本文介绍Terraform场景下,迁移后如何修改Terraform配置。
为什么需要修改Terraform配置
当您将用户主密钥(CMK)和凭据从共享版KMS(KMS 1.0)迁移到KMS 3.0实例中时,密钥和凭据会归属于特定的KMS实例,因此迁移后会增加一个KMS实例ID属性。
当Terraform检测到代码所描述的配置与实际基础设施对象存在差异时,便会制定变更计划以更新基础设施对象,从而使其与代码描述的状态相匹配。这会导致迁移的CMK或凭据被释放,并创建一个新的CMK或凭据。为了解决这一问题,迁移完成后,您需要按照以下步骤修改现有的Terraform配置。
修改Terraform配置
如果您不想修改原来的Terraform适应新的变更,使用方案一增加ignore_changes语句,如果您想使Terraform适应新的变更,选用方案二增加dkms_instance_id相关语句。
方案一:增加ignore_changes语句
配置了 ignore_changes 语句后,Terraform在执行计划(plan)和应用(apply)操作时,会忽略dkms_instance_id等字段的修改。
在"alicloud_kms_key"中执行以下操作:
增加
ignore_changes = [dkms_instance_id,automatic_rotation,rotation_interval]语句。如果密钥迁移前关闭了轮转,迁移完成后请开启密钥轮转。轮转的相关介绍,请参见密钥轮转。
为密钥设置默认策略。如果您需要自定义策略,请参见密钥策略概述。
示例中为密钥开启了轮转且轮转周期为90天,为密钥设置了默认密钥策略。具体使用时,请以您的实际业务为准。各配置项的详细介绍,请参见alicloud_kms_key。
resource "alicloud_kms_key" "default_key_encrypt_decrypt" {
# add this
lifecycle {
ignore_changes = [dkms_instance_id,automatic_rotation,rotation_interval]
}
automatic_rotation = "Enabled"
rotation_interval = "90d"
policy = <<EOF
{
"Statement": [
{
"Action": [
"kms:*"
],
"Effect": "Allow",
"Principal": {
"RAM": [
"acs:ram::5135****76002605:*"
]
},
"Resource": [
"*"
],
"Sid": "kms default key policy"
}
],
"Version": "1"
}
EOF
# end of add
description = "test tf"
key_usage = "ENCRYPT/DECRYPT"
key_spec = "Aliyun_AES_256"
origin = "Aliyun_KMS"
pending_window_in_days = 7
tags = {
"Environment" = "test"
"Name" = "KMS-01"
"SupportTeam" = "PlatformEngineering"
"Contact" = "group@example.com"
}
}在"alicloud_kms_secret"中执行以下操作:
增加
ignore_changes = [dkms_instance_id]语句。如果凭据迁移前关闭了轮转,迁移完成后请开启凭据轮转。
为凭据设置默认策略。如果您需要自定义策略,请参见凭据策略概述。
示例中凭据未开启轮转,凭据设置了默认凭据策略。具体使用时,请以您的实际业务为准。各配置项的详细介绍,请参见alicloud_kms_secret。
resource "alicloud_kms_secret" "kms_secret_general" {
# add this
lifecycle {
ignore_changes = [dkms_instance_id]
}
enable_automatic_rotation = false
policy = <<EOF
{
"Statement": [
{
"Action": [
"kms:*"
],
"Effect": "Allow",
"Principal": {
"RAM": [
"acs:ram::5135****76002605:*"
]
},
"Resource": [
"*"
],
"Sid": "kms default secret policy"
}
],
"Version": "1"
}
EOF
# end of add
secret_name = "kms_secret_general1"
description = "secret_data_kms_secret_general"
secret_type = "Generic"
force_delete_without_recovery = true
encryption_key_id = alicloud_kms_key.default_key_encrypt_decrypt.id
version_id = "v1"
secret_data_type ="text"
secret_data = "secret_data_kms_secret_general1"
}方案二:增加dkms_instance_id相关语句
增加dkms_instance_id相关的语句后,针对迁移后的密钥和凭据,Terraform可以准确识别dkms_instance_id的值,并将其配置到alicloud_kms_key资源和alicloud_kms_secret资源中。
以用户已把CMK fecbd43a-********-9c051c8cc26d 迁移到KMS实例(kst-hkk66e****boq8qsxxgxd)为例进行介绍。
在根目录的
main.tf文件中增加以下代码。在
locals中增加dkms_instance_id = var.use_existing_key == true || alicloud_kms_key.kms.0.dkms_instance_id != "" ? alicloud_kms_key.kms.0.dkms_instance_id : null。在
"alicloud_kms_key"中增加dkms_instance_id = var.dkms_instance_id。在
"alicloud_kms_secret"中增加dkms_instance_id = var.dkms_instance_id。
示例如下:
locals { this_kms_key_id = var.use_existing_key == true || var.existing_key_id != "" ? var.existing_key_id : concat(alicloud_kms_key.kms.*.id, [""])[0] dkms_instance_id = var.use_existing_key == true || alicloud_kms_key.kms.0.dkms_instance_id != "" ? alicloud_kms_key.kms.0.dkms_instance_id : null policy = var.use_existing_key == true || alicloud_kms_key.kms.0.policy != "" ? alicloud_kms_key.kms.0.policy : null automatic_rotation= var.use_existing_key == true || alicloud_kms_key.kms.0.automatic_rotation != "" ? alicloud_kms_key.kms.0.automatic_rotation : null rotation_interval= var.automatic_rotation == "Enabled" || alicloud_kms_key.kms.0.rotation_interval != "" ? alicloud_kms_key.kms.0.rotation_interval : null secret_name = var.secret == true ||alicloud_kms_secret.kms.0.secret_name != "" ? alicloud_kms_secret.kms.0.secret_name : null secret_type = var.secret == true ||alicloud_kms_secret.kms.0.secret_type != "" ? alicloud_kms_secret.kms.0.secret_type : null version_id = var.secret == true ||alicloud_kms_secret.kms.0.version_id != "" ? alicloud_kms_secret.kms.0.version_id : null force_delete_without_recovery = var.secret == true ||alicloud_kms_secret.kms.0.force_delete_without_recovery != "" ? alicloud_kms_secret.kms.0.force_delete_without_recovery : null secret_data = var.secret == true ||alicloud_kms_secret.kms.0.secret_data != "" ? alicloud_kms_secret.kms.0.secret_data : null secret_data_type = var.secret == true ||alicloud_kms_secret.kms.0.secret_data_type != "" ? alicloud_kms_secret.kms.0.secret_data_type : null enable_automatic_rotation = var.secret == true ||alicloud_kms_secret.kms.0.enable_automatic_rotation != "" ? alicloud_kms_secret.kms.0.enable_automatic_rotation : null } resource "alicloud_kms_key" "kms" { count = var.use_existing_key == true ? 0 : var.create_kms ? 1 : 0 description = var.description key_usage = var.key_usage pending_window_in_days = var.pending_window_in_days status = var.status policy = var.policy automatic_rotation = var.automatic_rotation rotation_interval = var.rotation_interval # add this dkms_instance_id = var.dkms_instance_id # end of add } resource "alicloud_kms_secret" "kms" { count = var.existing_key_id != "" ? var.existing_key_id : var.encrypt ? 1 : 0 secret_name = var.secret_name encryption_key_id = concat(alicloud_kms_key.kms.*.id, [""])[0] secret_type = var.secret_type version_id = var.version_id force_delete_without_recovery = var.force_delete_without_recovery # add this dkms_instance_id = var.dkms_instance_id # end of add secret_data = var.secret_data secret_data_type =var.secret_data_type enable_automatic_rotation = var.enable_automatic_rotation }在根目录
variable.tf文件中定义dkms_instance_id变量。重要default取值必须为""或null。# module default variable variable "dkms_instance_id" { description = "The ID of the KMS instance." type = string default = "" }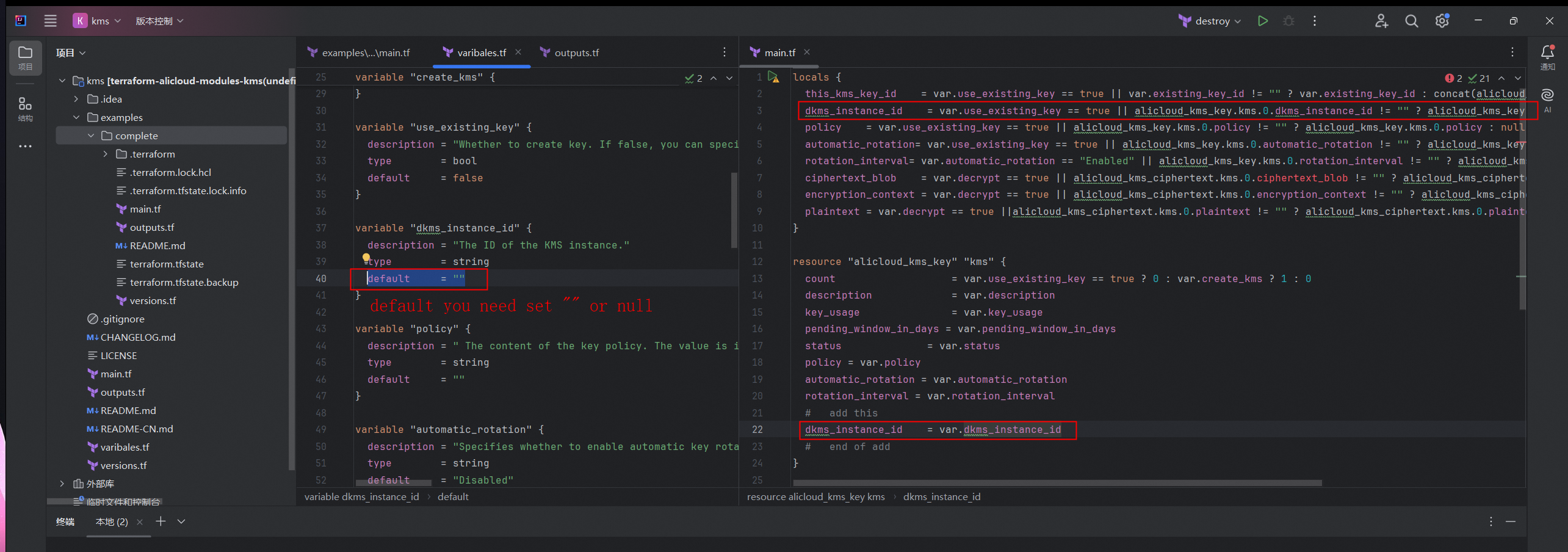
在密钥相关模块下增加实例ID的信息、设置密钥策略,并根据业务需要决定是否开启轮转。
轮转周期:示例中轮转周期为90天,请根据实际情况修改。
KMS实例ID:示例为
kst-hkk66e****boq8qsxxgxd,请根据实际情况修改。密钥策略:示例提供的为默认策略,如果您需要自定义策略,请参见密钥策略概述。
automatic_rotation = "Enabled" rotation_interval = "90d" dkms_instance_id = "kst-hkk66e****boq8qsxxgxd" policy = <<EOF { "Statement": [ { "Action": [ "kms:*" ], "Effect": "Allow", "Principal": { "RAM": [ "acs:ram::5135****76002605:*" ] }, "Resource": [ "*" ], "Sid": "kms default key policy" } ], "Version": "1" } EOF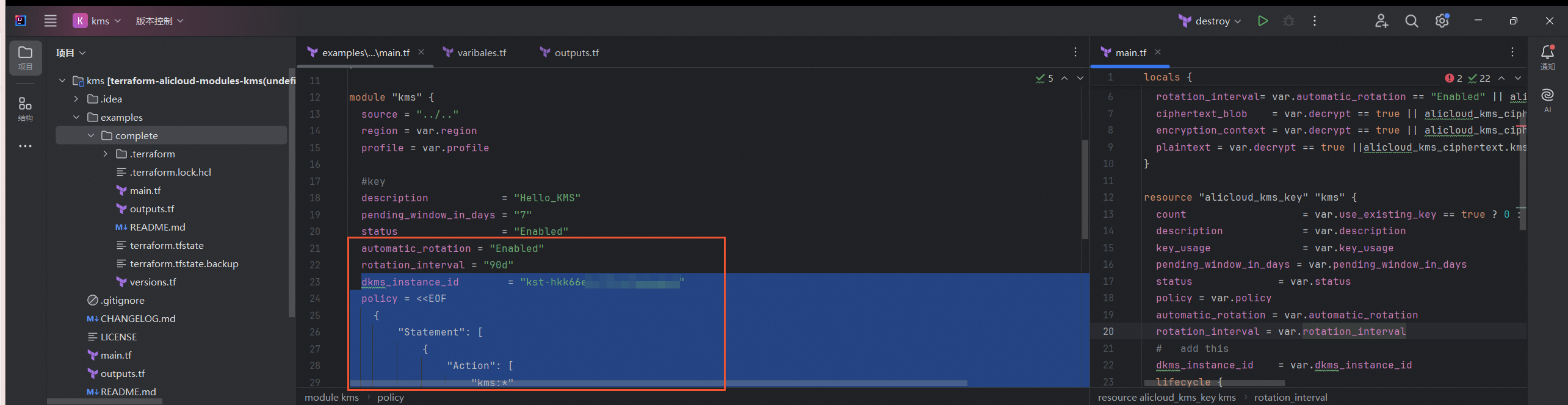
在凭据相关模块下增加实例ID的信息、设置凭据策略,并根据业务需要决定是否开启轮转。
轮转周期:示例中未开启轮转,请根据实际情况修改。
KMS实例ID:示例为
kst-hkk66e****boq8qsxxgxd,请根据实际情况修改。凭据策略:示例提供的为默认策略,如果您需要自定义策略,请参见凭据策略概述。
#secret secret_data = "secret_data_kms_secret_general1" secret_name = "kms_secret_general1" version_id = "v1" secret_data_type ="text" secret_type = "Generic" enable_automatic_rotation = false dkms_instance_id = "kst-hkk66e****boq8qsxxgxd" policy = <<EOF { "Statement": [ { "Action": [ "kms:*" ], "Effect": "Allow", "Principal": { "RAM": [ "acs:ram::5135****76002605:*" ] }, "Resource": [ "*" ], "Sid": "kms default secret policy" } ], "Version": "1" } EOF force_delete_without_recovery = true