本文为您介绍在首次使用ACK时,如何通过Terraform开通容器服务ACK并进行容器服务角色的授权。
本教程所含示例代码支持一键运行,您可以直接运行代码。一键运行
前提条件
由于阿里云账号(主账号)具有资源的所有权限,一旦发生泄露将面临重大风险。建议您使用RAM用户,并为该RAM用户创建AccessKey,具体操作方式请参见创建RAM用户和创建AccessKey。
为运行Terraform命令的RAM用户绑定以下最小权限策略,以获取管理本示例所涉及资源的权限。更多信息,请参见为RAM用户授权。
该权限策略允许RAM用户创建、查看和删除RAM角色,并支持对RAM角色权限策略的管理。
{ "Version": "1", "Statement": [ { "Effect": "Allow", "Action": [ "ram:GetRole", "ram:ListRoles", "ram:AttachPolicyToRole", "ram:ListPoliciesForRole", "ram:CreateRole", "ram:DetachPolicyFromRole", "ram:DeleteRole" ], "Resource": "*" } ] }准备Terraform运行环境,您可以选择以下任一方式来使用Terraform。
在Terraform Explorer中使用Terraform:阿里云提供了Terraform的在线运行环境,您无需安装Terraform,登录后即可在线使用和体验Terraform。适用于零成本、快速、便捷地体验和调试Terraform的场景。
Cloud Shell:阿里云Cloud Shell中预装了Terraform的组件,并已配置好身份凭证,您可直接在Cloud Shell中运行Terraform的命令。适用于低成本、快速、便捷地访问和使用Terraform的场景。
在本地安装和配置Terraform:适用于网络连接较差或需要自定义开发环境的场景。
使用的资源
alicloud_ack_service:自动开通容器服务ACK。
alicloud_ram_role:创建一个RAM角色。
alicloud_ram_role_policy_attachment:为RAM角色绑定其他权限。
alicloud_ram_roles:根据指定的过滤条件,返回阿里云账号中RAM角色的列表。
步骤一:开通容器服务ACK
在创建ACK集群前您需要开通容器服务。
创建一个工作目录,并在该工作目录中创建名为main.tf的配置文件,然后将以下代码复制到main.tf中。
// 开通容器服务ACK。 data "alicloud_ack_service" "open" { enable = "On" type = "propayasgo" }执行如下命令,初始化Terraform运行环境。
terraform init返回信息如下,Terraform初始化成功。
Terraform has been successfully initialized! You may now begin working with Terraform. Try running "terraform plan" to see any changes that are required for your infrastructure. All Terraform commands should now work. If you ever set or change modules or backend configuration for Terraform, rerun this command to reinitialize your working directory. If you forget, other commands will detect it and remind you to do so if necessary.执行如下命令,开通容器服务ACK。
terraform apply在执行过程中,根据提示输入
yes并按下Enter键,等待命令执行完成,若出现以下信息,则表示容器服务ACK开通成功。You can apply this plan to save these new output values to the Terraform state, without changing any real infrastructure. Do you want to perform these actions? Terraform will perform the actions described above. Only 'yes' will be accepted to approve. Enter a value: yes Apply complete! Resources: 0 added, 0 changed, 0 destroyed.
步骤二:授权角色
首次登录容器服务 Kubernetes 版时,需要为服务账号授予系统服务角色,具体步骤如下。
在
main.tf配置文件中增加如下授权模板。// 所需RAM角色。 variable "roles" { type = list(object({ name = string policy_document = string description = string policy_name = string })) default = [ { name = "AliyunCSManagedLogRole" policy_document = "{\"Statement\":[{\"Action\":\"sts:AssumeRole\",\"Effect\":\"Allow\",\"Principal\":{\"Service\":[\"cs.aliyuncs.com\"]}}],\"Version\":\"1\"}" description = "集群的日志组件使用此角色来访问您在其他云产品中的资源。" policy_name = "AliyunCSManagedLogRolePolicy" }, { name = "AliyunCSManagedCmsRole" policy_document = "{\"Statement\":[{\"Action\":\"sts:AssumeRole\",\"Effect\":\"Allow\",\"Principal\":{\"Service\":[\"cs.aliyuncs.com\"]}}],\"Version\":\"1\"}" description = "集群的CMS组件使用此角色来访问您在其他云产品中的资源。" policy_name = "AliyunCSManagedCmsRolePolicy" }, { name = "AliyunCSManagedCsiRole" policy_document = "{\"Statement\":[{\"Action\":\"sts:AssumeRole\",\"Effect\":\"Allow\",\"Principal\":{\"Service\":[\"cs.aliyuncs.com\"]}}],\"Version\":\"1\"}" description = "集群的存储组件使用此角色来访问您在其他云产品中的资源。" policy_name = "AliyunCSManagedCsiRolePolicy" }, { name = "AliyunCSManagedCsiPluginRole" policy_document = "{\"Statement\":[{\"Action\":\"sts:AssumeRole\",\"Effect\":\"Allow\",\"Principal\":{\"Service\":[\"cs.aliyuncs.com\"]}}],\"Version\":\"1\"}" description = "集群的存储组件使用此角色来访问您在其他云产品中的资源。" policy_name = "AliyunCSManagedCsiPluginRolePolicy" }, { name = "AliyunCSManagedCsiProvisionerRole" policy_document = "{\"Statement\":[{\"Action\":\"sts:AssumeRole\",\"Effect\":\"Allow\",\"Principal\":{\"Service\":[\"cs.aliyuncs.com\"]}}],\"Version\":\"1\"}" description = "集群的存储组件使用此角色来访问您在其他云产品中的资源。" policy_name = "AliyunCSManagedCsiProvisionerRolePolicy" }, { name = "AliyunCSManagedVKRole" policy_document = "{\"Statement\":[{\"Action\":\"sts:AssumeRole\",\"Effect\":\"Allow\",\"Principal\":{\"Service\":[\"cs.aliyuncs.com\"]}}],\"Version\":\"1\"}" description = "ACK Serverless集群的VK组件使用此角色来访问您在其他云产品中的资源。" policy_name = "AliyunCSManagedVKRolePolicy" }, { name = "AliyunCSServerlessKubernetesRole" policy_document = "{\"Statement\":[{\"Action\":\"sts:AssumeRole\",\"Effect\":\"Allow\",\"Principal\":{\"Service\":[\"cs.aliyuncs.com\"]}}],\"Version\":\"1\"}" description = "集群默认使用此角色来访问您在其他云产品中的资源。" policy_name = "AliyunCSServerlessKubernetesRolePolicy" }, { name = "AliyunCSKubernetesAuditRole" policy_document = "{\"Statement\":[{\"Action\":\"sts:AssumeRole\",\"Effect\":\"Allow\",\"Principal\":{\"Service\":[\"cs.aliyuncs.com\"]}}],\"Version\":\"1\"}" description = "集群审计功能使用此角色来访问您在其他云产品中的资源。" policy_name = "AliyunCSKubernetesAuditRolePolicy" }, { name = "AliyunCSManagedNetworkRole" policy_document = "{\"Statement\":[{\"Action\":\"sts:AssumeRole\",\"Effect\":\"Allow\",\"Principal\":{\"Service\":[\"cs.aliyuncs.com\"]}}],\"Version\":\"1\"}" description = "集群网络组件使用此角色来访问您在其他云产品中的资源。" policy_name = "AliyunCSManagedNetworkRolePolicy" }, { name = "AliyunCSDefaultRole" policy_document = "{\"Statement\":[{\"Action\":\"sts:AssumeRole\",\"Effect\":\"Allow\",\"Principal\":{\"Service\":[\"cs.aliyuncs.com\"]}}],\"Version\":\"1\"}" description = "集群操作时默认使用此角色来访问您在其他云产品中的资源。" policy_name = "AliyunCSDefaultRolePolicy" }, { name = "AliyunCSManagedKubernetesRole" policy_document = "{\"Statement\":[{\"Action\":\"sts:AssumeRole\",\"Effect\":\"Allow\",\"Principal\":{\"Service\":[\"cs.aliyuncs.com\"]}}],\"Version\":\"1\"}" description = "集群默认使用此角色来访问您在其他云产品中的资源。" policy_name = "AliyunCSManagedKubernetesRolePolicy" }, { name = "AliyunCSManagedArmsRole" policy_document = "{\"Statement\":[{\"Action\":\"sts:AssumeRole\",\"Effect\":\"Allow\",\"Principal\":{\"Service\":[\"cs.aliyuncs.com\"]}}],\"Version\":\"1\"}" description = "集群Arms插件使用此角色来访问您在其他云产品中的资源。" policy_name = "AliyunCSManagedArmsRolePolicy" }, { name = "AliyunCISDefaultRole" policy_document = "{\"Statement\":[{\"Action\":\"sts:AssumeRole\",\"Effect\":\"Allow\",\"Principal\":{\"Service\":[\"cs.aliyuncs.com\"]}}],\"Version\":\"1\"}" description = "容器服务(CS)智能运维使用此角色来访问您在其他云产品中的资源。" policy_name = "AliyunCISDefaultRolePolicy" }, { name = "AliyunOOSLifecycleHook4CSRole" policy_document = "{\"Statement\":[{\"Action\":\"sts:AssumeRole\",\"Effect\":\"Allow\",\"Principal\":{\"Service\":[\"oos.aliyuncs.com\"]}}],\"Version\":\"1\"}" description = "集群扩缩容节点池依赖OOS服务,OOS使用此角色来访问您在其他云产品中的资源。" policy_name = "AliyunOOSLifecycleHook4CSRolePolicy" }, { name = "AliyunCSManagedAutoScalerRole" policy_document = "{\"Statement\":[{\"Action\":\"sts:AssumeRole\",\"Effect\":\"Allow\",\"Principal\":{\"Service\":[\"cs.aliyuncs.com\"]}}],\"Version\":\"1\"}" description = "集群的弹性伸缩组件使用此角色来访问您在其他云产品中的资源。" policy_name = "AliyunCSManagedAutoScalerRolePolicy" } ] } // 查询RAM角色列表 data "alicloud_ram_roles" "roles" { policy_type = "Custom" name_regex = "^Aliyun.*Role$" } locals { # 提取所有所需RAM角色name all_role_names = [for role in var.roles : role.name] # 提取已存在的RAM角色name created_role_names = [for role in data.alicloud_ram_roles.roles.roles : role.name] # 计算补集:即找出还未创建的所需RAM角色 complement_names = setsubtract(local.all_role_names, local.created_role_names) # 待创建的RAM角色 complement_roles = [for role in var.roles : role if contains(local.complement_names, role.name)] } // 创建角色。 resource "alicloud_ram_role" "role" { for_each = { for r in local.complement_roles : r.name => r } name = each.value.name document = each.value.policy_document description = each.value.description force = true } // 角色关联系统权限。 resource "alicloud_ram_role_policy_attachment" "attach" { for_each = { for r in local.complement_roles : r.name => r } policy_name = each.value.policy_name policy_type = "System" role_name = each.value.name depends_on = [alicloud_ram_role.role] }说明在示例中,variable表示作为参数提供给Terraform使用的输入变量。本示例中参数值请参见附录,其中,服务角色是必选参数,可选角色请根据实际情况选择。
创建执行计划,并预览变更。
terraform plan执行如下命令应用执行计划,为您的账号进行角色授权。
terraform apply在执行过程中,根据提示输入
yes并按下Enter键,等待命令执行完成,若出现以下信息,则表示授权完成。Apply complete! Resources: 2 added, 0 changed, 0 destroyed.验证结果。
执行terraform show命令
您可以使用以下命令查询Terraform已创建的资源详细信息:
terraform show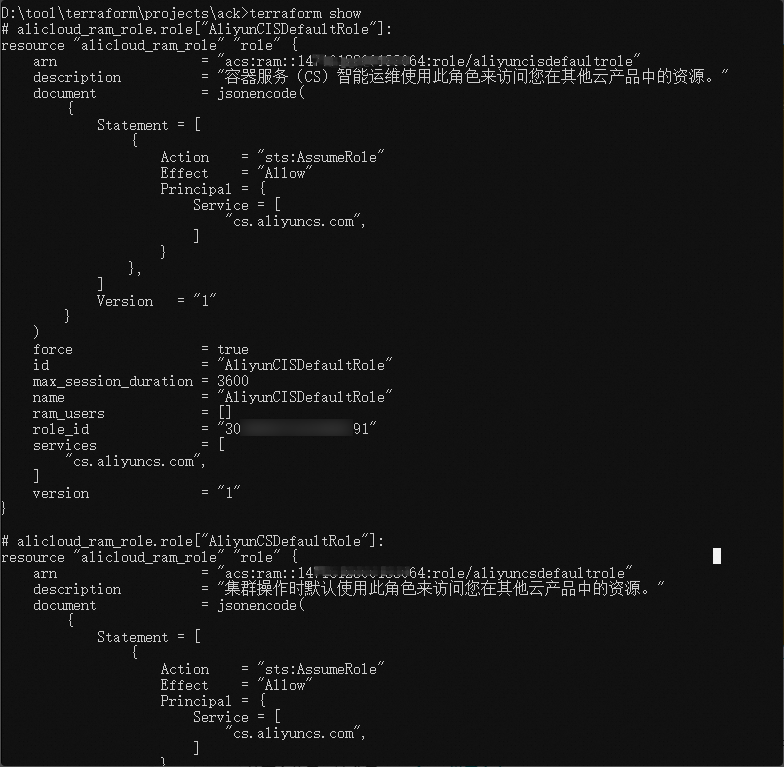
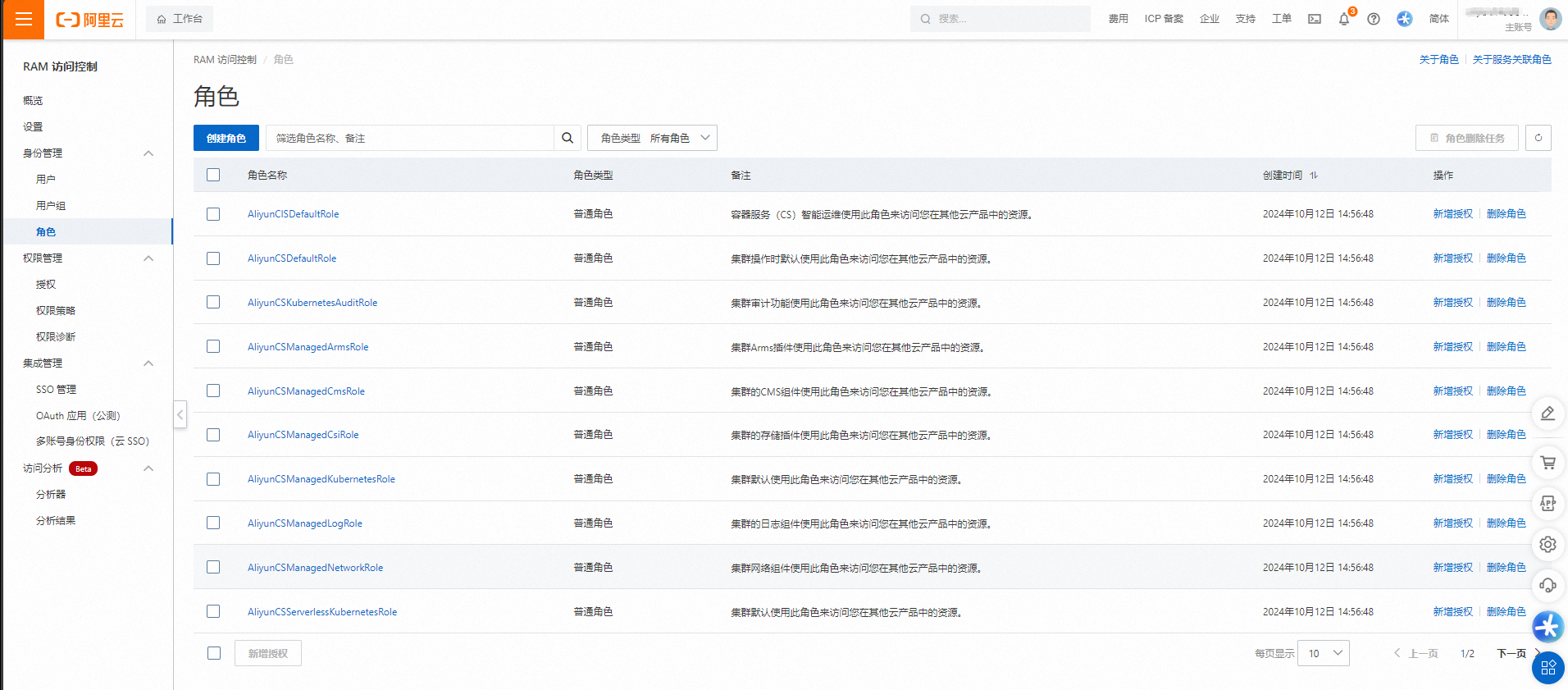
登录RAM控制台
登录RAM控制台,查看已创建的角色。
清理资源
当您不再需要上述通过Terraform创建或管理的资源时,请运行以下命令以释放资源。关于terraform destroy的更多信息,请参见Terraform常用命令。
terraform destroy完整示例
本教程所含示例代码支持一键运行,您可以直接运行代码。一键运行
示例代码
附录
服务角色
AliyunCSManagedLogRole
说明:
ACK托管集群和ACK Serverless集群的日志组件使用该角色访问您在SLS服务中的资源。
授权代码:
{ name = "AliyunCSManagedLogRole" policy_document = "{\"Statement\":[{\"Action\":\"sts:AssumeRole\",\"Effect\":\"Allow\",\"Principal\":{\"Service\":[\"cs.aliyuncs.com\"]}}],\"Version\":\"1\"}" description = "集群的日志组件使用此角色来访问您在其他云产品中的资源。" policy_name = "AliyunCSManagedLogRolePolicy" }
AliyunCSManagedCmsRole
说明:
ACK托管集群和ACK Serverless集群的监控组件使用该角色访问您在CMS、SLS服务中的资源。
授权代码:
{ name = "AliyunCSManagedCmsRole" policy_document = "{\"Statement\":[{\"Action\":\"sts:AssumeRole\",\"Effect\":\"Allow\",\"Principal\":{\"Service\":[\"cs.aliyuncs.com\"]}}],\"Version\":\"1\"}" description = "集群的CMS组件使用此角色来访问您在其他云产品中的资源。" policy_name = "AliyunCSManagedCmsRolePolicy" }
AliyunCSManagedCsiRole
说明:
ACK托管集群、ACK Edge集群和ACK Serverless集群的存储组件使用该角色访问您在ECS、NAS、OSS等服务中的资源。
授权代码:
{ name = "AliyunCSManagedCsiRole" policy_document = "{\"Statement\":[{\"Action\":\"sts:AssumeRole\",\"Effect\":\"Allow\",\"Principal\":{\"Service\":[\"cs.aliyuncs.com\"]}}],\"Version\":\"1\"}" description = "集群的存储插件使用此角色来访问您在其他云产品中的资源。" policy_name = "AliyunCSManagedCsiRolePolicy" }
AliyunCSManagedCsiPluginRole
说明:
ACK托管集群、ACK Edge集群和ACK Serverless集群的存储组件(新版csi-plugin组件)使用该角色访问您在ECS服务中的资源。
授权代码:
{ name = "AliyunCSManagedCsiPluginRole" policy_document = "{\"Statement\":[{\"Action\":\"sts:AssumeRole\",\"Effect\":\"Allow\",\"Principal\":{\"Service\":[\"cs.aliyuncs.com\"]}}],\"Version\":\"1\"}" description = "ACK托管集群、ACK Edge集群和ACK Serverless集群的存储组件(新版csi-plugin组件)使用该角色访问您在ECS服务中的资源。" policy_name = "AliyunCSManagedCsiPluginRolePolicy" }
AliyunCSManagedCsiProvisionerRole
说明:
ACK托管集群、ACK Edge集群和ACK Serverless集群的存储组件(新版csi-provisioner组件)使用该角色访问您在ECS、NAS、OSS服务中的资源。
授权代码:
{ name = "AliyunCSManagedCsiProvisionerRole" policy_document = "{\"Statement\":[{\"Action\":\"sts:AssumeRole\",\"Effect\":\"Allow\",\"Principal\":{\"Service\":[\"cs.aliyuncs.com\"]}}],\"Version\":\"1\"}" description = "ACK托管集群、ACK Edge集群和ACK Serverless集群的存储组件(新版csi-provisioner组件)使用该角色访问您在ECS、NAS、OSS服务中的资源。" policy_name = "AliyunCSManagedCsiProvisionerRolePolicy" }
AliyunCSServerlessKubernetesRole
说明:
ACK Edge集群和ACK Serverless集群使用该角色来访问您在ECS、VPC、SLB、Private Zone等服务中的资源。
授权代码:
{ name = "AliyunCSServerlessKubernetesRole" policy_document = "{\"Statement\":[{\"Action\":\"sts:AssumeRole\",\"Effect\":\"Allow\",\"Principal\":{\"Service\":[\"cs.aliyuncs.com\"]}}],\"Version\":\"1\"}" description = "集群默认使用此角色来访问您在其他云产品中的资源。" policy_name = "AliyunCSServerlessKubernetesRolePolicy" }
AliyunCSKubernetesAuditRole
说明:
ACK托管集群、ACK Edge集群和ACK Serverless集群的审计功能组件使用该角色来访问您在SLS服务中的资源。
授权代码:
{ name = "AliyunCSKubernetesAuditRole" policy_document = "{\"Statement\":[{\"Action\":\"sts:AssumeRole\",\"Effect\":\"Allow\",\"Principal\":{\"Service\":[\"cs.aliyuncs.com\"]}}],\"Version\":\"1\"}" description = "集群审计功能使用此角色来访问您在其他云产品中的资源。" policy_name = "AliyunCSKubernetesAuditRolePolicy" }
AliyunCSManagedNetworkRole
说明:
ACK托管集群、ACK Edge集群和ACK Serverless集群的网络组件使用该角色访问您在ECS、VPC服务中的资源。
授权代码:
{ name = "AliyunCSManagedNetworkRole" policy_document = "{\"Statement\":[{\"Action\":\"sts:AssumeRole\",\"Effect\":\"Allow\",\"Principal\":{\"Service\":[\"cs.aliyuncs.com\"]}}],\"Version\":\"1\"}" description = "集群网络组件使用此角色来访问您在其他云产品中的资源。" policy_name = "AliyunCSManagedNetworkRolePolicy" }
AliyunCSDefaultRole
说明:
容器服务 Kubernetes 版在管控操作中使用该角色访问您在ECS、VPC、SLB、ROS、ESS等服务中的资源。
授权代码:
{ name = "AliyunCSDefaultRole" policy_document = "{\"Statement\":[{\"Action\":\"sts:AssumeRole\",\"Effect\":\"Allow\",\"Principal\":{\"Service\":[\"cs.aliyuncs.com\"]}}],\"Version\":\"1\"}" description = "集群操作时默认使用此角色来访问您在其他云产品中的资源。" policy_name = "AliyunCSDefaultRolePolicy" }
AliyunCSManagedKubernetesRole
说明:
ACK托管集群和ACK Edge集群使用该角色访问您在ECS、VPC、SLB、ACR等服务中的资源。
授权代码:
{ name = "AliyunCSManagedKubernetesRole" policy_document = "{\"Statement\":[{\"Action\":\"sts:AssumeRole\",\"Effect\":\"Allow\",\"Principal\":{\"Service\":[\"cs.aliyuncs.com\"]}}],\"Version\":\"1\"}" description = "集群默认使用此角色来访问您在其他云产品中的资源。" policy_name = "AliyunCSManagedKubernetesRolePolicy" }
AliyunCSManagedArmsRole
说明:
ACK Edge集群和ACK Serverless集群的应用实时监控组件使用该角色访问您在ARMS服务中的资源。
授权代码:
{ name = "AliyunCSManagedArmsRole" policy_document = "{\"Statement\":[{\"Action\":\"sts:AssumeRole\",\"Effect\":\"Allow\",\"Principal\":{\"Service\":[\"cs.aliyuncs.com\"]}}],\"Version\":\"1\"}" description = "集群Arms插件使用此角色来访问您在其他云产品中的资源。" policy_name = "AliyunCSManagedArmsRolePolicy" }AliyunCISDefaultRole
说明:
ACK容器智能运维平台将使用该角色访问您在ECS、VPC、SLB等服务中的资源,为您提供诊断和巡检等服务。
授权代码:
{ name = "AliyunCISDefaultRole" policy_document = "{\"Statement\":[{\"Action\":\"sts:AssumeRole\",\"Effect\":\"Allow\",\"Principal\":{\"Service\":[\"cs.aliyuncs.com\"]}}],\"Version\":\"1\"}" description = "容器服务(CS)智能运维使用此角色来访问您在其他云产品中的资源。" policy_name = "AliyunCISDefaultRolePolicy" }
可选角色
AliyunCSManagedAcrRole
说明:
ACK托管集群、ACK Edge集群和ACK Serverless集群的免密组件镜像拉取使用该角色访问您在ACR容器镜像服务中的资源。
授权代码:
{ name = "AliyunCSManagedAcrRole" policy_document = "{\"Statement\":[{\"Action\":\"sts:AssumeRole\",\"Effect\":\"Allow\",\"Principal\":{\"Service\":[\"cs.aliyuncs.com\"]}}],\"Version\":\"1\"}" description = "集群的镜像拉取免密插件使用该角色访问您在ACR容器镜像服务中的资源。" policy_name = "AliyunCSManagedAcrRolePolicy" }
AliyunCSManagedNlcRole
说明:
ACK托管集群和ACK Edge集群的节点生命周期控制器使用该角色访问您的ECS和ACK节点池资源。
授权代码:
{ name = "AliyunCSManagedNlcRole" policy_document = "{\"Statement\":[{\"Action\":\"sts:AssumeRole\",\"Effect\":\"Allow\",\"Principal\":{\"Service\":[\"cs.aliyuncs.com\"]}}],\"Version\":\"1\"}" description = "集群托管节点池控制组件使用该角色访问您的ECS和ACK节点池资源。" policy_name = "AliyunCSManagedNlcRolePolicy" }
AliyunCSManagedAutoScalerRole
说明:
ACK托管集群、ACK Edge集群和ACK Serverless集群的弹性伸缩组件使用该角色访问您在ESS和ECS服务中的资源。
授权代码:
{ name = "AliyunCSManagedAutoScalerRole" policy_document = "{\"Statement\":[{\"Action\":\"sts:AssumeRole\",\"Effect\":\"Allow\",\"Principal\":{\"Service\":[\"cs.aliyuncs.com\"]}}],\"Version\":\"1\"}" description = "集群的弹性伸缩组件使用此角色来访问您在其他云产品中的资源。" policy_name = "AliyunCSManagedAutoScalerRolePolicy" }
AliyunCSManagedSecurityRole
说明:
ACK托管集群、ACK Edge集群和ACK Serverless集群的落盘加密和凭据管理组件使用该角色访问您在KMS服务中的资源。
授权代码:
{ name = "AliyunCSManagedSecurityRole" policy_document = "{\"Statement\":[{\"Action\":\"sts:AssumeRole\",\"Effect\":\"Allow\",\"Principal\":{\"Service\":[\"cs.aliyuncs.com\"]}}],\"Version\":\"1\"}" description = "集群的落盘加密插件使用该角色访问您在KMS服务中的资源。" policy_name = "AliyunCSManagedSecurityRolePolicy" }
AliyunCSManagedCostRole
说明:
ACK托管集群、ACK Edge集群和ACK Serverless集群的成本分析组件使用该角色访问您在账单管理API、ECS和ECI服务中的资源。
授权代码:
{ name = "AliyunCSManagedCostRole" policy_document = "{\"Statement\":[{\"Action\":\"sts:AssumeRole\",\"Effect\":\"Allow\",\"Principal\":{\"Service\":[\"cs.aliyuncs.com\"]}}],\"Version\":\"1\"}" description = "集群的成本分析组件使用该角色访问您在账单管理API、ECS和ECI服务中的资源。" policy_name = "AliyunCSManagedCostRolePolicy" }
AliyunCSManagedNimitzRole
说明:
ACK Edge集群的管控组件使用该角色访问您在智能接入网关、VPC和云企业网CEN服务中的资源。
授权代码:
{ name = "AliyunCSManagedNimitzRole" policy_document = "{\"Statement\":[{\"Action\":\"sts:AssumeRole\",\"Effect\":\"Allow\",\"Principal\":{\"Service\":[\"cs.aliyuncs.com\"]}}],\"Version\":\"1\"}" description = "ACK灵骏集群的网络组件使用该角色访问您在智能计算灵骏服务中的资源。" policy_name = "AliyunCSManagedNimitzRolePolicy" }
AliyunCSManagedBackupRestoreRole
说明:
ACK托管集群、ACK Edge集群和ACK Serverless集群的备份中心服务组件使用该角色访问您在云备份(Cloud Backup)服务和OSS服务中的资源。
授权代码:
{ name = "AliyunCSManagedBackupRestoreRole" policy_document = "{\"Statement\":[{\"Action\":\"sts:AssumeRole\",\"Effect\":\"Allow\",\"Principal\":{\"Service\":[\"cs.aliyuncs.com\"]}}],\"Version\":\"1\"}" description = "集群的备份中心组件使用该角色访问您在云备份(Cloud Backup)服务和OSS服务中的资源。" policy_name = "AliyunCSManagedBackupRestoreRolePolicy" }
AliyunCSManagedEdgeRole
说明:
ACK Edge集群的管控组件使用该角色访问您在智能接入网关、VPC和云企业网CEN服务中的资源。
授权代码:
{ name = "AliyunCSManagedEdgeRole" policy_document = "{\"Statement\":[{\"Action\":\"sts:AssumeRole\",\"Effect\":\"Allow\",\"Principal\":{\"Service\":[\"cs.aliyuncs.com\"]}}],\"Version\":\"1\"}" description = "ACK Edge集群的管控组件使用该角色访问您在智能接入网关、VPC和云企业网CEN服务中的资源。" policy_name = "AliyunCSManagedEdgeRolePolicy" }
AliyunOOSLifecycleHook4CSRole
说明:
系统运维管理OOS使用该角色访问您在容器服务 Kubernetes 版、ECS、PolarDB等服务中的资源。
授权代码:
{ name = "AliyunOOSLifecycleHook4CSRole" policy_document = "{\"Statement\":[{\"Action\":\"sts:AssumeRole\",\"Effect\":\"Allow\",\"Principal\":{\"Service\":[\"oos.aliyuncs.com\"]}}],\"Version\":\"1\"}" description = "集群扩缩容节点池依赖OOS服务,OOS使用此角色来访问您在其他云产品中的资源。" policy_name = "AliyunOOSLifecycleHook4CSRolePolicy" }
相关文档
Terraform介绍,请参见Terraform产品介绍。
ROS提供了Terraform托管服务,因此您可以直接在ROS控制台部署Terraform模板。详细操作,请参见创建Terraform类型资源栈。