Get Fortinet FortiGate on Alibaba Cloud by visiting our Marketplace:
Fortinet FortiGate (PAYG) Next-Generation Firewall (4 vCPUs)
Fortinet FortiGate (PAYG) Next-Generation Firewall (8 vCPUs)
In this 3-part article series, we will show you in detail the steps for deploying and configuring Fortinet FortiGate (FGT) A-P High Availability (HA) on Alibaba Cloud between availability zones (AZ).
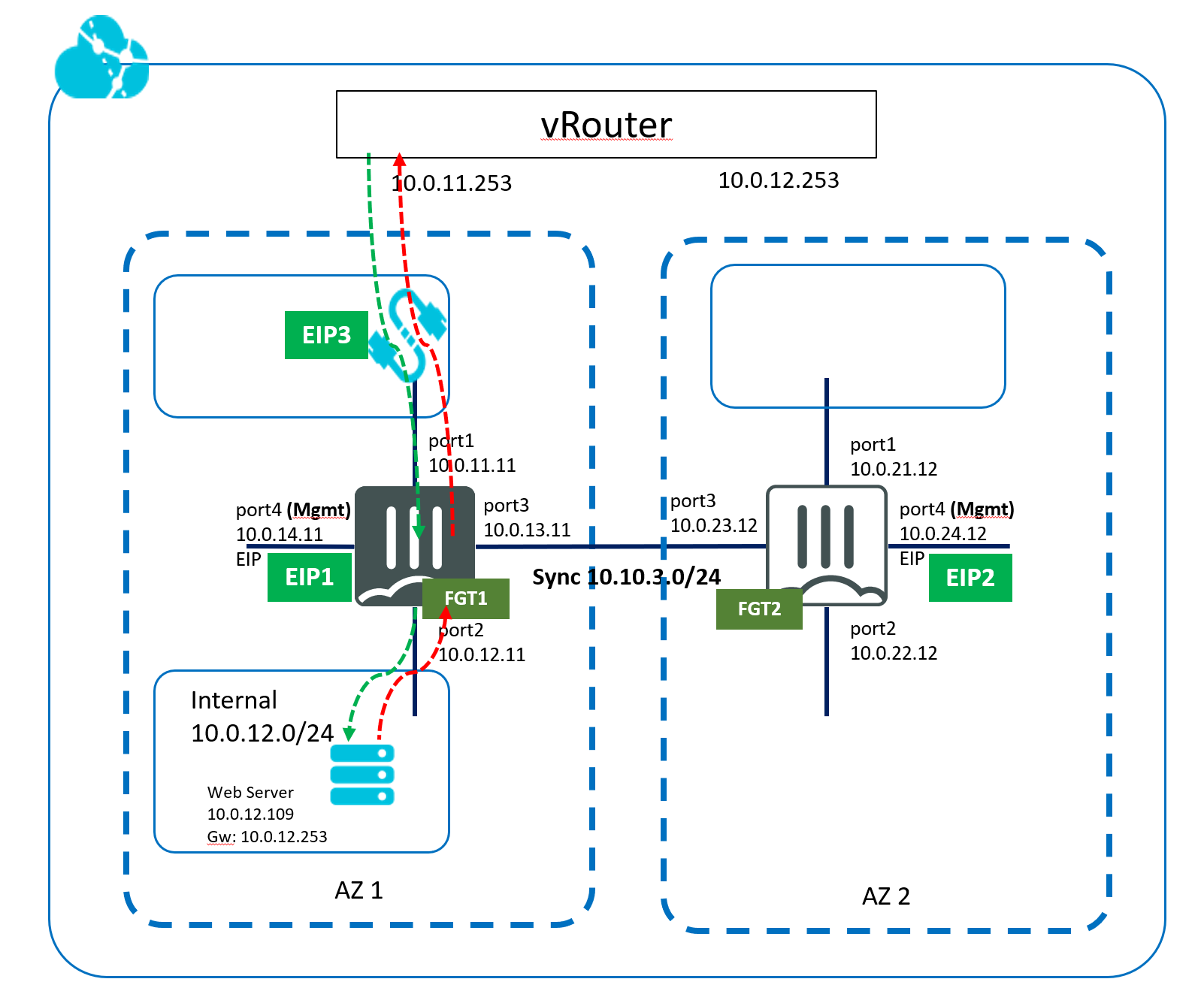
In our setup, two FGT are in different AZ zones but in a single Region. On the left, FGT1, is Master as it is configured with a higher priority. On the right, FGT2, is slave (passive) and not forwarding any client traffic.
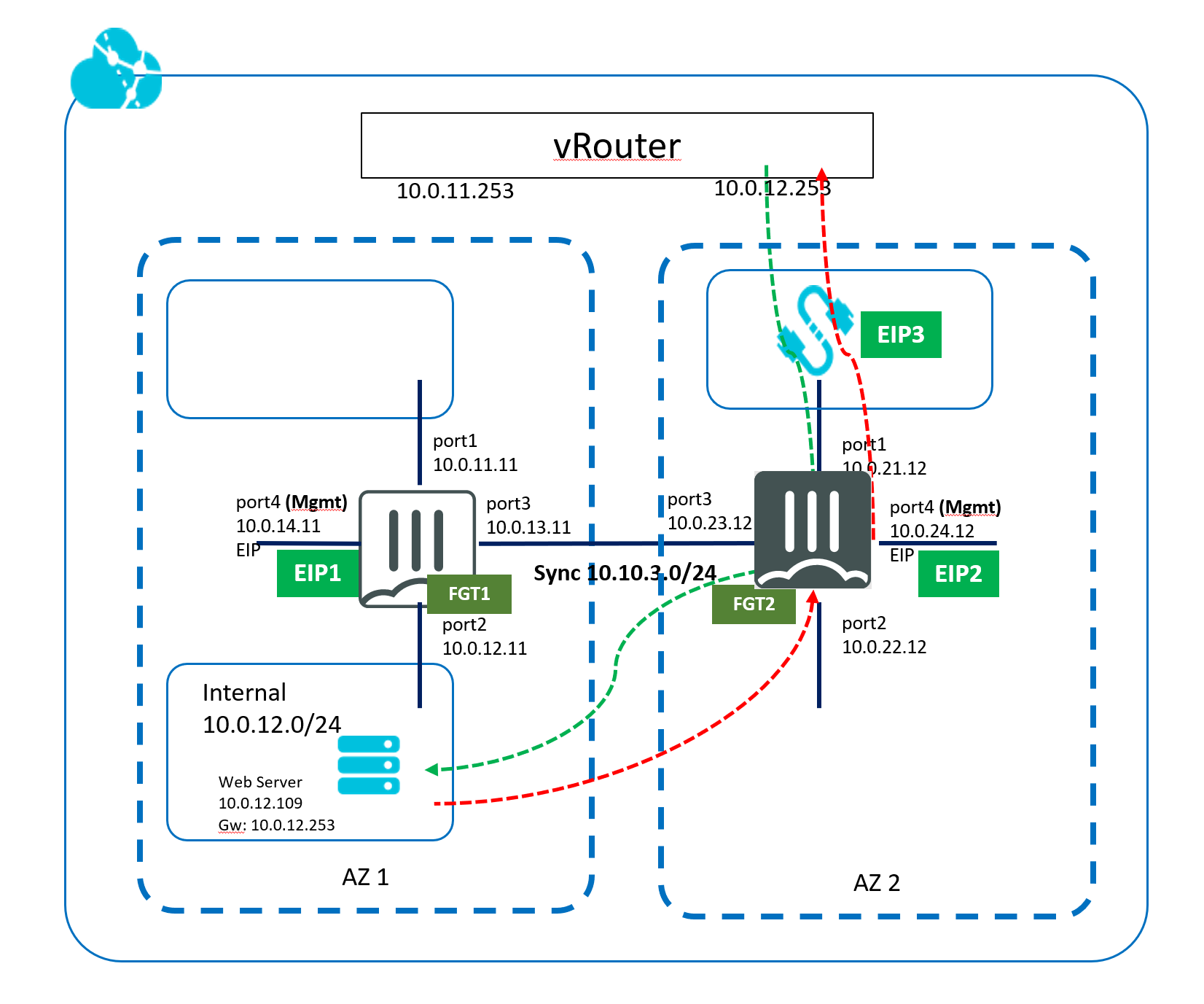
Both FGTs are in an HA Cluster with unicast heartbeat messages via port3. For whatever reason, if Heartbeat messages is not received from peer, FGT2 will assume master role, and associate itself with EIP3 and change VPC default route to 10.0.22.12 for vswitch internal to new Master.
A Web Server with IP (10.0.12.109) represents protected traffic in AZ1. When FGT2 becomes master, web server will use FGT2 for traffic in/out.
Here is a list of items needed before proceeding with the configuration.
You'll need two Fortigate BYOL Licenses. You can contact alisales@fortinet.com to apply for a license. Once you have the licenses, Activate your BYOL license at support.fortinet.com to register your license, and download the license file.
You should have an Alibaba Cloud account, or access to one through a RAM account. You can create a free account at https://www.alibabacloud.com/campaign/free-trial
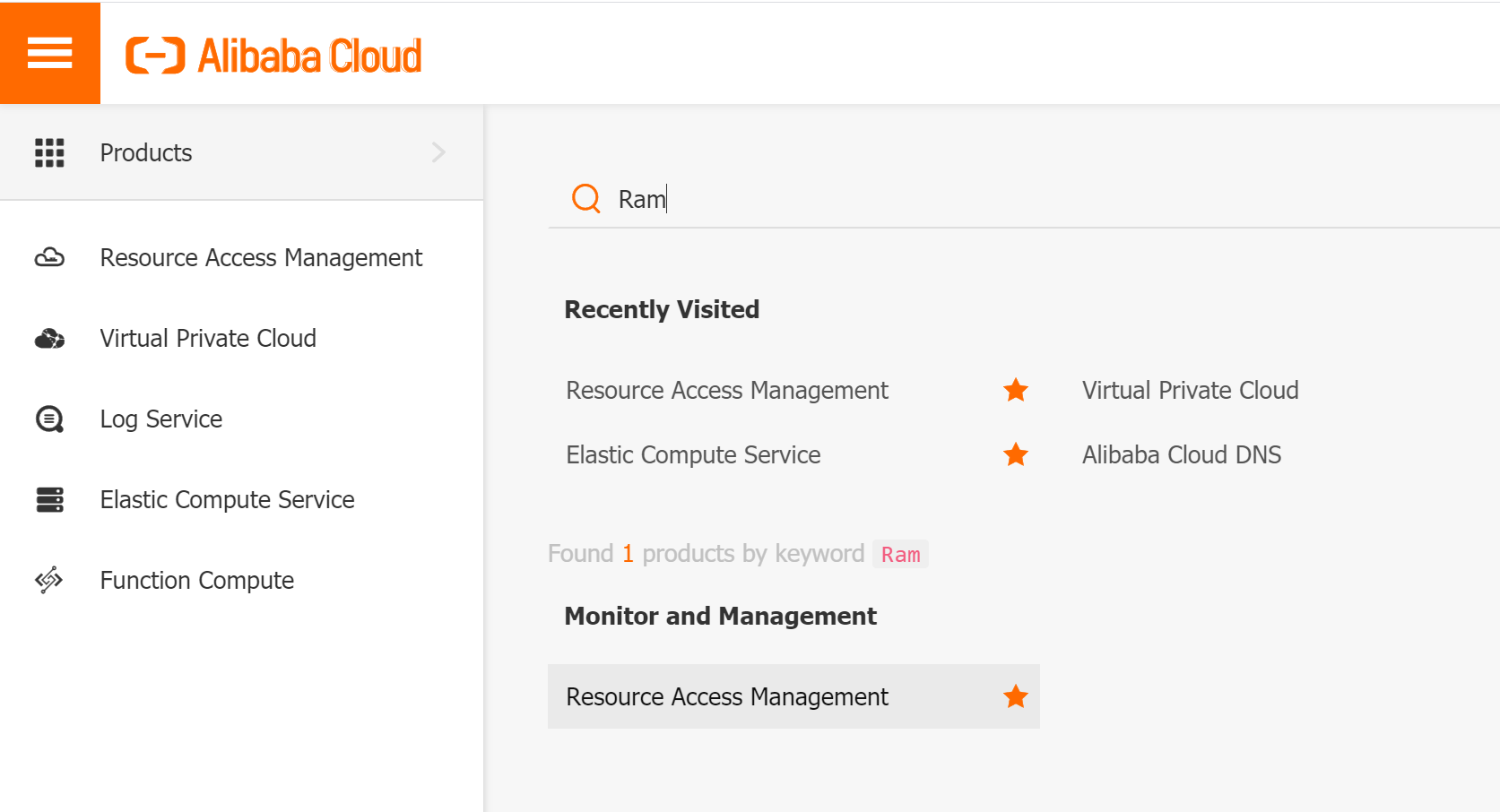
If you are accessing through a RAM account, you should have at least AliyunVPCFullAccess, AliyunECSFullAccess, AliyunRAMFullAccess, AliyunEIPFullAccess privileges.
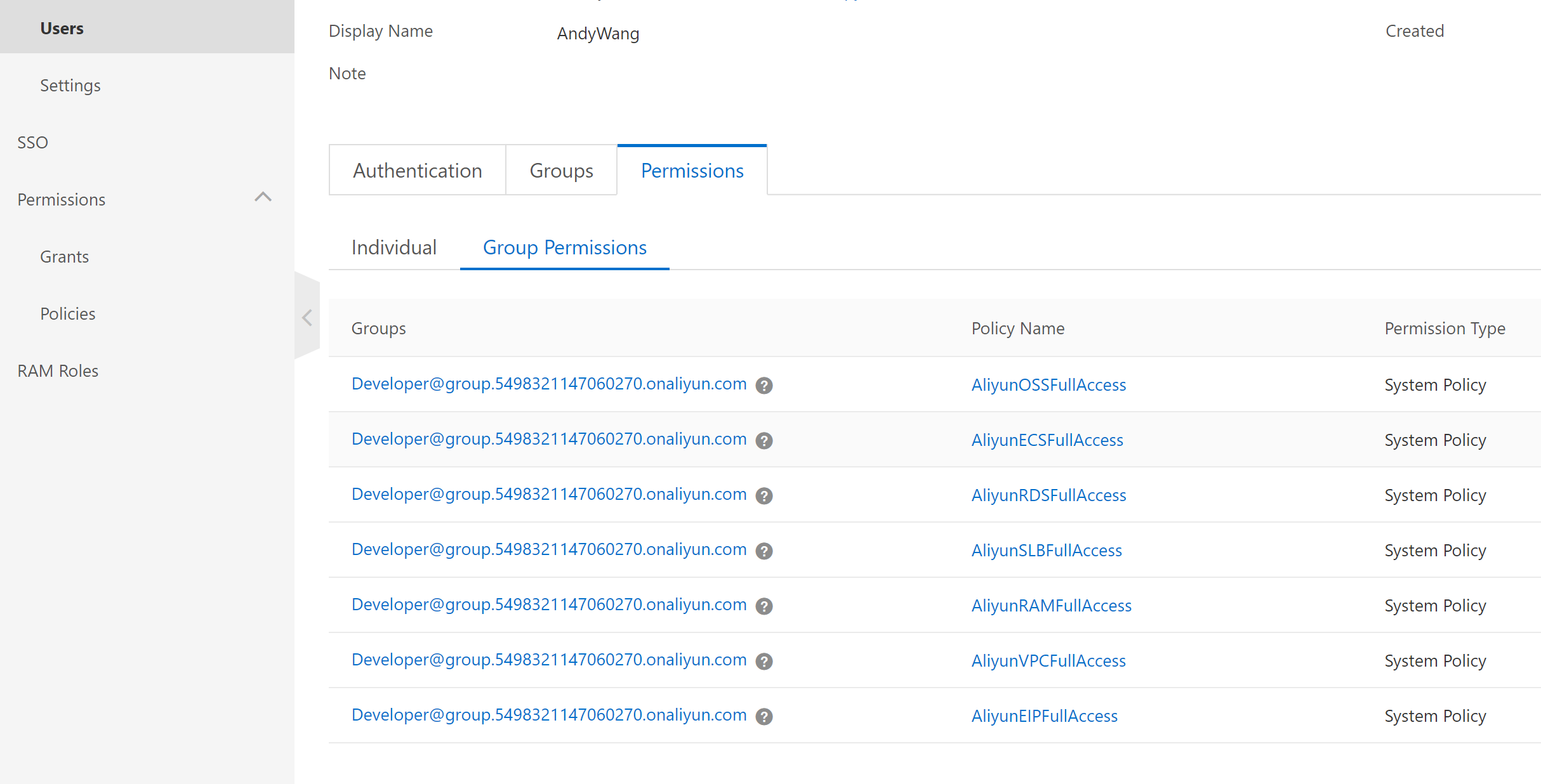

Generate your Access/Secret Combination if you want to use terraform or aliyuncli to deploy/manage resources. For example, you can use terraform script to provision all resource by using https://github.com/yagosys/fortigate_aliyun/tree/master/AP-CrossZone
You can also use Aliyun GUI to deploy the resource.
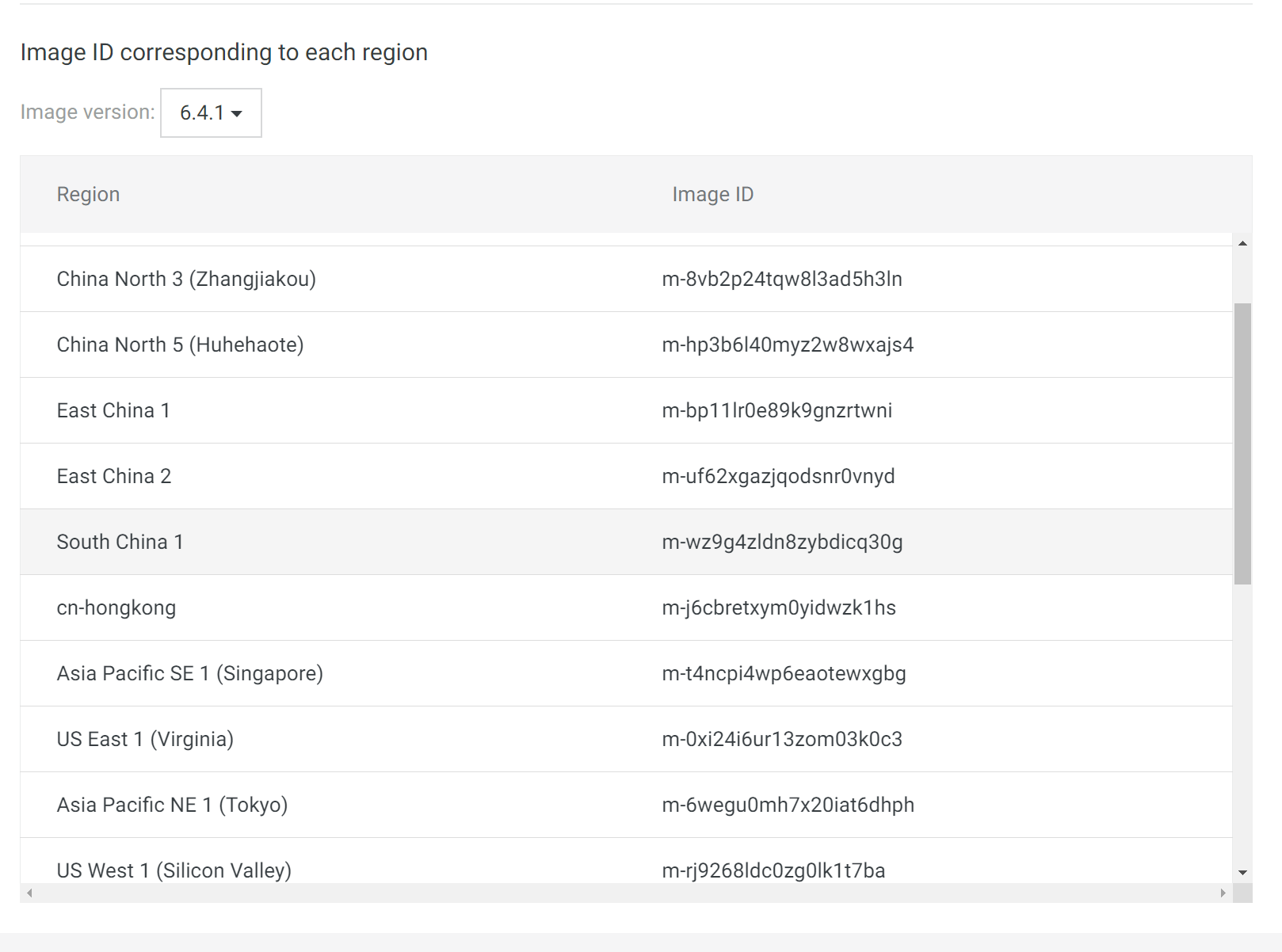
Find Fortigate image from the Alibaba Cloud Marketplace and locate Fortigate images.
Write down the region id and image id if you use terraform or cli to provision resource.
Alibaba Cloud does not always have the same computer instance in different AZ zones. So you have to check which AZ zone has the computer instance type you needed. If you are using the GUI, you can use it to select the AZ zone, but if you use CLI or terraform, you need to find the AZ zone for the InstanceType.
You can also use aliyun cli to get region id and also the availability zone for the required instance type. To run Fortigate A-P, you will need an instance that able to support at least 4 NICs.
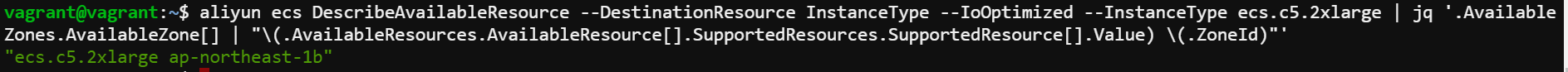
Above you will find this instance type is only available in zone ap-northeast-1b.
To plan your VPC CIDR, you will need 1 VPC, 1 Region, two zones, and computing optimized instances which support 4NICs.
Create a VPC for the FortiGate A-P by following this guide
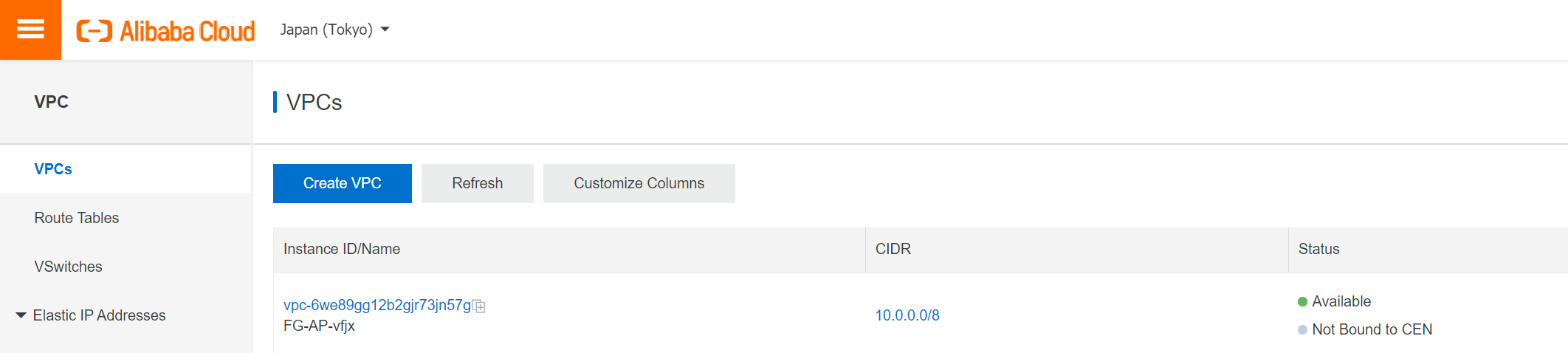
4 switches in Tokyo Zone A, 4 Switches in Tokyo Zone B. Assign vswitch CIDR blocks by following the cookbook.
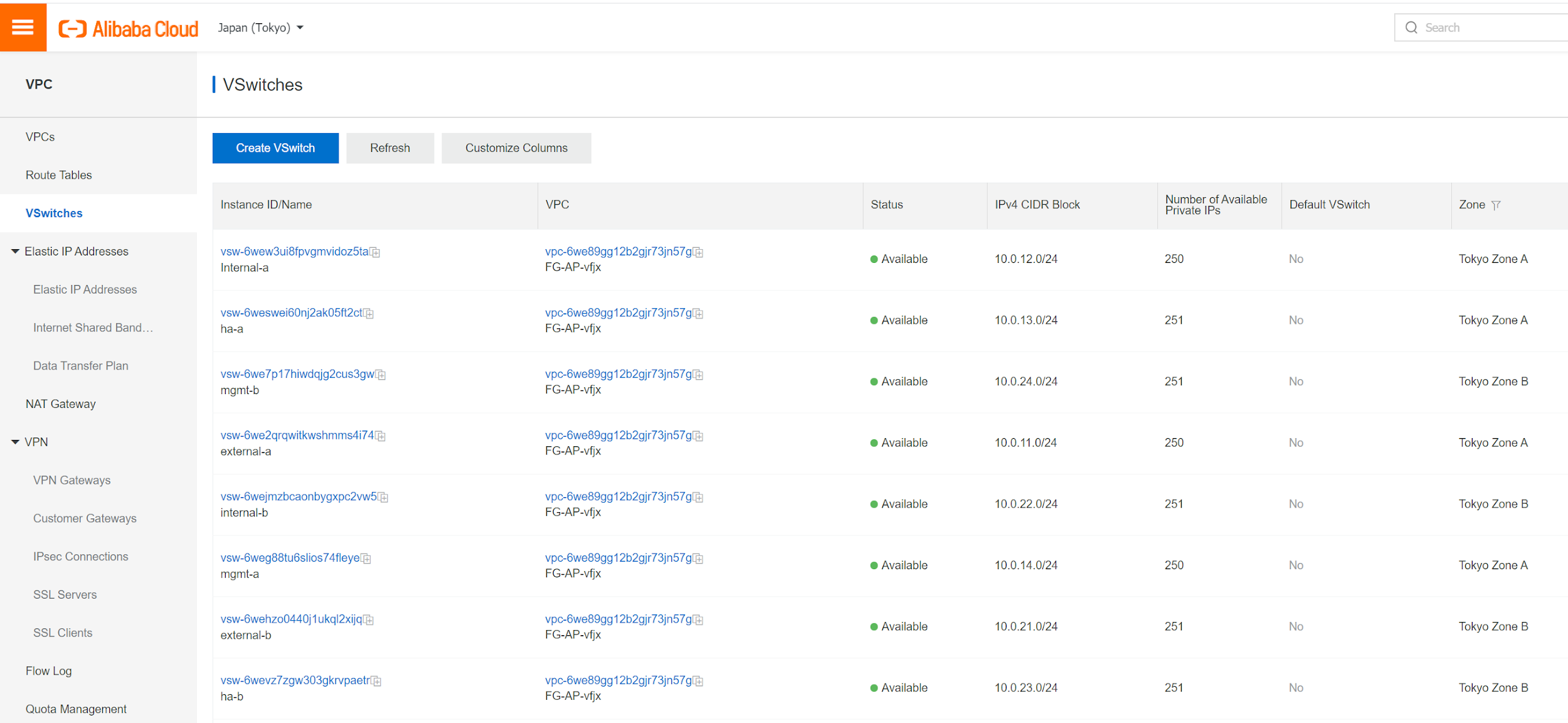
The switch named "external" is for internet facing, while "internal" is for protected traffic, and "ha" is for clustering traffic. We'll use "mgmt" for fortigate traffic that access aliyun metadata service (acs). The communication between vswitch in different zones has to go through vrouter according to the associated routing table.
The next step is we need to create a security-group and instance. Go to Alibaba Cloud ECS product to create those, as those are ECS related resources.
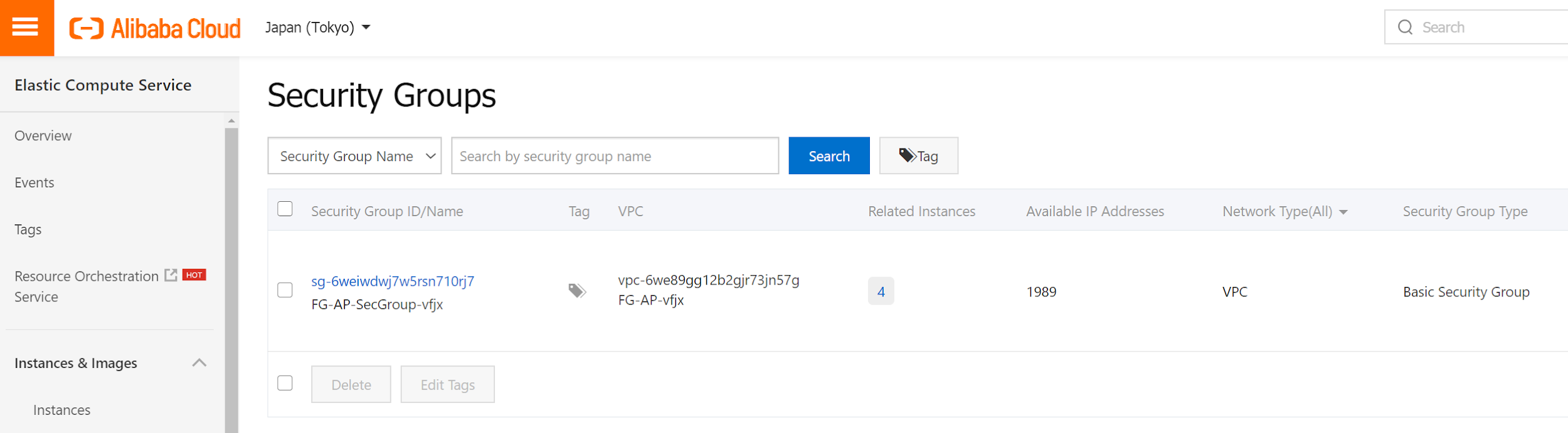
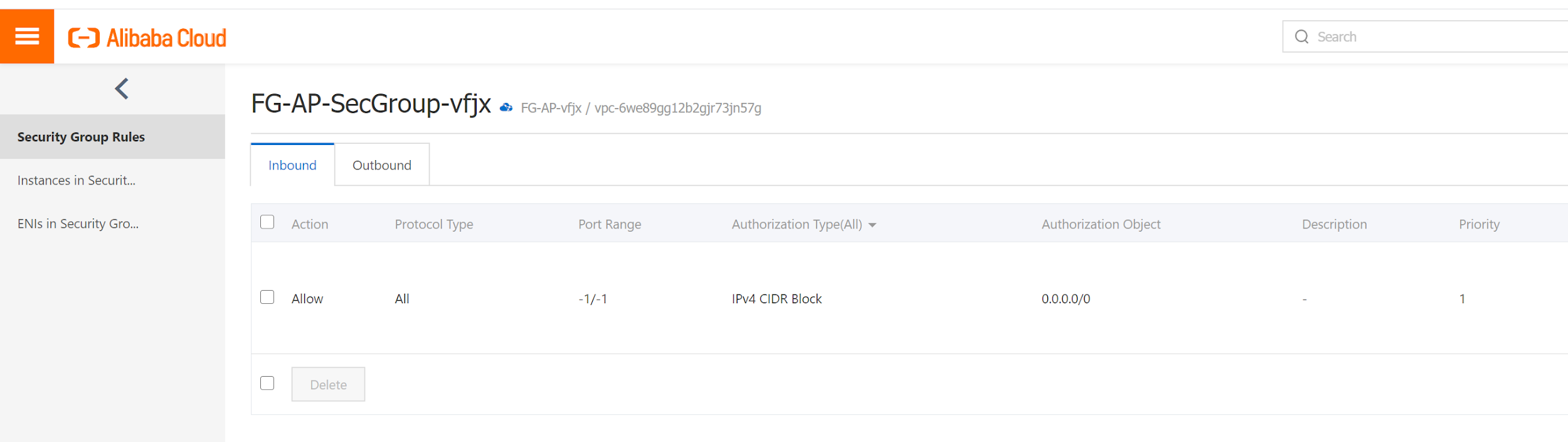
To simplify the installation, here I allow all protocols during the installation. After that, we can refine the policy to more restricted rules. No need to config outbound rules.
Later on, we will need to associate SecurityGroup with ENI and instances.
Visit our Marketplace and choose from Fortinet FortiGate (PAYG) Next-Generation Firewall (4 vCPUs) or Fortinet FortiGate (PAYG) Next-Generation Firewall (8 vCPUs)
Click to choose your plan; we can choose either Pay-As-you-go or subscription billing method for the instance. If you want to try a few days, you might want to choose pay-as-you-go.
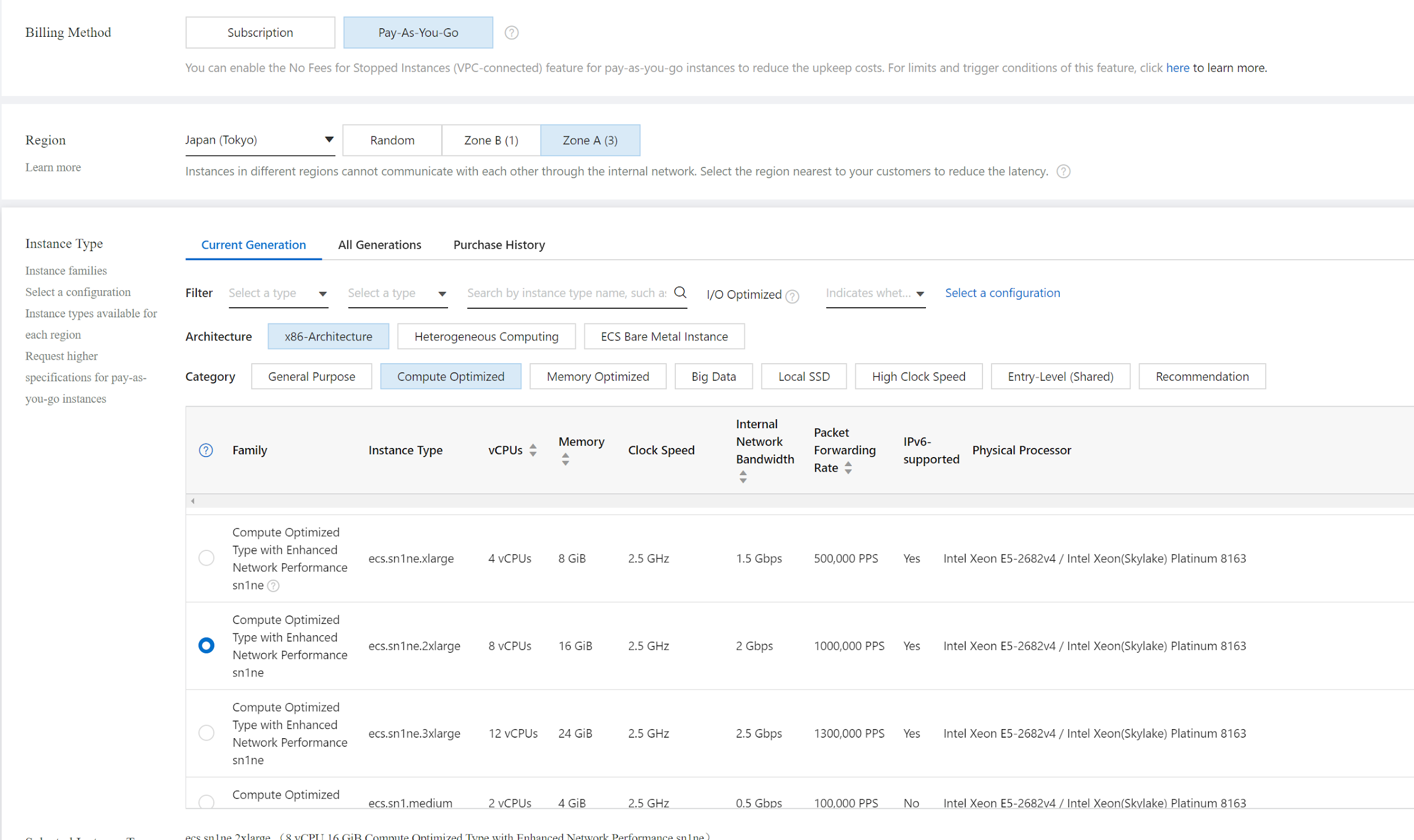
Select Region, Zone, "compute Optimized" category. Images will be automatically selected. Add Data Disk if you want to log to a local disk. Here we select zone A for fortigate-Primary. The instance type here is ecs.sn1ne.2xlarge
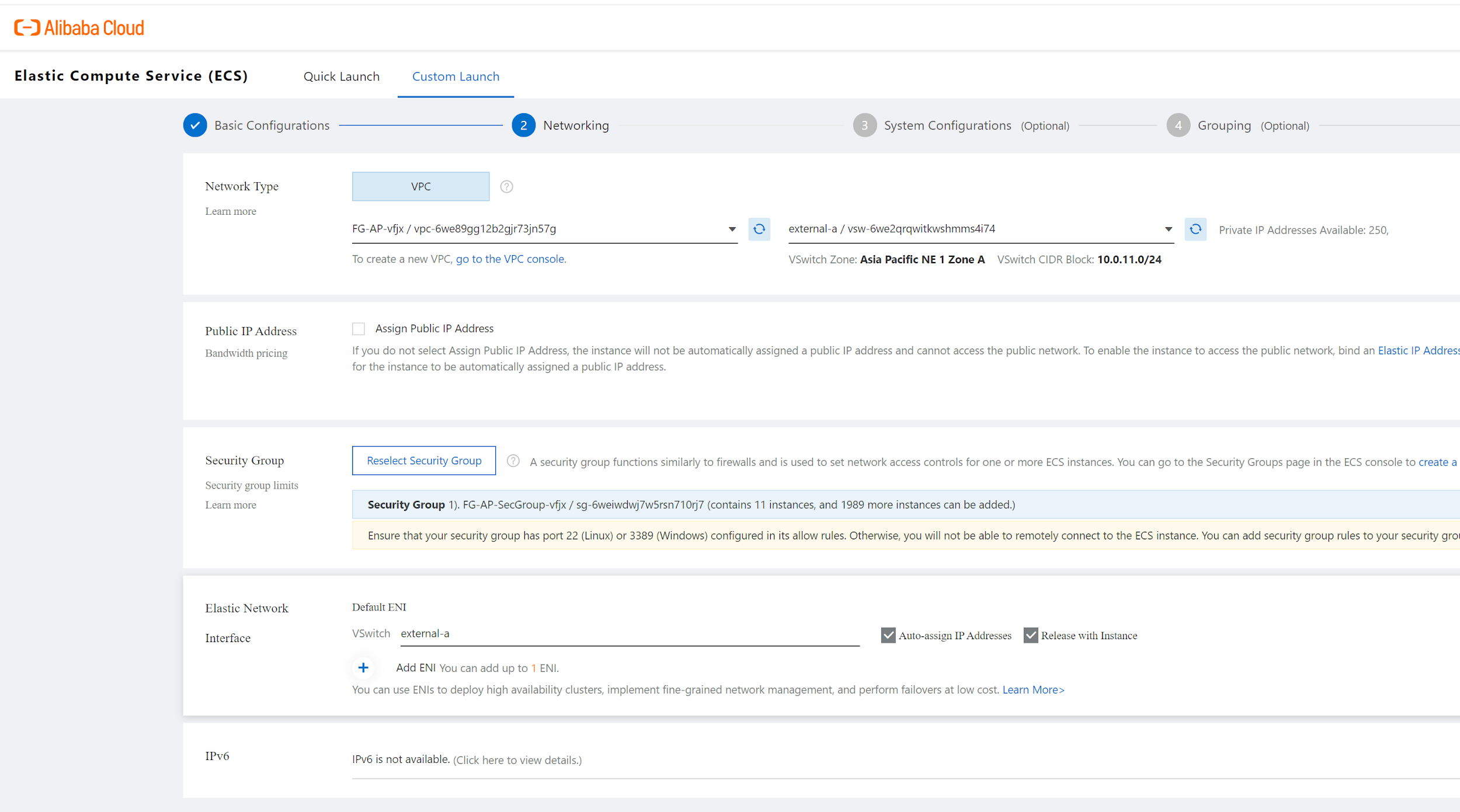
Select VPC, external-a switch, as we want Fortigate Primary IP bound to external switch, so it will get an IP address from 10.0.11.0/24 CIDR block. We do not need to check "Assign Public IP address" as later on, we will create an EIP and bind to fortigate primary interface. Select the Security group we just created. You will also notice that a Default ENI will be created and attached to Vswitch external-A.
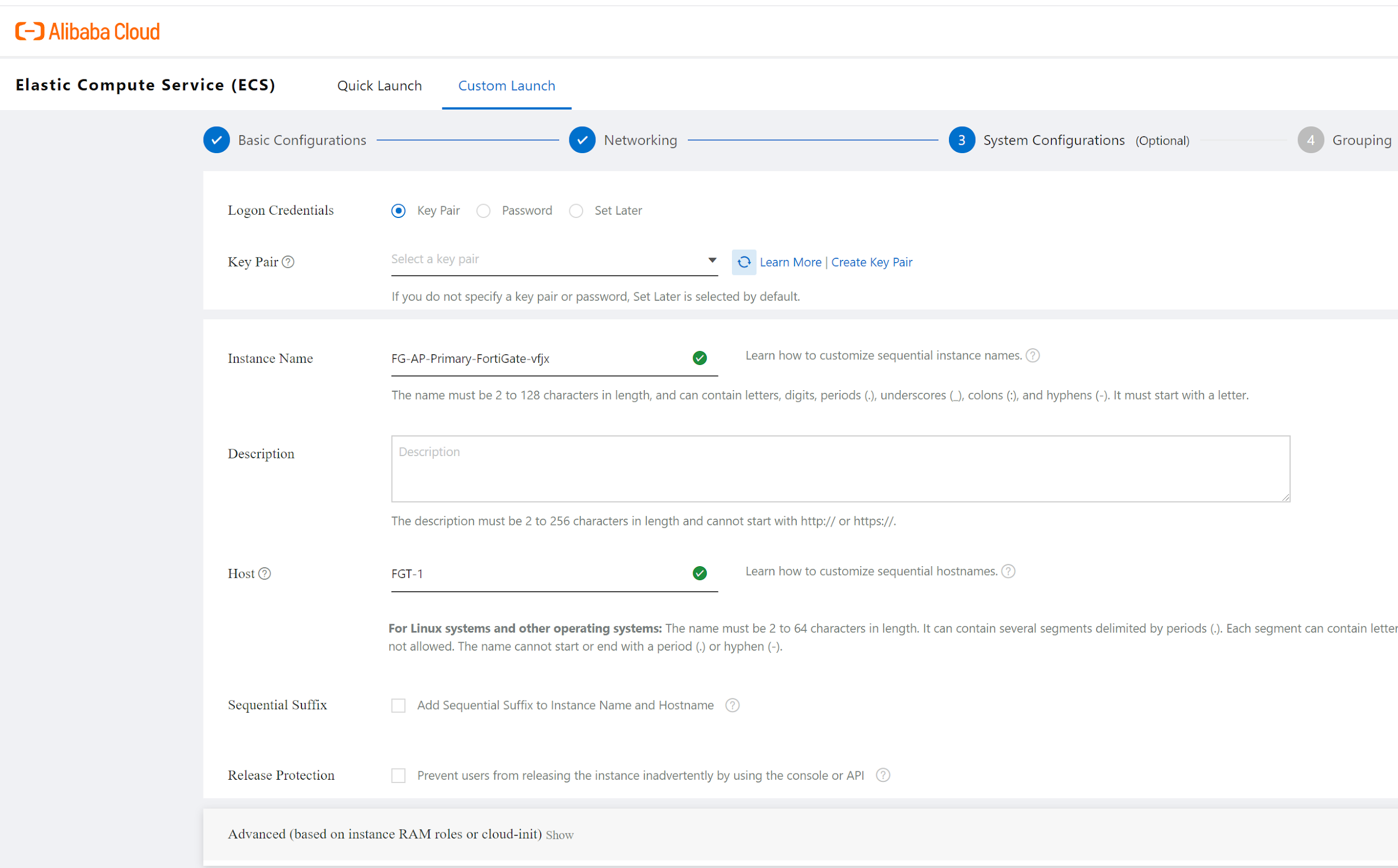
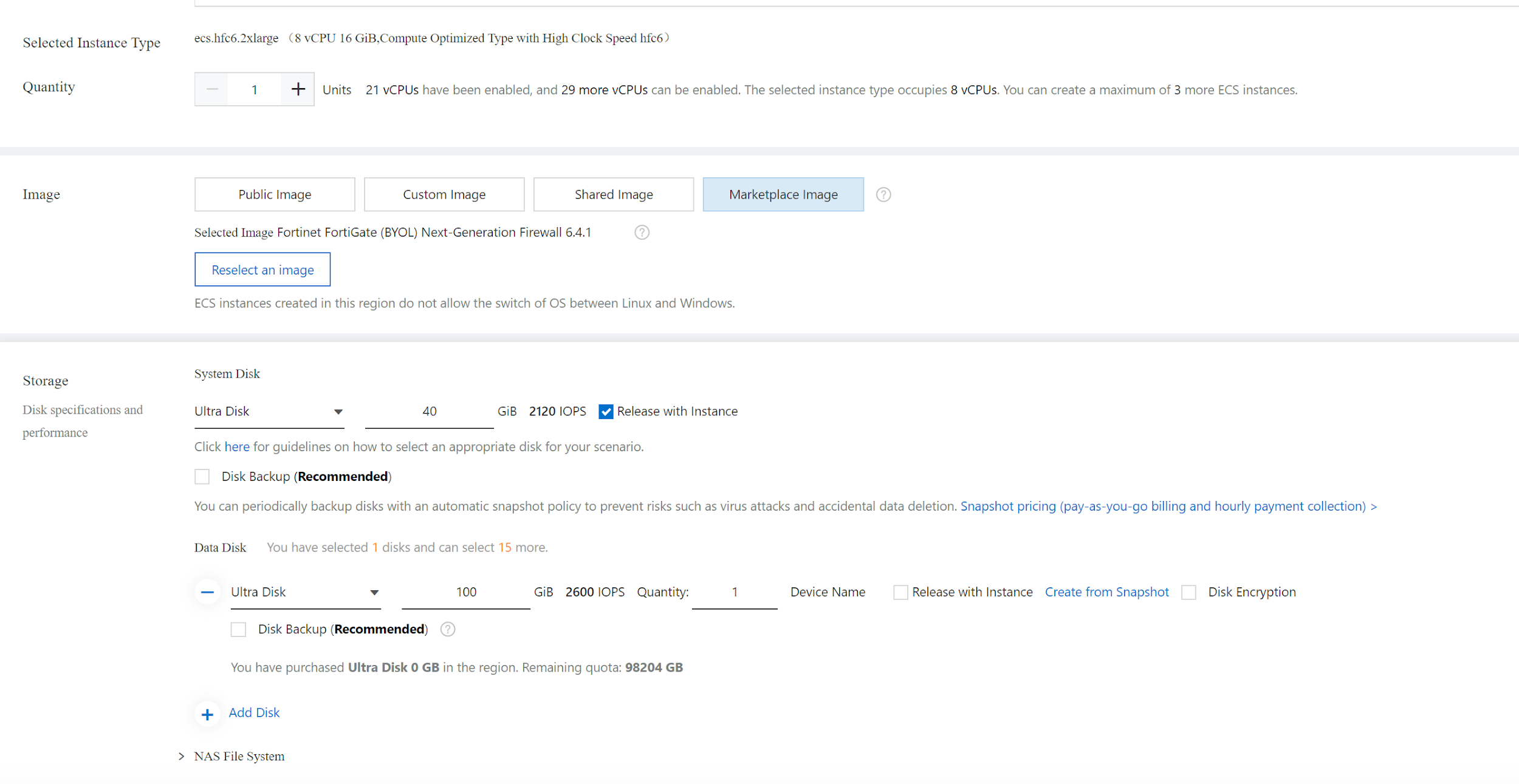
You do not need to choose a key pair, the default password for fortigate instance will be the instance ID. Set up the instance Name and Host name. Use default for rest configuration and access "Terms of Service" for your created Instances. Do the same to create another fortigate instance in AZ B.
Next we will create additional ENI and EIP and associate with instances just created.
We will need to create 3 ENIs for each fortigate in each Availability zone. A total of 6 ENIs have to be created and a total of 3 EIPs. EIP3 binds to FGT-1 primary interface, EIP1 binds to FGT-1 ENI3, EIP2 binds to FGT-2 ENI3.
You have to select VPC, Vswtich, and SecurityGroup for that ENI, and you also need to assign a Primary Private IP for the ENI. Each ENI will be associated to the corresponding vswitch with an IP address belonging to that subnet.
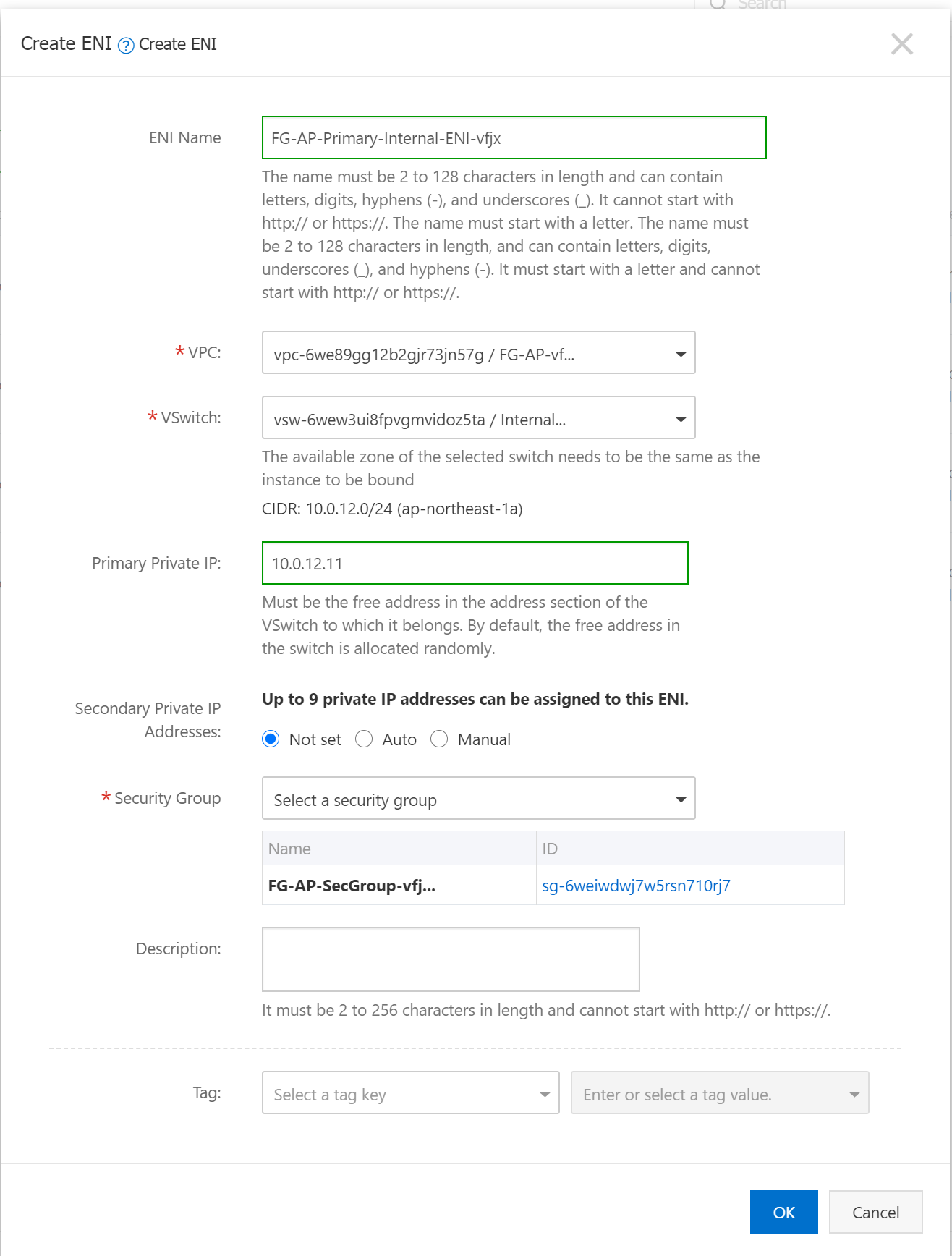
Next, you will need to create EIP, and Bind EIP to ENI. You should see the result below.
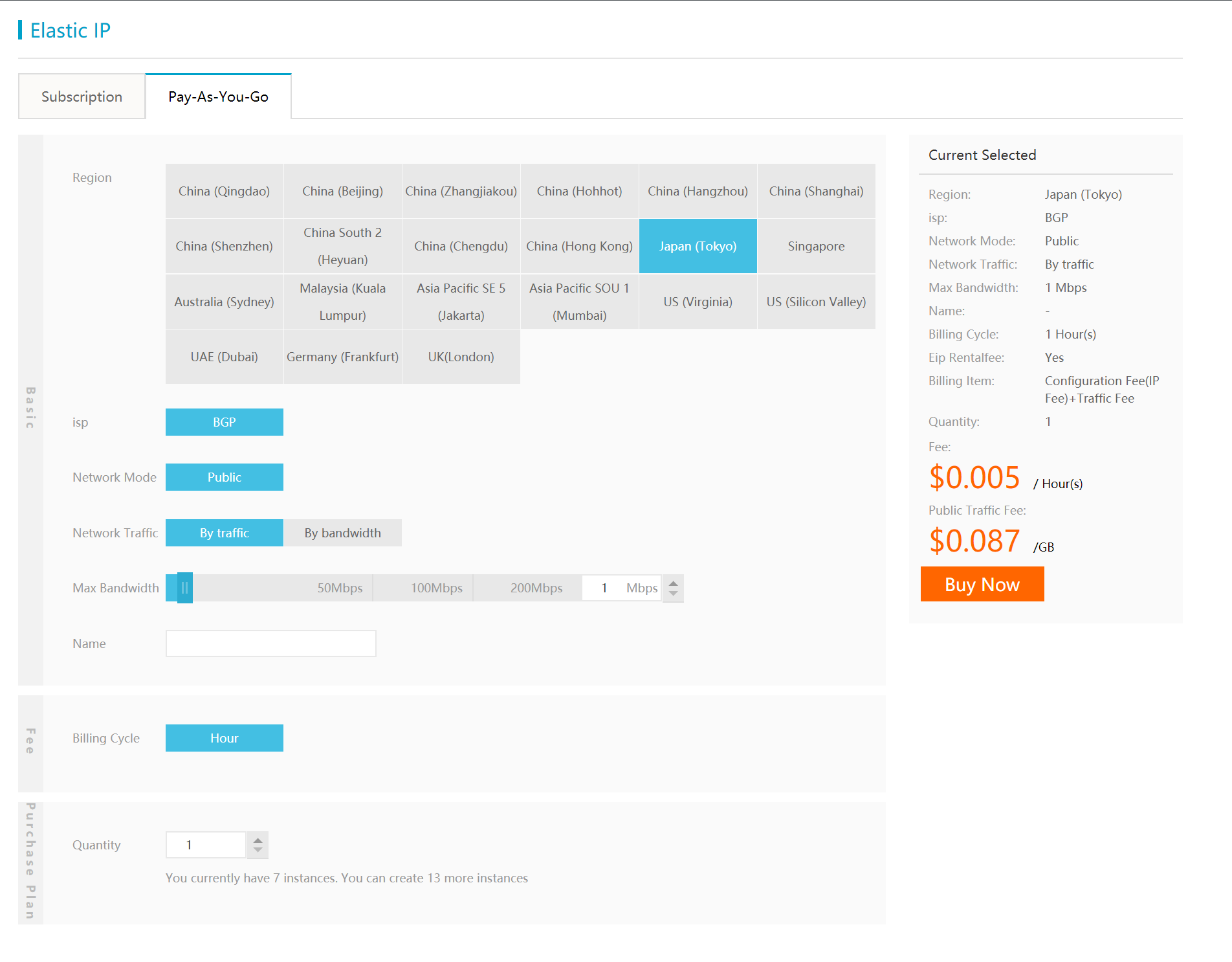
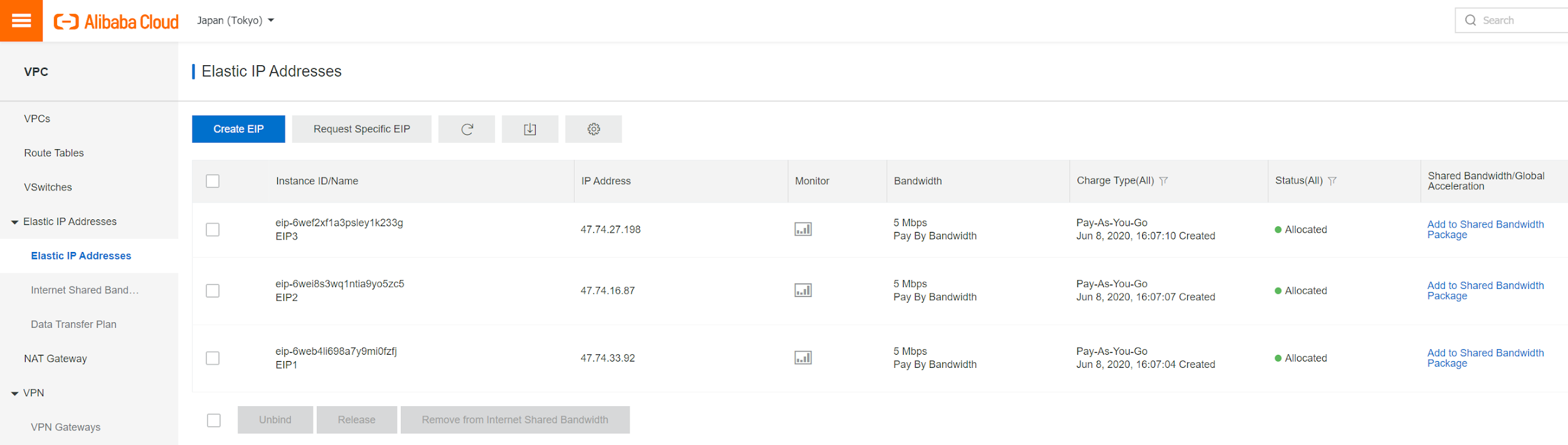
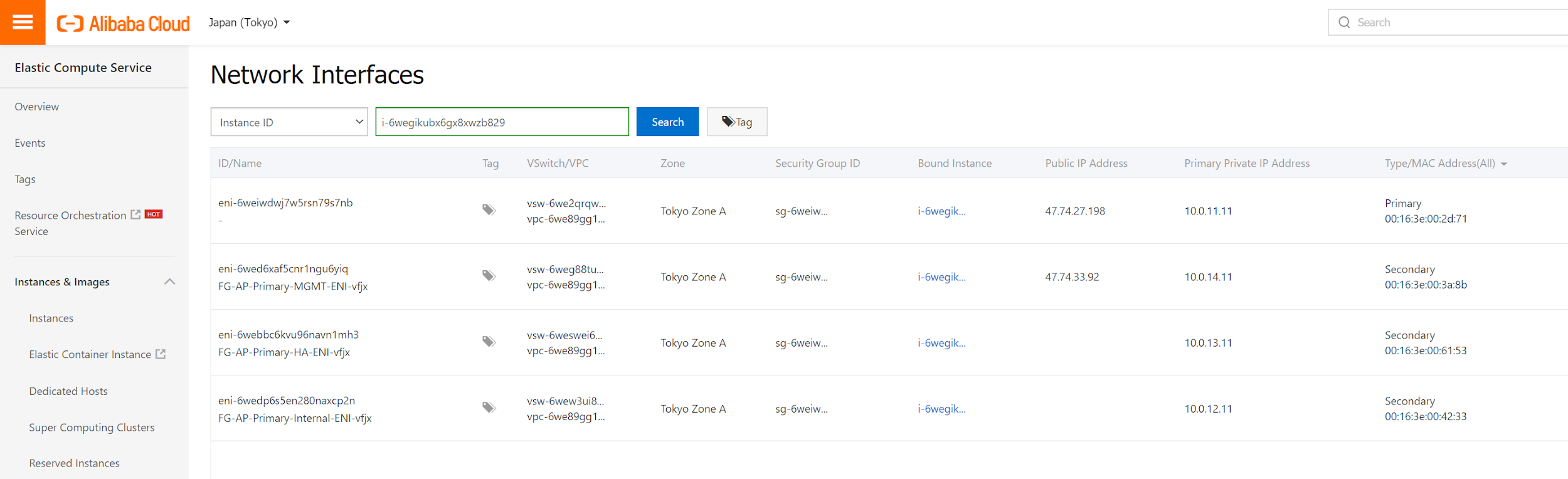
Above you see that FGT-1 in zone A is associated with 4 ENIs. The first one in the list is the one created by default with instances, which is associated with EIP3. The other 3 ENIs are additional ENIs, which are marked as type "Secondary". The first "Secondary" ENI is associated with EIP1.
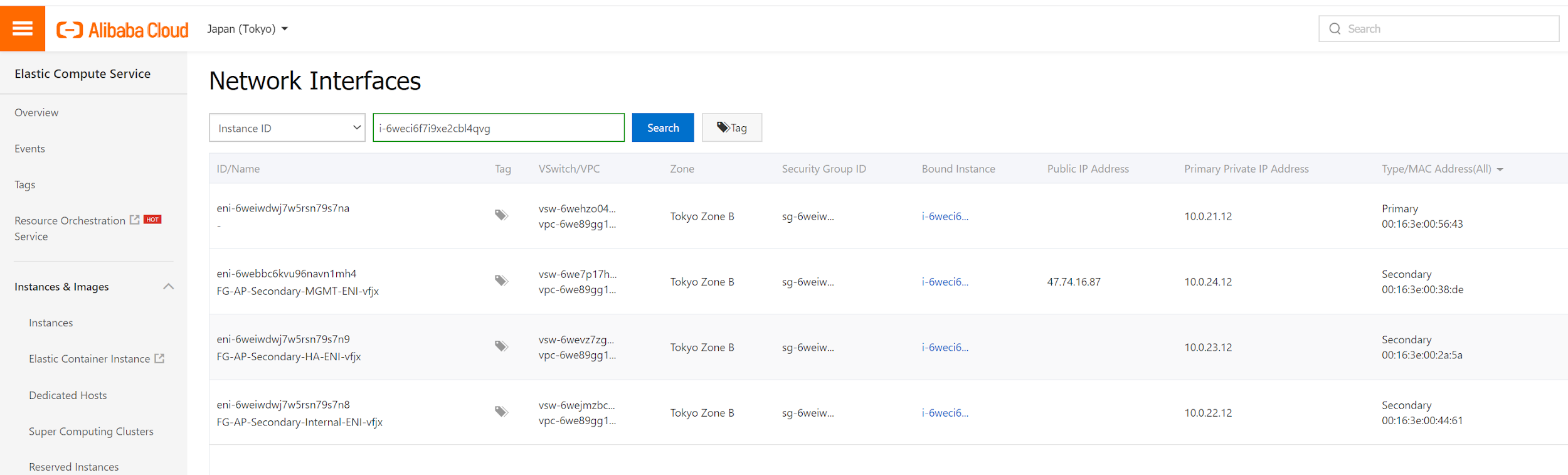
For FGT-2 in zone B, EIP2 is associated with MGMT ENI.
By default, a system routing table is created for each VPC and associated with vswitch in this VPC. In our case, we want the internal switch (internal-a) to point all traffic towards fortigate instance in Zone A. So we have to create a custom route and create a rule entry to add a default router that point to FGT-1 first secondary ENI. By doing this, all the traffic from subnet (10.0.12.0/24) will be routed to fortigate instance secondary ENI (which is fortigate Port 2). So the traffic will be handled by Foritgate instead go directly to vrouter. Inside Fortigate, we have a default router point to aliyun vRouter for traffic leave VPC router to internet or aliyun CEN.
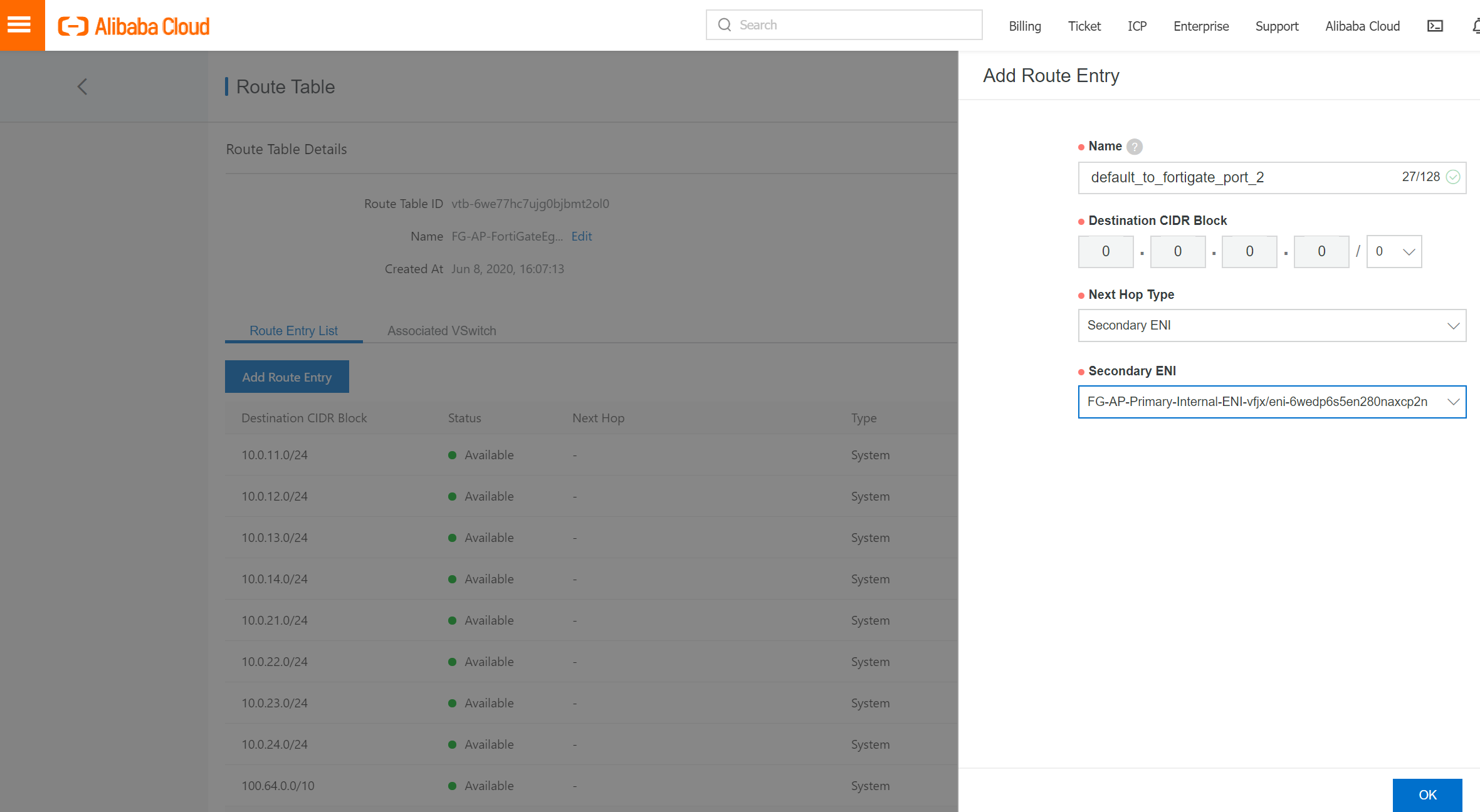
Here we added a default route "Deafult_to_fortigate_port_2" pointing to instance primary fortigate secondary ENI.
This custom routing table will also be automatically associated with vswitch named "internal-a", and this vswitch "internal-a" will also be unassociated from the system routing table.
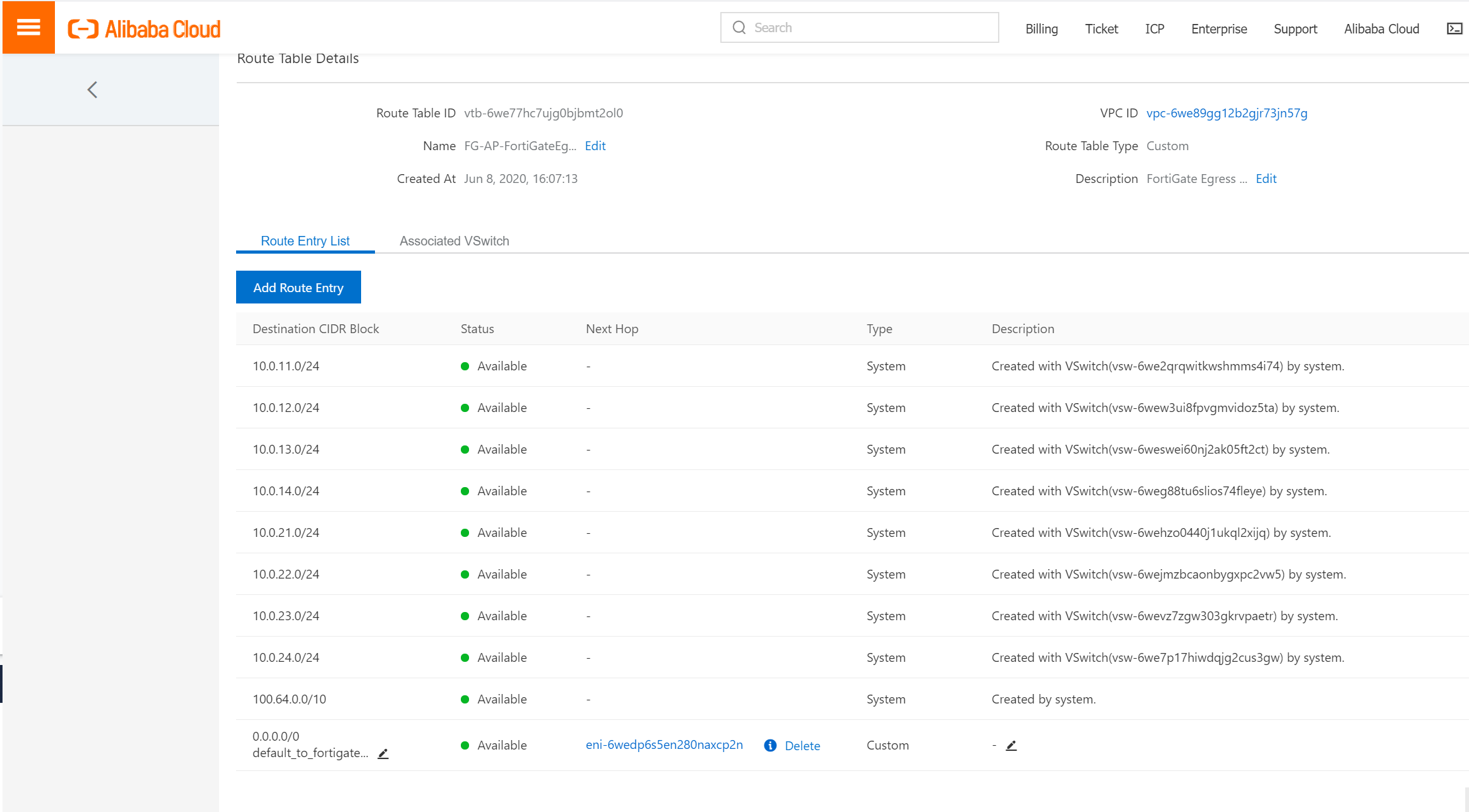
You will see the routing table above.
This is needed for FGT to access alicloud metadata services. We create two tags with Name:FGT1 and Name:FGT2 respectively.
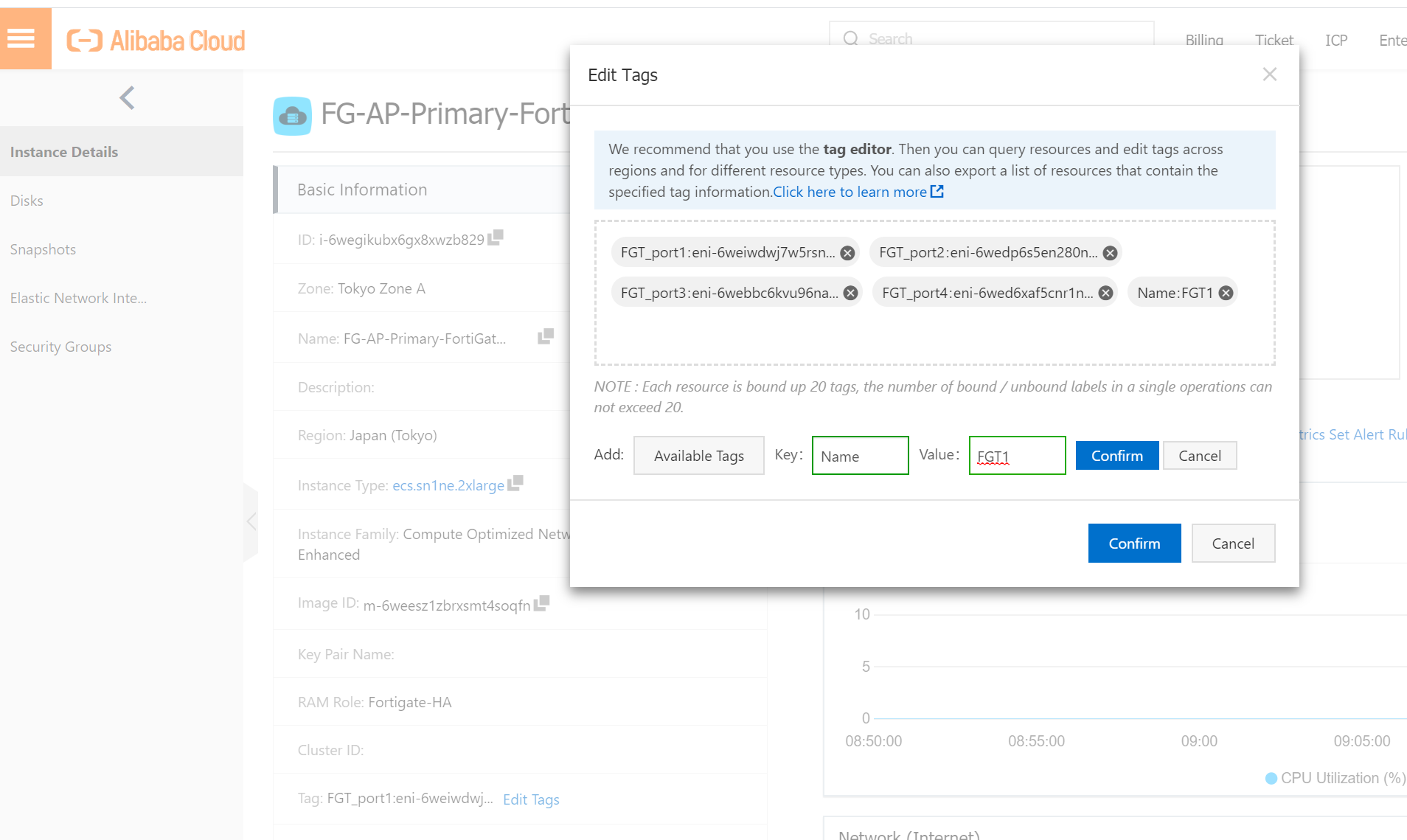
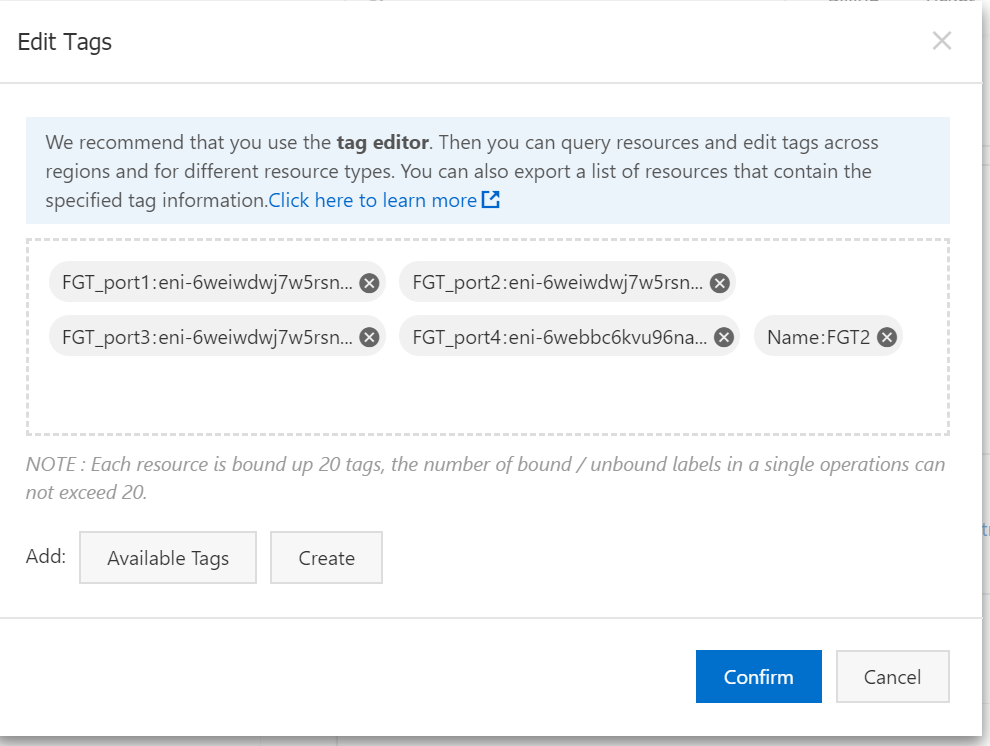
Finally, you should see all tags like below.
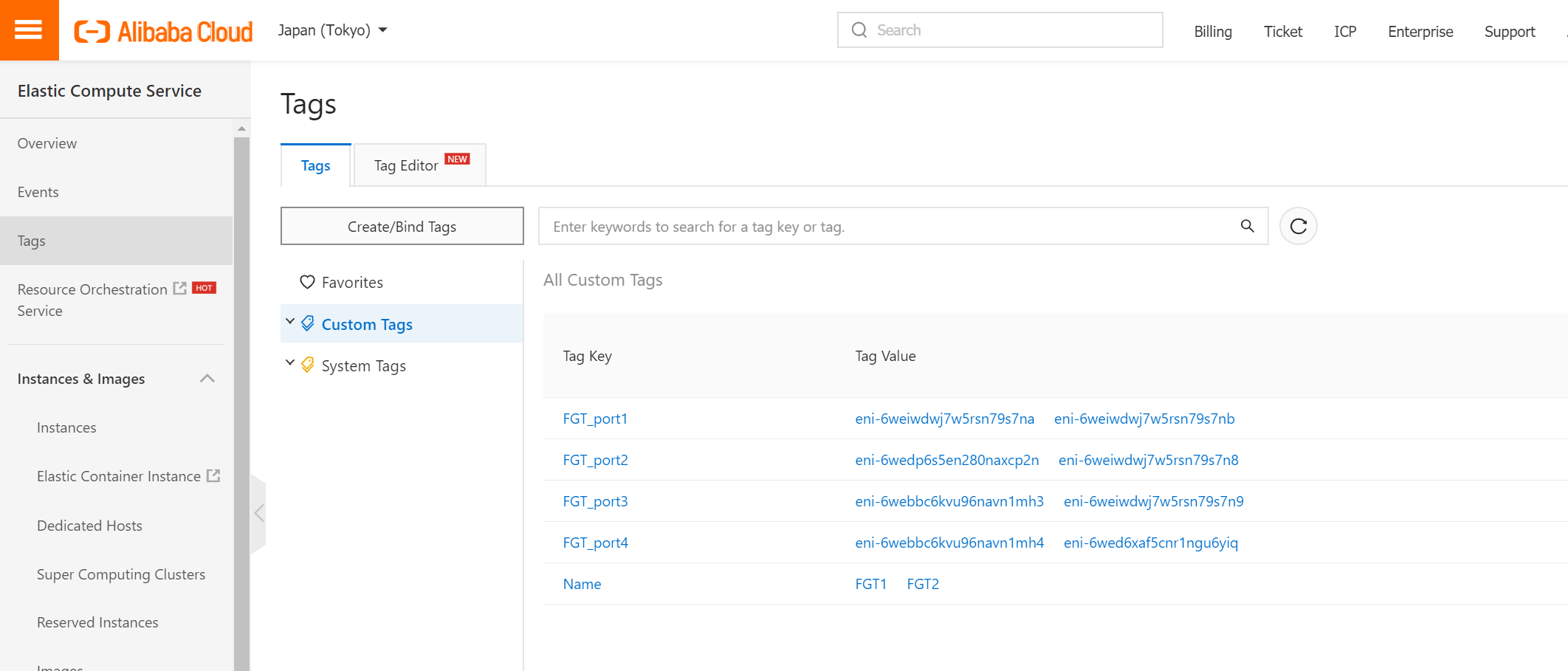
We need FGT1 to retrieve information from aliyun metadata services. This is needed for failover to work. Fortigate needs to know the EIP3 is associated with which Fortigate.
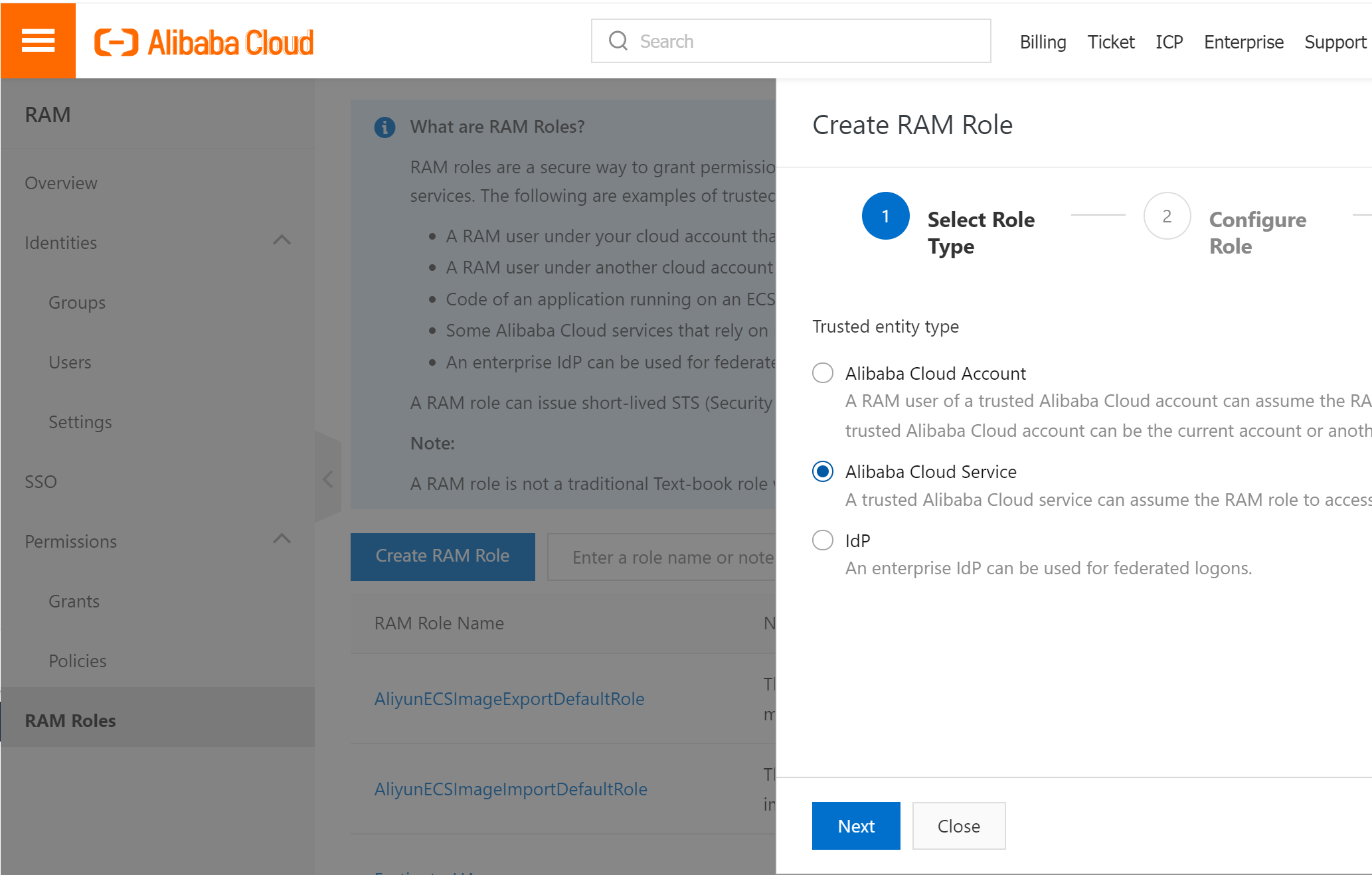
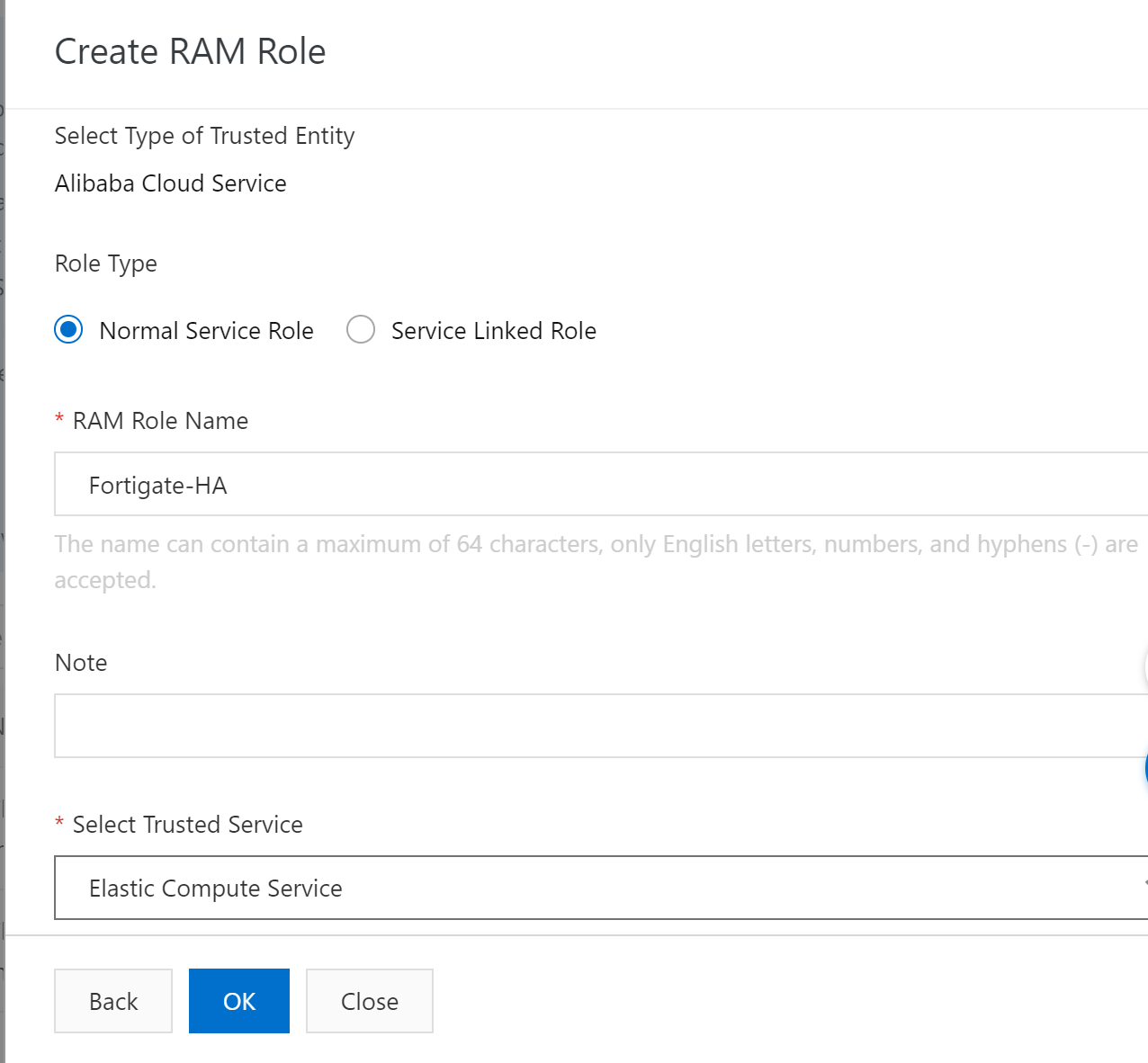
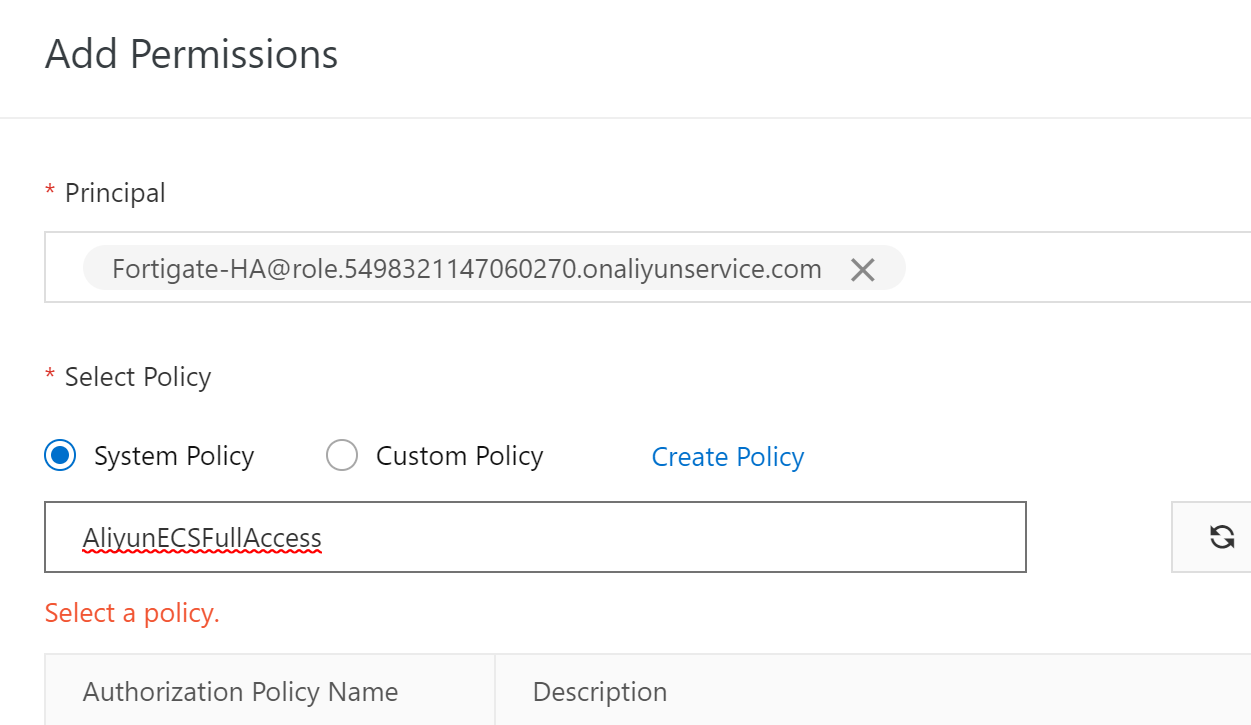
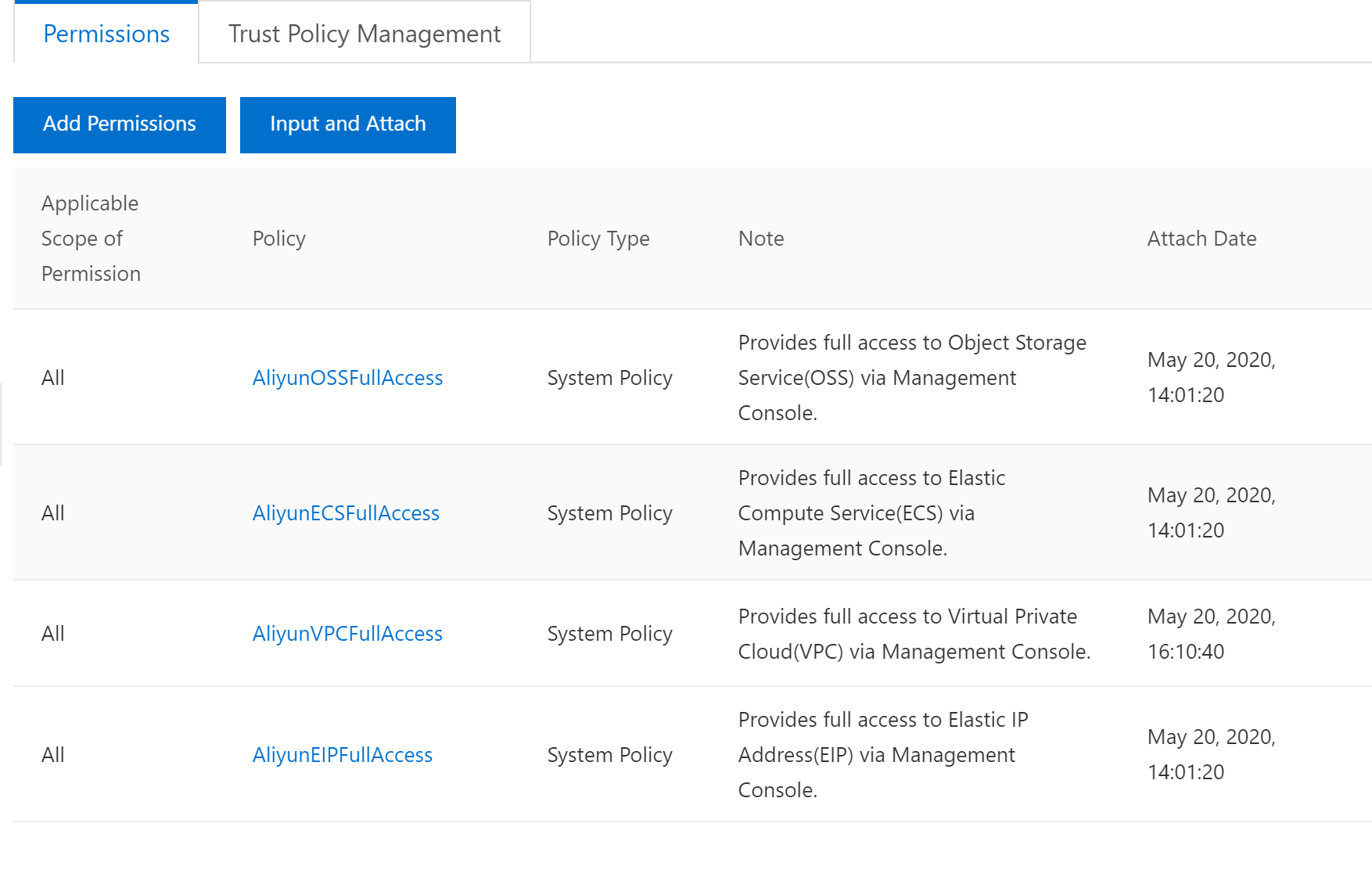
Add AliyunECSFUllAccess, AliyunVPCFullAccess, and AliyunEIPFullAccess .
Then bind RAM rule to two Fortigate instances.
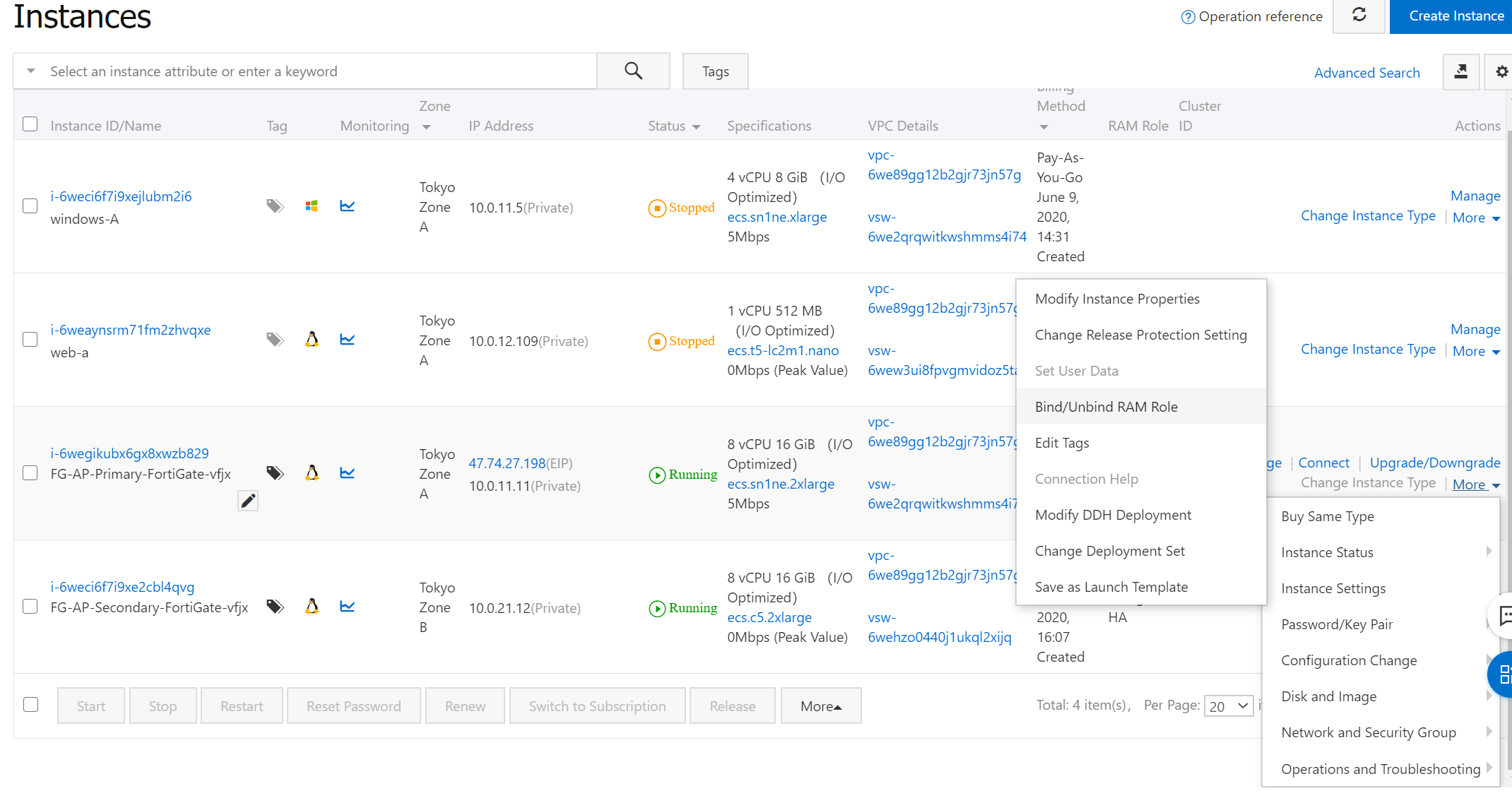
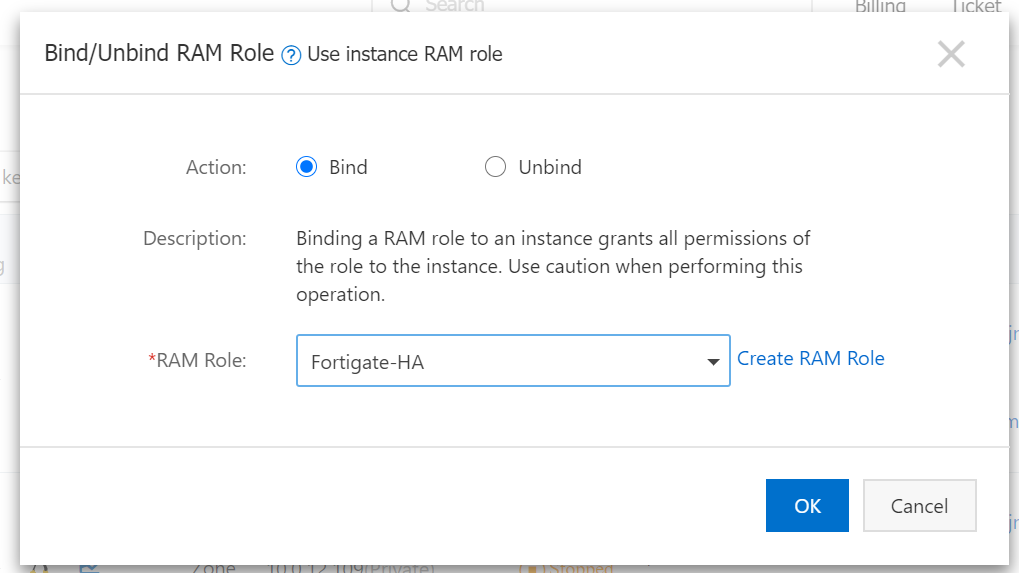
Do the same for FGT2 in zone.
We have completed the setup on Alibaba Cloud, and have successfully launched the FortiGate instance in both zone A and zone B. We have also configured the custom routing table and added a default route point to FortiGate.
In the following blogs, we will set up Fortigate to enable HA across AZs.
https://github.com/yagosys/fortigate_aliyun/tree/master/AP-CrossZone
Get Fortinet FortiGate on Alibaba Cloud by visiting our Marketplace:
Fortinet FortiGate (PAYG) Next-Generation Firewall (4 vCPUs)
Fortinet FortiGate (PAYG) Next-Generation Firewall (8 vCPUs)
Setting Up Palo Alto Networks VM-Series Firewall on Alibaba Cloud

21 posts | 12 followers
FollowMarketplace - August 18, 2020
Marketplace - August 18, 2020
Marketplace - February 21, 2019
Marketplace - September 17, 2021
Alibaba Cloud Community - August 18, 2022
ApsaraDB - March 4, 2021

21 posts | 12 followers
Follow WAF(Web Application Firewall)
WAF(Web Application Firewall)
A cloud firewall service utilizing big data capabilities to protect against web-based attacks
Learn More Cloud Firewall
Cloud Firewall
Provides traffic control and security protection for the Internet, virtual private cloud (VPCs), and hosts in VPCs
Learn More Web Hosting Solution
Web Hosting Solution
Explore Web Hosting solutions that can power your personal website or empower your online business.
Learn More Web App Service
Web App Service
Web App Service allows you to deploy, scale, adjust, and monitor applications in an easy, efficient, secure, and flexible manner.
Learn MoreMore Posts by Marketplace
5089809431687947 January 18, 2021 at 12:46 am
i dont know how you come up with that tag can further explain please