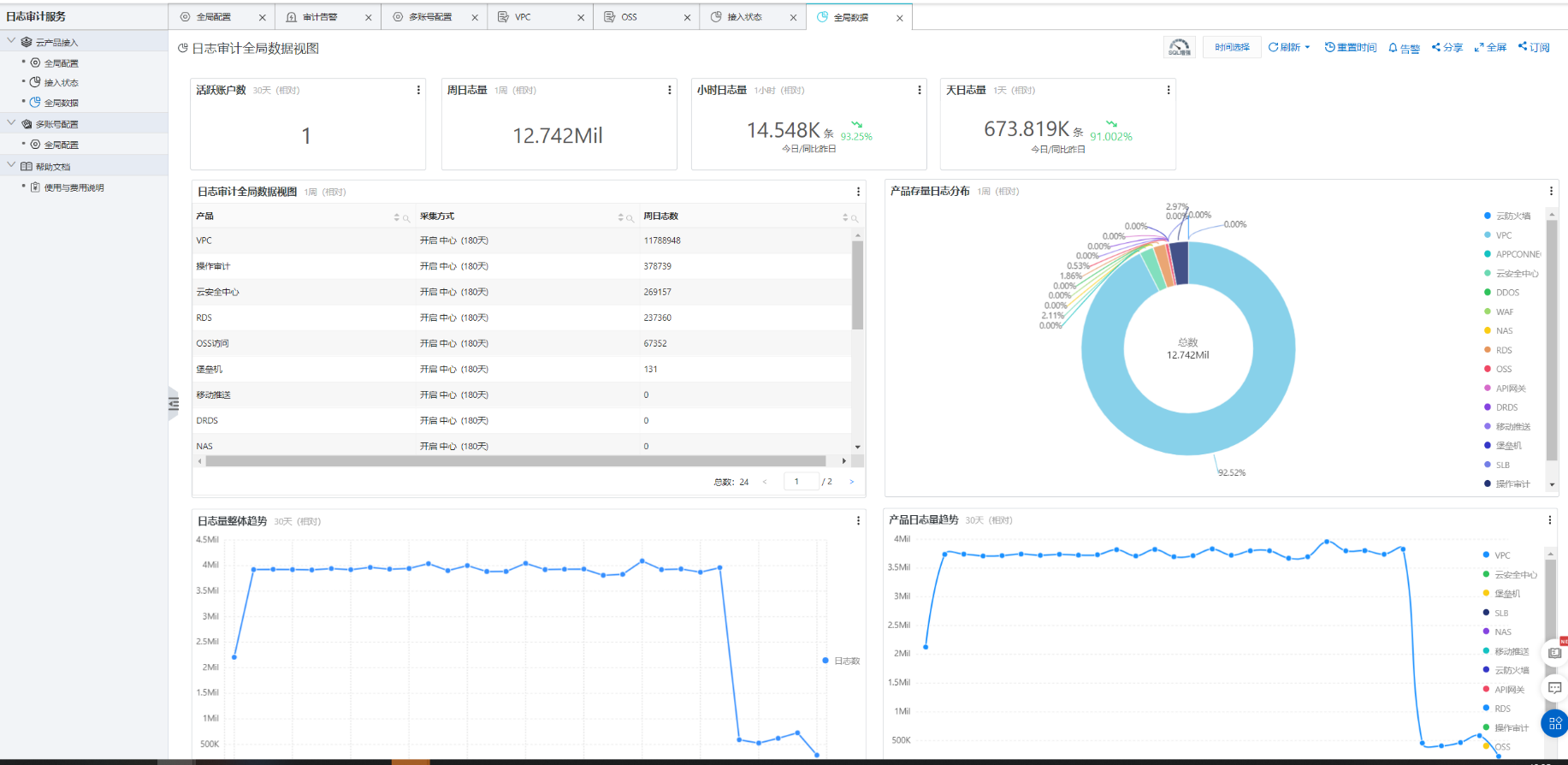
When you configure Log Audit Service for multiple accounts, you can select a resource directory and have all accounts in that directory export their logs to the specified Logstore. You can also specify a number of accounts in the resource directory to export logs to the Logstore.
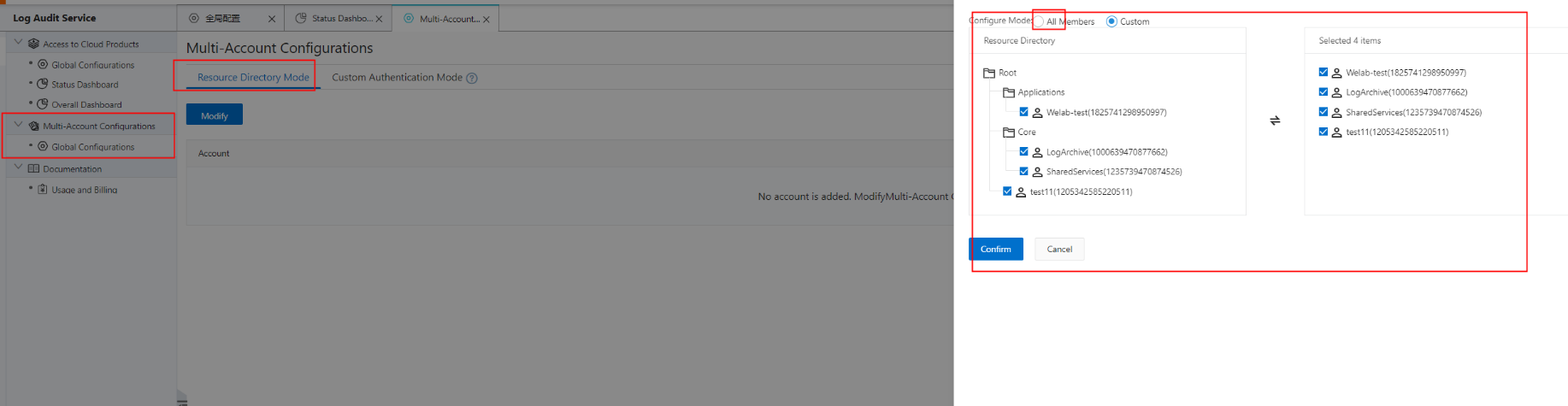
If you have multiple accounts that are not linked to a resource directory, you can still use the custom mode to collect logs across multiple accounts. Simply use an AccessKey pair to collect audit logs from each account.
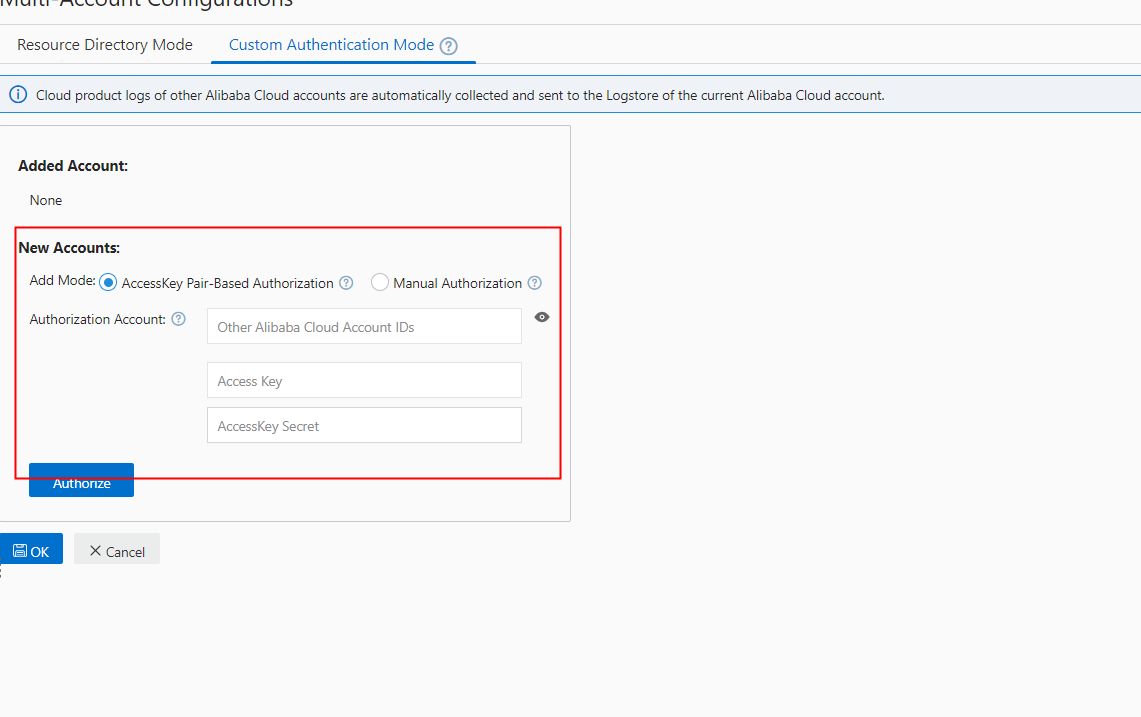
A common issue during daily O&M is when a colleague changes a configuration, and no one else is aware of it. This can lead to confusion and errors later. Since configuration changes are typically considered normal and do not trigger alerts, this can be problematic. Is there a better way to manage this?
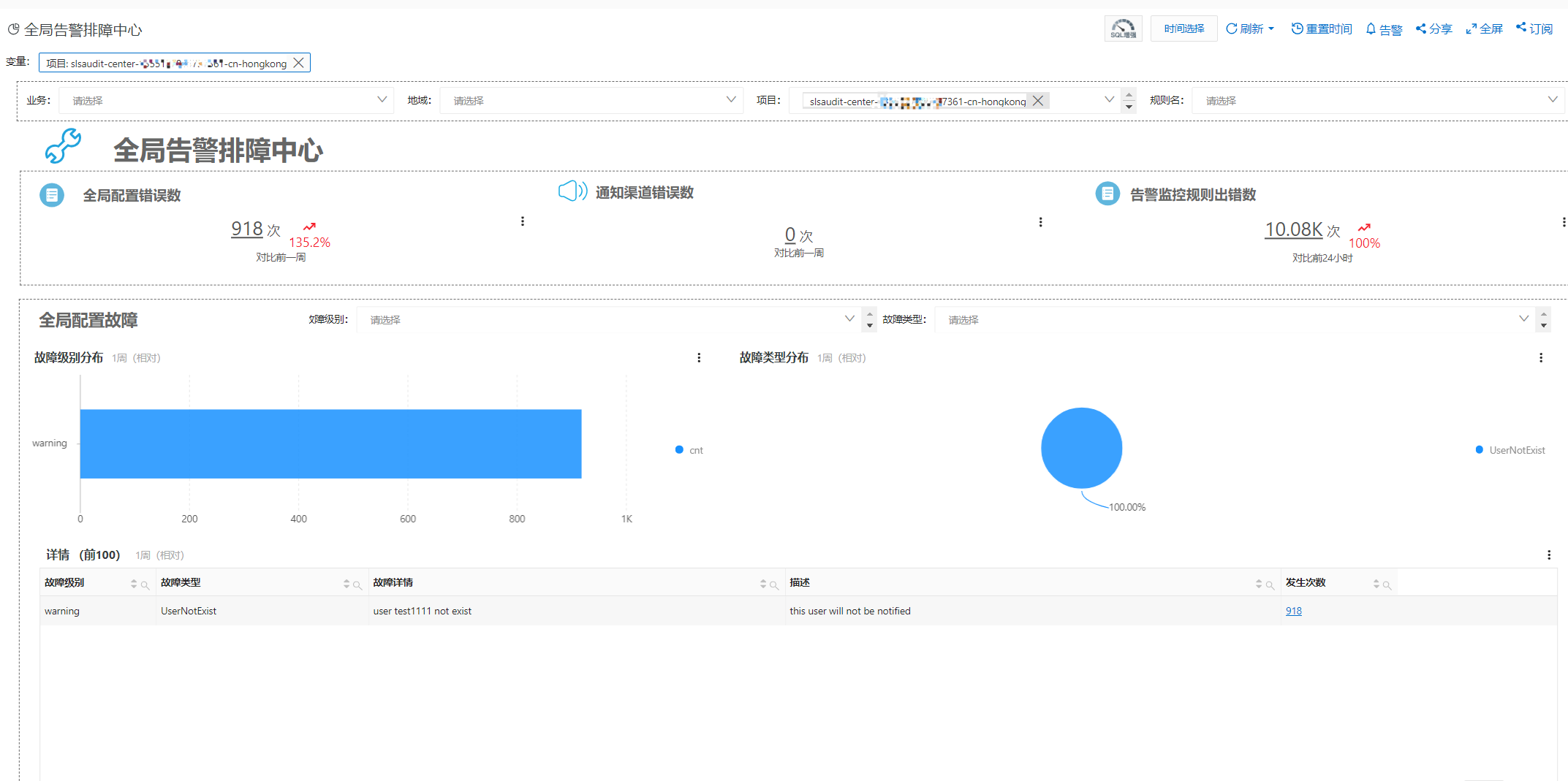
Alibaba Cloud Cloud Config is a resource audit tool that helps track configuration history and ensure compliance. Cloud Config makes it easy to monitor infrastructure, even with many resources. This tool works very well in practice.
Let's introduce how to use Cloud Config.
Compliance Package Creation
First, you need to create a custom compliance package, which consists of a set of rules:
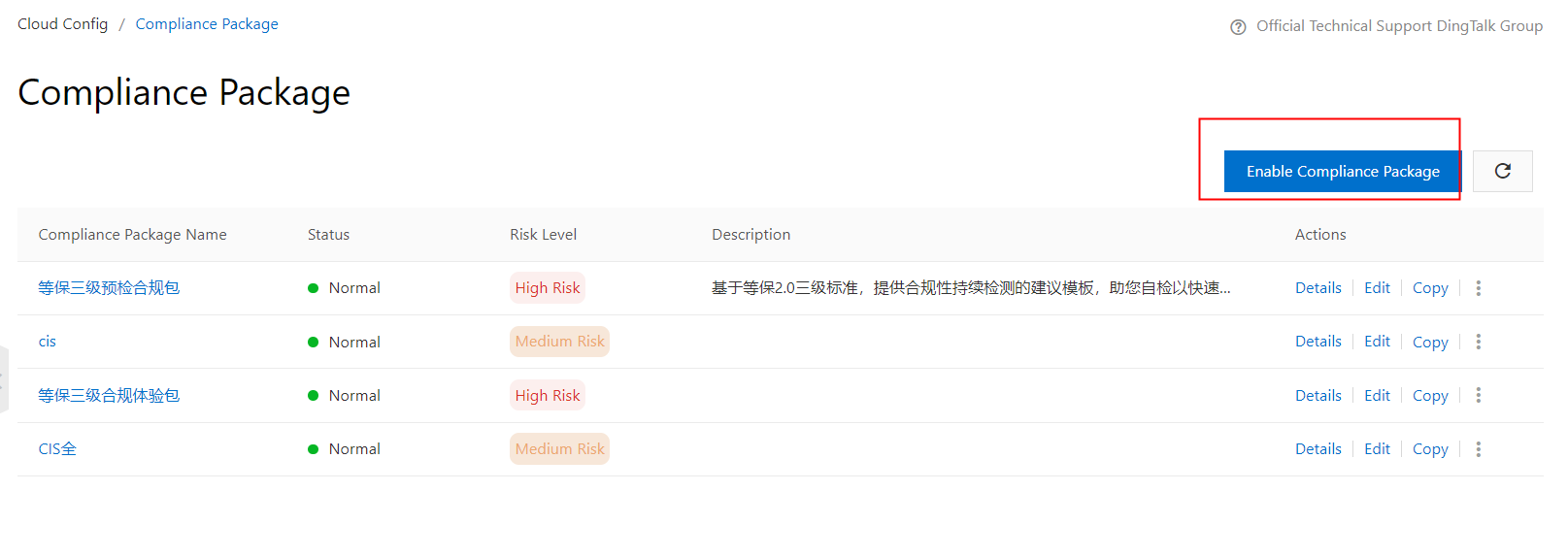
You can define the risk levels and create different combinations of rules. Each rule has its own risk level. When the compliance package is high-risk, it does not mean all the rules are high-risk.
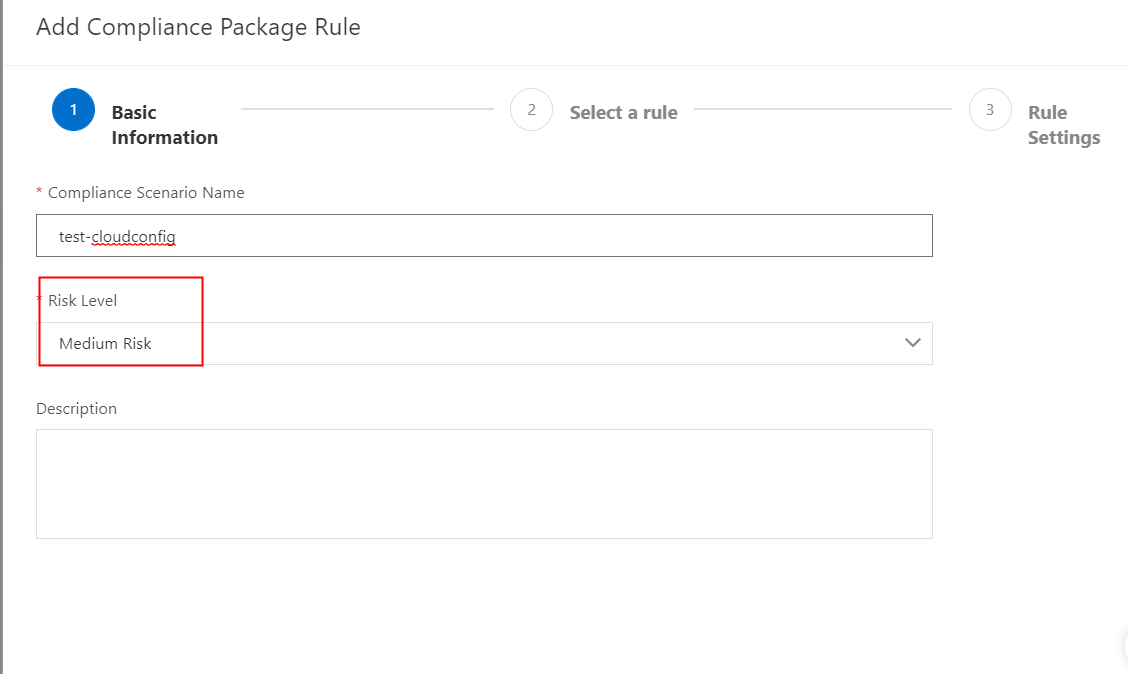
The service offers many pre-defined rules for compliance packages. You do not need to select all rules from a single package. You can choose specific rules from different packages, making it easy to customize to your needs.
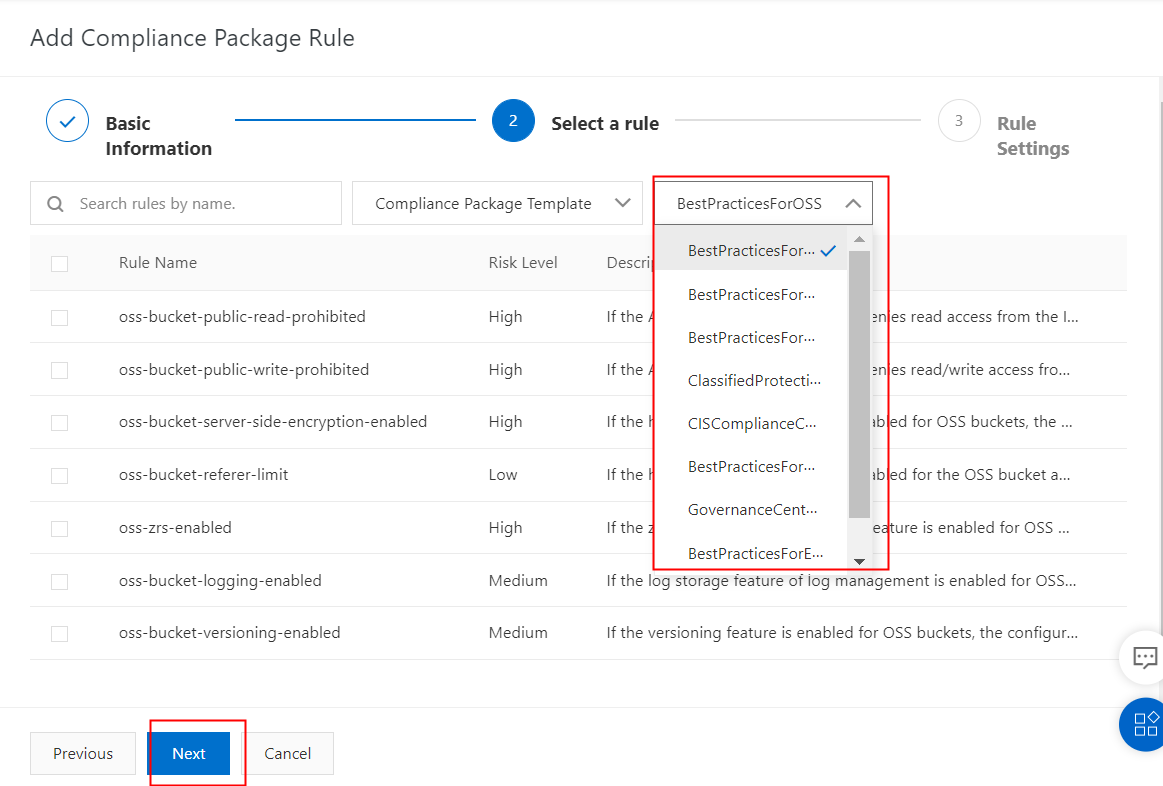
After selecting the rules, you will see a review page where you can adjust parameters such as password length and case sensitivity to meet your company's standards. You can also modify these settings later. In addition, you can set the priority for each rule as high, medium, or low. All these settings have recommended default values.
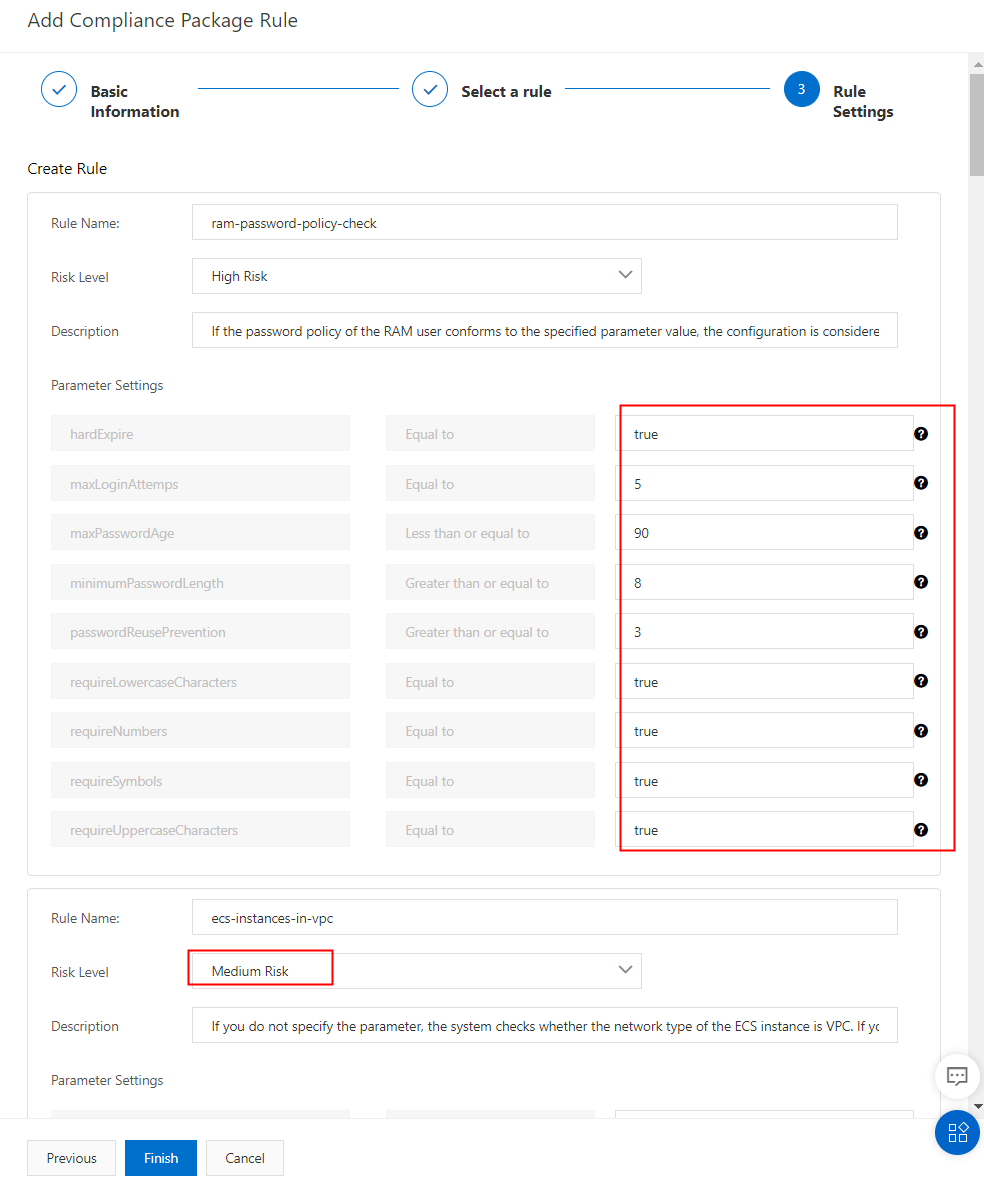
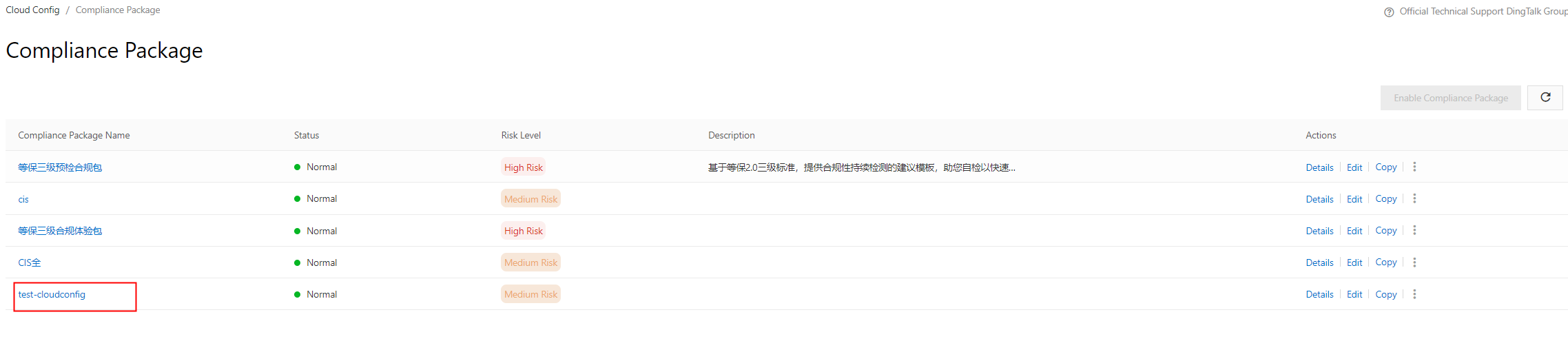
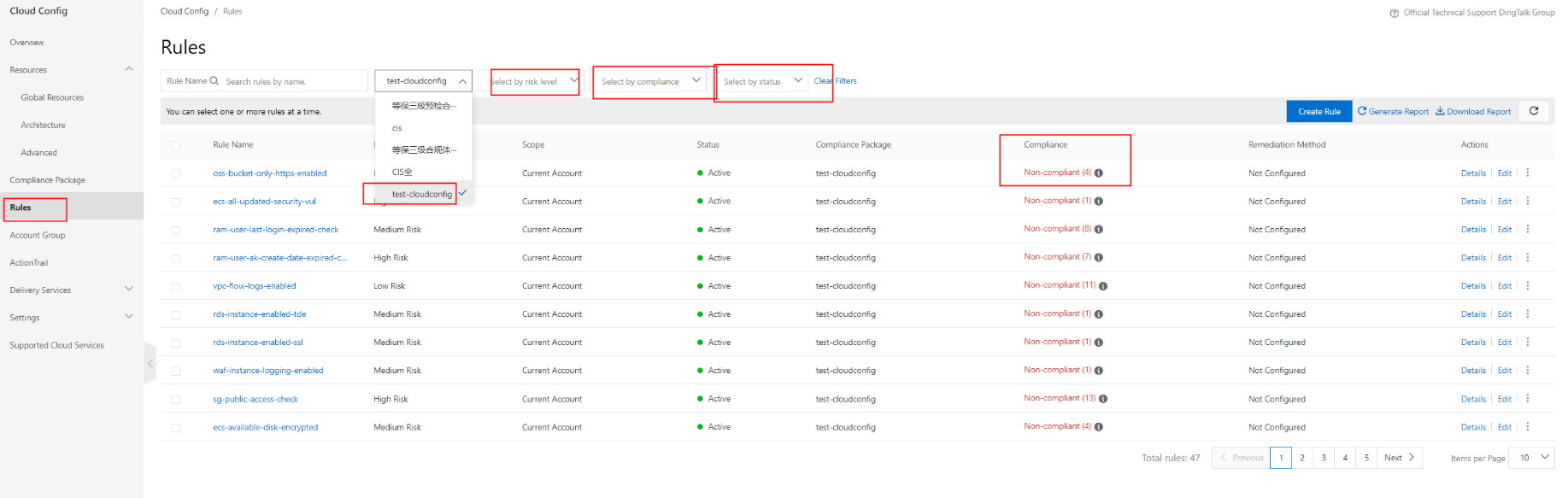
To monitor and detect issues, you can filter compliance packages and associated risks on the Rules page.
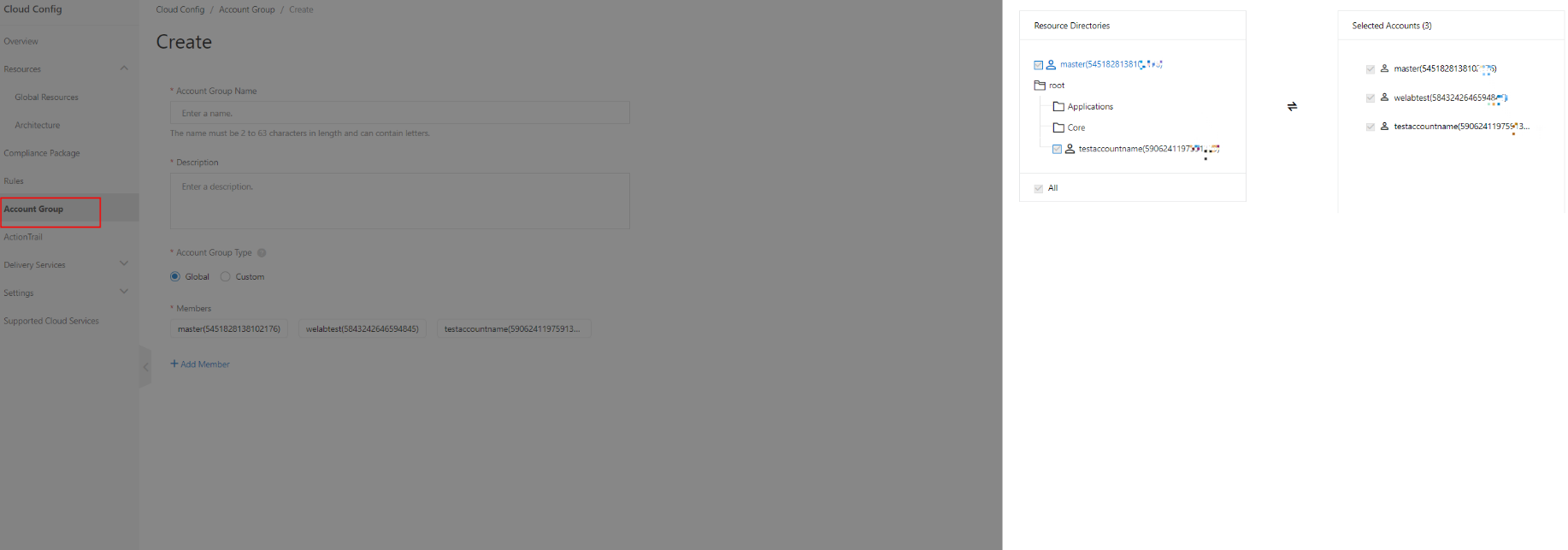
Cloud Config supports settings for multiple accounts within a resource directory.
In the account group, you can create and manage rules for multiple accounts, which is convenient.
Each module includes three common questions that are often of concern. We hope this helps address your queries.
• Are there any other key products for customer access security besides the mentioned access detection?
Yes, these include Resource Access Management (RAM), CloudSSO, and integrated IdP solutions. An access detection mechanism detects and addresses issues while they are happening or after they have already occurred. To prevent issues, we need access control. For RAM account logons, make sure that you assign appropriate permissions in the RAM console. Be specific—avoid giving everyone administrator access, as excessive permissions can have significant negative impacts. If customers use systems such as Azure AD or their own access control systems, we can integrate them as an IdP. Since access control is closely tied to each enterprise's organizational structure, we will not go into detail here.
• Why use a bastionhost when I can set up a Linux server as a jump server for log storage, which is more cost-effective?
While a bastionhost is indeed more expensive, it offers unique benefits. If a jump server you set up is compromised by hackers or malicious internal actions, logs can be deleted or significant damage can be done, making it difficult to trace issues. A bastionhost, with its independent mechanism, ensures secure storage of operation recordings, command execution logs, connection logs, and file transfers. It also includes approval workflows for dangerous commands. These features, unique to SaaS products, are why we recommend using a bastionhost.
• If I follow all the recommendations, am I completely secure?
Unfortunately, no. While we covered the main access methods, real-world usage often involves scenarios requiring interaction with the Internet, such as ECS with elastic IP addresses (EIPs), which allow direct access. This necessitates careful configuration of network ACLs and cross-access permissions. For example, an OSS bucket used for uploading reimbursement invoices may require public access to allow employees to submit from anywhere.
All public-facing services, such as EIPs, external database interfaces, and OSS public links, must be configured and controlled strictly according to need. Unnecessary public access should be avoided.
We recommend keeping a separate file to manage and control permissions for all public-facing service ports and links.
• Are there any important points to consider when using CloudMonitor on the international site (alibabacloud.com)?
Yes, the international site sends alert notifications via email and DingTalk. Notifications via SMS and phone calls are not supported in all countries. Therefore, we recommend installing the DingTalk app to receive the latest monitoring notifications promptly.
• If I use all the services provided by CloudMonitor, can I be completely worry-free?
Not exactly. CloudMonitor monitors the stability of Alibaba Cloud services from a product and infrastructure perspective. You still need to pay close attention to application-specific monitoring, depending on the nature of your application. Alibaba Cloud offers Application Real-Time Monitoring Service (ARMS) for comprehensive application monitoring, which includes proactive monitoring, application performance monitoring, and mobile performance monitoring.
• If I use SLS, do I still need to integrate a third-party SOC for enhanced operations monitoring?
In most cases, SLS is sufficient for your needs, and there is no need to integrate a third-party SOC. SLS provides alert notifications to inform you of any issues. The most valuable part of a SOC is its analysis model. A SOC is only necessary when you have a specialized application requiring in-depth monitoring with complex rules that are hard to manage. In other situations, you can configure these rules directly in SLS.
• Since Log Audit Service has its own dedicated Logstore, how are the costs calculated?
Log Audit Service does have its own dedicated Logstore. It essentially duplicates the product's output logs into the Log Audit Service Logstore for analysis. This means the same log is stored in two different Logstores within your SLS, providing redundancy. The cost is calculated according to the standard billing logic of SLS.
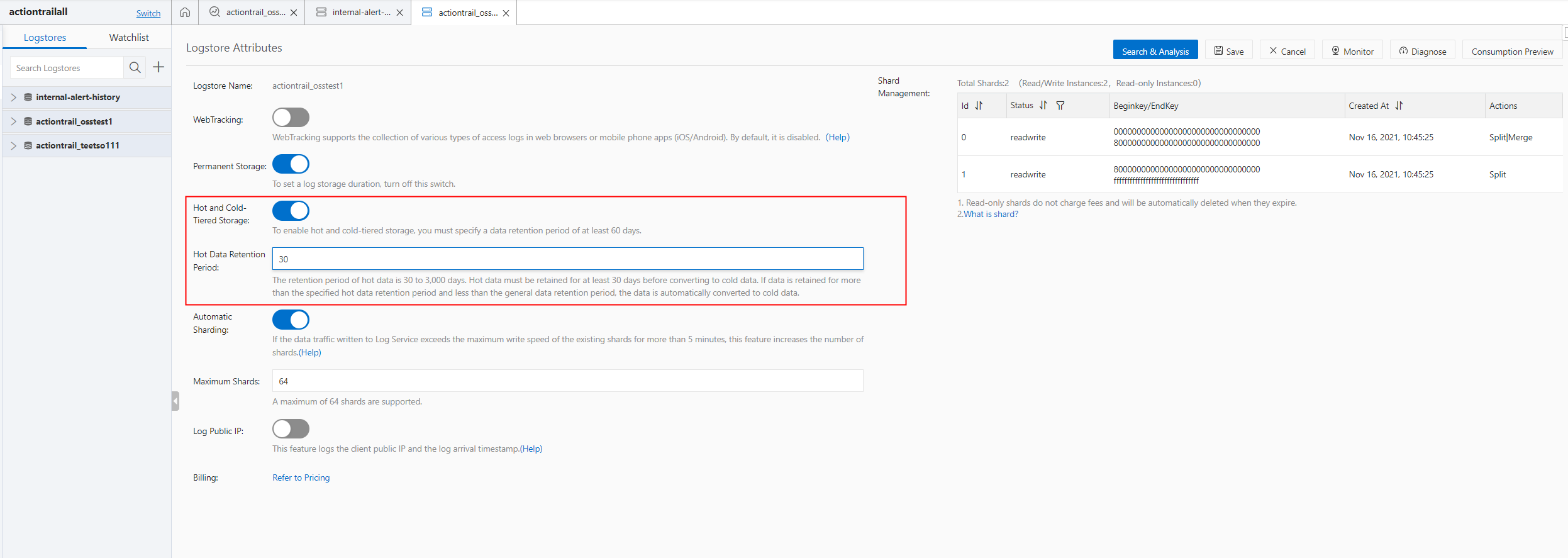
• What is the detection mechanism of Cloud Config, and how often does it detect anomalies?
There are a few types of detection mechanisms, which are detailed in the specific detection rules of Cloud Config. For example, changes in RAM permissions can be synchronized immediately. Most resources are synchronized every 10-15 minutes, while some configurations are checked periodically, The longest period seen at present is only 24 hours.
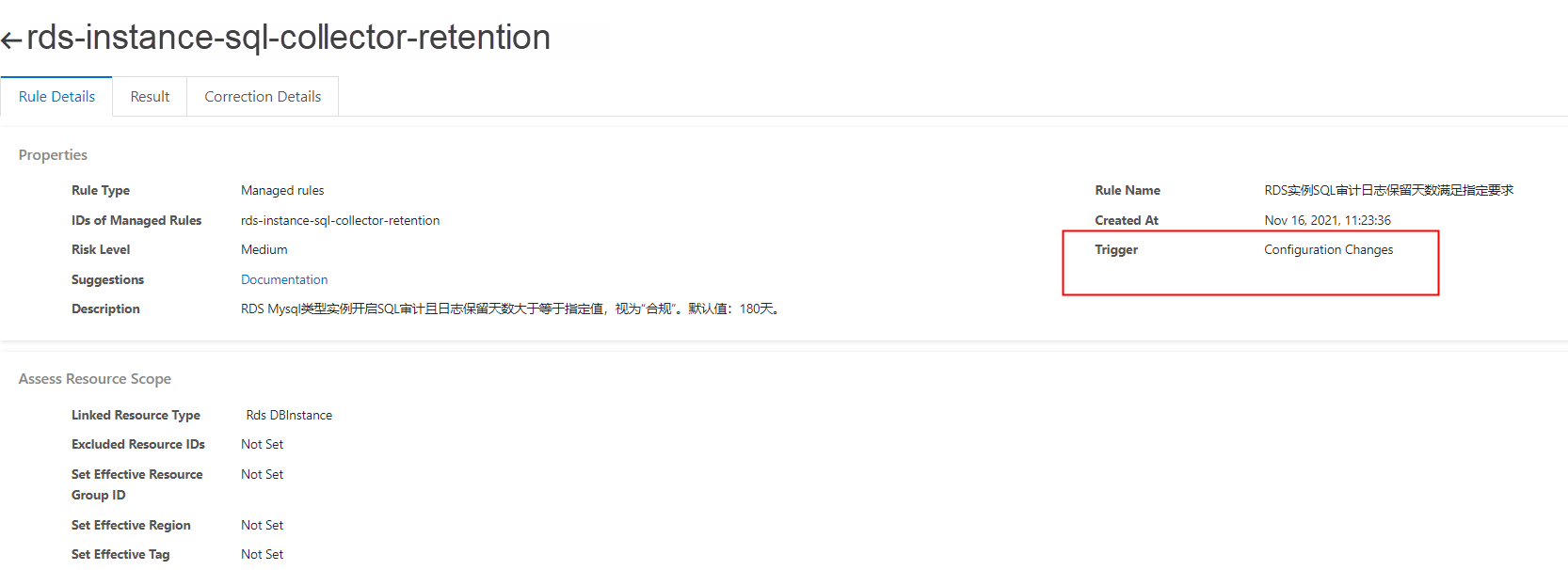
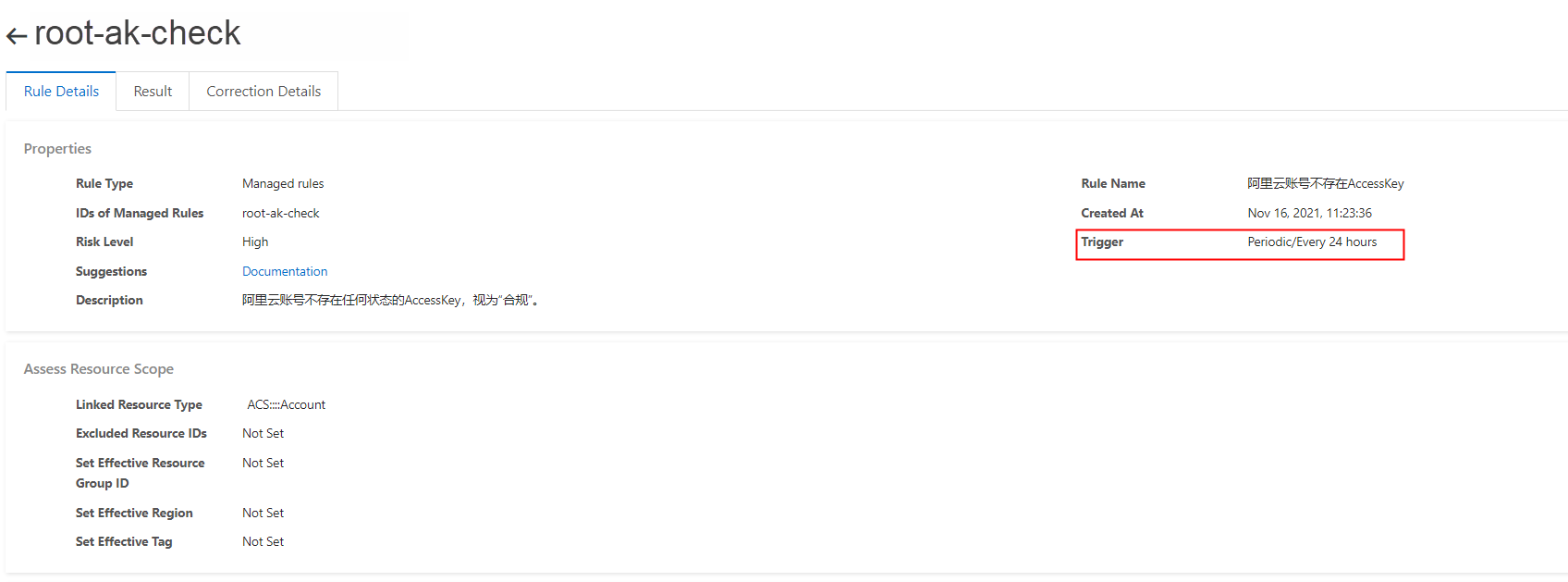
• How does Cloud Config notify customers, and how are alerts triggered?
Cloud Config is primarily managed via the console. The product itself does not have a built-in mechanism for external alerts. However, you can export relevant data to SLS, which can then trigger alerts.
• If I enable the default compliance packages in Cloud Config and no issues are found, does that mean I am compliant with the standards?
Not necessarily. First, compliance standards are multi-dimensional and comprehensive. Cloud Config focuses on detecting configuration issues, but full compliance requires considering other factors as well. Second, the product provides default rules to facilitate usage, but these may not cover every aspect of the compliance standards. Some requirements need to be assessed based on specific user information and cannot be solely achieved with the product. Therefore, collaboration is necessary to ensure full compliance.
• Why is this titled as operations monitoring for the international site? Is it the same for the China site, and what are the differences?
The title focuses on the international site because I work in international services, and this guide is based on services supported by the international site. However, all the products and features mentioned are fully supported by the China site as well. You can use them with confidence. The China site may also have additional new products and features that are not yet available on the international site. We appreciate your support for the international site and look forward to more new products and features being available on the international site as soon as possible.
Disclaimer: The views expressed herein are for reference only and don't necessarily represent the official views of Alibaba Cloud.
Alibaba Cloud Launches Open-Source Math LLMs that Can Solve Complex Math Problems

1,347 posts | 477 followers
FollowAlibaba Cloud Community - August 30, 2024
CloudSecurity - December 8, 2025
Kidd Ip - May 29, 2025
Kidd Ip - September 22, 2025
Alibaba Clouder - November 28, 2018
ApsaraDB - October 24, 2025

1,347 posts | 477 followers
Follow Security Center
Security Center
A unified security management system that identifies, analyzes, and notifies you of security threats in real time
Learn More Security Solution
Security Solution
Alibaba Cloud is committed to safeguarding the cloud security for every business.
Learn More Data Security on the Cloud Solution
Data Security on the Cloud Solution
This solution helps you easily build a robust data security framework to safeguard your data assets throughout the data security lifecycle with ensured confidentiality, integrity, and availability of your data.
Learn More Security Overview
Security Overview
Simple, secure, and intelligent services.
Learn MoreMore Posts by Alibaba Cloud Community