MaxCompute的密钥管理对象Keyset,每个Keyset可以存放1个到多个密钥,您可以在Keyset中增加密钥来实现密钥的轮转,并且可以查看原始密钥。本文介绍KeySet的使用。
注意事项
请您妥善保存Keyset和解密参数。一旦丢失,经Keyset加密的数据将无法解密,即数据无法找回。
准备数据
创建表mf_test_data并添加数据。
--创建表
create table mf_test_data(id string,name string,tel string);
--插入数据
insert into mf_test_data values(1,'kyle','13900001234'),(2,'tom','13900001111');
--查询数据
select * from mf_test_data;
--返回
+----+------+-----+
| id | name | tel |
+----+------+-----+
| 1 | kyle | 13900001234 |
| 2 | tom | 13900001111 |
+----+------+-----+直接使用Keyset
示例1:新建Keyset。
select NEW_KEYSET('AES-GCM-256', 'my first keyset');返回结果如下。
+------+ | _c0 | +------+ | =0A=10260nZQEAMAsSF7mB=12\=0A3=0A=0BAES-GCM-256=12=20=C4t=13+=8E=DD=9D=E8=A0=AA=B4=ED~1`=B7=C6=D0K=D3=FC=D4n=DF=DF=D4=C3)=E8=96=0E=17=18=01=20=02=10=01=1A=10260nZQEAMAsSF7mB=20=02*=0Fmy=20first=20keyset | +------+示例2:将Keyset内容转化为明文,方便查看。
select KEYSET_TO_JSON(NEW_KEYSET('AES-GCM-256', 'my first keyset'));返回结果如下。
+-----+ | _c0 | +-----+ | { "key": [{ "description": "my first keyset", "key_id": "Ra4nZQEAoBuiGbmB", "key_meta_data": { "key_material_origin": "Origin_ALIYUN_MAXCOMPUTE", "key_material_type": "SYMMETRIC", "type": "AES-GCM-256", "value": "/LFKWhw18hz+OBO490YKmjQQDNVWJLOueaUAKKiem/k="}, "output_prefix_type": "PREFIX_ALIYUN_MAXCOMPUTE", "status": "ENABLED"}], "primary_key_id": "Ra4nZQEAoBuiGbmB"} |示例3:在Keyset中新增密钥并将新增密钥设置主密钥。
在
AES-GCM-256算法类型密钥中新增一个AES-SIV-CMAC-128算法类型的密钥。select KEYSET_TO_JSON( ADD_KEY_TO_KEYSET( NEW_KEYSET('AES-GCM-256', 'my first keyset'), 'AES-SIV-CMAC-128', unhex('b75585cf321cdcad42451690cdb7bfc49c26092f60f854e72d43244c55620a3d'), '' ) );返回结果如下。
+-----+ | _c0 | +-----+ | { "key": [{ "description": "my first keyset", "key_id": "+q8nZQEAgAMtJLmB", "key_meta_data": { "key_material_origin": "Origin_ALIYUN_MAXCOMPUTE", "key_material_type": "SYMMETRIC", "type": "AES-GCM-256", "value": "Hj//ZKxLE/t0Uq7XRJQoe2OYNwlauDdGmkaQbMfnZ80="}, "output_prefix_type": "PREFIX_ALIYUN_MAXCOMPUTE", "status": "ENABLED"}, { "description": "", "key_id": "+q8nZQEAML2VArmB", "key_meta_data": { "key_material_origin": "Origin_RAW", "key_material_type": "SYMMETRIC", "type": "AES-SIV-CMAC-128", "value": "t1WFzzIc3K1CRRaQzbe/xJwmCS9g+FTnLUMkTFViCj0="}, "output_prefix_type": "PREFIX_ALIYUN_MAXCOMPUTE", "status": "ENABLED"}], "primary_key_id": "+q8nZQEAML2VArmB"} | +-----+系统自动生产一个新密钥并设置新密钥为主密钥。
select KEYSET_TO_JSON( ROTATE_KEYSET( NEW_KEYSET('AES-GCM-256', 'my first keyset'), 'AES-GCM-256') );返回结果如下。
+-----+ | _c0 | +-----+ | { "key": [{ "description": "my first keyset", "key_id": "TbEnZQEAUIEJC7mB", "key_meta_data": { "key_material_origin": "Origin_ALIYUN_MAXCOMPUTE", "key_material_type": "SYMMETRIC", "type": "AES-GCM-256", "value": "TLAKX8y0/aUbMAtElI+oicEw1fWSTJhZs1D2i3AAf40="}, "output_prefix_type": "PREFIX_ALIYUN_MAXCOMPUTE", "status": "ENABLED"}, { "key_id": "TbEnZQEAAIy0IrmB", "key_meta_data": { "key_material_origin": "Origin_ALIYUN_MAXCOMPUTE", "key_material_type": "SYMMETRIC", "type": "AES-GCM-256", "value": "jPewQsmbsajzM/gLNX9QFtENs2n9uvhgrgcrcGgl0A0="}, "output_prefix_type": "PREFIX_ALIYUN_MAXCOMPUTE", "status": "ENABLED"}], "primary_key_id": "TbEnZQEAAIy0IrmB"} | +-----+
示例4:数据加解密。
创建表mf_keyset并写入Keyset。
---创建表 create table mf_keyset (id string,ks binary); ---创建Keyset并存入表mf_keyset中 insert into mf_keyset select '1',NEW_KEYSET('AES-GCM-256', 'my first keyset');
对表mf_test_data中的tel字段进行加解密。
将表
mf_test_data中的tel字段加密。select id, name, ENHANCED_SYM_ENCRYPT(ks,tel) as tel from (SELECT id,name,tel FROM mf_test_data) JOIN (SELECT ks FROM mf_keyset WHERE id = '1') a ;返回结果如下。
+----+------+------+ | id | name | tel | +----+------+------+ | 1 | kyle | =0B=88=A5=0Ak=AD=E0=9A=B4=EC=CC=1F=F9=DEk\=16=0F=BD=F1=03=8B=95=F0@=88s=EE=1E=8A=D2=05=83=B5'e=01=00=A0=C5=0BXu=A5Z&<=01=F8=C5Q=89=A9=A6=80=E2=0F=1A)=02fa=CF=07'=1B'=EB=FD=CF=E9 | | 2 | tom | =0B=88=A5=0Ak=AD=E0=9A=B4=EC=CC=1F=F9=DEk\=16=0F=BD=F1=03=8B=95=F0@=88s=EE=1E=8A=D2=05=83=B5'e=01=00=10=FC=0BXu=A5+3=D5=1Fb=C0=88=AC=90=AA=FE!C=F0=99y&=9C=89=0E=9B=8FD=16=E0=96, | +----+------+------+将表
mf_test_data中的tel字段解密。select id, name, ENHANCED_SYM_DECRYPT(ks, ENHANCED_SYM_ENCRYPT(ks,tel), '')as tel from (SELECT id,name,tel FROM mf_test_data) JOIN (SELECT ks FROM mf_keyset WHERE id = '1') a ;返回结果如下。
+----+------+------+ | id | name | tel | +----+------+------+ | 1 | kyle | 13900001234 | | 2 | tom | 13900001111 | +----+------+------+
结合KMS使用Keyset
MaxCompute支持结合KMS进行数据加密,系统会自动生成加解密数据的密钥Keyset,该Keyset与KMS密钥结合生成Keyset_KMS,用户需要保存Keyset_KMS。若需要数据加解密时,需要提供Keyset_KMS,然后系统会结合KMS密钥对Keyset_KMS进行加解密,还原成加密数据的Keyset并对数据进行加解密。
结合KMS使用Keyset的介绍如下图所示。
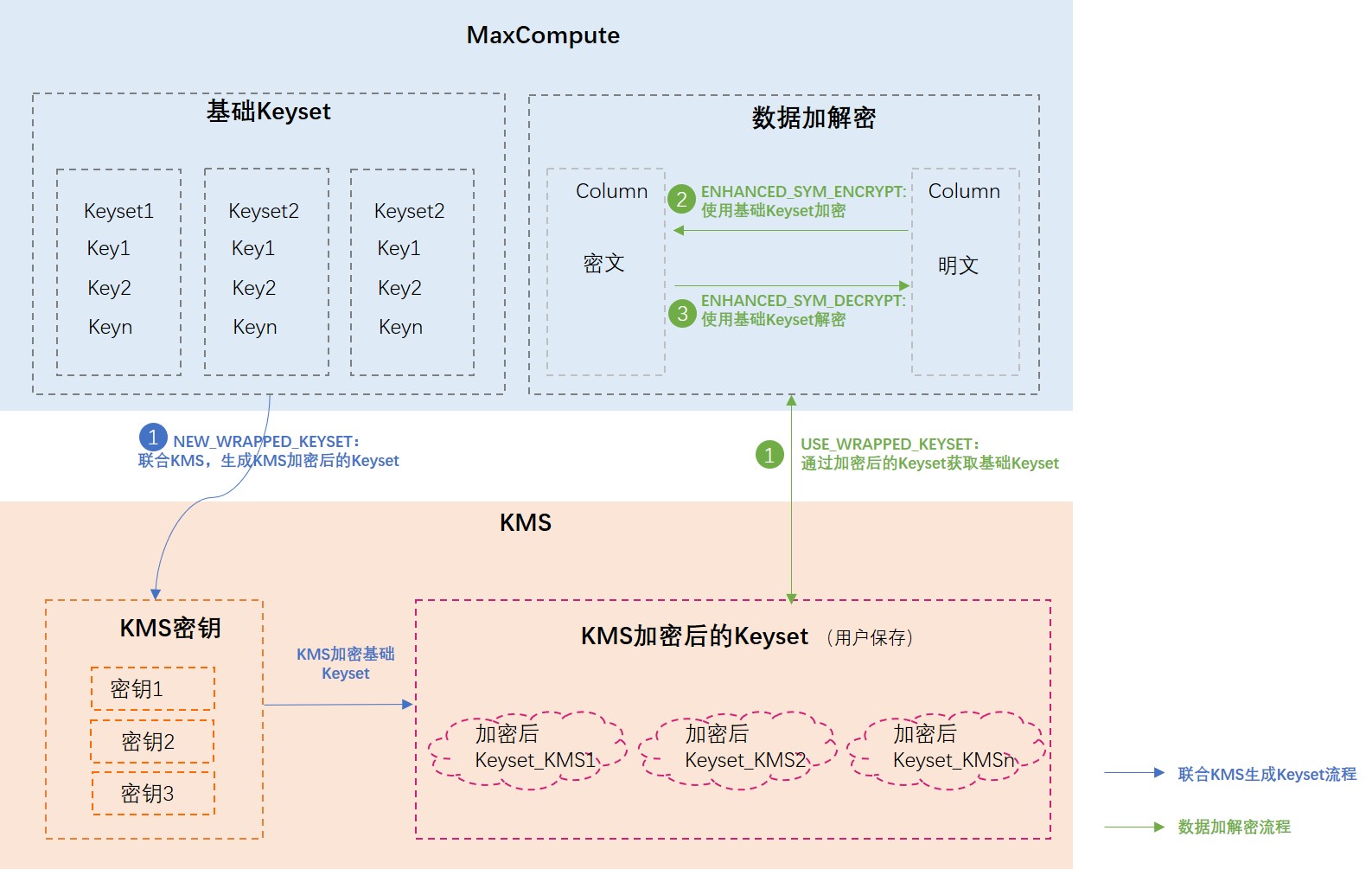
开通KMS并完成配置
开通KMS,并购买KMS软件密钥管理实例。具体操作,请参见购买和启用KMS实例。
创建密钥,并在密钥详情页面获取密钥ARN。具体操作,请参见软件密钥。
本示例中,创建的密钥ARN为
acs:kms:cn-beijing:189273228874****:key/key-bjj6527b6c6465hsf****。为MaxCompute授予KMS权限,允许MaxCompute使用KMS进行加解密操作。
说明使用KMS对MaxCompute的Keyset进行进一步封装加密后,您需要给MaxCompute授予KMS加解密的权限,以保障后续执行加解密命令时,MaxCompute命令的正常运行。
主要操作思路为:
创建一个RAM角色,角色的可信实体类型为阿里云服务、受信服务为大数据计算服务。操作详情请参见创建可信实体为阿里云服务的RAM角色。
为上述创建的角色添加系统权限:AliyunKMSCryptoUserAccess,允许MaxCompute使用KMS进行加解密。操作详情请参见为RAM角色授权。
假设您使用阿里云账号USER_A完成上述操作,则此时阿里云账号USER_A可以正常进行加密Keyset操作。
本文以创建角色
mf-secr为例,其中mf-secr的ARN为acs:ram::189273228874****:role/mf-secr。
(可选)如果您后续希望使用USER_A的RAM用户、或者其他账号(USER_B及其RAM用户)进行加解密,您还需进行以下的授权操作。
使用USER_A的RAM用户进行加解密
为USER_A的RAM用户新建权限策略(角色
mf-secr的PassRole权限)并授权给RAM用户,即允许RAM用户使用角色mf-secr,配置详情请参见为RAM用户授权。示例权限策略脚本内容如下。{ "Statement": [ { "Effect": "Allow", "Action": "ram:PassRole", "Resource": "acs:ram:*:*:role/mf-secr" } ], "Version": "1" }使用USER_B及其RAM用户进行加解密
重要跨账号使用封装密钥集加解密,相关函数中的
role_chain参数必填,结合如下示例角色相关信息,示例为'acs:ram::188538605451****:role/b-secr,acs:ram::189273228874****:role/mf-secr2b'。操作思路如下:
在阿里云账号USER_A中创建一个新的RAM角色(
mf-secr2b),角色的可信实体类型为阿里云账号、信任的云账号为USER_B。操作详情请参见创建可信实体为阿里云账号的RAM角色。为创建的
mf-secr2b角色授予mf-secr的PassRole权限,示例权限策略内容请参见使用USER_A的RAM用户进行加解密。在阿里云账号USER_B中创建一个新的RAM角色(
b-secr),角色的可信实体类型为阿里云服务、受信服务为大数据计算服务。操作详情请参见创建可信实体为阿里云服务的RAM角色。为创建的
b-secr角色授予mf-secr2b角色的AssumeRole权限,示例权限策略脚本内容如下。{ "Version": "1", "Statement": [ { "Effect": "Allow", "Action": "sts:AssumeRole", "Resource": "acs:ram:*:189273228874****:role/mf-secr2b" } ] }(可选)如果USER_B的RAM用户使用USER_A创建的封装密钥集进行加解密,还需要给USER_B的RAM用户授予
b-secr角色的PassRole权限,示例权限策略脚本内容如下。{ "Statement": [ { "Effect": "Allow", "Action": "ram:PassRole", "Resource": "acs:ram:*:*:role/b-secr" } ], "Version": "1"
结合KMS进行加解密
示例1:新建封装Keyset。
select hex(NEW_WRAPPED_KEYSET('acs:kms:cn-beijing:189273228874****:key/key-bjj6527b6c6465hsf****', 'acs:ram::189273228874****:role/mf-secr', 'AES-GCM-256', 'hello'));返回结果如下。
+-----+ | _c0 | +-----+ | 613256354C574A71616A59314D6A64694E6D4D324E44593161484E6D65576732595331315A586435646D4678596A6C36555437693738632B647070524B46334E5263497567384A6B36716C4E54354133734F6E4776376258453132524E6C4B6E5163703859787132536C6D794F6E4A6975797541745448374F6B5132412B4B6947502F4A7530756477694B736B503033576643726E45646D666F6F324D61774F7A452F4F55314A51643268397941384F6B425644665A59746D3968775576536E543744684276723773464A714A47394D7770765064484B6A457A6F4A3533716E57766F4339634639413348556E433641434A6438444170583275326B2B4177776941487668575279304941445031373461794A2F50773D3D | +-----+示例2:重新加密封装Keyset。
select REWRAP_KEYSET('acs:kms:cn-beijing:189273228874****:key/key-bjj6527b6c6465hsf****', 'acs:ram::189273228874****:role/mf-secr', unhex('613256354C574A71616A59314D6A64694E6D4D324E44593161484E6D65576732595331315A586435646D4678596A6C36555437693738632B647070524B46334E5263497567384A6B36716C4E54354133734F6E4776376258453132524E6C4B6E5163703859787132536C6D794F6E4A6975797541745448374F6B5132412B4B6947502F4A7530756477694B736B503033576643726E45646D666F6F324D61774F7A452F4F55314A51643268397941384F6B425644665A59746D3968775576536E543744684276723773464A714A47394D7770765064484B6A457A6F4A3533716E57766F4339634639413348556E433641434A6438444170583275326B2B4177776941487668575279304941445031373461794A2F50773D3D'));返回结果如下。
+------+ | _c0 | +------+ | a2V5LWJqajY1MjdiNmM2NDY1aHNmeWg2YS11ZXd5dmFxYjl60Kftgx5o1sQH4kkwRboFSYUmcVKjF1GKF+JU5gKSp3xOF1xjKdb6fGZyNuD4YSAzqNTD7x7j5fzTLW2+9a+8BmS1z3ZP1RjNL6Lp93FAC4NWg/jtggh6WOTXrVoG67/CfzdWro65YDTPZpe52K416gpfW18GXSOzu9q4swMti0UrScl/fTg6eOIMYgoPCfBh9qvXhNSR72J+qXU1vHcyYNQL6UewsBE2suVRFQ=3D=3D |示例3:密钥轮转。
select ROTATE_WRAPPED_KEYSET('acs:kms:cn-beijing:189273228874****:key/key-bjj6527b6c6465hsf****', 'acs:ram::189273228874****:role/mf-secr', unhex('613256354C574A71616A59314D6A64694E6D4D324E44593161484E6D65576732595331315A586435646D4678596A6C36555437693738632B647070524B46334E5263497567384A6B36716C4E54354133734F6E4776376258453132524E6C4B6E5163703859787132536C6D794F6E4A6975797541745448374F6B5132412B4B6947502F4A7530756477694B736B503033576643726E45646D666F6F324D61774F7A452F4F55314A51643268397941384F6B425644665A59746D3968775576536E543744684276723773464A714A47394D7770765064484B6A457A6F4A3533716E57766F4339634639413348556E433641434A6438444170583275326B2B4177776941487668575279304941445031373461794A2F50773D3D'), 'AES-GCM-256', 'descrption');返回结果如下。
+------+ | _c0 | +------+ | a2V5LWJqajY1MjdiNmM2NDY1aHNmeWg2YS11ZXd5dmFxYjl67ZxGgfbQhsOududp3FuxLFW1qWt7fF2fT2mAqFekH3D/SoooVf1Jgj0dS/3kxHLQImthef+fCca5vRbVYbOeSsjhGI841WhJvYE1KzRuTpV04SpzVimCovlPPiYCm1649Vhkua1/zUu2W0ioCPnXzHIANhoOIXM2mAV+EfuRCjLUtcJhMdCnu+whHwkGXMYugtXmLxZIBHaJNvO9I3tntplTzxElVmj/LpDrAkg0mKahLJa7FhcJ8cn/JHjp9sk0MhHQc/5X14vHBJuulkYkukcF/kZ+AFVfWes5pZOMs8Og3pYEjCESMiiMONy/CpIrYepapgsKqRAmCGxRv/7aDOZyaAV5Jdz31NotMCBi/hrYBwyU0QdAq5pvsOEdXVIJyazViQ=3D=3D | +------+示例4:数据加解密。
创建表
mf_keyset_kms并写入Keyset。-----创建表 create table mf_keyset_kms (id string,ks binary); -----生产keyset加密后写入表 insert into mf_keyset_kms select '1', NEW_WRAPPED_KEYSET( 'acs:kms:cn-beijing:189273228874****:key/key-bjj6527b6c6465hsf****', 'acs:ram::189273228874****:role/mf-secr', 'AES-GCM-256', 'description');确认写入结果。
----查询表 select id,hex(ks) from mf_keyset_kms; ----返回结果如下 +----+------+ | id | ks | +----+------+ | 1 | 613256354C574A71616A59314D6A64694E6D4D324E44593161484E6D65576732595331315A586435646D4678596A6C36555437693738632B647070524B46334E5263497567384A6B36716C4E54354133734F6E4776376258453132524E6C4B6E5163703859787132536C6D794F6E4A6975797541745448374F6B5132412B4B6947502F4A7530756477694B736B503033576643726E45646D666F6F324D61774F7A452F4F55314A51643268397941384F6B425644665A59746D3968775576536E543744684276723773464A714A47394D7770765064484B6A457A6F4A3533716E57766F4339634639413348556E433641434A6438444170583275326B2B4177776941487668575279304941445031373461794A2F50773D3D |对表
mf_test_data中的tel字段进行加解密。将表
mf_test_data中的tel字段加密。--加密tel列,目前keyset只能输入常量 select id, name, ENHANCED_SYM_ENCRYPT( USE_WRAPPED_KEYSET('acs:kms:cn-beijing:189273228874****:key/key-bjj6527b6c6465hsf****', 'acs:ram::189273228874****:role/mf-secr', unhex('613256354C574A71616A59314D6A64694E6D4D324E44593161484E6D65576732595331315A586435646D4678596A6C36555437693738632B647070524B46334E5263497567384A6B36716C4E54354133734F6E4776376258453132524E6C4B6E5163703859787132536C6D794F6E4A6975797541745448374F6B5132412B4B6947502F4A7530756477694B736B503033576643726E45646D666F6F324D61774F7A452F4F55314A51643268397941384F6B425644665A59746D3968775576536E543744684276723773464A714A47394D7770765064484B6A457A6F4A3533716E57766F4339634639413348556E433641434A6438444170583275326B2B4177776941487668575279304941445031373461794A2F50773D3D') ), tel ) as tel FROM mf_test_data;返回结果如下。
+----+------+------+ | id | name | tel | +----+------+------+ | 1 | kyle | =1A=B88=F7=C5A=DF=DC=91=A6R=F8{=EB=A5_x=AD=AF=FF=9A=14=D81<=8BO=EB=F5=D3Jn=E8=0ESe=01=00=A0=AC=0D=C8=0De=B9=E4=84=AB=F0f=AE~Dt=C5W=FAx=A5=11=01t=95=DF=FA/-=BC7=C5G | | 2 | tom | =1A=B88=F7=C5A=DF=DC=91=A6R=F8{=EB=A5_x=AD=AF=FF=9A=14=D81<=8BO=EB=F5=D3Jn=E8=0ESe=01=00=B0=BF=0D=C8=0DejL{;.w0=80,=E6=86V@b=F3=AB=DEY=A6=02=07=001=E0[=E7V | +----+------+------+将表
mf_test_data中的tel字段解密。select id, name, ENHANCED_SYM_DECRYPT( USE_WRAPPED_KEYSET('acs:kms:cn-beijing:189273228874****:key/key-bjj6527b6c6465hsf****', 'acs:ram::189273228874****:role/mf-secr', unhex('613256354C574A71616A59314D6A64694E6D4D324E44593161484E6D65576732595331315A586435646D4678596A6C36555437693738632B647070524B46334E5263497567384A6B36716C4E54354133734F6E4776376258453132524E6C4B6E5163703859787132536C6D794F6E4A6975797541745448374F6B5132412B4B6947502F4A7530756477694B736B503033576643726E45646D666F6F324D61774F7A452F4F55314A51643268397941384F6B425644665A59746D3968775576536E543744684276723773464A714A47394D7770765064484B6A457A6F4A3533716E57766F4339634639413348556E433641434A6438444170583275326B2B4177776941487668575279304941445031373461794A2F50773D3D') ), ENHANCED_SYM_ENCRYPT( USE_WRAPPED_KEYSET('acs:kms:cn-beijing:189273228874****):key/key-bjj6527b6c6465hsf****', 'acs:ram::189273228874****:role/mf-secr', unhex('613256354C574A71616A59314D6A64694E6D4D324E44593161484E6D65576732595331315A586435646D4678596A6C36555437693738632B647070524B46334E5263497567384A6B36716C4E54354133734F6E4776376258453132524E6C4B6E5163703859787132536C6D794F6E4A6975797541745448374F6B5132412B4B6947502F4A7530756477694B736B503033576643726E45646D666F6F324D61774F7A452F4F55314A51643268397941384F6B425644665A59746D3968775576536E543744684276723773464A714A47394D7770765064484B6A457A6F4A3533716E57766F4339634639413348556E433641434A6438444170583275326B2B4177776941487668575279304941445031373461794A2F50773D3D') ), tel ), '' ) as tel FROM mf_test_data;返回结果如下。
+----+------+------+ | id | name | tel | +----+------+------+ | 1 | kyle | 13900001234 | | 2 | tom | 13900001111 | +----+------+------+